Fraud Resources
Curated and created for anti-fraud professionals, find the latest news, trends, analysis, topics and reports in these ACFE resources.

This report explores the structure, priorities and performances of in-house fraud investigation teams, providing insights to assess operational effectiveness and strengthen anti-fraud strategies.

Understand how your compensation and benefits compare to your colleagues, including those who have earned the Certified Fraud Examiner (CFE) credential, to help you better plan for the future and advance your career.

To provide best-practices guidance for assessing and managing fraud risks, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) partnered with the Association of Certified Fraud Examiners (ACFE) to create the Fraud Risk Management Guide.

Fraud Magazine is a digital publication delivering timely and insightful information on the latest trends, tools and techniques in the anti-fraud profession.

Find news, analysis and commentary on the global fight against fraud on the ACFE’s official blog. Features insight from ACFE staff and experts in the fields of digital forensics, fraud risk management, compliance and more.

A free, bimonthly e-newsletter highlighting anti-fraud news and analysis, as well as the latest ACFE events and updates.

In this episode of Fraud Talk, ACFE Research Specialist Sam May interviews Patrick Gushue, Acting Director of the Department of Justice's Corporate Whistleblower Awards pilot program. Together, they delve into the program's mission to uncover corporate crime by empowering whistleblowers and fostering a culture of accountability. Patrick provides an in-depth look at the program's focus on internal reporting, compliance frameworks and innovative incentives designed to encourage reporting of misconduct.
Published in Podcasts

Join ACFE Public Information Specialist Stefanie Hallgren in this episode of Fraud Talk, as she dives in with Brandi Pritchard, Assistant Director of Special Investigations at the Washington State Auditor's Office. With International Fraud Awareness Week on the horizon, Pritchard shares the story behind the Auditor’s Office’s dedication to fraud prevention and the unique challenges they face, especially within smaller government entities. From engaging tactics that bring fraud awareness to the community to the “trust but verify” approach that underscores their work, Pritchard reveals how Fraud Week creates a ripple effect inspiring both vigilance and accountability.
Published in Podcasts

In this episode of Fraud Talk, Mason Wilder sits down with Marta Cadavid, founder of NoFraudLatin, to explore the unique challenges of detecting and preventing fraud in Latin America. Cadavid shares her journey, including the creation of a Latin American-specific fraud tree, and how cultural nuances shape the approach to fraud communication. They discuss the vital role of artificial intelligence in analyzing human behavior and predicting fraudulent actions.
Published in Podcasts

Mary Ann Miller, a seasoned cybersecurity and fraud expert, joins Rihonna Scoggins, ACFE Content Manager, on Fraud Talk to dissect the evolving threat landscape of identity fraud and the cutting-edge strategies organizations can deploy to combat it. Miller emphasizes the need to move beyond traditional identity validation methods, focusing instead on diverse attributes and signals to confirm authenticity. They explore the future of passwordless security, highlighting its potential to enhance both security and user experience.
Published in Podcasts

Eddie Miro, author of 'Outlaw Summer, Cyber Dreams: The Hacker's Journey Through Crime and Redemption,' joins John Gill, President of the ACFE, on Fraud Talk to share his story of transformation from hacker to educator. Eddie opens up about his troubled family background and his descent into criminal activities. They delve into the critical topics of physical security, social engineering and the importance of user awareness training for small to medium-sized companies.
Published in Podcasts

Amanda Holden, a partner with Deloitte's Financial Crimes, joins Samuel May, ACFE research specialist, on Fraud Talk to uncover the intricacies of fraud prevention and program integrity in the Canadian public sector. They navigate the crucial role of proactive prevention and detection, addressing the unique challenges faced by public entities in a rapidly evolving fraud landscape. Holden explores the essential COSO framework, emphasizing the balance between expediency and robust fraud controls. Dive into Holdens’s expert insights on breaking down cultural barriers, enhancing information sharing and leveraging cutting-edge data analytics and technology.
Published in Podcasts

Javier Leiva, a writer, investigative journalist, producer and podcaster, joins Jason Zirkle, ACFE Training Director, on Fraud Talk to discuss the use of OSINT in investigations. They delve into the challenges, ethical considerations and future of OSINT investigations. Listen in as Leiva shares insights and tips for leveraging OSINT effectively and responsibly, and delves into the myth of Frank Abagnale.
Published in Podcasts

In this episode of Fraud Talk, Tony McClements, Head of Investigations at Martin Kenny & Co., delves into the infamous U.K. Post Office scandal with ACFE Content Manager, Rihonna Scoggins. As McClements unravels the layers of this miscarriage of justice, he discusses the critical failures of the Horizon IT system and the damaging effects of withheld disclosures during legal proceedings.
Published in Podcasts

In this episode of Fraud Talk, Andi McNeal, ACFE Chief Training Officer, and ACFE Research Director, Mason Wilder, delve into the critical insights of Occupational Fraud 2024: A Report to the Nations, discussing its evolution, consistent themes and groundbreaking findings. They explore the significance of tips and internal controls in detecting fraud, the increased median losses attributed to the COVID-19 pandemic and the shift towards web-based reporting mechanisms. Concluding with actionable advice, the episode underscores the value of the report in enhancing anti-fraud programs and heightening fraud awareness within organizations.
Published in Podcasts

In this episode of Fraud Talk, ACFE Content Manager Rihonna Scoggins, sits down with Amii Barnard-Bahn, an acclaimed coach for legal and compliance executives, to dissect the nuances of navigating difficult conversations as anti-fraud professionals. Barnard-Bahn outlines a six-step strategy to not only prepare the messenger but also to prime the audience, ensuring a blend of empathy and clarity. From psychological readiness to the rehearsal of delivery and understanding the influence of gender dynamics, this episode is packed with insights.
Published in Podcasts

In this episode of Fraud Talk, ACFE Content Manager Rihonna Scoggins meets with Christian Focacci, CEO and Founder of Threat Digital, to discuss the future of risk management and compliance software. The discussion delves into the groundbreaking advancements in large language models, their role in processing unstructured text and the critical importance of explainability in AI-driven solutions. Focacci also addresses the issue of AI washing and offers practical advice for companies and fraud examiners on integrating AI to optimize processes.
Published in Podcasts

In this special edition of Fraud Talk, we focus on the ACFE's annual round-up featured in Fraud Magazine, a highlight anticipated by many in the industry. This year, we offer you an exclusive behind-the-scenes glimpse into the process of selecting the top five most scandalous frauds of 2023. Join John Warren, CEO of the ACFE, and Jennifer Liebman, Assistant Editor of Fraud Magazine, as they meticulously unravel each case, providing an in-depth analysis and insight into the complexities and implications of these notable frauds.
Published in Podcasts





In this episode, ACFE Community Manager Rihonna Scoggins reads a case study submitted by Eduardo “Ed” Cuyos. The case study follows Ed's investigation into fraudulent activities previously missed by the Defense Criminal Investigative Service (DCIS) and the Department of Defense Inspector General (DODIG).
Published in Podcasts

International Fraud Awareness Week provides space to highlight fraud prevention and detection initiatives at companies around the world. Thousands of groups have pledged as Supporting Organizations over the past 22 years, with more doing their part ahead of Fraud Week 2022, held on November 13-19. Bruce Dorris, President and CEO at the ACFE, sits down with John Duffley, the ACFE’s Communications Manager, to discuss how you can participate in Fraud Week, the annual ACFE Board of Regents voting cycle, and what lies ahead as the ACFE enters its 35th year.
Published in Podcasts

In Episode 125 of Fraud Talk, ACFE Training Director Jason Zirkle, CFE, is joined by military veterans from around the world to share their backgrounds and how their experiences have aided them in their roles as CFEs and anti-fraud professionals. Collins Wanderi, CFE, Bill Stakes, CFE, and Monica Meeks, CFE, discuss the tools they’ve gained and advice they offer to veterans and active-duty military members looking to earn their CFE credential.
Published in Podcasts

Eddie Antar founded the Crazy Eddie electronics retail chain in Brooklyn, New York, which rose to prominence across the New York-New Jersey area throughout the 1970s. Operating undetected for years, Eddie’s business practices were grounded in fraud from the very beginning. In Episode 124 of Fraud Talk, Gary Weiss, author of “Retail Gangster: The Insane, Real-Life Story of Crazy Eddie,” discusses this wide-ranging fraud case and ultimate unraveling with ACFE Chief Training Officer John Gill, J.D., CFE.
Published in Podcasts

In the fight against fraud, it can be hard to remember why we do it, especially when the fraudsters never seem to quit. Associate professor of accounting, taxation and business law at SUNY Old Westbury, Dr. David Glodstein, began the Justice for Fraud Victims Project to teach his students — and remind fraud examiners — who we're fighting for: the victims. In this episode, join Dr. Glodstein, CFE, and Kate Pospisil, CFE, the Communications Specialist at the ACFE, as they discuss the Justice for Fraud Victims Project, why programs like this matter and what we can do to further the fight for justice.
Published in Podcasts

The intersection of cyber security and fraud examination is ever-expanding in our new technological landscape. At the 33rd Annual ACFE Global Fraud Conference, ACFE Research Manager Mason Wilder, CFE, and Deputy Superintendent and Director of the Intelligence Unit at the New York Department of Financial Services (NYDFS), Roderick Chambers sat down to discuss the importance of technical controls and knowledge to protect your organization from fraud.
Published in Podcasts

Washington State’s Largest Ponzi Scheme was the catalyst for Tod McDonald, CPA to start his company and push for innovation in financial e-discovery. Years later, he and Garth Leonard, CFE, from Valid8 Financial, join ACFE Community Manager Rihonna Scoggins to explore the current resources at hand to combat fraud and how fraud examiners can assess what tools are the right fit for them in this evolving landscape.
Published in Podcasts

William Shakespeare is widely considered to be one of the most prolific and influential writers of all time. But one group of individuals, who call themselves “Oxfordians” and their theory the "Shakespeare Authorship Question," falsely claim that what we know to be Shakespeare's plays and poetry were actually penned by someone else. In this episode, ACFE Chief Training Officer John Gill, J.D., CFE, joins Michael Pocalyko, CFE, the CEO of SI, as they look at how the qualities of those claiming to disprove Shakespeare's authorship parallel the character of financial and investment fraudsters.
Published in Podcasts

While victims of traditional identity theft often catch it quickly, victims of medical identity theft may not know they are victims until they need critical medical treatment. In this episode, Scott Ward, CFE, senior vice president at Qlarant, discusses the insidious nature of medical identity theft, the impact it has on its victims and what people and governments can do to help combat it.
Published in Podcasts

In this episode, Jim Ducharme, COO of Outseer, a leading technology company in the fight against payment fraud, talks about the rise of "Buy Now, Pay Later" services and how fraudsters are exploiting these new avenues of credit. He also discusses identity assurance and how companies are working to combat payment fraud without adding hurdles for consumers.
Published in Podcasts

In this episode, Larry Nielsen, a detective who has spent the last several years teaching himself about cryptocurrencies, shares advice for fraud examiners who are interested in expanding their toolkits to accommodate cryptocurrency investigations. He also discusses some of his experiences tracing cryptocurrencies in both a law enforcement capacity and as a consultant.
Published in Podcasts

In this episode, renowned tech journalist and podcast host Takara Small discusses what the future of data breaches, cybercrime and cryptocurrency might look like for both individuals and organizations. She also speaks about the role online media plays in exposing fraud and the importance of supporting women, BIPOC and young people breaking into the tech space.
Published in Podcasts

In this episode of Fraud Talk, ACFE Content Manager Rihonna Scoggins interviews Fraud Magazine Assistant Editor Crystal Zuzek, co-author of "Under Pressure". They explore the rising fraud risks facing Gen Z and millennials, both as victims and as perpetrators. From emotionally manipulative scams like sextortion to friendly fraud and the glamorization of con artists, Zuzek shares insight and real stories that reveal how digital lifestyles and economic pressures are shaping the next generation.
Published in Podcasts

Whistleblowers are often key to uncovering fraud—but what happens after they report? In this episode of Fraud Talk, Jacqueline Garrick, founder of Whistleblowers of America and the Workplace Promise Institute, shares her journey from whistleblower to advocate. From moral injury to PTSD, Garrick shares how peer support and trauma-informed workplaces can protect whistleblowers and strengthen fraud prevention efforts.
Published in Podcasts

In this episode of Fraud Talk, ACFE Content Manager Rihonna Scoggins speaks with Victor Cardona, adjunct professor of forensic accounting at California State Polytechnic University, Pomona, to discuss their “Day in the Life of an IRS Agent” program. The initiative immerses students in real-world forensic accounting and criminal investigation scenarios, offering a hands-on look at careers in fraud prevention and compliance. Cardona shares how interactive education, mentorship and networking are key to inspiring the next generation of anti-fraud professionals—and why promoting ethical standards early on is essential in shaping the future workforce.
Published in Podcasts

In this episode of Fraud Talk, ACFE Communications Director John Duffley sits down with Mason Wilder, CFE, ACFE Research Director, to break down the newly released In-House Fraud Investigation Teams: 2025 Benchmarking Report. Dive into a detailed discussion on how organizations are structuring their fraud teams—from the increasing number of investigators to the unique challenges they face across different company sizes. Learn about the role of in-house teams, the evolving skill sets required in today’s complex fraud landscape and the critical balance between case volume and team efficiency.
Published in Podcasts

Artificial intelligence (AI) is revolutionizing fraud prevention in the banking industry, enhancing detection and risk management. But with these advancements come new challenges—fraudsters using AI to exploit vulnerabilities, biases in algorithms and the need for regulatory adaptation. In this episode, ACFE Content Manager Rihonna Scoggins speaks with fraud expert Kennedy Meda about the impact of AI on banking fraud, the balance between automation and human oversight and how financial institutions can stay ahead of emerging threats.
Published in Podcasts

In this episode of Fraud Talk, John Warren, J.D., CFE, CEO of the ACFE, and Jennifer Liebman, CFE, Editor-in-Chief of Fraud Magazine, delve into some of 2024's most scandalous fraud cases. From Boeing's guilty plea tied to deadly aviation crashes to Vietnam's sentencing of a real estate tycoon to death for embezzlement, they explore the global implications of these high-profile frauds. Tune in to understand the evolving nature of fraud, including the role of AI and platforms like TikTok in modern schemes, and uncover critical lessons for prevention and compliance.
Published in Podcasts

