Fraud Resources
Curated and created for anti-fraud professionals, find the latest news, trends, analysis, topics and reports in these ACFE resources.

The ACFE and Grant Thornton partnered to create this report highlighting a changing landscape of fraud risks and technologies and how organizations can build, mature and enhance their fraud risk management programs for the future.

Understand how your compensation and benefits compare to your colleagues, including those who have earned the Certified Fraud Examiner (CFE) credential, to help you better plan for the future and advance your career.

To provide best-practices guidance for assessing and managing fraud risks, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) partnered with the Association of Certified Fraud Examiners (ACFE) to create the Fraud Risk Management Guide.

Fraud Magazine is a digital publication delivering timely and insightful information on the latest trends, tools and techniques in the anti-fraud profession.

Find news, analysis and commentary on the global fight against fraud on the ACFE’s official blog. Features insight from ACFE staff and experts in the fields of digital forensics, fraud risk management, compliance and more.

A free, bimonthly e-newsletter highlighting anti-fraud news and analysis, as well as the latest ACFE events and updates.

In this episode of Fraud Talk, ACFE Research Specialist Sam May interviews Patrick Gushue, Acting Director of the Department of Justice's Corporate Whistleblower Awards pilot program. Together, they delve into the program's mission to uncover corporate crime by empowering whistleblowers and fostering a culture of accountability. Patrick provides an in-depth look at the program's focus on internal reporting, compliance frameworks and innovative incentives designed to encourage reporting of misconduct.
Published in Podcasts

Join ACFE Public Information Specialist Stefanie Hallgren in this episode of Fraud Talk, as she dives in with Brandi Pritchard, Assistant Director of Special Investigations at the Washington State Auditor's Office. With International Fraud Awareness Week on the horizon, Pritchard shares the story behind the Auditor’s Office’s dedication to fraud prevention and the unique challenges they face, especially within smaller government entities. From engaging tactics that bring fraud awareness to the community to the “trust but verify” approach that underscores their work, Pritchard reveals how Fraud Week creates a ripple effect inspiring both vigilance and accountability.
Published in Podcasts

In this episode of Fraud Talk, Mason Wilder sits down with Marta Cadavid, founder of NoFraudLatin, to explore the unique challenges of detecting and preventing fraud in Latin America. Cadavid shares her journey, including the creation of a Latin American-specific fraud tree, and how cultural nuances shape the approach to fraud communication. They discuss the vital role of artificial intelligence in analyzing human behavior and predicting fraudulent actions.
Published in Podcasts

Mary Ann Miller, a seasoned cybersecurity and fraud expert, joins Rihonna Scoggins, ACFE Content Manager, on Fraud Talk to dissect the evolving threat landscape of identity fraud and the cutting-edge strategies organizations can deploy to combat it. Miller emphasizes the need to move beyond traditional identity validation methods, focusing instead on diverse attributes and signals to confirm authenticity. They explore the future of passwordless security, highlighting its potential to enhance both security and user experience.
Published in Podcasts

Amanda Holden, a partner with Deloitte's Financial Crimes, joins Samuel May, ACFE research specialist, on Fraud Talk to uncover the intricacies of fraud prevention and program integrity in the Canadian public sector. They navigate the crucial role of proactive prevention and detection, addressing the unique challenges faced by public entities in a rapidly evolving fraud landscape. Holden explores the essential COSO framework, emphasizing the balance between expediency and robust fraud controls. Dive into Holdens’s expert insights on breaking down cultural barriers, enhancing information sharing and leveraging cutting-edge data analytics and technology.
Published in Podcasts

Javier Leiva, a writer, investigative journalist, producer and podcaster, joins Jason Zirkle, ACFE Training Director, on Fraud Talk to discuss the use of OSINT in investigations. They delve into the challenges, ethical considerations and future of OSINT investigations. Listen in as Leiva shares insights and tips for leveraging OSINT effectively and responsibly, and delves into the myth of Frank Abagnale.
Published in Podcasts

In this episode of Fraud Talk, Tony McClements, Head of Investigations at Martin Kenny & Co., delves into the infamous U.K. Post Office scandal with ACFE Content Manager, Rihonna Scoggins. As McClements unravels the layers of this miscarriage of justice, he discusses the critical failures of the Horizon IT system and the damaging effects of withheld disclosures during legal proceedings.
Published in Podcasts

In this episode of Fraud Talk, Andi McNeal, ACFE Chief Training Officer, and ACFE Research Director, Mason Wilder, delve into the critical insights of Occupational Fraud 2024: A Report to the Nations, discussing its evolution, consistent themes and groundbreaking findings. They explore the significance of tips and internal controls in detecting fraud, the increased median losses attributed to the COVID-19 pandemic and the shift towards web-based reporting mechanisms. Concluding with actionable advice, the episode underscores the value of the report in enhancing anti-fraud programs and heightening fraud awareness within organizations.
Published in Podcasts

