Organizational Vulnerabilities in a Protracted Work-from-Home Scenario
By Savita Nair Jan 12, 2023
By Savita Nair Jan 12, 2023
The beginning of 2020 saw a rapid increase in COVID-19 cases. By mid-2020, the pandemic had spread at such an alarming pace, with no vaccine in sight, that governments across the globe turned to lockdowns and border closures to contain its transmission. As a result, state, business and other private institutions had to drastically alter traditional models of working. With no resumption of “ops normal” in sight, most organizations adopted a remote working culture, which has remained even after COVID-19’s containment.
The result has been the normalization of work-from-home culture. This has only grown as service professionals seek a better work-life balance, the elimination of commuting time and improved efficiency. Certain organizations were also in favor of the reduced overhead costs, with many moving to smaller offices and hotdesking arrangements in which several workers use a single workstation at different times.
This article, however, delves into the risks of such an unplanned remote working scenario and discusses why organizations must assess and mitigate the increased risk of employee fraud in the new work environment, where traditional internal controls will be ineffective.
While COVID-19 dramatically altered the face of the corporate work environment across the board, certain sectors have been more comfortable adopting a remote or hybrid work culture for the long term. Prior to the pandemic, only certain sectors like IT, accounting and technical services provided employees the flexibility for remote working. But information-sensitive sectors like banking, insurance, healthcare, education and construction had limited to no room for such arrangements. In November 2020, an analysis conducted by McKinsey’s Global Institute in the United States indicated that the finance and insurance sectors have the highest possibility and flexibility of remote working.
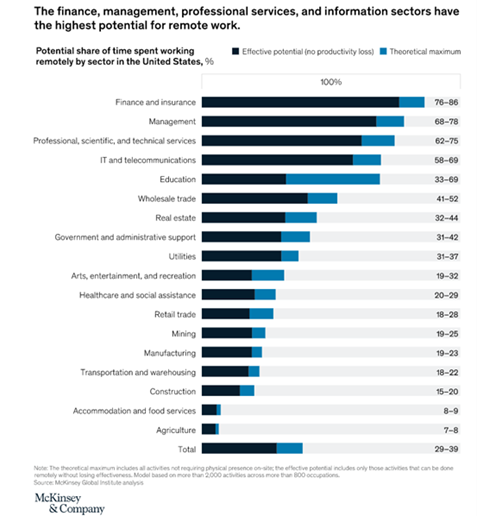
Image 1 – McKinsey’s Report on What’s next for remote work: An analysis of 2,000 tasks, 800 jobs, and nine countries, November 2020
The prolonged work-from-home practice has led corporate employees to reassess their work-life priorities, especially in the wake of mass deaths and the health scare brought on by COVID-19. Many employees relocated to their home cities to be closer to family while several others committed themselves to a dedicated health regime. A CFO survey conducted by Gartner reveals that post COVID-19, close to 50% of employees prefer remote working.
Much has been written about work-from-home or the hybrid model being the silver lining of COVID-19, as it made employees and organizations realize that much could be achieved beyond the office walls. However, as we all rejoice at the possibility of less time in traffic, more time for leisure and better work-life balance, we ought to take a step back and evaluate how this change affects the organization’s risk. When organizations plan a major shift in operations, a proper change in management protocol must be followed. This requires inputs from risk managers to ensure that the proposed changes do not compromise the safety of the organization or adversely affect its operations.
Since the remote working model was a relatively new construct for a majority of companies that made this shift during the pandemic, no such change management planning was undertaken. However, if companies are considering moving to a remote work or hybrid model on a more permanent basis, such an exercise must be initiated to discover the fault lines that can have catastrophic consequences if left unaddressed. Viewed from a fraud examiner’s lens, the shift in work environment leads to higher risk, and though these may vary in magnitude by sector and organization, the broader threats include data theft, cybercrime and occupational fraud.