Belinda Kitos, CFE, CICA and president of SCF Inc., was elected as treasurer of her homeowners association, but when she opened the books she discovered a $1.2 million fraud in her own backyard. In this month's episode of Fraud Talk, Kitos and Jason Zirkle, training director of the ACFE, explore their own experiences investigating HOA fraud and the red flags of these schemes.
Published in Podcasts

The National Heath Care Anti-Fraud Association (NHCAA) estimates conservatively that healthcare fraud costs the U.S. approximately $68 billion annually. Why is there so much fraud and abuse with insurance claims and why has this problem gone on so long? In this month's episode of Fraud Talk, Paul Kilby, Editor in Chief of Fraud Magazine, discusses the role of artificial intelligence (AI) in combatting healthcare fraud with Theja Birur, Chief Technology Officer and founder of 4L Data Intelligence.
Published in Podcasts
.png)
In this haunting episode of Fraud Talk, investigate the ghostly disappearance of Phases, Inc., a Tennessee nonprofit dedicated to helping women with substance abuse issues. Tune in with Michael Booher, CFE, CPA, from the Tennessee Comptroller of the Treasury and Rihonna Scoggins, ACFE Community Manager, to discover how this ghost story unfolds and the truths lurking in Phases, Inc.'s shadows.
Published in Podcasts

"We've been trying to reach you about your car's extended warranty" is an all-too-common robocall scam aiming to bilk victims out of their money. Alex Quilici, CEO of YouMail, discusses the intricacies of robocalls, what differentiates beneficial robocalls from scams and the regulations that both aid and obstruct the fight against these schemes with Jennifer Liebman, CFE, assistant editor of Fraud Magazine, in the latest episode of Fraud Talk.
Published in Podcasts

Tom Cronkright, the lead witness in the FBI's indictment of Black Axe, an international cybercrime syndicate based out of Nigeria, speaks with ACFE President John Gill, J.D., CFE, in this month's episode of Fraud Talk. As the co-founder of CertifID and CEO of a title agency, Tom has been at the forefront of helping the real estate industry address payments fraud and discusses his experience as a victim of fraud and the operations of the international fraud group he helped indict.
Published in Podcasts

In this month's episode of Fraud Talk, ACFE Chief Training Officer John Gill, CFE, meets with attorney David Fleck, Esq., who represents victims of business, real estate and investment fraud in lawsuits to recover their money, property and dignity. They discuss trends in real estate fraud including investment fraud, title theft and deed fraud, mortgage fraud and wire transfer fraud.
Published in Podcasts

In Episode 133 of Fraud Talk, Editor in Chief of Fraud Magazine Paul Kilby speaks with Kathryn Westmore, the Senior Research Fellow for the Center for Financial Crime and Security Studies at the Royal United Services Institute, a military and defense think tank in the U.K. Kathryn discusses the increase in fraud in the U.K., government initiatives and the balance between data sharing and data privacy.
Published in Podcasts

In Episode 132 of Fraud Talk, ACFE Research Specialist Sam May meets with Rob Sand, the Iowa State Auditor. Rob speaks about the Hot Lotto fraud scandal he prosecuted, totaling more than $25 million, as well as helping the state of Iowa improve their systems and processes to better investigate and audit potential frauds.
Published in Podcasts

In Episode 131 of Fraud Talk, Tyler Hatcher, Special Agent in Charge of the Los Angeles field office of the Internal Revenue Service's Criminal Investigation division, joins ACFE Communications Manager John Duffley. Tyler reflects on the IRS-CI division's growth during his 21 years, the process behind evaluating allegations and pursuing criminal cases, growing uses of cryptocurrencies, common tax fraud schemes, the impacts of the CARES Act and Inflation Reduction Act, and much more.
Published in Podcasts

In this episode, Jenny Radcliffe, aka "The People Hacker," discusses her expertise as an ethical social engineer, honing those skills at an early age on the streets of Liverpool, and unique challenges she has faced over the years. Joining ACFE Community Manager Rihonna Scoggins during Women's History Month, Jenny explains how being a woman in her field and gender biases she has observed played a significant role in understanding the "human element" behind social engineering. Her new book "People Hacker: Confessions of a Burglar for Hire" is available now in the U.K.
Published in Podcasts

In Episode 129 of Fraud Talk, Tony McClements, the Head of Investigations at Martin Kenney & Co., discusses his career trajectory through three decades in law enforcement to the private practice cases he oversees today. Joining ACFE Communications Manager John Duffley, Tony outlines the challenges between both types of investigations, the benefits to building a team of young, up-and-coming investigators, and emerging technologies and data reports that can be utilized for complex cases.
Published in Podcasts

In this episode, the ACFE's Chief Training Officer John Gill sat down with Charles Antonucci, the former president of The Park Avenue Bank, who was convicted in 2015 of trying to defraud the Troubled Asset Relief Program (TARP). Antonucci also pleaded guilty to other charges including self-dealing, bribery, embezzlement of bank funds, and a multi-million fraud scheme involving an insurance company.
*The ACFE does not compensate convicted fraudsters.
Published in Podcasts



Published in Podcasts










For the first time since the original report was published in 1996, the ACFE Report to the Nations on Occupational Fraud and Abuse has been translated into Arabic thanks to the efforts of the ACFE Saudi Arabia Chapter, with support from Saudi Aramco.
Published in Press Releases

The Association of Certified Fraud Examiner’s (ACFE) first-ever Law Enforcement Government Anti-Fraud Summit will be November 21 in Washington, D.C., at the Hyatt Regency Washington on Capitol Hill.
Published in Press Releases

According to the 2016 ACFE Report to the Nations on Occupational Fraud and Abuse, organizations across the globe lose an average of $150,000 each time they fall victim to fraud and an estimated 5% of their revenues annually.
Published in Press Releases

“I think this whole offshore financial structure that’s been allowed to grow like a canker … the whole thing’s got out of control,” said investigative journalist Clare Rewcastle Brown in an interview with the Association of Certified Fraud Examiners (ACFE).
Published in Press Releases

The Committee of Sponsoring Organizations of the Treadway Commission (COSO) announced today the release of the Fraud Risk Management Guide, a new research report that offers a blueprint for helping organizations to establish an overall fraud risk-management program.
Published in Press Releases

According to the Association of Certified Fraud Examiner’s (ACFE) latest report, Canadian fraudsters were more likely to receive no punishment from their employers than being asked to resign.
Published in Press Releases

Academy Award-Winning Actor Richard Dreyfuss, Judge Jed S. Rakoff, New York Times investigative journalist David Barboza and other experts will address more than 3,000 anti-fraud professionals gathering for the 27th Annual Association of Certified Fraud Examiners (ACFE) Global Fraud Conference in Las Vegas, June 12-17.
Published in Press Releases

“Waste, fraud and abuse” has become a pervasive soundbite in the 2016 U.S. presidential election, but just how much fraud is actually occurring in the government?
Published in Press Releases

When hundreds of anti-fraud professionals from Europe gather in Brussels on March 20-22 for the 2016 ACFE European Fraud Conference, president and founder of TRACE International, Alexandra Wrage, hopes that she can shed some light on corruption and compliance issues around the world, including those affecting football’s governing body.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE) have signed a Corporate Alliance agreement with Saudi Aramco which will allow selected Saudi Aramco employees to benefit through full ACFE membership, along with exclusive on-site training opportunities, discounted ACFE conferences and seminars, self-study courses, free quarterly webinars and access to the ACFE network of fraud examiner practitioners.
Published in Press Releases

With increased financial pressure causing fraud to rise an estimated 20% during the U.S. holiday shopping season, the Association of Certified Fraud Examiners (ACFE) reminds business owners and management to take a preventive stance to lower their risk.
Published in Press Releases

Two years after the world’s largest anti-fraud association held its Asia-Pacific Fraud Conference in Singapore for the first time, anti-fraud professionals are preparing to gather again in a country commonly considered a model for keeping fraud and corruption in check.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE) has announced a partnership with Airbus to provide ethics and compliance training and certification among its employees.
Published in Press Releases

For the second year in a row, James D. (Jim) Ratley, CFE, president and CEO of the Association of Certified Fraud Examiners (ACFE), has been selected by Accounting Today as “One of the Top 100 Most Influential People.” The annual list includes business leaders, government figures and luminaries who are “shaping the profession now and in the future.”
Published in Press Releases

Raiffeisen Bank International AG (RBI), a leading European universal banking group, has announced a partnership with the Association of Certified Fraud Examiners (ACFE) to increase anti-fraud knowledge and certification among its employees.
Published in Press Releases

Hundreds of professional fraud fighters from around Canada will gather Sept. 8-11, 2013 in Montreal to share best practices in fraud prevention and detection at the 2013 Association of Certified Fraud Examiner’s (ACFE) Canadian Fraud Conference. Data analytics, open-source intelligence and new laws and regulations are among the timely fraud training issues on the agenda.
Published in Press Releases

Internal Auditor magazine has announced that Dr. Joseph T. Wells, CFE, CPA, founder and chairman of the Association of Certified Fraud Examiners (ACFE), has been named 2013 Outstanding Contributor for his April 2012 article “Inside the Fraudster's Mind.”
Published in Press Releases

More than 2,600 anti-fraud professionals have gathered at the ARIA Resort & Casino here for the 24th Annual ACFE Global Fraud Conference, setting record attendance for an event that is the largest of its kind in the world.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE) announced today its selection of Allan Dodds Frank as the recipient of its 2013 Guardian Award, bestowed annually on a journalist whose “determination, perseverance, and commitment to the truth have contributed significantly to the fight against fraud.”
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE), the world’s largest anti-fraud organization and premier provider of anti-fraud training and education, has announced that Richard G. Brody, Ph.D., CFE, CPA, and Bruce G. Dubinsky, M.S., CFE, CPA, have been elected to the ACFE Board of Regents.
Published in Press Releases

Preet Bharara, U.S. Attorney for the Southern District of New York, ex-Enron CFO Andrew Fastow and award-winning actor Stacy Keach head the list of keynote speakers for the 24th Annual Association of Certified Fraud Examiners’ (ACFE) Global Fraud Conference, June 23-28, 2013 at ARIA Resort & Casino in Las Vegas.
Published in Press Releases

In conjunction with their annual International Fraud Awareness Week, November 12-18, 2017, the Association of Certified Fraud Examiners (ACFE) has offered up two videos explaining why people commit fraud, and what common traits fraudsters possess.
Published in Press Releases

In the Association of Certified Fraud Examiner’s (ACFE) In-House Fraud Investigation Teams: 2017 Benchmarking Report, fraud investigation teams said the top skills they are currently seeking or expecting to add are digital forensic skills and cybersecurity skills.
Published in Press Releases

The largest gathering of anti-fraud professionals from the Asia-Pacific region will take place in Hong Kong this autumn at the 2017 ACFE Fraud Conference Asia-Pacific. The conference will be held 17-19 September at the Kowloon Shangri-La Hong Kong, and feature sessions and speeches from leaders in the compliance and cybercrime industry.
Published in Press Releases

Dr. Sam Foote, the whistleblower who brought the U.S. Veterans Affairs (VA) scandal to light in 2014, will be awarded the ACFE Sentinel Award at the 28th Annual ACFE Global Fraud Conference in Nashville, June 18-23.
Published in Press Releases

Former Director of FinCEN Jennifer Shasky Calvery, investigative journalist Andrew Jennings, former FBI agent Eric O’Neill and other experts will address more than 3,000 anti-fraud professionals gathering for the 28th Annual Association of Certified Fraud Examiners (ACFE) Global Fraud Conference in Nashville, June 18-23.
Published in Press Releases

It's unfortunately common this time of year for individuals to file their taxes only to find out that someone has already claimed their return. This type of identity theft can be upsetting, but it may be even more upsetting if they found out their identity was stolen not through a fault of their own, but due to their employer falling victim to a scam.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE), the world’s largest anti-fraud organization and premier provider of anti-fraud training and education, has announced that Leah D. Lane, CFE, has been named chairman of the 2017-2018 ACFE Board of Regents.
Published in Press Releases

Famous for her work investigating and exposing the large and complex 1MDB scandal, Clare Rewcastle Brown believes that European banks should be considered partially culpable for the Malaysian-based fraud. Scheduled to address hundreds of anti-fraud professionals in London, 19-21 March, for the 2017 ACFE Fraud Conference Europe, Brown says that international bodies around the world could do more to investigate and prosecute fraud.
Published in Press Releases

With the widespread distribution of COVID vaccines now promising hope for a “return to normal,” business leaders need to understand that some of the changes in the business landscape are not temporary — and these changes will have a big impact on their organizations’ fraud risk.
Published in Press Releases

Cybersecurity expert Robert Herjavec and former U.S. Attorney of the Southern District of New York Preet Bharara will address 5,000 anti-fraud professionals at the virtual 32nd Annual ACFE Global Fraud Conference on June 21-23.
Published in Press Releases

According to the ACFE’s latest report, the Fraud Awareness Training Benchmarking Report, 14% of respondents said board members receive no fraud training.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE), in collaboration with the Capital Market Authority of Saudi Arabia, will host the 2021 ACFE Fraud Conference Middle East in a virtual format, 7-8 April.
Published in Press Releases

Award-winning journalist, broadcaster and author Misha Glenny says that ransomware should be the top concern of European organizations — and that they’re not prepared.
Published in Press Releases

Paul Kilby, an editor and journalist with more than two decades of experience, will replace Dick Carozza, CFE, who's retiring as the editor-in-chief of the ACFE’s flagship publication Fraud Magazine.
Published in Press Releases

James D. Ratley, CFE, president of the Association of Certified Fraud Examiners (ACFE) has been selected as one of Security magazine's Most Influential Security Executives for 2010.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE) will host its 21st Annual Fraud Conference & Exhibition, July 25-30, 2010 at Gaylord National Hotel in Washington, D.C., headlined by keynote speakers including Special Inspector General Neil M. Barofsky, overseer of the Troubled Asset Relief Program (TARP), and court-appointed Madoff trustee Irving Picard.
Published in Press Releases

Organizations around the world lose an estimated 5% of their annual revenues to fraud, according to a survey of Certified Fraud Examiners (CFEs) who investigated cases between January 2008 and December 2009.
Published in Press Releases