In this episode of Fraud Talk, ACFE Content Manager Rihonna Scoggins, sits down with Amii Barnard-Bahn, an acclaimed coach for legal and compliance executives, to dissect the nuances of navigating difficult conversations as anti-fraud professionals. Barnard-Bahn outlines a six-step strategy to not only prepare the messenger but also to prime the audience, ensuring a blend of empathy and clarity. From psychological readiness to the rehearsal of delivery and understanding the influence of gender dynamics, this episode is packed with insights.
Published in Podcasts

In this episode of Fraud Talk, ACFE Content Manager Rihonna Scoggins meets with Christian Focacci, CEO and Founder of Threat Digital, to discuss the future of risk management and compliance software. The discussion delves into the groundbreaking advancements in large language models, their role in processing unstructured text and the critical importance of explainability in AI-driven solutions. Focacci also addresses the issue of AI washing and offers practical advice for companies and fraud examiners on integrating AI to optimize processes.
Published in Podcasts

In this special edition of Fraud Talk, we focus on the ACFE's annual round-up featured in Fraud Magazine, a highlight anticipated by many in the industry. This year, we offer you an exclusive behind-the-scenes glimpse into the process of selecting the top five most scandalous frauds of 2023. Join John Warren, CEO of the ACFE, and Jennifer Liebman, Assistant Editor of Fraud Magazine, as they meticulously unravel each case, providing an in-depth analysis and insight into the complexities and implications of these notable frauds.
Published in Podcasts

In this episode of Fraud Talk, ACFE Communications Director John Duffley welcomes back forensic accountant and consultant Chris Ekimoff, CFE, CPA, for a conversation on career development, personal branding and professional visibility in the anti-fraud field. Drawing on his experience as a practitioner, educator and speaker, Ekimoff shares practical advice on using social media authentically, evaluating opportunities, balancing general expertise with specialization and building meaningful professional relationships both online and in person. Their discussion also explores consulting, managing client expectations, storytelling as a critical skill, and why “dedicate, don’t dabble” is key to long-term growth and impact.
Published in Podcasts

In this episode of Fraud Talk, Fraud Magazine Editor-in-Chief Jen Liebman, CFE, is joined by ACFE President and CEO John Warren, J.D., CFE, to break down the most scandalous frauds of 2025 and what they reveal about today’s global fraud landscape. The discussion explores a series of sprawling international schemes, from what may be the largest Medicare fraud in U.S. history to cyber scam operations tied to human trafficking, pig butchering cryptocurrency scams, government corruption that destabilized a national economy and a state-sponsored crypto hack linked to North Korea. Along the way, they examine the growing scale and sophistication of transnational fraud, the human consequences behind the headlines and the critical role anti-fraud professionals play in confronting increasingly complex financial crime.
Published in Podcasts





In this episode, ACFE Community Manager Rihonna Scoggins reads a case study submitted by Eduardo “Ed” Cuyos. The case study follows Ed's investigation into fraudulent activities previously missed by the Defense Criminal Investigative Service (DCIS) and the Department of Defense Inspector General (DODIG).
Published in Podcasts

International Fraud Awareness Week provides space to highlight fraud prevention and detection initiatives at companies around the world. Thousands of groups have pledged as Supporting Organizations over the past 22 years, with more doing their part ahead of Fraud Week 2022, held on November 13-19. Bruce Dorris, President and CEO at the ACFE, sits down with John Duffley, the ACFE’s Communications Manager, to discuss how you can participate in Fraud Week, the annual ACFE Board of Regents voting cycle, and what lies ahead as the ACFE enters its 35th year.
Published in Podcasts

In Episode 125 of Fraud Talk, ACFE Training Director Jason Zirkle, CFE, is joined by military veterans from around the world to share their backgrounds and how their experiences have aided them in their roles as CFEs and anti-fraud professionals. Collins Wanderi, CFE, Bill Stakes, CFE, and Monica Meeks, CFE, discuss the tools they’ve gained and advice they offer to veterans and active-duty military members looking to earn their CFE credential.
Published in Podcasts

Eddie Antar founded the Crazy Eddie electronics retail chain in Brooklyn, New York, which rose to prominence across the New York-New Jersey area throughout the 1970s. Operating undetected for years, Eddie’s business practices were grounded in fraud from the very beginning. In Episode 124 of Fraud Talk, Gary Weiss, author of “Retail Gangster: The Insane, Real-Life Story of Crazy Eddie,” discusses this wide-ranging fraud case and ultimate unraveling with ACFE Chief Training Officer John Gill, J.D., CFE.
Published in Podcasts

In the fight against fraud, it can be hard to remember why we do it, especially when the fraudsters never seem to quit. Associate professor of accounting, taxation and business law at SUNY Old Westbury, Dr. David Glodstein, began the Justice for Fraud Victims Project to teach his students — and remind fraud examiners — who we're fighting for: the victims. In this episode, join Dr. Glodstein, CFE, and Kate Pospisil, CFE, the Communications Specialist at the ACFE, as they discuss the Justice for Fraud Victims Project, why programs like this matter and what we can do to further the fight for justice.
Published in Podcasts