Data theft is the act of stealing computer-based information from an unknowing victim with the intent of compromising privacy or obtaining confidential information. In today’s IT-heavy business environment, organizations prize data as their most valuable asset, and, consequently, traditional workplaces have built-in layers of security for data protection. As the backbone of the world economy, financial services firms have especially stringent data privacy policies and IT systems to protect confidential information. With this framework in place, most financial institutions were not in favor of remote work prior to the pandemic, as it may have involved accessing sensitive information from outside the company’s network. In the midst of the pandemic, however, these organizations had to devise workarounds for employees to access such information from their homes to avoid business interruptions.
Similarly, other sectors were forced to provide access to company and client data on unprotected public Wi-Fi or home ISPs, as well as allow the transfer of files between work and personal devices. Sharing of devices, such as laptops, routers and printers, is common in a work-from-home environment, which poses an additional threat when roommates or family members work for different organizations. Likewise, with multiple people working from home, the likelihood of co-occupants listening in on sensitive conversations increases. Companies also need to be even more conscious of data in the hands of untrustworthy employees who may intentionally misuse data to obtain ill-gotten gains. Any such breach of confidential data could lead to legal implications, loss of customer trust and reputational damage.
To address these risks, IT departments should consider augmenting security measures with the use of VPNs and require all employees to use secure home networks, create complex passwords and adjust settings on their computers to lock after short periods of no use. As an additional layer of protection, many organizations implemented multi-factor authentication and initiated annual training on data security and privacy, including consequences of a data breach. At an organizational level, all employees can be required to read and sign an acceptable use policy for electronic devices, social media and company data.
When was the last time you installed that security patch on your home computer? When did you run the last anti-virus program? When does the warranty period lapse on your home printer? Most people do not remember to diligently install and keep up with the latest security updates despite several email reminders from the IT team. As such, employees unwittingly leave the door open for cyberattacks. In addition, employees often work long and odd hours from home and may have their guards down while tackling professional and personal responsibilities simultaneously. As a result, they may be quick to fall victim to phishing, denial of service attacks, identity theft and ransomware attacks.
Organizations can test their employees by devising phishing attacks of their own to identify gullible employees who should be provided targeted training regarding malicious cyber activities. Additionally, IT departments should retain control of software updates and installations so the individual user cannot override those controls without administrative rights retained by IT. The same should be true for employees that opt for a “bring your own device policy,” which ensures company networks and systems are not put at risk by lax security protocols on an employee’s personal devices.
While data theft and cybercrime are instances of external attack, organizations face the biggest threat from unsupervised employees. Let us now examine the increased risk of fraud due to change in work environment through the lens of the Fraud Triangle, which states that “individuals are motivated to commit fraud when three elements come together: 1) some kind of perceived pressure 2) some perceived opportunity 3) some way to rationalize the fraud as not being inconsistent with one’s values.”
With the worst of the pandemic behind us, businesses have resumed operations with gusto, with competition for market share higher than ever across many industries. However, businesses are still recovering from the after-effects of the pandemic, including supply chain disruptions and loss of long-term contracts, among others. Therefore, not all organizations have been able to revert to pre-pandemic levels of performance bonuses and raises for staff.
From a macro perspective, the pent-up demand and post-pandemic successes, as well as the Russian invasion of Ukraine, have driven inflation to record highs across the world. The increased cost of living, coupled with marginal, if any, increase in salaries, creates financial pressure on employees who may be tempted to cut a few corners to get ahead of the pack.
A remote working environment opens doors to theft and fraud because physical controls, network access, IT security protocols and managerial oversight are relaxed. In this work model, companies provide employees with the ability to access confidential data and documents from home, albeit with security measures. However, these controls are not as effective as those at a physical work location where employees are deterred by CCTV cameras, private IP (Intellectual Property) addresses and close monitoring by supervisors.
COVID-19 took a toll on not only people’s health but also their pay checks. Myriads of professionals let go during the pandemic have had to take opportunities at lower salaries while others have accepted lower pay with existing employers. In addition, these employees have limited physical interaction and bonding with their teammates. As a result, interpersonal rapport and the team connection is weaker than it would have been if they had been working side-by-side at physical offices. Furthermore, physical distance that allows emotional distancing from the larger team or organization makes it easier for individual employees to rationalize wrongdoing, wherein they justify their actions as a common occurrence or as a fitting reply for being underappreciated. As mentioned earlier, the post-pandemic era continues to pose financial challenges, which makes it easier to rationalize obtaining undue financial gain when employees perceive companies to be doing well but not equitably rewarding its workers.