With seasonal hiring in the U.S. expected to be at its highest level in years, fraud experts warn that companies that loosen their usual processes in order to add staff quickly put themselves at increased risk to fraud.
Published in Press Releases

Brian Krebs, the investigative reporter behind KrebsOnSecurity who exposed massive data breaches, cybercriminals and the service providers who catered to them, has been selected to receive the Association of Certified Fraud Examiners (ACFE) Guardian Award.
Published in Press Releases

For the third year in a row, James D. (Jim) Ratley, CFE, president and CEO of the Association of Certified Fraud Examiners (ACFE), has been selected by Accounting Today as “One of the Top 100 Most Influential People.”
Published in Press Releases

Woodford will tell his story and reflect on the current state of corruption and fraud in business in his keynote address at the 2014 ACFE Asia-Pacific Fraud Conference, November 16-18, 2014 in Hong Kong.
Published in Press Releases

Hundreds of professional fraud fighters from around Canada will gather next month at Toronto Marriott Downtown Eaton Centre to share best practices in fraud prevention and detection at the 2014 ACFE Canadian Fraud Conference, September 7-10, 2014.
Published in Press Releases

FBI Director Louis J. Freeh, Transparency International founder Peter Eigen and other experts will address nearly 3,000 anti-fraud professionals gathering here this week for the 25th Annual Association of Certified Fraud Examiners (ACFE) Global Fraud Conference.
Published in Press Releases

Organizations around the world lose an estimated 5% of their annual revenues to occupational fraud, according to a survey of Certified Fraud Examiners (CFEs) who investigated cases between January 2012 and December 2013.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE), the world’s largest anti-fraud organization and premier provider of anti-fraud training and education, has announced that Bruce G. Dubinsky, M.S., CFE, CPA, has been named chairman of the ACFE Board of Regents.
Published in Press Releases

As technology continues to advance, criminals come up with ways to exploit it just as quickly.
Published in Press Releases

The 2018 ACFE Report to the Nations on Occupational Fraud and Abuse showed that the leading detection method for fraud was through tips.
Published in Press Releases

Academy Award® Winner Bryan Fogel, the director and writer of ICARUS, Clare Rewcastle Brown, the investigative journalist who helped bring the international 1MDB scandal to light and other experts will address more than 3,000 anti-fraud professionals gathering this week for the 29th Annual ACFE Global Fraud Conference.
Published in Press Releases

Over the past decade, fewer and fewer fraud cases were referred to law enforcement.
Published in Press Releases

Dr. Jessica Barker addressed hundreds of anti-fraud professionals today at the 2018 ACFE Fraud Conference Europe and told them that a new weak point in organizations’ cybersecurity might stem from an unlikely source — General Data Protection Regulation (GDPR) compliance.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE) and the Abu Dhabi Accountability Authority (ADAA) have joined hands to assert ADAA’s Knowledge Center as an ACFE Authorized Knowledge Center, marking a major milestone in ADAA’s efforts to provide professional advanced training and support to Abu Dhabi government entities and employees.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE) announced today that Bruce Dorris, J.D., CFE, CPA, has been named the incoming president and CEO.
Published in Press Releases

The partnership will elevate competency for fraud investigators and auditors.
Published in Press Releases

Following two years of virtual-only events, the 2022 ACFE Fraud Conference Canada brings anti-fraud professionals from around the region back together for three days of educational sessions and networking.
Published in Press Releases

This year’s virtual event opens doors for professionals working in law enforcement, government entities and non-governmental organizations (NGOs) to learn specialized knowledge and gather valuable techniques to take on the latest anti-fraud challenges facing the profession.
Published in Press Releases

The 2022 Compensation Guide for Anti-Fraud Professionals highlights salary trends across the global anti-fraud industry and provides benchmarks in areas such as compensation and job satisfaction to help anti-fraud professionals inform their career decisions.
Published in Press Releases

The 2022 ACFE Fraud Conference Asia-Pacific returns in-person for the first time in three years, with a number of global anti-fraud professionals scheduled to deliver keynote sessions in Singapore.
Published in Press Releases

Managing Fraud Risks in an Evolving ESG Environment, a guide to help organizations investing in ESG initiatives avoid fraud, was released in conjunction with the start of the 33rd Annual ACFE Global Fraud Conference, held in Nashville, TN and virtually.
Published in Press Releases

SEC Director of Enforcement Gurbir Grewal, best-selling author Michael Lewis and others will address attendees at the 33rd Annual ACFE Global Fraud Conference, held in person for the first time in three years.
Published in Press Releases

Between 2012 and 2022, fraud cases were caught faster, causing smaller losses according to data in Occupational Fraud 2022: A Report to the Nations. The report, which looked at fraud trends over the past 10 years, also showed that criminal prosecutions of fraud cases were down, while civil cases were up.
Published in Press Releases

This annual event brings anti-fraud education and awareness to businesses and consumers worldwide.
Published in Press Releases

Keynote speakers for this year's event will include podcaster/tech expert Amber Mac and former Speaker of British Columbia's Legislative Assembly, Dr. Darryl Plecas.
Published in Press Releases

The three-day hybrid event September 20-22 will bring together anti-fraud professionals in the Asia-Pacific region to discuss emerging fraud trends and technology.
Published in Press Releases

The self-paced, online training program will be tailored to banking, financial services institutions and partners.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE) has appointed John Gill, J.D., CFE, as President of the ACFE; John Warren, J.D. CFE, will take over as Chief Executive Officer of the world’s largest anti-fraud organization.
Published in Press Releases

Half of organizations plan to use more artificial intelligence in their due diligence.
Published in Press Releases

Published in Press Releases


The two-day event will be held in Dubai on 8-9 May, 2023, returning for its eighth annual conference in the region.
Published in Press Releases

The flagship event of the Association of Certified Fraud Examiners (ACFE) will feature U.S. government leaders, industry-leading experts and a notorious fraudster all leading discussions on emerging trends, techniques and perspectives at the world’s largest anti-fraud conference.
Published in Press Releases

The online conference, which will be held March 27-29, will also feature more than a dozen educational sessions led by experts across anti-fraud, auditing, cybersecurity and technology industries.
Published in Press Releases

Rachel Wilson, Director of Cybersecurity at Morgan Stanley, and Kelly Donovan, Whistleblower and Advocate, will serve as keynote speakers for the third annual event.
Published in Press Releases

The founder and former president of the World Anti-Doping Agency (WADA), Dick Pound, has spent decades battling corruption and bribery within the International Olympic Committee.
Published in Press Releases

Carson Block, the founder and chief investment officer of Muddy Waters Capital LLC, made headlines at the beginning of 2020 when he posted a report to Twitter accusing Chinese coffee company Luckin Coffee Inc. of fraudulently inflating sales.
Published in Press Releases

Danske Bank whistleblower Howard Wilkinson, security expert Jules Kroll, WIRED magazine Editor-in-Chief Nicholas Thompson and other experts will address thousands of anti-fraud professionals, June 22-24, at the virtual 31st Annual ACFE Global Fraud Conference.
Published in Press Releases

According to a new report from the Association of Certified Fraud Examiners (ACFE), a single case of occupational fraud costs the victim organization an average of more than $1.5 million, and Certified Fraud Examiners (CFEs) estimate that organizations lose 5% of their revenues each year to fraud.
Published in Press Releases

If you have lived long enough, you have been affected by some unforeseen calamity.
Published in Press Releases

Under the patronage of His Highness Sheikh Maktoum bin Mohammed bin Rashid Al Maktoum, Deputy Ruler of Dubai, the General Directorate of Residency and Foreigners Affairs (GDRFA-Dubai) along with the Association of Certified Fraud Examiners (ACFE) will host the 2020 ACFE Fraud Conference Middle East in Dubai 23-25 February.
Published in Press Releases

A measure approved last week by the House Financial Services Committee to change Sarbanes-Oxley audit rules would lead to a higher incidence of fraud and an increase in the amount of fraud losses, according to the Association of Certified Fraud Examiners (ACFE).
Published in Press Releases

The Criminal Investigation Division of the Internal Revenue Service (IRS-CI) recently joined the ACFE Law Enforcement Partnership by officially recognizing the Certified Fraud Examiner (CFE) credential for hiring and promotional purposes.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE) presented its annual Cliff Robertson Sentinel Award Wednesday to Pamela Davis, CEO of Edward Hospital in near Chicago, at the 20th Annual ACFE Fraud Conference & Exhibition in Las Vegas.
Published in Press Releases

The ACFE is hosting its 20th Annual Fraud Conference & Exhibition in Las Vegas, where more than 2,000 attendees will hear keynote speakers including Madoff whistleblower Harry Markopolos, CFE, CFA and second U.S. Secretary of Homeland Security Michael Chertoff at the largest gathering of anti-fraud professionals in the world.
Published in Press Releases

Well-meaning victims, courts, the media and the public actually believe that Bernard Madoff, sentenced recently to a record 150 years in prison, stole 65 billion dollars. Not hardly — not even close.
Published in Press Releases

Intense financial pressure during the economic crisis has led to an increase of fraud, according to a survey of fraud experts conducted by the Association of Certified Fraud Examiners (ACFE).
Published in Press Releases

The inaugural event, under the patronage of the UAE Ministry of Economy, will gather insightful speakers to guide anti-fraud professionals into a new era of audit, fraud prevention and information technology.
Published in Press Releases

Fortune 500 companies, government agencies, small businesses and more share a collective mission during the week to spread anti-fraud education, tools and resources to their staff and communities.
Published in Press Releases

The ACFE's annual one-day event brings together anti-fraud professionals from government and law enforcement agencies.
Published in Press Releases


The ACFE's 2024 Compensation Guide for Anti-Fraud Professionals, which highlights salary and benefit differences among ACFE members, also shows continued gender diversification in the profession.
Published in Press Releases

Published in Press Releases

This annual conference brings together anti-fraud professionals from across the Asia-Pacific region for three days of discussion on the latest trends, technologies and solutions for detecting and preventing fraud.
Published in Press Releases

The world's largest gathering of anti-fraud professionals drew more than 5,800 attendees from 88 countries to the ARIA Resort and Casino in Las Vegas and online for its 2024 event.
Published in Press Releases

Whistleblowers, federal fraud fighters, an NFL legend and more will take the stage as keynote speakers at the 35th Annual ACFE Global Fraud Conference.
Published in Press Releases

Median losses of the fraud cases analyzed in this year’s report increased 24% compared to the 2022 Report to the Nations. The COVID-19 pandemic might be partly to blame.
Published in Press Releases

Published in Press Releases

The fourth annual event explores the challenges unique to women in the anti-fraud industry through idea sharing, exchanging resources and networking with industry leaders.
Published in Press Releases

The UAE Accountability Authority (UAEAA) partners with the world’s largest organization of anti-fraud professionals to host the premier educational event for fraud fighters in the Middle East.
Published in Press Releases

Global survey of anti-fraud professionals by the ACFE and SAS reveals incredible GenAI enthusiasm – but past benchmarking studies suggest a more challenging reality.
Published in Press Releases

Published in Press Releases

The median fraud loss for organizations in Canada is about 127,000 CAD, according to a fraud survey conducted by the Association of Certified Fraud Examiners (ACFE) last year.
Published in Press Releases

Anti-fraud professionals will gather in Singapore for expert training and professional networking at the 2011 ACFE Asia-Pacific Fraud Conference, 23-25 October at Marina Bay Sands hotel and resort.
Published in Press Releases

U.S. Attorney General Lanny Breuer was among the distinguished keynote speakers who recognized the fraud-fighting efforts of more than 2,300 professionals in attendance at the 22nd Annual ACFE Fraud Conference and Exhibition.
Published in Press Releases

More than 2,300 professional fraud sleuths descended upon the San Diego Convention Center Sunday for the week-long 22nd Annual ACFE Fraud Conference & Exhibition.
Published in Press Releases

The impact of fraud on business in Europe will be on the minds of nearly 150 anti-fraud professionals when they meet at the 2011 ACFE European Fraud Conference next week, 17-19 April 2011, in Brussels.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE), the world's largest anti-fraud organization and premier provider of anti-fraud training and education, has announced that Johnnie R. Bejarano, DBA, CFE, CPA, and E. Wendell Hopewell, MBA, CFE, CPA, have been elected to the ACFE Board of Regents.
Published in Press Releases

More than 300 anti-fraud professionals will gather at Atlantis, the Palm in Dubai on February 14-15, 2016 to discuss emerging issues in fraud prevention and listen to leaders in the anti-fraud field.
Published in Press Releases

More than 250 anti-fraud professionals from around the Asia-Pacific region will gather for the 2015 Association of Certified Fraud Examiners (ACFE) Asia-Pacific Fraud Conference at Marina Bay Sands in Singapore, November 4-6, to listen to leaders in the anti-fraud field, along with an unlikely special guest: a convicted fraudster.
Published in Press Releases

Cybersecurity expert Brian Krebs, Leslie R. Caldwell, U.S. Department of Justice assistant attorney general, Criminal Division, and other experts will address more than 3,000 anti-fraud professionals gathering here this week for the 26th Annual Association of Certified Fraud Examiners (ACFE) Global Fraud Conference.
Published in Press Releases

K & N Kenanga Holdings Berhad (Kenanga Group), the holding company of the largest independent investment bank in Malaysia*, Kenanga Investment Bank Berhad (KIBB), is the first Southeast Asian organisation to partner with the Association of Certified Fraud Examiners (ACFE), the world’s largest anti-fraud organisation.
Published in Press Releases

Your social security number could be the ticket for a fraudster seeking to claim a false tax refund or worse, according to the Internal Revenue Service (IRS). A fraud expert offers some tips for preventing such crime – or at least catching it early.
Published in Press Releases

The Financial Audit Department (FAD) – Dubai Government announced Thursday a partnership with the Association of Certified Fraud Examiners (ACFE), the world’s largest anti-fraud organization, to provide expert fraud training and certification for FAD employees.
Published in Press Releases

The annual flagship event for the Association of Certified Fraud Examiners (ACFE) was held in Nashville, Tennessee, and virtually.
Published in Press Releases

Speakers at the 36th Annual ACFE Global Fraud Conference will present trending fraud topics including government fraud, AI, cybersecurity and more.
Published in Press Releases

Empowering Professionals to Strengthen Fraud Risk Management
Published in Press Releases