The intersection of cyber security and fraud examination is ever-expanding in our new technological landscape. At the 33rd Annual ACFE Global Fraud Conference, ACFE Research Manager Mason Wilder, CFE, and Deputy Superintendent and Director of the Intelligence Unit at the New York Department of Financial Services (NYDFS), Roderick Chambers sat down to discuss the importance of technical controls and knowledge to protect your organization from fraud.
Published in Podcasts

Washington State’s Largest Ponzi Scheme was the catalyst for Tod McDonald, CPA to start his company and push for innovation in financial e-discovery. Years later, he and Garth Leonard, CFE, from Valid8 Financial, join ACFE Community Manager Rihonna Scoggins to explore the current resources at hand to combat fraud and how fraud examiners can assess what tools are the right fit for them in this evolving landscape.
Published in Podcasts

William Shakespeare is widely considered to be one of the most prolific and influential writers of all time. But one group of individuals, who call themselves “Oxfordians” and their theory the "Shakespeare Authorship Question," falsely claim that what we know to be Shakespeare's plays and poetry were actually penned by someone else. In this episode, ACFE Chief Training Officer John Gill, J.D., CFE, joins Michael Pocalyko, CFE, the CEO of SI, as they look at how the qualities of those claiming to disprove Shakespeare's authorship parallel the character of financial and investment fraudsters.
Published in Podcasts

While victims of traditional identity theft often catch it quickly, victims of medical identity theft may not know they are victims until they need critical medical treatment. In this episode, Scott Ward, CFE, senior vice president at Qlarant, discusses the insidious nature of medical identity theft, the impact it has on its victims and what people and governments can do to help combat it.
Published in Podcasts

In this episode, Jim Ducharme, COO of Outseer, a leading technology company in the fight against payment fraud, talks about the rise of "Buy Now, Pay Later" services and how fraudsters are exploiting these new avenues of credit. He also discusses identity assurance and how companies are working to combat payment fraud without adding hurdles for consumers.
Published in Podcasts

In this episode, Larry Nielsen, a detective who has spent the last several years teaching himself about cryptocurrencies, shares advice for fraud examiners who are interested in expanding their toolkits to accommodate cryptocurrency investigations. He also discusses some of his experiences tracing cryptocurrencies in both a law enforcement capacity and as a consultant.
Published in Podcasts

In this episode, renowned tech journalist and podcast host Takara Small discusses what the future of data breaches, cybercrime and cryptocurrency might look like for both individuals and organizations. She also speaks about the role online media plays in exposing fraud and the importance of supporting women, BIPOC and young people breaking into the tech space.
Published in Podcasts

In this episode of Fraud Talk, ACFE Communications Director John Duffley sits down with Heather Vescent, a futurist, researcher and CEO of The Purple Tornado, to explore how strategic foresight can empower anti-fraud professionals to anticipate emerging threats and adapt to rapid technological change. The conversation covers the evolving role of AI in fraud detection, the importance of human intuition alongside automation, and the promise and challenges of new technologies such as decentralized identity. Vescent shares practical insights on blending technology and human expertise to build resilient, future-ready anti-fraud programs.
Published in Podcasts

In this episode of Fraud Talk, we explore an often-overlooked risk factor inside organizations: boredom. Guest Garth Sheriff, CFE, CPA, educator and former actor, joins ACFE Content Manager Rihonna Scoggins to examine how disengagement in ethics training and workplace culture can quietly open the door to fraud. Sheriff draws on his unique background in accounting, acting and continuing education to show why storytelling and lived experience matter more than checklists when it comes to ethics.
Published in Podcasts

In this episode of Fraud Talk, ACFE Content Manager Rihonna Scoggins speaks with David Maimon, a leading cyber crime and dark web researcher, to explore how the fraud landscape is being shaped by technology and organized criminal networks. Maimon shares how his work monitoring dark web activity uncovers trends like the use of AI in fraud, the rise of synthetic identities and the exploitation of death row inmates' information. He breaks down the fraud ecosystem, explains how public data can fuel identity theft and highlights red flags that can help fraud teams spot synthetic profiles.
Published in Podcasts

In this episode of Fraud Talk, ACFE Content Manager Rihonna Scoggins speaks with Shai Gabay, CEO and co-founder of TrustMi, to explore how fraudsters are capitalizing on overworked teams, rushed vendor payments and internal blind spots to execute sophisticated B2B payment scams. From AI-assisted impersonation to social engineering tactics that prey on urgency, Gabay breaks down the fraud risks hiding in plain sight and what organizations can do to stay ahead without slowing down.
Published in Podcasts