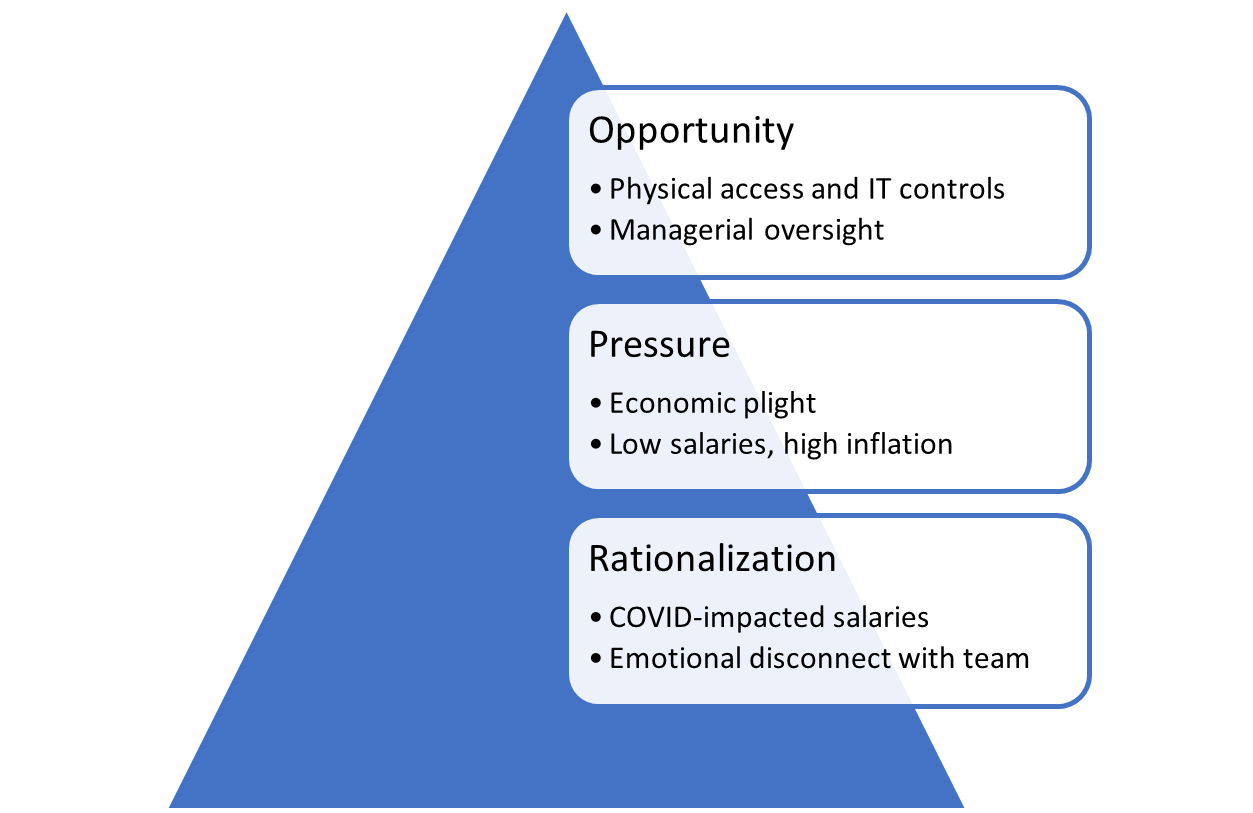
By understanding the pressures, rationalizations and opportunities that can lead to errant behavior by different levels of staff, anti-fraud professionals can devise practical measures to modify current internal controls and develop new means to mitigate the risk of fraud in a remote working environment.
In a remote working environment, managers have little oversight over how employees spend their day. Often, tasks can be completed faster, but employees may choose not to inform their superiors, who may then assign additional work to them. This phenomenon is known as time theft, where an employee receives pay for working a certain number of hours without having worked for the stated time duration.