The ACFE and ACCA to focus on research and learning in three-year MOU.
Published in Press Releases

The three-day hybrid event features multiple tracks of educational sessions highlighting the latest trends, tools and techniques for fraud prevention, deterrence and investigation.
Published in Press Releases

The fifth annual event will bring together anti-fraud professionals for a day of learning and networking.
Published in Press Releases

The In-House Fraud Investigation Teams: 2025 Benchmarking Report examines common trends in caseloads, credentials, recovery of fraud losses and more within companies' fraud investigation teams.
Published in Press Releases

Documented allegations of fraud against Madoff Investment Securities, LLC were presented to the Securities Exchange Commission as early as 1999 by Harry Markopolos, a Certified Fraud Examiner.
Published in Press Releases

The Office of the Inspector General (OIG) for the National Reconnaissance Office (NRO) recently announced its official recognition of the Certified Fraud Examiner (CFE) credential for hiring and promotional purposes.
Published in Press Releases

U.S. organizations lose an estimated seven percent of their annual revenues to fraud, according to a survey of Certified Fraud Examiners who investigated cases between January 2006 and February 2008.
Published in Press Releases

The Association of Certified Fraud Examiners (ACFE) will be hosting its 19th Annual Fraud Conference & Exhibition on July 13-18, 2008 in Boston, featuring an opening keynote address by Senator George Mitchell.
Published in Press Releases

The Office of the Inspector General (OIG) for the U.S. Department of the Interior (DOI) recently recognized the Certified Fraud Examiner (CFE) credential for hiring and promotional purposes.
Published in Press Releases

A case involving Texas Supreme Court Justice David Medina, a Harris County Grand Jury, and the Harris County District Attorney is raising a debate as to whether politics or a lack of evidence played a role in the dismissal of indictments.
Published in Press Releases

Increased financial pressure is the leading reason fraud takes an estimated 20% uptick during the U.S. holiday season, according to a new survey of Certified Fraud Examiners (CFEs). A majority of these experts believe employee embezzlement is the type of fraud most likely to increase during this period.
Published in Press Releases

Red flags of fraud, detecting deception, conducting online investigations and other trending topics will be top discussion items when anti-fraud professionals from across Europe convene on 17-19 March 2013 at the ACFE European Fraud Conference in Prague.
Published in Press Releases

Nearly 250 professional fraud fighters from around Canada arrived at the Ottawa Marriott Sunday to share best practices in fraud prevention and detection at the 2012 ACFE Canadian Fraud Conference. The largest anti-fraud event in the country kicked off with a pre-conference session on conducting internal investigations, and the main conference continues today through Wednesday.
Published in Press Releases

Professional fraud fighters from around the Asia-Pacific region will gather for training and to share best practices in fraud prevention and detection at the 2012 ACFE Asia-Pacific Fraud Conference, 4-6 Nov. 2012 in Hong Kong.
Published in Press Releases

James D. (Jim) Ratley, CFE, president and CEO of the Association of Certified Fraud Examiners (ACFE), has been selected by Accounting Today as One of the Top 100 Most Influential People of 2012. The exclusive list includes President Barack Obama, Mitt Romney, SEC Chair Mary Shapiro and other dignitaries and business leaders.
Published in Press Releases

More than 2,300 professional fraud sleuths will arrive here Sunday for the 23rd Annual ACFE Fraud Conference & Exhibition, June 17-22, 2012. The world’s largest gathering of anti-fraud professionals will take place at the Gaylord Palms Resort and Convention Center.
Published in Press Releases

Organizations around the world lose an estimated 5% of their annual revenues to fraud, according to a survey of Certified Fraud Examiners (CFEs) who investigated cases between January 2010 and December 2011. Applied to the estimated 2011 Gross World Product, this figure translates to a potential total fraud loss of more than $3.5 trillion.
Published in Press Releases

For “choosing truth over self” in exposing the Olympus accounting scandal, Michael Woodford has been selected to receive the Association of Certified Fraud Examiners’ (ACFE) Cliff Robertson Sentinel Award for 2012.
Published in Press Releases

Anti-fraud professionals from across Europe will convene for training and discussion of the hottest fraud topics in the region when they meet on 25-27 March at the 2012 ACFE European Fraud Conference in London.
Published in Press Releases

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives
.png)


Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives




Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives



While DeFi might hold a lot of promise for proponents of cryptocurrency and whatever Web 3.0 becomes, these large-scale losses show that the platforms and apps feature several serious, exploitable fraud risks.
Published in Fraud Examiner Archives

Similar to the overconfidence bias, illusory superiority is described as when you overestimate your own abilities when compared to others. Confidence is an important trait for fraud examiners, but too much of it can lead to mistakes in investigations — and illusory superiority can contribute to overconfidence in imperceptible ways.
Published in Fraud Examiner Archives

In nearly every state, guardians are considered fiduciaries. As such, they have a duty to act in their clients’ best financial interests. Sadly, that’s not always the case.
Published in Fraud Examiner Archives

While STRs may be a lucrative opportunity for many, they are not without fraudsters targeting them as well.
Published in Fraud Examiner Archives

Consumers should be wary of any QR code provided by an unknown source; such codes should be treated like unknown hyperlinks.
Published in Fraud Examiner Archives

Corporate leaders are faced with a moral dilemma, weighing the financial interests of their stakeholders against the public interest in unifying against the violent invasion of a sovereign nation. Further complicating the situation, some corporate leaders must also determine whether to cut ties with their own employees based in Russia — employees with families to feed and support.
Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

On July 15, a South Korean treasure hunting company called the Shinil Group claimed it found the wreck of a Russian warship, the Dmitrii Donskoi. The ship sank east of the Korean Peninsula more than 100 years prior during a 1905 battle with the Japanese while carrying a cargo of 200 tons of gold bullion, according to Shinil’s claim.
Published in Fraud Examiner Archives

When large corporations, agencies or insurance companies establish relief funds, fraudsters rationalize their thefts because they believe that these large entities can absorb the costs. Since huge settlements involve numerous transactions and claims, fraudsters often hope that their actions will be lost in an enormous sea of data. The allure of a big payout can be a draw for fraudsters. Luckily, there is an answer: big data analytics.
Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

David Rodriguez, CFE, CPA, CIA combined multiple study techniques to pass the 90-Day CFE Exam Challenge. Here he outlines how he succeeded using the challenge group, different study methods and support from others in the ACFE Community.
Published in ACFE Insights Blog

Reuters recently reported that more than half a dozen British banks were in advanced talks with law enforcement and government agencies over plans to systematically share intelligence on major financial crimes such as money laundering and terrorism financing.
Published in ACFE Insights Blog

Today brings both sadness and joy as the Association of Certified Fraud Examiners bids farewell to outgoing President and CEO Bruce Dorris, who leaves the ACFE to take some time for himself and his family before beginning the next chapter of his career.
Published in ACFE Insights Blog

Artificial intelligence (AI) itself is not inherently fraudulent. AI is a field of computer science that focuses on the development of computer systems that can perform tasks that typically require human-like intelligence, such as learning, problem solving and decision making.
Published in ACFE Insights Blog

Like any tool, AI can be wielded for malicious purposes. Fraudsters are increasingly leveraging AI to enhance the efficiency and sophistication of their scams.
Published in ACFE Insights Blog

According to the Antwerp World Diamond Center (AWDC), about 1,700 companies and 4,500 traders concentrated in an area of about one square kilometer trade 84% of all rough diamonds worldwide.
Published in ACFE Insights Blog

The Ritchie-Jennings Memorial Scholarship provides an opportunity for students to advance their education and anti-fraud career paths. Additionally, it supports their anti-fraud interests by providing a full year of ACFE membership. Award amounts are $10,000, $7,500, $5,000 and $2,000 and are paid directly to the recipient’s university or college.
Published in ACFE Insights Blog

Multi-level marketing (MLM) companies have been around for decades, but they have recently gained popularity in the health and wellness industry. You’ve seen these companies promoting on social media, like the ubiquitous “Hey hun!” in your Facebook Messenger, or perhaps even approaching you in public squares and asking to join their “exclusive” club, buy their product or join their workout group.
Published in ACFE Insights Blog

This blog serves as part two in a three-part series on Benford’s Law.
Published in ACFE Insights Blog

Conventional wisdom suggests that each digit has an equal chance of being the first digit, but Benford's law shows that lower numerals always have a greater chance at being the leading digit compared to higher numerals.
Published in ACFE Insights Blog

When investigating fraudulent activity as it relates to letters of credit, red flags are important to explore during the preliminary investigation to identify money laundering.
Published in ACFE Insights Blog

Medicare fraud poses a significant threat to the integrity and sustainability of the Medicare program. A recent and troubling Medicare fraud case in Florida involved nurse practitioner Elizabeth Hernandez, who was convicted of fraudulently billing over $200 million for unnecessary orthotic braces and genetic testing.
Published in ACFE Insights Blog

The name Frank Abagnale Jr. is synonymous with check fraud and counterfeiting. His story, which was popularized in the 2002 film "Catch Me If You Can," starred Leonardo DiCaprio as the master imposter himself. Though times have changed nearly 60 years later, Abagnale's schemes serve as a warning to banks and businesses to be on high alert for check fraud.
Published in ACFE Insights Blog

A new phishing scam preying on Best Buy customers is making the rounds. The fraudulent email claims to be from Best Buy's tech support team Geek Squad and tricks users into giving away personal information. Do not take the bait — this is what you need to know to avoid becoming a victim.
Published in ACFE Insights Blog
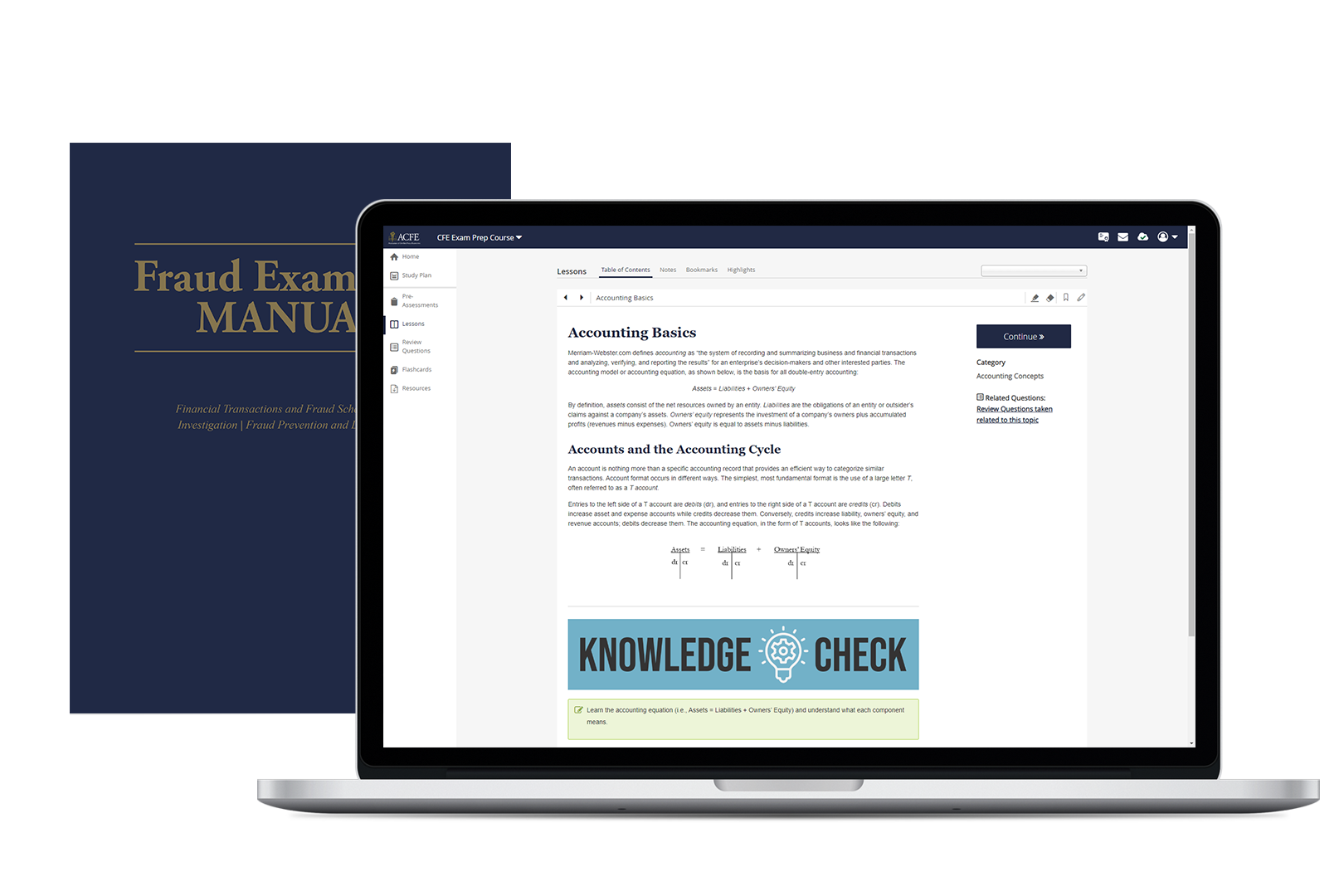
This new update to the CFE Exam Prep Course makes studying for your CFE Exam an easier process with integrated lessons and Knowledge Checks to ensure you are gaining the most from your study time.
Published in ACFE Insights Blog

In the ever-evolving landscape of fraud, staying informed about emerging trends is not just a choice — it is a necessity. As professionals in the field of fraud prevention, we understand that knowledge is our most potent weapon against the ever-adaptive tactics of fraudsters.
Published in ACFE Insights Blog

Engaging in clickbait quizzes could lead to providing hackers with enough information to bypass common security protocols on your personal accounts.
Published in ACFE Insights Blog

Fraud is a pervasive issue that affects businesses, organizations and individuals across various industries. Often, an organization is surprised to find itself a victim of fraud, especially when the perpetrator is a trusted employee. According to the Association of Certified Fraud Examiners Occupational Fraud 2022: A Report to the Nations, organizations lose approximately five percent of revenue to fraud each year with the average loss per case totaling more than $1.78 million.
Published in ACFE Insights Blog