In this episode of Fraud Talk, ACFE Communications Director John Duffley speaks with Jim McConnell, CFE, about the growing threat of applicant fraud and hiring scams. With job seekers under increasing pressure, scammers exploit emotions and new technologies to steal personal information, impersonate companies and damage employer brands. McConnell breaks down the red flags of fraudulent recruiters, the rise of comment poisoning on platforms like LinkedIn, and how CFEs and HR teams can work together to spot and stop this emerging threat.
Published in Podcasts

In this episode of Fraud Talk, ACFE Content Manager Rihonna Scoggins interviews Fraud Magazine Assistant Editor Crystal Zuzek, co-author of "Under Pressure". They explore the rising fraud risks facing Gen Z and millennials, both as victims and as perpetrators. From emotionally manipulative scams like sextortion to friendly fraud and the glamorization of con artists, Zuzek shares insight and real stories that reveal how digital lifestyles and economic pressures are shaping the next generation.
Published in Podcasts

Whistleblowers are often key to uncovering fraud—but what happens after they report? In this episode of Fraud Talk, Jacqueline Garrick, founder of Whistleblowers of America and the Workplace Promise Institute, shares her journey from whistleblower to advocate. From moral injury to PTSD, Garrick shares how peer support and trauma-informed workplaces can protect whistleblowers and strengthen fraud prevention efforts.
Published in Podcasts

In this episode of Fraud Talk, ACFE Content Manager Rihonna Scoggins speaks with Victor Cardona, adjunct professor of forensic accounting at California State Polytechnic University, Pomona, to discuss their “Day in the Life of an IRS Agent” program. The initiative immerses students in real-world forensic accounting and criminal investigation scenarios, offering a hands-on look at careers in fraud prevention and compliance. Cardona shares how interactive education, mentorship and networking are key to inspiring the next generation of anti-fraud professionals—and why promoting ethical standards early on is essential in shaping the future workforce.
Published in Podcasts

In this episode of Fraud Talk, ACFE Communications Director John Duffley sits down with Mason Wilder, CFE, ACFE Research Director, to break down the newly released In-House Fraud Investigation Teams: 2025 Benchmarking Report. Dive into a detailed discussion on how organizations are structuring their fraud teams—from the increasing number of investigators to the unique challenges they face across different company sizes. Learn about the role of in-house teams, the evolving skill sets required in today’s complex fraud landscape and the critical balance between case volume and team efficiency.
Published in Podcasts

Artificial intelligence (AI) is revolutionizing fraud prevention in the banking industry, enhancing detection and risk management. But with these advancements come new challenges—fraudsters using AI to exploit vulnerabilities, biases in algorithms and the need for regulatory adaptation. In this episode, ACFE Content Manager Rihonna Scoggins speaks with fraud expert Kennedy Meda about the impact of AI on banking fraud, the balance between automation and human oversight and how financial institutions can stay ahead of emerging threats.
Published in Podcasts

In this episode of Fraud Talk, John Warren, J.D., CFE, CEO of the ACFE, and Jennifer Liebman, CFE, Editor-in-Chief of Fraud Magazine, delve into some of 2024's most scandalous fraud cases. From Boeing's guilty plea tied to deadly aviation crashes to Vietnam's sentencing of a real estate tycoon to death for embezzlement, they explore the global implications of these high-profile frauds. Tune in to understand the evolving nature of fraud, including the role of AI and platforms like TikTok in modern schemes, and uncover critical lessons for prevention and compliance.
Published in Podcasts



Published in Podcasts










Belinda Kitos, CFE, CICA and president of SCF Inc., was elected as treasurer of her homeowners association, but when she opened the books she discovered a $1.2 million fraud in her own backyard. In this month's episode of Fraud Talk, Kitos and Jason Zirkle, training director of the ACFE, explore their own experiences investigating HOA fraud and the red flags of these schemes.
Published in Podcasts

The National Heath Care Anti-Fraud Association (NHCAA) estimates conservatively that healthcare fraud costs the U.S. approximately $68 billion annually. Why is there so much fraud and abuse with insurance claims and why has this problem gone on so long? In this month's episode of Fraud Talk, Paul Kilby, Editor in Chief of Fraud Magazine, discusses the role of artificial intelligence (AI) in combatting healthcare fraud with Theja Birur, Chief Technology Officer and founder of 4L Data Intelligence.
Published in Podcasts
.png)
In this haunting episode of Fraud Talk, investigate the ghostly disappearance of Phases, Inc., a Tennessee nonprofit dedicated to helping women with substance abuse issues. Tune in with Michael Booher, CFE, CPA, from the Tennessee Comptroller of the Treasury and Rihonna Scoggins, ACFE Community Manager, to discover how this ghost story unfolds and the truths lurking in Phases, Inc.'s shadows.
Published in Podcasts