One way to curb time theft is to eliminate the temptation by changing the Key Performance Indicators (KPIs) from time-based to achievement-based targets. Instead of setting targets by the staff’s experience level alone, managers should actively understand the strengths and weaknesses of their subordinates and set individual targets accordingly. For instance, one employee might be a whiz at Excel spreadsheets and be able to complete a data sorting task faster than another employee who is not as familiar with that software and its functions.
Companies can also consider the following measures and apply those that align with their organizational ethos:
The Cambridge Dictionary defines moonlighting as “the act of working at an extra job, especially without telling your main employer.” White-collar professionals typically will have a clause in their agreement that prohibits them from taking up other employment. In the work-from-home scenario, it is easier to run afoul of this clause and work multiple jobs from the comfort of one’s home. However, in doing so, employees risk compromising company data and client information, and they could even engage in IP theft if they work with two competing firms.
In September 2022, major IT giants in India — Wipro and Infosys — sent a stern warning to employees that moonlighting would not be tolerated, with the former even terminating employment of some 300 professionals over allegations of moonlighting. However, India’s minister of state for electronics and information technology supported the practice, declaring: “This is the age of employee-entrepreneurs and companies must now understand there has been a structural shift in the minds and attitudes of the young Indian tech workforce.” In light of such changing trends, companies must consider framing a clear policy on dual employment, specifying the terms and conditions for dual employment, if permitted.
Along with other support functions, human resources and payroll functions are also operating remotely. In larger organizations, especially in a white-collar setup, companies may have arrangements where salaries are wire transferred to employee bank accounts. In such instances, the maker-checker system is embedded within the enterprise resource planning (ERP) software or companies’ approval matrices. However, in smaller establishments, salary payments may be via cash or check. For check payments, remote working hinders the maker-checker system, allowing the person writing the check more freedom to tamper with payments. To deter such fraud schemes, companies should consider transitioning to electronic transfer of amounts to employee bank accounts, as these involve negligible costs in comparison to the high cost of fraud. Alternatively, employees in the payroll department can be asked to undertake critical tasks like making and approving salary and other high-value payments from the confines of the office. This is especially applicable when the workforce does not utilize an ERP platform for human resources or finance functions.
Similarly, those in human resources have a higher chance of colluding with placement agencies that assist with identification of candidates, especially when their conversations are occurring outside the office and not within earshot of colleagues. To prevent such instances of fraud, companies can consider routine remote monitoring of their emails, wherein forensic data analyses are undertaken to identify suspicious communications. Likewise, it is advised to prohibit employees from communicating with external vendors outside the company’s authorized communication systems, which can be monitored. These measures will, at the least, make employees fear that their misconduct may be discovered and, in turn, may act as a deterrent.
Remote working was an unplanned detour for most organizations, but this phenomenon is here to stay. Therefore, organizations must evaluate the vulnerabilities of this model and empower staff with training and tools to effectively thwart the threats of cybercrime and data theft. Companies must also recognize the pressures and opportunities this work environment presents to employees and alter oversight measures, as well as develop an atmosphere wherein it is difficult for employees to rationalize a deviation from the company ethos. The aim should be to consider this a change management project in reverse, wherein risk mapping and mitigation needs to be undertaken post-implementation.
Savita Nair is a Managing Director in J.S. Held’s Global Investigations Practice. She has led multiple advisory engagements for Fortune 500, private equity, and law firms related to business intelligence, corporate investigations, and litigation support in Asia Pacific and North America. Based in Mumbai, she provides clients with services such as risk consulting, project management, strategic advisory, and organizational development. She is a Certified Public Accountant (inactive), Certified Fraud Examiner, and a Certified Anti-Money Laundering Specialist.
Vrinda Thakore is an Associate in J.S. Held’s Global Investigations Practice in South Asia. Based in Mumbai, Vrinda has experience in fraud and corporate investigations, due diligence, business intelligence, data analysis and process reviews across various sectors. Prior to joining J.S. Held, Vrinda was associated with Indian accounting firms, where her primary focus was fraud and corporate investigations, and matters involving whistle-blower complaints. She has also managed forensic audits and investigations.