Anna Sorokin, the so-called “fake German heiress” (perhaps better known by her alias Anna Delvey), came dangerously close to duping a hedge fund out of $25 million. According to The New York Times, she intended to defraud the financial institution by creating fake bank statements in Adobe Photoshop, a task that she said took “surprisingly little time.”
Published in ACFE Insights Blog

Federal law does not explicitly criminalize falsifying business records, but the act is criminalized under several federal regulations.
Published in ACFE Insights Blog

According to the Wiley Online Library, “Financial literacy is the ability to use knowledge and skills to manage financial resources effectively for a lifetime of financial well-being." Sounds pretty useful, right? But how do we learn financial literacy? And when should we start?
Published in ACFE Insights Blog

Despite strict regulations in India, drug diversion to the normal market remains a persistent problem, compromising patient safety and industry credibility.
Published in ACFE Insights Blog

Indigenous peoples around the world face marginalization and exploitation, leading to increased vulnerability. This puts them at a particular risk for fraud, as opportunistic fraudsters take advantage of systemic inequalities. Fraud against indigenous communities is especially harmful due to the unique challenges these groups face.
Published in ACFE Insights Blog

While NFTs offer numerous benefits, such as increased security and unique ownership, they also present new fraud risks. Understanding these risks and how to mitigate them is essential for organizations that are considering investing in NFTs.
Published in ACFE Insights Blog

Mason Wilder, the Research Manager at the Association of Certified Fraud Examiners (ACFE), sat down with Steve Dawson, CFE, CPA, and James Rumph, CFE, CIA, CPA, for a virtual webinar hosted by the ACFE and The Institute of Internal Auditors (The IIA).
Published in ACFE Insights Blog

In this episode of Fraud Talk, the ACFE's Chief Training Officer John Gill sat down with Charles Antonucci, the former president of The Park Avenue Bank, who was convicted in 2015 of trying to defraud the Troubled Asset Relief Program (TARP). Antonucci also pleaded guilty to other charges including self-dealing, bribery, embezzlement of bank funds, and a multi-million fraud scheme involving an insurance company. The ACFE does not compensate convicted fraudsters.
Published in ACFE Insights Blog

In this episode, Jenny Radcliffe, aka "The People Hacker," discusses her expertise as an ethical social engineer, honing those skills at an early age on the streets of Liverpool, and unique challenges she has faced over the years. Joining ACFE Community Manager Rihonna Scoggins during Women's History Month, Jenny explains how being a woman in her field and gender biases she has observed played a significant role in understanding the "human element" behind social engineering
Published in ACFE Insights Blog

With addiction being the most severe form of substance use disorder (SUD), symptoms can range from moderate to severe. In 2021, drug abuse was added to the list of high-risk situations by the Government Accountability Office (GAO). GAO high-risk list are areas susceptible to increased fraud, waste and abuse.
Published in ACFE Insights Blog

A new estate fraud case is center-stage in South Carolina’s courts. The Palmetto state has been a hotbed of probate, trust and conservator fraud cases dating back more than half a decade.
Published in ACFE Insights Blog

With suspect property fraud schemes, many vandalism insurance claims may appear innocuous at first glance. However, every claims adjuster must be prepared to identify, handle, and most importantly, defeat the elements of fraud that may be present within these types of losses.
Published in ACFE Insights Blog

White-collar crime, an insidious and complex category of offenses, extends far beyond the conventional image of criminal activity. Understanding white-collar crime is crucial for individuals and finance, law and security professionals in our interconnected world.
Published in ACFE Insights Blog

The head of Peru's judiciary, Javier Arévalo Vela, recently publicly highlighted Peru's success in recovering the proceeds of corruption and related financial crimes through its non-conviction based forfeiture law, Extinción de Dominio.
Published in ACFE Insights Blog

As the modern fascination with true crime escalates, perhaps no documentarian today presents the stories of our past with more profundity than Joe Berlinger. The director’s next endeavor figures to hit home for not just millions of Americans but anti-fraud professionals around the world, too.
Published in ACFE Insights Blog

Armed with an innate passion for justice and a keen understanding of the criminal mind, Allison Benkert, CFE, has carved a remarkable career path dedicated to unraveling fraud, seeking truth and ensuring accountability.
Published in ACFE Insights Blog

Frank Dara, CFE worked his way up from a Loss Prevention in-store Detective to becoming the North America Investigations Manager for Nike after years of fraud fighting. This is his story in his own words.
Published in ACFE Insights Blog

Aristotelis Konstantinos Koufos and Francesca Gabella, CFE, a dynamic duo united by their shared passion for fraud prevention and audit, take us on an insightful journey through their mentor-mentee relationship and their experiences in the ACFE Mentoring Program.
Published in ACFE Insights Blog

This exclusive resource marks a consolidation of our three existing newsletters into a unified, comprehensive source of knowledge and insights aimed at empowering you in the fight against fraud.
Published in ACFE Insights Blog

If you have the CFE Exam Prep Course, the Prep Toolkit or are planning to get either of the two, we invite you to sign up for the 90-Day CFE Exam Challenge and earn your Certified Fraud Examiner (CFE) credential.
Published in ACFE Insights Blog

Often linked to organized crime, white-collar crimes pose a persistent challenge today. These are usually nonviolent crimes like identity theft, mortgage fraud, computer crimes and tax evasion. To bring the culprits to justice, it's important to prosecute them rigorously.
Published in ACFE Insights Blog

Tax season can be a stressful time for many people, and it's important to be vigilant in order to protect yourself from tax preparer fraud. By following these tips, you can help protect yourself from tax preparer fraud and ensure that your tax return is accurate and handled properly. If you suspect that you've been a victim of tax preparer fraud, contact the IRS immediately.
Published in ACFE Insights Blog

To counter fraud's growing threat, information sharing mechanisms related to fraud detection and prevention have advanced significantly. Notably, an increasing number of fraudulent information-sharing initiatives are now adopting a public-private partnership approach, involving cooperation between government agencies, law enforcement and private sector entities.
Published in ACFE Insights Blog

Meet Hasmik Meloyan, one of the latest recipients of the ACFE's Ritchie-Jennings Memorial Scholarship. Hasmik's journey is a testament to her relentless pursuit of academic and professional growth, all aimed at making a significant difference in the anti-fraud arena.
Published in ACFE Insights Blog

Meet Jordan Newman, a driven individual who received the prestigious Ritchie-Jennings Memorial Scholarship for excelling in his professional and academic pursuits.
Published in ACFE Insights Blog

Co-published by the Committee of Sponsoring Organizations of the Treadway Commission (COSO) and the Association of Certified Fraud Examiners (ACFE), the Fraud Risk Management Guide provides direction for creating a comprehensive program to manage fraud risks within an organization.
Published in ACFE Insights Blog

Today, Pride Month is a time to celebrate the achievements of the LGBTQ+ community and to advocate for greater equality and acceptance. For those who identify as LGBTQ+ or are allies, it's an opportunity to learn more about the community and support their rights.
Published in ACFE Insights Blog

Despite all of the advancements in security measures in our modern era and through the long history of check fraud, the creativity and sophistication of fraudsters continue to pose significant challenges.
Published in ACFE Insights Blog

In the aftermath of events like Hurricane Idalia and the wildfires in Hawaii, it is crucial to be aware of the various types of fraud that can emerge.
Published in ACFE Insights Blog

The investigative process is essential for uncovering crimes, particularly white-collar crimes. These are crimes committed by individuals, organizations or public officials for financial gain, often without resorting to violence. Edwin Sutherland, one of the pioneers in this field, recognized the complex nature of these offenses.
Published in ACFE Insights Blog

Sam Bankman-Fried's meteoric rise was coupled with an aura of mystery, and questions began to circulate about the integrity of his financial dealings.
Published in ACFE Insights Blog

The U.K.’s Economic Crime and Corporate Transparency Bill made its way through the House of Commons and, more recently, the House of Lords. As the bill approaches becoming law and faces only a few final steps before being law, an analysis of details and slated changes is timely.
Published in ACFE Insights Blog

In the ever-evolving landscape of the digital world, influencer marketing has taken center stage as a powerful tool for brands and businesses to reach their target audience. However, with great power comes great responsibility, and as the industry continues to grow, so does the potential for fraud. Let's delve into the world of influencer fraud and explore its many faces, consequences and potential solutions.
Published in ACFE Insights Blog

As part of the Internet Archive, the Wayback Machine contains a historic log of an estimated 735 billion web pages, making it an incredibly powerful database supporting a range of businesses and industries.
Published in ACFE Insights Blog

Multi-level marketing (MLM) companies and pyramid schemes share similarities like recruitment-focused structures but have key differences, such as the sale of products in MLMs versus pyramid schemes that redistribute payments and fees to early investors.
Published in ACFE Insights Blog

Booking a vacation rental online comes with the convenience of browsing listings from the comfort of home. But it also opens the door to scammers trying to take advantage of unsuspecting travelers.
Published in ACFE Insights Blog

In the world of corporate espionage, uncovering the truth can be a daunting task. But when a global research firm approached us to investigate the simultaneous resignation of two key employees in the latter half of 2020, we knew we had our work cut out for us. The management suspected that the employees were leaving to join a competitor in the same region and requested an eDiscovery review to determine the truth.
Published in ACFE Insights Blog

A group of investors who had invested USD $100 million in an educational institution were concerned about the institution's operations and suspected that their funds were being misused. Our team of experts took on the case, employing a range of techniques and procedures to uncover the truth.
Published in ACFE Insights Blog

Patient Assistance Programs (PAPs) provide free or low-cost medications to eligible patients who cannot afford them. Despite regulatory oversight, instances of PAP fraud have been reported globally.
Published in ACFE Insights Blog

Toward the end of the spring season, our team was contacted by the internal audit head of a global retail organization who requested that we investigate several abnormal transactions in a recently acquired subsidiary, referred to as "PQR," located in the western region of India.
Published in ACFE Insights Blog

As the landscape of financial crime continues to evolve, financial institutions must stay vigilant and prepared to address emerging risks. In this regard, aligning anti-money laundering (AML) programs with the Financial Crimes Enforcement Network AML Priorities becomes crucial.
Published in ACFE Insights Blog

This year, nine candidates have been selected to fill three positions on the 2024-2025 Board of Regents.
Published in ACFE Insights Blog

Although well-intentioned, the U.K.’s fiscal response to the COVID pandemic has been seriously flawed, creating huge opportunities for fraudsters to exploit multiple shortcomings of the various schemes offered by the government to help support businesses.
Published in ACFE Insights Blog

Behavioral biometrics are used to verify the identity of an individual through the analysis of patterns of human behavior. Unlike traditional biometric methods, behavioral biometrics are a more convenient and less intrusive form of identification.
Published in ACFE Insights Blog

The most affordable homes can be the ones built as part of a homeowner’s association (HOA) – nothing wrong with that. The surroundings are always maintained through the HOA and the only thing homeowners need to worry about is the interior of the house, as well as paying regular monthly dues to the HOA. But after settling in, it may quickly become apparent that living under an HOA involves a level of oversight that can be surprising.
Published in ACFE Insights Blog

It is important to recognize the critical role whistleblowers play in efforts to combat financial crime. However, while countries such as the United States and Canada have paved the way here, the United Kingdom has been slow to follow suit.
Published in ACFE Insights Blog

The 36th Annual ACFE Global Fraud Conference is set to have an extraordinary lineup of keynote speakers, networking opportunities, a fundraising concert and more.
Published in ACFE Insights Blog

What if the largest enabler of fraud is not a rogue employee, but an executive who believes they are doing the right thing for the business? Discover how senior leaders can unintentionally enable fraud by prioritizing efficiency over ethics.
Published in ACFE Insights Blog

Wondering how to turn “invisible” fraud-prevention wins into a clear case for a raise or promotion? In this Q&A, veteran managers reveal the performance metrics, certifications and soft-skills that convince decision-makers you’re ready for the next step.
Published in ACFE Insights Blog

What if the very strategy that makes a company efficient is also what makes it vulnerable to fraud? Explore how fraud can quietly thrive in streamlined organizations and what anti-fraud professionals can do about it.
Published in ACFE Insights Blog

What does it take to earn your CFE credential? Two professionals share their motivations, study strategies and how becoming a Certified Fraud Examiner (CFE) advanced their careers.
Published in ACFE Insights Blog

In 2021, JPMorgan acquired Charlie Javice's startup, Frank, for $175 million, only to soon discover they were victims of her scam. Learn how even banking giants like JPMorgan can fall victim to fraud by not taking the proper due diligence measures.
Published in ACFE Insights Blog

Even well-intentioned medical professionals can face legal consequences when they neglect the business side of health care. Understanding the revenue cycle is key to spotting fraud, reducing risk and maintaining compliance.
Published in ACFE Insights Blog

Responding to fraud requires careful investigation, objective decision-making and clear documentation. Discover the steps organizations should take after discovering fraud, from internal investigations to criminal referrals, with insights from Occupational Fraud 2024: A Report to the Nations.
Published in ACFE Insights Blog

David Judd, a Michigan nurse practitioner, billed for an unattainable number of patient visits and hours, leading to significant overpayments from Medicare. Read more about this scheme, known as the "Impossible Day", where health care providers will fraudulently claim they worked more than 24 hours in a single day.
Published in ACFE Insights Blog

Risk management professionals play a vital role in identifying vulnerabilities and building resistance against fraud. By integrating fraud risk into broader organizational strategies, they help prevent schemes before they start and support a culture of accountability.
Published in ACFE Insights Blog

Health care fraud continues to drain vital resources from the U.S. system, impacting patients and providers alike. This blog breaks down the latest data, trends and enforcement efforts behind the $54 billion recovered through the False Claims Act since 1987.
Published in ACFE Insights Blog

Drexel University held their 11th annual Fraud and Internal Control Case Competition (F1C3), giving students the opportunity to practice their anti-fraud skills in a realistic, professional environment.
Published in ACFE Insights Blog

Home health care is ripe for fraud, with the federal government estimating that 69% of the population will need caregiving—a vulnerable population that could be very appealing to fraudsters seeking to exploit Medicare and Medicaid systems.
Published in ACFE Insights Blog

As private sector companies in Mexico continue to reshape business efficiencies and increase in value, accountability and oversight remain as important as ever. Explore why regulatory efforts and internal investigations must meet the growing demand in the region.
Published in ACFE Insights Blog