"We've been trying to reach you about your car's extended warranty" is an all-too-common robocall scam aiming to bilk victims out of their money. Alex Quilici, CEO of YouMail, discusses the intricacies of robocalls, what differentiates beneficial robocalls from scams and the regulations that both aid and obstruct the fight against these schemes with Jennifer Liebman, CFE, assistant editor of Fraud Magazine, in the latest episode of Fraud Talk.
Published in Podcasts

Tom Cronkright, the lead witness in the FBI's indictment of Black Axe, an international cybercrime syndicate based out of Nigeria, speaks with ACFE President John Gill, J.D., CFE, in this month's episode of Fraud Talk. As the co-founder of CertifID and CEO of a title agency, Tom has been at the forefront of helping the real estate industry address payments fraud and discusses his experience as a victim of fraud and the operations of the international fraud group he helped indict.
Published in Podcasts

In this month's episode of Fraud Talk, ACFE Chief Training Officer John Gill, CFE, meets with attorney David Fleck, Esq., who represents victims of business, real estate and investment fraud in lawsuits to recover their money, property and dignity. They discuss trends in real estate fraud including investment fraud, title theft and deed fraud, mortgage fraud and wire transfer fraud.
Published in Podcasts

In Episode 133 of Fraud Talk, Editor in Chief of Fraud Magazine Paul Kilby speaks with Kathryn Westmore, the Senior Research Fellow for the Center for Financial Crime and Security Studies at the Royal United Services Institute, a military and defense think tank in the U.K. Kathryn discusses the increase in fraud in the U.K., government initiatives and the balance between data sharing and data privacy.
Published in Podcasts

In Episode 132 of Fraud Talk, ACFE Research Specialist Sam May meets with Rob Sand, the Iowa State Auditor. Rob speaks about the Hot Lotto fraud scandal he prosecuted, totaling more than $25 million, as well as helping the state of Iowa improve their systems and processes to better investigate and audit potential frauds.
Published in Podcasts

In Episode 131 of Fraud Talk, Tyler Hatcher, Special Agent in Charge of the Los Angeles field office of the Internal Revenue Service's Criminal Investigation division, joins ACFE Communications Manager John Duffley. Tyler reflects on the IRS-CI division's growth during his 21 years, the process behind evaluating allegations and pursuing criminal cases, growing uses of cryptocurrencies, common tax fraud schemes, the impacts of the CARES Act and Inflation Reduction Act, and much more.
Published in Podcasts

In this episode, Jenny Radcliffe, aka "The People Hacker," discusses her expertise as an ethical social engineer, honing those skills at an early age on the streets of Liverpool, and unique challenges she has faced over the years. Joining ACFE Community Manager Rihonna Scoggins during Women's History Month, Jenny explains how being a woman in her field and gender biases she has observed played a significant role in understanding the "human element" behind social engineering. Her new book "People Hacker: Confessions of a Burglar for Hire" is available now in the U.K.
Published in Podcasts

In Episode 129 of Fraud Talk, Tony McClements, the Head of Investigations at Martin Kenney & Co., discusses his career trajectory through three decades in law enforcement to the private practice cases he oversees today. Joining ACFE Communications Manager John Duffley, Tony outlines the challenges between both types of investigations, the benefits to building a team of young, up-and-coming investigators, and emerging technologies and data reports that can be utilized for complex cases.
Published in Podcasts

In this episode, the ACFE's Chief Training Officer John Gill sat down with Charles Antonucci, the former president of The Park Avenue Bank, who was convicted in 2015 of trying to defraud the Troubled Asset Relief Program (TARP). Antonucci also pleaded guilty to other charges including self-dealing, bribery, embezzlement of bank funds, and a multi-million fraud scheme involving an insurance company.
*The ACFE does not compensate convicted fraudsters.
Published in Podcasts

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives
.png)


Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives




Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives


Published in Fraud Examiner Archives



While DeFi might hold a lot of promise for proponents of cryptocurrency and whatever Web 3.0 becomes, these large-scale losses show that the platforms and apps feature several serious, exploitable fraud risks.
Published in Fraud Examiner Archives

Similar to the overconfidence bias, illusory superiority is described as when you overestimate your own abilities when compared to others. Confidence is an important trait for fraud examiners, but too much of it can lead to mistakes in investigations — and illusory superiority can contribute to overconfidence in imperceptible ways.
Published in Fraud Examiner Archives

In nearly every state, guardians are considered fiduciaries. As such, they have a duty to act in their clients’ best financial interests. Sadly, that’s not always the case.
Published in Fraud Examiner Archives

While STRs may be a lucrative opportunity for many, they are not without fraudsters targeting them as well.
Published in Fraud Examiner Archives

Consumers should be wary of any QR code provided by an unknown source; such codes should be treated like unknown hyperlinks.
Published in Fraud Examiner Archives

Corporate leaders are faced with a moral dilemma, weighing the financial interests of their stakeholders against the public interest in unifying against the violent invasion of a sovereign nation. Further complicating the situation, some corporate leaders must also determine whether to cut ties with their own employees based in Russia — employees with families to feed and support.
Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