Traditionally a heavier lift, spear phishing is using new tools to make these schemes more effective and easier for fraudsters to execute. Explore how AI is automating research to craft customized spear phishing strategies.
Published in ACFE Insights Blog

Recent cases highlight how kickbacks are often disguised through lavish gifts, hidden payments and sham business arrangements, emphasizing the importance of maintaining ethical practices in health care.
Published in ACFE Insights Blog

Fraud detection is a growing challenge, but researchers like Ivy Munoko are exploring how AI and key audit factors can improve detection efforts. Supported by the ACFE Research Institute, her work provides critical insights for auditors, fraud examiners and regulators navigating an evolving fraud landscape.
Published in ACFE Insights Blog

Health care fraud remains a major problem in the anti-fraud field, requiring a deep understanding of industry terminology for effective investigations.
Published in ACFE Insights Blog

As fraud risks evolve, having a strong in-house investigation team is crucial—but how do you gauge its effectiveness? The In-House Fraud Investigation Teams: 2025 Benchmarking Report delivers key insights on team structure, case resolution and training investments to help you strengthen your fraud response strategy.
Published in ACFE Insights Blog

While many organizations are still adjusting to AI-driven risks introduced by industry leaders like OpenAI and Google, a new wave of AI tools like DeepSeek presents fresh challenges that organizations must address.
Published in ACFE Insights Blog

The first ACFE Report to the Nations was published nearly 30 years ago in 1996. It would be overly simplistic to say that fraud has grown since then, but the data clearly shows significant increases as more information has been reported by CFEs around the world.
Published in ACFE Insights Blog

Fraud can infiltrate even the most secure organizations, leaving a trail of financial and reputational damage in its wake. When fraud arises, forensic accountants play a critical role in uncovering the truth, guiding investigations and safeguarding organizational integrity.
Published in ACFE Insights Blog

Read on to discover Cecilia’s approach to exam preparation, how the challenge helped her succeed and her advice for future participants aiming to earn their CFE credential.
Published in ACFE Insights Blog

Arthur Andersen, Enron and WorldCom certainly left behind a legacy that changed the financial world, especially that of the public company. The Public Company Accounting Oversight Board (PCAOB) was born thanks to SOX and with it brought attention and improvements.
Published in ACFE Insights Blog

Each year, Certified Fraud Examiners (CFEs) in good standing are given the opportunity to help foster the growth and development of the anti-fraud profession by casting votes for the Association of Certified Fraud Examiners (ACFE) Board of Regents.
Published in ACFE Insights Blog

In today’s modern age almost every business is dependent on the internet and information technology to accomplish a variety of daily operational tasks. From emails to e-commerce and e-banking, sensitive business activities are conducted via the internet. While the internet has undoubtedly made it easier for businesses of all shapes and sizes to operate, it has also made it easier for cybercriminals to gain access to confidential information and systems.
Published in ACFE Insights Blog

Abigail had her first introduction to the fraud industry when a former coworker referred her to an open position at their health insurance company. Later she began her work as a Fraud Coordinator in 2018 and since has made the transition to becoming a Fraud Analyst. In 2021, Abigail joined the 90-Day CFE Exam Challenge, where she was able to study and pass her exams within 90 days.
Published in ACFE Insights Blog

After years of experience leading hundreds of fraud-related investigations, Dr. Tim Klatte, CFE made the decision to prepare for the CFE exam with the help of the 90-Day CFE Exam Challenge.
Published in ACFE Insights Blog

Now available at ACFE.com/Government, this new hub offers multiple forms of content for government and public administration professionals to expand their knowledge base and continue developing skills essential to the prevention and detection of fraud at various levels of government.
Published in ACFE Insights Blog

The U.S. Department of Justice (DOJ) announced in early February 2022 that they had arrested two individuals, Ilya Lichtenstein and his wife Heather Morgan. When the couple was arrested in connection with the theft of cryptocurrency from the Bitfinex cryptocurrency exchange in 2016 and subsequent laundering of the proceeds, it led to one of the most valuable seizures of illicit proceeds in law enforcement history.
Published in ACFE Insights Blog

It comes as no surprise to learn that Lisa Osofsky is stepping down next summer after five years as head of the U.K.’s Serious Fraud Office (SFO). Ms. Osofsky has overseen an often contentious five years at the helm of the U.K.’s leading fraud prosecution agency.
Published in ACFE Insights Blog

On July 14, 2022, Mike Esposito, owner of The ‘In’ Groove record store in Phoenix, Ariz., stated that MoFi has been using digital files in its production of so-called original master tape albums despite marketing the reissues as authentic.
Published in ACFE Insights Blog

An investigation into fraudulent activities was turned over to me after three other independent investigators did not satisfy the leadership of the results. Here is how my team calculated the $611K loss due to fraud that other investigations missed.
Published in ACFE Insights Blog

Recently, I worked on a case wherein a whistleblower raised allegations on two employees that the company was engaging in unethical practices. The allegations included bribery and corruption, conflict of interest, breach of code of conduct, misappropriation of assets, high prices and poor quality of products supplied and abuse of position.
Published in ACFE Insights Blog

Unfortunately, not all causes we are called to join have a noble motive; some of them are organized by unscrupulous individuals who take advantage of our generosity to steal our money. But how can you donate without being a victim of a charity scam?
Published in ACFE Insights Blog

A self-proclaimed amateur rapper nicknamed the “Crocodile of Wall Street,” Heather Morgan, along with her husband Ilya Lichtenstein, were arrested and charged with conspiracy to allegedly launder $4.5 billion in stolen Bitcoin.
Published in ACFE Insights Blog

Joshua David Nicholas, the head trader of cryptocurrency platform EmpiresX, pleaded guilty on September 8 in an alleged investment fraud that raised around $100 million for the company, according to the U.S. Justice Department.
Published in ACFE Insights Blog

The growing trend of shoppers preferring pajamas and pumpkin pie to cold weather and crowds reached an all-time high in 2021 as online shopping for the holiday season soared due to the COVID-19 pandemic. In 2022, global online sales again hit a new high of $281 billion during Cyber Week (Thanksgiving Day through Cyber Monday). So, what do all these numbers mean for fraud examiners?
Published in ACFE Insights Blog

After seven days of deliberations, a jury in California found Theranos founder Elizabeth Holmes guilty on four out of 11 federal fraud charges on January 3, 2022.
Published in ACFE Insights Blog

On Thursday, a jury of seven women and five men convicted Ramesh “Sunny” Balwani on 12 counts of federal fraud.
Published in ACFE Insights Blog

While victims of traditional identity theft often catch it quickly, victims of medical identity theft may not know they are victims until they need critical medical treatment. In this episode of Fraud Talk, Scott Ward, CFE, senior vice president at Qlarant, discusses the insidious nature of medical identity theft, the impact it has on its victims and what people and governments can do to help combat it.
Published in ACFE Insights Blog

Tod McDonald, CPA and Garth Leonard, CFE, from Valid8 Financial, join ACFE Community Manager Rihonna Scoggins in the most recent episode of Fraud Talk to explore the current resources at hand for fraud examiners.
Published in ACFE Insights Blog

In this excerpt from episode 118 of Fraud Talk, Jim Ducharme, COO of Outseer, talks with Rihonna Scoggins, ACFE Community Manager, about how Buy Now, Pay Later services are being exploited through identity theft.
Published in ACFE Insights Blog

In this excerpt from episode 123 of Fraud Talk, Kate Pospisil, ACFE Communications Specialist, and associate professor of accounting, taxation and business law at SUNY Old Westbury, Dr. David Glodstein, speak about how the Justice for Fraud Victims Project benefits underprivileged groups and small businesses, while allowing the next generation of fraud fighters to learn and gain professional experience.
Published in ACFE Insights Blog

In Episode 125 of Fraud Talk, ACFE Training Director Jason Zirkle, CFE, is joined by Collins Wanderi, CFE, Bill Stakes, CFE, and Monica Meeks, CFE, to discuss the tools they’ve gained and advice they offer to veterans and active-duty military members looking to earn their CFE credential.
Published in ACFE Insights Blog

In this excerpt from episode 124 of Fraud Talk, ACFE Chief Training Officer John Gill, J.D., CFE, and Gary Weiss, author of “Retail Gangster: The Insane, Real-Life Story of Crazy Eddie,” talk about the insurance scheme Eddie Antar committed but was never caught for.
Published in ACFE Insights Blog

The Justice Department charged 47 defendants on September 20th for allegedly defrauding a federal program that provided food for needy children during the pandemic, describing the scheme — totaling nearly $250 million — as the largest uncovered to date.
Published in ACFE Insights Blog

In an email obtained by “The Ankler,” it was revealed that Michael Lewis, the author of "The Big Short", has been working on profiling the Sam Bankman-Fried’s rise to power, as well as a once-budding rivalry between the 30-year-old billionaire and Binance CEO Changpeng Zhao.
Published in ACFE Insights Blog

Synthetic identity fraud occurs when perpetrators combine piecemeal and, at times, factual information to create a new identity.
Published in ACFE Insights Blog

In the past year, record numbers of employees have been quitting their jobs, and sometimes leaving entire industries. With so much turmoil in the job market, it comes as no surprise that fraudsters are pouncing. Career scammers are targeting job seekers using LinkedIn to reach out with fake offers and requesting personal information.
Published in ACFE Insights Blog

Cognitive bias is when an investigator's own assumptions or beliefs impact their judgment of information and evidence. When investigating fraud, it is important that the investigator be able to think clearly and make unbiased decisions.
Published in ACFE Insights Blog

Alexandre De Genaro, CFE, realized he was on the right path when he garnered his first confession during a fraud investigation. After spending time in information security and loss prevention, De Genaro is now the Head of Business Security, Latin America for General Mills.
Published in ACFE Insights Blog

Angelica Isgleas Pacheco, CFE, began her career as an auditor for an accounting firm. She found her love for fighting fraud through her career and has excelled due to her passion for her community. This is her story in her own words.
Published in ACFE Insights Blog

Diana Muyibi is a graduate student studying at State University of New York (SUNY), Old Westbury and also a proud past recipient of the ACFE’s Ritchie-Jennings Memorial Scholarship. Diana is in the Master of Science in forensic accounting program and is expected to graduate this spring.
Published in ACFE Insights Blog

Michael Mingo-Dabney, CFE, began his career as an anti-fraud professional after learning about the prevalent embezzlement and money laundering corrupting a town in Colombia while serving as a volunteer for the Peace Corps. Michael continues his work against fraud as a fraud analyst for C2 Alaska, as well as serving as a contractor for the Securities and Exchange Commission’s Division of Enforcement.
Published in ACFE Insights Blog

Paul McCormack, CFE, began his career in anti-fraud as a forensic accountant and after gaining a wealth of experience, he made the leap and started his own freelance writing business in the fraud and compliance space. Paul has written for countless publications and companies throughout the industry, including Fraud Magazine.
Published in ACFE Insights Blog

Ryan Cannon is an undergraduate student studying at the University at Albany and also a proud past recipient of the ACFE’s Ritchie-Jennings Memorial Scholarship. Ryan is pursuing a dual major in Homeland Security and Business Administration.
Published in ACFE Insights Blog

Sherene Teo, CFE, began her career in anti-fraud as an auditor in China and after encouragement she applied to become an in-house investigator which helped her gain experience to join her new team at Microsoft.
Published in ACFE Insights Blog

ACFE member William Klun spent decades working in the financial industry before setting his sights on fighting fraud. In addition to his drive to seek the truth, he also spends time helping refugees find asylum. Here is his story in his own words.
Published in ACFE Insights Blog

The ACFE Mentoring Program connects members to anti-fraud professionals from all over the world who can offer a wealth of resources, experience, advice and guidance. Mentees can search among registered mentors to find individuals whose experience and expertise match the areas in which they wish to be mentored. Caroline Kaye initially reached out to Holly Atkins, CFE, after viewing her mentor profile on the ACFE Community, and since then the pair have been connecting through their personal and professional experience.
Published in ACFE Insights Blog

The ACFE Mentoring Program connects members to anti-fraud professionals from all over the world who can offer a wealth of resources, experience, advice and guidance. Kate Rolan initially reached out to David Harper, CFE, after seeing his experience in law enforcement and investigations on the ACFE Community. This is Kate and David’s mentoring story.
Published in ACFE Insights Blog

CFEs have a good eye for email scams and can usually spot them quickly. But sometimes the language and graphics are so convincing that they fool even the most skilled observer.
Published in ACFE Insights Blog

Could increased disclosure and whistleblower protections for private companies prevent another fraud scheme like Theranos?
Published in ACFE Insights Blog

We have compiled a list of the most popular recent limited series, documentaries and films about fraud that can add context to known cases, illustrate some common fraud schemes and provide insight into the fraudsters at the center of these now infamous frauds.
Published in ACFE Insights Blog

With all the busy work of report writing, speaking to law enforcement, preparing for court and filing examination findings, investigators do not always remember the trauma a financial loss can be to the victim.
Published in ACFE Insights Blog

As experienced fraud examiners know, fraud comes in many varieties, including tales that are truly frightening. These fraudsters were willing to play any type of trick to take their ill-begotten treats. Read on to learn more about this year’s tales of terrifying fraud, but don’t say we didn’t warn you.
Published in ACFE Insights Blog

Reality is simply based in fact, whether it be an event or transaction. A fraudster’s movement is a documented reality. Reality, or the truth, is simply confirmed by documentation, digital footprints and verifiable eyewitnesses, which can be pieced together to reveal the factual timeline.
Published in ACFE Insights Blog

In September 2021, the IRS published a request for proposal titled, “Development of Exploitation Techniques Against Cryptowallets.” According to supporting documentation, it appears that the digital forensics unit of their Criminal Investigations branch has repeatedly run into scenarios involving the seizure of crypto hardware wallets (also known as cold storage devices) that could not be accessed due to their security features.
Published in ACFE Insights Blog

Besides its stable political and economic environment, what makes the land of tulips and windmills so attractive to corporate giants such as Starbucks, Google and Amazon?
Published in ACFE Insights Blog

Supreme Audit Institutions (SAIs) play an important role in national and global economy by ensuring that public resources are managed properly and in accordance with established rules.
Published in ACFE Insights Blog

The U.S. Department of Justice (DOJ) has brought insider trading charges against Ishan Wahi, a former Coinbase product manager, Nikhil Wahi and Sameer Ramani after they allegedly made profits of more than $1 million by buying crypto assets before their listings on the exchange.
Published in ACFE Insights Blog

The Association of Certified Fraud Examiners (ACFE) is proud to announce that Thomas Caulfield, CFE, and Natalie Lewis, CFE, have been elected to the 2023–24 ACFE Board of Regents. Fellow Certified Fraud Examiners (CFEs) elected them from candidates selected by the Board's nomination committee. Caulfield and Lewis will take office at the Board's meeting in February.
Published in ACFE Insights Blog

In 2021, Russian crude and condensate output reached 10.5 million barrels per day, making up 14% of the world’s total supply. In the same year, Russia exported oil worth USD 300 billion, accounting for 11% of the global oil trade. The country exports most of its oil production, with almost all going to Europe (about 80%) and Asia (about 20%).
Published in ACFE Insights Blog

Money mules continue to play a key role in international money laundering operations. Accordingly, both Europol and the FBI have recently stepped up their efforts to raise public awareness about money mules and how to avoid becoming one.
Published in ACFE Insights Blog

Whistleblowing is one of the most powerful weapons in the fight against fraud, money laundering and corruption, but the United Kingdom’s approach needs to be reconsidered. Whistleblowing can be a testy subject, but I believe it is potentially one of the most powerful weapons in our anti-money laundering (AML) arsenal.
Published in ACFE Insights Blog

Online payments through apps such as Zelle are easy to use and serve a valid purpose in today’s digital society. However, as easy as they are to use, they also give fraudsters an easily accessible path to steal your money.
Published in ACFE Insights Blog

At the 33rd Annual ACFE Global Fraud Conference, Roderick Chambers speaks with ACFE Research Manager Mason Wilder, CFE, to discuss the importance of technical controls and knowledge to protect your organization from fraud.
Published in ACFE Insights Blog

In this excerpt from episode 117, Larry Nielson talks with Mason Wilder, CFE, about how prevalent cryptocurrency is in his fraud work, and how crypto is being used in traditional crime as a new medium.
Published in ACFE Insights Blog

William Shakespeare is widely considered to be one of the most prolific and influential writers of all time. But one group of individuals, who call themselves “Oxfordians” and their theory the "Shakespeare Authorship Question," falsely claim that what we know to be Shakespeare's plays and poetry were actually penned by someone else.
Published in ACFE Insights Blog

International pop star Shakira has been in the spotlight this past week – not because of a new album or performance, but for a looming trial in a tax fraud case.
Published in ACFE Insights Blog

Pride Month may be over, but, for scammers, the calendar doesn’t matter: There’s fraud to be had every month of the year.
Published in ACFE Insights Blog

Recent reports show that PPP loan fraud soared in the last two years, putting billions of taxpayer dollars in the pockets of fraudsters and criminals.
Published in ACFE Insights Blog

Stock market manipulation and insider trading fraud are perennial challenges, with fraudsters capitalizing on information asymmetry and exploiting investor psychology.
Published in ACFE Insights Blog

If you have the CFE Exam Prep Course, the Prep Toolkit or are planning to get either of the two, we invite you to sign up for the 90-Day CFE Exam Challenge and earn your Certified Fraud Examiner (CFE) credential by March 31, 2025.
Published in ACFE Insights Blog

Welcome to Fraudify Wrapped 2024! Drawing from industry trends, news stories and expert insights, we have compiled a recap of the biggest fraud developments of the year.
Published in ACFE Insights Blog

The Association of Certified Fraud Examiners (ACFE) is proud to announce that Annemari Krugel, CFE, and Mark J. Sullivan, CFE, CPP, CFI, have been elected to the 2025–2026 ACFE Board of Regents. Fellow Certified Fraud Examiners (CFEs) elected them from candidates selected by the Board's nomination committee. Krugel and Sullivan will take office in February 2025.
Published in ACFE Insights Blog

When the Association of Certified Fraud Examiners (ACFE) conducted its first Report to the Nation in 1996, one of the purposes was to describe the typical occupational fraud perpetrator. In 1996, our results showed that the typical fraudster was a college-educated, married, white, male employee. While some consistencies remain, much has changed in recent years.
Published in ACFE Insights Blog

Food fraud is dangerous for many reasons. It has the potential to cause harm to people and the economy through its deception. When ingredients are removed or added, it greatly changes the product that is being sold, which may harm individuals, as well as damage the reputations of companies and industries at large.
Published in ACFE Insights Blog

Among the most valuable assets in an organization’s fraud prevention toolkit is its internal audit team. Internal auditors have the advantage of an insider’s view of an organization’s controls, making them uniquely positioned to help identify fraud risks and support investigations.
Published in ACFE Insights Blog

What does it mean to have an organization that has a culture that ensures a massive theft does not occur—or if someone does attempt a fraud, it is caught early?
Published in ACFE Insights Blog

This year, six candidates are on the ballot and will fill two open positions on the 2025-2026 ACFE Board of Regents. All CFEs who are in good standing have until November 30, 2024, to cast their votes. The newly elected Regents will each serve a two-year term beginning in February 2025.
Published in ACFE Insights Blog

As part of this exciting shift, Fraud Magazine will transition to become a fully digital, online publication. The January/February 2025 issue will be the final printed and shipped version of the magazine, honoring the publication’s long history and celebrating its growth into the future.
Published in ACFE Insights Blog

Are you gearing up to take the Certified Fraud Examiner (CFE) exam? Proper preparation is key to success, and here is how you can effectively strategize and streamline your study process.
Published in ACFE Insights Blog

This yearly compilation, which dates back to 1990, highlights key cases involving conflict of interest, bribery and corruption by federal employees, contractors, grant recipients and others.
Published in ACFE Insights Blog

This article presents a detailed case study of a leading automobile company that undertook a comprehensive investigation into allegations of kickbacks, conflicts of interest among its vendors and employees, and theft of high-quality automotive paint.
Published in ACFE Insights Blog

Whether it is hosting a training session, sharing educational materials on social media or joining a community initiative, there are many ways to contribute to the fight against fraud.
Published in ACFE Insights Blog

The 2024 Compensation Guide for Anti-Fraud Professionals comes with several new findings and analysis, reflecting the evolving landscape of the anti-fraud profession.
Published in ACFE Insights Blog

We are thrilled to announce that Fraud Magazine will relaunch an updated version of our website in the spring of 2025!
Published in ACFE Insights Blog

Motivated by the potential for recognition, professional growth and networking within the anti-fraud community, Isaac Asamoah Amponsah seized the opportunity, seeing his scholarship not just as financial support but as a catalyst for future career advancement and impact in the field of anti-fraud.
Published in ACFE Insights Blog

The Chase Bank "money glitch" trend recently gained traction on social media platforms, where influencers and scammers misled many into believing they can get free money from banks by exploiting a so-called "glitch."
Published in ACFE Insights Blog

On July 19, 2024, CrowdStrike pushed out an update to one of its programs, a vulnerability scanning tool called Falcon Sensor, that contained a significant bug. For computers running on a Microsoft Windows operating system, this faulty update caused the computer to crash.
Published in ACFE Insights Blog

By examining some of the most notorious historical frauds and integrating insights from the ACFE’s Occupational Fraud 2024: A Report to the Nations, businesses can better protect themselves from similar pitfalls today.
Published in ACFE Insights Blog

While support groups play a critical role, there are additional resources and strategies that can further aid in the recovery process for fraud victims.
Published in ACFE Insights Blog

This article provides an overview of a comprehensive forensic investigation conducted for a prominent Indian firm in the IT and ITeS industry.
Published in ACFE Insights Blog

The suspected borrower company was dealing in garments, while the suppliers were traders of animal husbandry products, revealing even more inconsistencies in the trade activities and additional evidence of round-tipping of transactions.
Published in ACFE Insights Blog

Package delivery scams typically involve fraudulent communications claiming to be from legitimate shipping companies. Scammers use various tactics to deceive recipients into believing they have a package waiting for delivery, a missed delivery attempt or an outstanding fee that needs to be paid.
Published in ACFE Insights Blog

In the specialized field of Applied Behavior Analysis (ABA) therapy, which is crucial for improving behaviors in individuals with autism and other developmental conditions, the importance of adhering to ethical standards cannot be overstated. However, dishonest and fraudulent activities frequently jeopardize this field's credibility.
Published in ACFE Insights Blog

Fraud detection often requires sharp observational skills and a keen eye for detail. While many tools and techniques can aid in this process, one of the most effective methods is recognizing behavioral red flags.
Published in ACFE Insights Blog

Occupational Fraud 2024: A Report to the Nations not only identifies the top anti-fraud controls that can help protect organizations, but it also illustrates what can happen when controls are weak or altogether missing.
Published in ACFE Insights Blog

Artificial intelligence (AI) is becoming an increasing problem not just for hackers and fraudsters, but also for identity theft. Recently, there have been an influx of deepfakes of celebrities, but not just their faces—their voices.
Published in ACFE Insights Blog

The ACFE's recently released Occupational Fraud: 2024 A Report to the Nations paints a clear picture: tip lines remain the most effective tool for detecting fraud, uncovering 43% of cases.
Published in ACFE Insights Blog

On March 28, 2024, Samuel Bankman-Fried, the founder of the cryptocurrency trading firm Alameda Research and the cryptocurrency exchange FTX, was sentenced to 25 years in federal prison for his role in several fraud schemes. Because the sentencing guidelines are advisory, federal judges have discretion when sentencing offenders. This can result in wide discrepancies between offenders who have been convicted of similar or identical offenses, even within the same federal jurisdiction.
Published in ACFE Insights Blog

From massive corporate fraud in China to sophisticated cryptocurrency thefts and international scam networks, these cases underline the persistent challenges in combating financial crime.
Published in ACFE Insights Blog

Having a safe, secure and reliable reporting system for employees to use will help ensure that wrongdoing is reported while whistleblowers are protected.
Published in ACFE Insights Blog

Artificial Intelligence to commit healthcare fraud or to prevent healthcare fraud? The gradual acceptance of artificial intelligence in many industries including the healthcare sector is seen by many as a giant revolutionary step.
Published in ACFE Insights Blog

The latest insights from the Occupational Fraud 2024: A Report to the Nations spotlight a significant shift towards web-based reporting mechanisms, signaling an opportunity to involve Generation Z (Gen Z) in the fight against fraud.
Published in ACFE Insights Blog

In a webinar presented to ACFE Corporate Alliance members and ACFE Law Enforcement and Government Alliance members, Lauren Kohr and Victor Cardona, CFE, delve into the significance of establishing public-private partnerships (PPP).
Published in ACFE Insights Blog

The ACFE is not only here to help you attain your Certified Fraud Examiner (CFE) credential, but to help you utilize it to its fullest potential. From improving your skills to finding the perfect job fit, the ACFE has your back every step of the way.
Published in ACFE Insights Blog

According to the UN Conference on Trade and Development, in 2023 maritime trade accounted for over 80% of international trade, carried out by vessels flagged and owned by different countries and manned by international crews.
Published in ACFE Insights Blog

Beneath the glossy labels and vibrant packaging, a darker trend is emerging: greenwashing. This deceptive practice not only misleads consumers but also undermines genuine efforts toward environmental sustainability for a profit.
Published in ACFE Insights Blog

The SNPR proposal seeks to “add a prohibition on the impersonation of individuals and extend liability for violations of the Rule to parties who provide goods and services with knowledge or reason to know that those goods or services will be used in impersonations of the kind that are themselves unlawful under the Rule.”
Published in ACFE Insights Blog

The Indian pharmaceutical sector is increasingly facing a formidable challenge — the diversion of institutional drugs to retail markets.
Published in ACFE Insights Blog

From unlocking new career opportunities, to staying ahead of industry trends, networking empowers fraud examiners to thrive in a dynamic landscape where collaboration and knowledge exchange are essential.
Published in ACFE Insights Blog

Few leaders have demonstrated a commitment quite like Jeanette LeVie, who is celebrating her retirement after 32 years of service to the ACFE.
Published in ACFE Insights Blog

In this guide, we will explore various strategies to help you leverage your CFE credential effectively and advance your career in the fraud examination field.
Published in ACFE Insights Blog

As recipients of the ACFE Research Institute (ARI) grant, Marie Rice and David Glodstein stand at the forefront of advancing the field of fraud examination and prevention.
Published in ACFE Insights Blog

The 13th edition of the ACFE’s biennial research report continues its pivotal role in shedding light on the pervasive issue of occupational fraud, offering unparalleled insights into the mechanics of fraud within organizations worldwide.
Published in ACFE Insights Blog

There are consistent factors in fraud, like social engineering tactics that exploit human behavioral tendencies or external financial pressures that lead fraudsters to commit their crimes, but there are also trends and themes that emerge and affect the anti-fraud profession on a more limited timeframe.
Published in ACFE Insights Blog

February is Black History Month, a time when we celebrate the contributions and achievements of Black Americans throughout history. As we reflect on the past and present struggles of the Black community, it's important to highlight and support organizations that are actively working to make a difference.
Published in ACFE Insights Blog

The 2024 Anti-Fraud Technology Benchmarking Report, developed by the Association of Certified Fraud Examiners (ACFE) in partnership with SAS, highlights a significant trend in the fight against fraud.
Published in ACFE Insights Blog

Between 1999 and 2015, more than 900 U.K. post office branch managers were wrongly accused of theft or fraud due to a flawed computer system. This scandal has had profound consequences, including imprisonment, financial ruin and other tragic outcomes in the years that followed.
Published in ACFE Insights Blog

Finding work in the fraud examination field can be very challenging. Colin May, CFE, provides some perspective and ideas on how to stay motivated and resilient during a difficult job search.
Published in ACFE Insights Blog

While it may seem like a lower-level scam, gift card fraud has real consequences for retailers. An analysis of data drawn from the Federal Trade Commission’s Consumer Sentinel database found that gift card scams have led to a consumer loss of $148 million.
Published in ACFE Insights Blog

Fighting fraud is everyone’s responsibility, and I thank all of you, our members, for rising to the challenge.
Published in ACFE Insights Blog

In the continued pursuit of reducing fraud worldwide, the Association of Certified Fraud Examiners (ACFE) has joined the Anti-Fraud Collaboration (AFC) as its newest member.
Published in ACFE Insights Blog