On July 15, a South Korean treasure hunting company called the Shinil Group claimed it found the wreck of a Russian warship, the Dmitrii Donskoi. The ship sank east of the Korean Peninsula more than 100 years prior during a 1905 battle with the Japanese while carrying a cargo of 200 tons of gold bullion, according to Shinil’s claim.
Published in Fraud Examiner Archives

When large corporations, agencies or insurance companies establish relief funds, fraudsters rationalize their thefts because they believe that these large entities can absorb the costs. Since huge settlements involve numerous transactions and claims, fraudsters often hope that their actions will be lost in an enormous sea of data. The allure of a big payout can be a draw for fraudsters. Luckily, there is an answer: big data analytics.
Published in Fraud Examiner Archives

Published in Fraud Examiner Archives

Explore the Anti-Fraud Blueprint, developed in partnership with Grant Thornton, and learn how the step-by-step framework can help organizations build, assess and mature their fraud risk management programs.
Published in ACFE Insights Blog

Behind every credential, case and conference is a community built on integrity and connection. Hear from ACFE staff on what makes fraud fighters so special.
Published in ACFE Insights Blog

Lulling is deceptive technique that creates false reassurance and keeps victims engaged. In this blog, explore how fraud examiners can effectively recognize, unravel and document these schemes.
Published in ACFE Insights Blog

This blog examines how organizations can effectively plan investigations while remaining compliant with the DPDP Act 2023 and the DPDP Rules 2025, empowering investigators to adapt confidently to the evolving legal landscape.
Published in ACFE Insights Blog

In this blog, ACFE Training Director Jason Zirkle, CFE, shares practical tips on spotting potential scams and identity theft threats, explains why filing taxes early reduces your fraud risk and offers other advice to help you avoid becoming a victim.
Published in ACFE Insights Blog

Explore the current state of whistleblowing in Mexico, international best practices, and the necessary steps to build a more robust and protective environment for those who expose wrongdoing in the private sector.
Published in ACFE Insights Blog

Payroll fraud involving false overtime claims causes significant financial losses for organizations, with average losses increasing over recent years. Discover how this issue affects various sectors globally and the strong preventive measures it requires to combat it.
Published in ACFE Insights Blog

While sextortion was once viewed as a form of cyber harassment, it has evolved into a structured financial crime ecosystem. Discover how financial institutions can leverage FinCEN guidance and behavioral analytics to detect patterns and protect at-risk populations.
Published in ACFE Insights Blog

While hospice care provides essential comfort and care to patients at the end of life, the industry faces risks from for-profit exploitation and deceptive practices. Explore common hospice fraud schemes and the efforts required to protect those most vulnerable.
Published in ACFE Insights Blog

David Rodriguez, CFE, CPA, CIA combined multiple study techniques to pass the 90-Day CFE Exam Challenge. Here he outlines how he succeeded using the challenge group, different study methods and support from others in the ACFE Community.
Published in ACFE Insights Blog

Reuters recently reported that more than half a dozen British banks were in advanced talks with law enforcement and government agencies over plans to systematically share intelligence on major financial crimes such as money laundering and terrorism financing.
Published in ACFE Insights Blog

Today brings both sadness and joy as the Association of Certified Fraud Examiners bids farewell to outgoing President and CEO Bruce Dorris, who leaves the ACFE to take some time for himself and his family before beginning the next chapter of his career.
Published in ACFE Insights Blog

Artificial intelligence (AI) itself is not inherently fraudulent. AI is a field of computer science that focuses on the development of computer systems that can perform tasks that typically require human-like intelligence, such as learning, problem solving and decision making.
Published in ACFE Insights Blog

Like any tool, AI can be wielded for malicious purposes. Fraudsters are increasingly leveraging AI to enhance the efficiency and sophistication of their scams.
Published in ACFE Insights Blog

According to the Antwerp World Diamond Center (AWDC), about 1,700 companies and 4,500 traders concentrated in an area of about one square kilometer trade 84% of all rough diamonds worldwide.
Published in ACFE Insights Blog

The Ritchie-Jennings Memorial Scholarship provides an opportunity for students to advance their education and anti-fraud career paths. Additionally, it supports their anti-fraud interests by providing a full year of ACFE membership. Award amounts are $10,000, $7,500, $5,000 and $2,000 and are paid directly to the recipient’s university or college.
Published in ACFE Insights Blog

Multi-level marketing (MLM) companies have been around for decades, but they have recently gained popularity in the health and wellness industry. You’ve seen these companies promoting on social media, like the ubiquitous “Hey hun!” in your Facebook Messenger, or perhaps even approaching you in public squares and asking to join their “exclusive” club, buy their product or join their workout group.
Published in ACFE Insights Blog

This blog serves as part two in a three-part series on Benford’s Law.
Published in ACFE Insights Blog

Conventional wisdom suggests that each digit has an equal chance of being the first digit, but Benford's law shows that lower numerals always have a greater chance at being the leading digit compared to higher numerals.
Published in ACFE Insights Blog

When investigating fraudulent activity as it relates to letters of credit, red flags are important to explore during the preliminary investigation to identify money laundering.
Published in ACFE Insights Blog

Medicare fraud poses a significant threat to the integrity and sustainability of the Medicare program. A recent and troubling Medicare fraud case in Florida involved nurse practitioner Elizabeth Hernandez, who was convicted of fraudulently billing over $200 million for unnecessary orthotic braces and genetic testing.
Published in ACFE Insights Blog

The name Frank Abagnale Jr. is synonymous with check fraud and counterfeiting. His story, which was popularized in the 2002 film "Catch Me If You Can," starred Leonardo DiCaprio as the master imposter himself. Though times have changed nearly 60 years later, Abagnale's schemes serve as a warning to banks and businesses to be on high alert for check fraud.
Published in ACFE Insights Blog

A new phishing scam preying on Best Buy customers is making the rounds. The fraudulent email claims to be from Best Buy's tech support team Geek Squad and tricks users into giving away personal information. Do not take the bait — this is what you need to know to avoid becoming a victim.
Published in ACFE Insights Blog
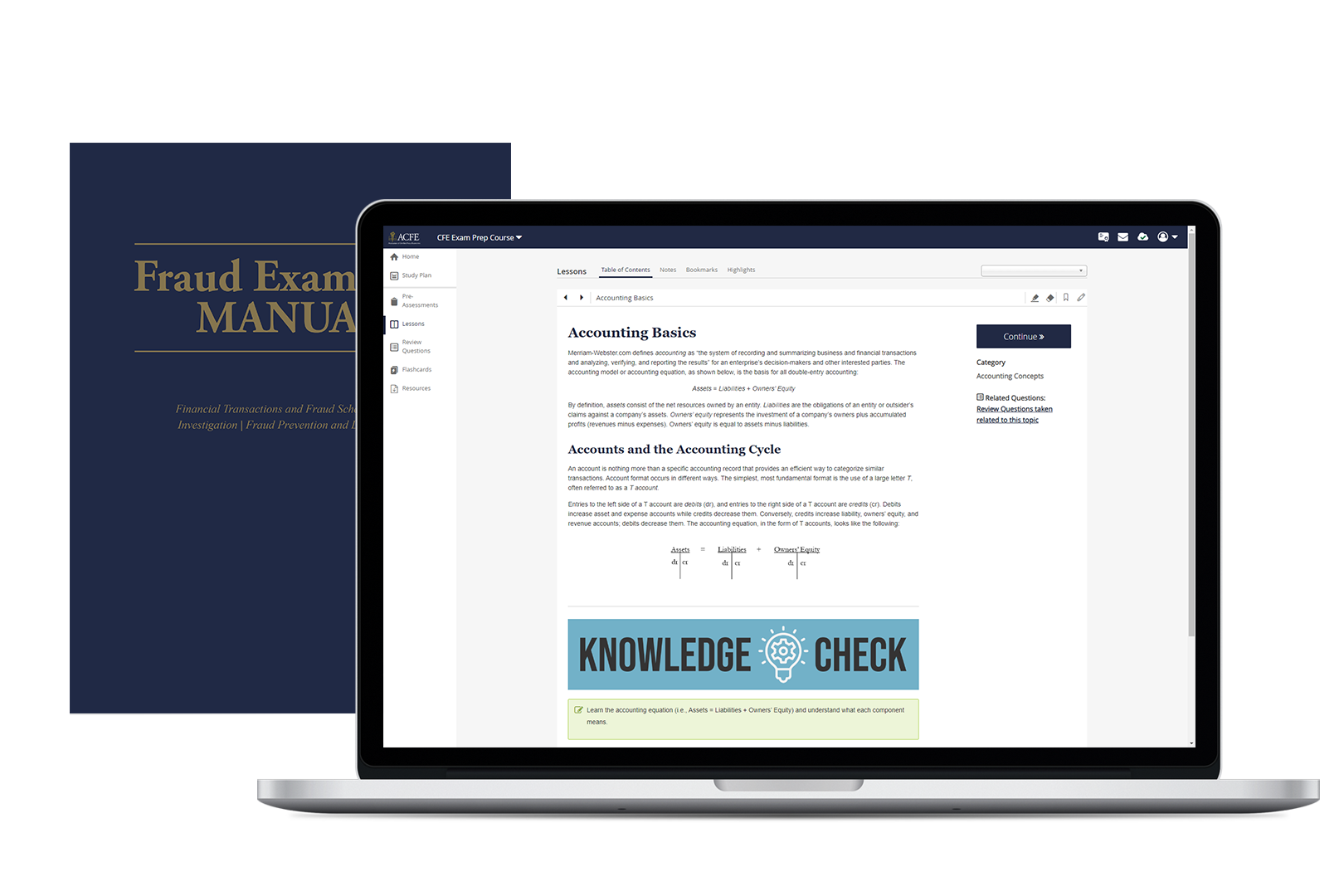
This new update to the CFE Exam Prep Course makes studying for your CFE Exam an easier process with integrated lessons and Knowledge Checks to ensure you are gaining the most from your study time.
Published in ACFE Insights Blog