Each year, the ACFE honors outstanding individuals and organizations who make significant contributions to fighting fraud. The ACFE is proud to recognize these exceptional individuals for their invaluable service in the ongoing fight against fraud through the ACFE Awards.
Published in ACFE Insights Blog

There appeared to be an overwhelmingly substantial number of “high loss” fraud schemes being perpetrated in 2022 (as reported by the Federal Trade Commission). This was shocking as it appeared to show more high loss cases than low loss cases. This would signal a marked departure from decades of historical statistics. Statistics we, in program oversight, rely upon to strategize our anti-fraud endeavors.
Published in ACFE Insights Blog

As a result of the memorandum titled “Individual Accountability for Corporate Wrongdoing” issued by former U.S. Deputy Attorney General (DAG) Sally Yates on September 9, 2015, even those who merely had knowledge that something wrong was happening but didn’t report it would potentially face penalties.
Published in ACFE Insights Blog

According to the National Health Care Anti-Fraud Association, the U.S. loses tens of billions of dollars each year to health care fraud. This post discusses five common billing schemes, and how to detect and prevent them.
Published in ACFE Insights Blog

An act of fraud rarely occurs without subsequent acts to hide it. In the time after a fraud takes place, perpetrators are working in multiple ways to either circumvent controls or take advantage of a lack of controls.
Published in ACFE Insights Blog


The growing abundance of internal and external threats can make it difficult to stay ahead of fraudsters. While fraud itself hasn’t changed all that much in recent years, the risks continue to grow in both size and complexity as technology changes and the ability to move, share and expose corporate assets becomes easier. In today’s technology-crazed age, the scope of risk is growing, and businesses that do not keep up with evolving threats will be vulnerable.
Published in ACFE Insights Blog

Dubbed the “archetype of avarice” by The New York Times, Dennis Kozlowski could have written the book on how NOT to set an ethical tone at the top.
Published in ACFE Insights Blog

If you suspect fraud has occurred at your organization, take these immediate action steps.
Published in ACFE Insights Blog

We have compiled a list of 10 fraud-related podcasts that will have you laughing and learning the whole way through.
Published in ACFE Insights Blog

Joseph Cox, an investigative reporter at VICE, enlisted the help of a friendly hacker to report on a service called Sakari, a company that streamlines mass SMS messaging for businesses. The hacker was able to use the service to reroute all of Cox’s text messages to the hacker’s device, and Cox didn’t receive a single notification about the theft of his number. He just stopped receiving text messages.
Published in ACFE Insights Blog

I hosted a weekly virtual class and talked about the 5Ws and 1H of writing — What, Why, Who, Where, When and How. I learned this concept from a former boss while working on an investigation, and it’s a tool commonly used by journalists, researchers and psychologists. These occupations can be similar to investigators in that they all strive to unearth issues as well as understand the psychology behind an individual’s actions.
Published in ACFE Insights Blog

E-payment through third-party channels or platforms — like Venmo, Cash App, Alipay or WeChat Pay — is widely used in our daily life, especially as COVID-19 spread and stay-at-home restrictions fueled precipitous growth of third-party payments. To understand these risks, let’s take a look at the third-party payment flow and bring out the iterated anti-money laundering (AML) measures as well as the major difficulties to implement them.
Published in ACFE Insights Blog

Bernadette Kakooza, CFE, is more than just an accomplished fraud fighter. As the first female Inspector General for the Detroit Public Schools Community District, she works hard for her geographic community as well as her anti-fraud community. In addition to spearheading investigations to save taxpayer money, she’s an active member of the Southeastern Michigan ACFE chapter and mentors fellow ACFE members.
Published in ACFE Insights Blog

Matthew Stock, J.D., CFE, CPA, is the director of the Whistleblower Rewards Practice at Zuckerman Law, where he leverages his experience as an attorney and external auditor to assist whistleblowers to investigate and disclose complex financial frauds to the government.
Published in ACFE Insights Blog

For me, one thing that came about during the pandemic is that my husband and I love watching movies together. We both have our favorite genres, but I especially enjoy a movie that involves parts of my career in the anti-fraud profession. Recently, on an ACFE Community discussion post, a question was posed: What is your favorite fraud movie?
Published in ACFE Insights Blog

In February 2021, a user known as Singularity0x01 posted a .ZIP file on RaidForums, an online forum used by hackers and cybercriminals to share leaked data. The file, entitled “Compilation of Many Breaches (COMB) 3.8Billion (Public),” contained usernames and passwords from potentially more than half of all internet users.
Published in ACFE Insights Blog

In order to protect yourself and your company from a business email compromise (BEC) attack, you should stay up to date on different tactics and techniques used by fraudsters. Here are a few key pieces of information included in a recent Better Business Bureau report that you should know about BEC scams.
Published in ACFE Insights Blog

Take a look at the current fraud prevention plan you have in place and evaluate its effectiveness.
Published in ACFE Insights Blog

In the most recent episode of the ACFE’s podcast, Fraud Talk, Julia Johnson, CFE, Research Specialist at the ACFE, breaks down three recent case studies of frauds that were committed from behind bars. She explains how the schemes were perpetrated and what fraud examiners can learn from each case.
Published in ACFE Insights Blog

Benford’s Law can be a tricky concept to grasp at first, but it provides an extra method for fraud examiners to test data for potentially fraudulent activity. Here’s more on what it is exactly and how fraud examiners can use it.
Published in ACFE Insights Blog

For anyone who made a New Year’s resolution to pass the CFE Exam this year, now may be the perfect time for you to take the first necessary steps to earn the Certified Fraud Examiner credential. Sometimes the hardest part of achieving a goal is simply getting started.
Published in ACFE Insights Blog

According to the ACFE’s Report to the Nations, organizations with less than 100 employees suffered larger median losses than those of larger companies. In other words, fraud can happen at any organization, no matter the size, so it’s important to understand the warning signs. So, what are the warning signs to look out for?
Published in ACFE Insights Blog

Recently, Charles Washington, CFE, spoke on a panel for an ACFE webinar titled “A Conversation About Diversity, Equity and Inclusion in the Anti-Fraud Profession.” In this post, he digs in even further into this topic to share insights and advice on how you can make an impact in your own workplace and foster a culture of diversity, equity and inclusion as an anti-fraud professional.
Published in ACFE Insights Blog

Monica Modi Dalwadi, CFE, CPA, is a managing partner in the D.C. area for Baker Tilly. She works primarily with owners and financial officers of companies, providing business consulting services. She also acts as a valued advisor to her clients as a partner and leader in risk, internal audit and cybersecurity.
Published in ACFE Insights Blog

In this episode of Fraud Talk, Mason Wilder, CFE, ACFE senior research specialist, and Brian Fox, vice president of strategic partnerships at Thomson Reuters and president & founder of Confirmation, discuss the rise and fall of the German payments group, Wirecard.
Published in ACFE Insights Blog

We all have so many questions right now. When will this be over? How can I keep moving when it feels like the world is telling me to stand still? What does the future hold? While I can’t answer any of these questions for you, I can answer a question we have been getting here at the ACFE: what are some easy ways for me to get my CPE while social distancing?
Published in ACFE Insights Blog

As anti-fraud professionals, we are trained to find and fix the opportunities for fraudulent activity within our organizations. But there are usually only a few of us and many employees. How is a small team, or single fraud professional, supposed to deter and detect all fraud?
Published in ACFE Insights Blog

The ACFE’s 2020 Report to the Nations not only identifies the top anti-fraud controls that can help protect organizations, but also illustrates what can happen when controls are weak or altogether missing.
Published in ACFE Insights Blog























Published in Videos








Published in Videos



Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives
.png)


Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives




Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives



While DeFi might hold a lot of promise for proponents of cryptocurrency and whatever Web 3.0 becomes, these large-scale losses show that the platforms and apps feature several serious, exploitable fraud risks.
Published in Fraud Examiner Archives

Similar to the overconfidence bias, illusory superiority is described as when you overestimate your own abilities when compared to others. Confidence is an important trait for fraud examiners, but too much of it can lead to mistakes in investigations — and illusory superiority can contribute to overconfidence in imperceptible ways.
Published in Fraud Examiner Archives

In nearly every state, guardians are considered fiduciaries. As such, they have a duty to act in their clients’ best financial interests. Sadly, that’s not always the case.
Published in Fraud Examiner Archives

While STRs may be a lucrative opportunity for many, they are not without fraudsters targeting them as well.
Published in Fraud Examiner Archives

Consumers should be wary of any QR code provided by an unknown source; such codes should be treated like unknown hyperlinks.
Published in Fraud Examiner Archives

Corporate leaders are faced with a moral dilemma, weighing the financial interests of their stakeholders against the public interest in unifying against the violent invasion of a sovereign nation. Further complicating the situation, some corporate leaders must also determine whether to cut ties with their own employees based in Russia — employees with families to feed and support.
Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

On July 15, a South Korean treasure hunting company called the Shinil Group claimed it found the wreck of a Russian warship, the Dmitrii Donskoi. The ship sank east of the Korean Peninsula more than 100 years prior during a 1905 battle with the Japanese while carrying a cargo of 200 tons of gold bullion, according to Shinil’s claim.
Published in Fraud Examiner Archives

When large corporations, agencies or insurance companies establish relief funds, fraudsters rationalize their thefts because they believe that these large entities can absorb the costs. Since huge settlements involve numerous transactions and claims, fraudsters often hope that their actions will be lost in an enormous sea of data. The allure of a big payout can be a draw for fraudsters. Luckily, there is an answer: big data analytics.
Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

The inaugural event, under the patronage of the UAE Ministry of Economy, will gather insightful speakers to guide anti-fraud professionals into a new era of audit, fraud prevention and information technology.
Published in Press Releases

Fortune 500 companies, government agencies, small businesses and more share a collective mission during the week to spread anti-fraud education, tools and resources to their staff and communities.
Published in Press Releases

The ACFE's annual one-day event brings together anti-fraud professionals from government and law enforcement agencies.
Published in Press Releases


The ACFE's 2024 Compensation Guide for Anti-Fraud Professionals, which highlights salary and benefit differences among ACFE members, also shows continued gender diversification in the profession.
Published in Press Releases

Published in Press Releases

This annual conference brings together anti-fraud professionals from across the Asia-Pacific region for three days of discussion on the latest trends, technologies and solutions for detecting and preventing fraud.
Published in Press Releases

The world's largest gathering of anti-fraud professionals drew more than 5,800 attendees from 88 countries to the ARIA Resort and Casino in Las Vegas and online for its 2024 event.
Published in Press Releases

Whistleblowers, federal fraud fighters, an NFL legend and more will take the stage as keynote speakers at the 35th Annual ACFE Global Fraud Conference.
Published in Press Releases

Median losses of the fraud cases analyzed in this year’s report increased 24% compared to the 2022 Report to the Nations. The COVID-19 pandemic might be partly to blame.
Published in Press Releases

Published in Press Releases

The fourth annual event explores the challenges unique to women in the anti-fraud industry through idea sharing, exchanging resources and networking with industry leaders.
Published in Press Releases

The UAE Accountability Authority (UAEAA) partners with the world’s largest organization of anti-fraud professionals to host the premier educational event for fraud fighters in the Middle East.
Published in Press Releases

Global survey of anti-fraud professionals by the ACFE and SAS reveals incredible GenAI enthusiasm – but past benchmarking studies suggest a more challenging reality.
Published in Press Releases

Published in Press Releases























Published in Videos








Published in Videos



Find resources for ACFE members and others to foster diversity, equity and inclusion in the anti-fraud community and beyond.

From synthetic business identities to cybercrime to theft of services, the risks of transacting with other businesses can be significant.

Anti-fraud practitioners have a critical role to play in the future of ESG programs. Regulatory and reporting frameworks are struggling to keep up with the pace of change.

Tips are the most common way fraud schemes are detected. An effective whistleblower hotline is a vital part of a comprehensive anti-fraud program.

The Global Fraud Survey gathers meaningful information on how fraud is committed, how it is detected, who commits it and how organizations respond.

The following resources were established to aid government organizations in detecting and preventing government fraud at all levels around the world.

Since the Association of Certified Fraud Examiners began in 1988, we have produced relevant, one-of-a-kind publications dedicated to covering the latest in fraud prevention and detection.

Use these ACFE tools to help you assess fraud risk, create your own fraud response plan and find the expertise you need.

Fraud professionals can use these tools to assist organizations in identifying fraud risks and developing a fraud risk response.

Clear, credible and sound policies are the cornerstones of effective fraud prevention. Use our already developed and tested documents to guide you in crafting policies, proposals, reports and forms.

Discover our featured case studies and learn how many of today’s fraud cases are old schemes dressed in new technology with a new cast of characters.

From case studies to the latest data, find what you need to stay up to date on the latest in fraud prevention and detection with these free ACFE resources.

Shell companies can be used to commit nearly every type of fraud — from simple billing fraud schemes to complex, multi-jurisdictional money laundering operations.


If you need assistance with investigating a potential fraud or proactively protecting your organization from future frauds, a CFE is your best resource.


Strengthen fraud risk management with COSO and the ACFE's guidelines, featuring essential tools and strategies for developing effective anti-fraud programs.

We have frequently heard from our members about a desire to benchmark their organizations’ internal fraud investigation teams.

The ACFE's Fraud Risk Assessment tool is an invaluable resource for fraud examiners to use in identifying and addressing their clients' or employers' vulnerabilities to internal fraud.

Discover the latest insights on anti-fraud technologies' effectiveness in managing fraud risk, and learn how organizations are leveraging data and technology in their anti-fraud programs.

The Fraud Awareness Training Benchmarking Report highlights training's role in enhancing anti-fraud controls and policy compliance.

The ACFE’s 2022 Compensation Guide for Anti-Fraud Professionals benchmarks salary and benefits across several categories, including industry, experience, certification and many others.

Test your company’s fraud health with this free training resource featuring a checklist.

The latest fraud news, insights and ACFE member-exclusive resources delivered to your inbox.

ACFE report finds direct correlation between economic downswings and fraudulent activity

CFE members in good standing can share and promote their CFEs through custom-designed letterhead and business cards.

The ACFE Brand Guidebook, as well as the accompanying resources below, are designed to help you promote yourself and your affiliation with the ACFE.

Resources and reporting tools to use if you or someone you know has been affected by fraud.