In the ever-evolving landscape of fraud, staying informed about emerging trends is not just a choice — it is a necessity. As professionals in the field of fraud prevention, we understand that knowledge is our most potent weapon against the ever-adaptive tactics of fraudsters.
Published in ACFE Insights Blog

Engaging in clickbait quizzes could lead to providing hackers with enough information to bypass common security protocols on your personal accounts.
Published in ACFE Insights Blog

Fraud is a pervasive issue that affects businesses, organizations and individuals across various industries. Often, an organization is surprised to find itself a victim of fraud, especially when the perpetrator is a trusted employee. According to the Association of Certified Fraud Examiners Occupational Fraud 2022: A Report to the Nations, organizations lose approximately five percent of revenue to fraud each year with the average loss per case totaling more than $1.78 million.
Published in ACFE Insights Blog

Anna Sorokin, the so-called “fake German heiress” (perhaps better known by her alias Anna Delvey), came dangerously close to duping a hedge fund out of $25 million. According to The New York Times, she intended to defraud the financial institution by creating fake bank statements in Adobe Photoshop, a task that she said took “surprisingly little time.”
Published in ACFE Insights Blog

Federal law does not explicitly criminalize falsifying business records, but the act is criminalized under several federal regulations.
Published in ACFE Insights Blog

According to the Wiley Online Library, “Financial literacy is the ability to use knowledge and skills to manage financial resources effectively for a lifetime of financial well-being." Sounds pretty useful, right? But how do we learn financial literacy? And when should we start?
Published in ACFE Insights Blog

Despite strict regulations in India, drug diversion to the normal market remains a persistent problem, compromising patient safety and industry credibility.
Published in ACFE Insights Blog

Indigenous peoples around the world face marginalization and exploitation, leading to increased vulnerability. This puts them at a particular risk for fraud, as opportunistic fraudsters take advantage of systemic inequalities. Fraud against indigenous communities is especially harmful due to the unique challenges these groups face.
Published in ACFE Insights Blog

While NFTs offer numerous benefits, such as increased security and unique ownership, they also present new fraud risks. Understanding these risks and how to mitigate them is essential for organizations that are considering investing in NFTs.
Published in ACFE Insights Blog

Mason Wilder, the Research Manager at the Association of Certified Fraud Examiners (ACFE), sat down with Steve Dawson, CFE, CPA, and James Rumph, CFE, CIA, CPA, for a virtual webinar hosted by the ACFE and The Institute of Internal Auditors (The IIA).
Published in ACFE Insights Blog

In this episode of Fraud Talk, the ACFE's Chief Training Officer John Gill sat down with Charles Antonucci, the former president of The Park Avenue Bank, who was convicted in 2015 of trying to defraud the Troubled Asset Relief Program (TARP). Antonucci also pleaded guilty to other charges including self-dealing, bribery, embezzlement of bank funds, and a multi-million fraud scheme involving an insurance company. The ACFE does not compensate convicted fraudsters.
Published in ACFE Insights Blog

In this episode, Jenny Radcliffe, aka "The People Hacker," discusses her expertise as an ethical social engineer, honing those skills at an early age on the streets of Liverpool, and unique challenges she has faced over the years. Joining ACFE Community Manager Rihonna Scoggins during Women's History Month, Jenny explains how being a woman in her field and gender biases she has observed played a significant role in understanding the "human element" behind social engineering
Published in ACFE Insights Blog

With addiction being the most severe form of substance use disorder (SUD), symptoms can range from moderate to severe. In 2021, drug abuse was added to the list of high-risk situations by the Government Accountability Office (GAO). GAO high-risk list are areas susceptible to increased fraud, waste and abuse.
Published in ACFE Insights Blog

A new estate fraud case is center-stage in South Carolina’s courts. The Palmetto state has been a hotbed of probate, trust and conservator fraud cases dating back more than half a decade.
Published in ACFE Insights Blog

With suspect property fraud schemes, many vandalism insurance claims may appear innocuous at first glance. However, every claims adjuster must be prepared to identify, handle, and most importantly, defeat the elements of fraud that may be present within these types of losses.
Published in ACFE Insights Blog

White-collar crime, an insidious and complex category of offenses, extends far beyond the conventional image of criminal activity. Understanding white-collar crime is crucial for individuals and finance, law and security professionals in our interconnected world.
Published in ACFE Insights Blog

The head of Peru's judiciary, Javier Arévalo Vela, recently publicly highlighted Peru's success in recovering the proceeds of corruption and related financial crimes through its non-conviction based forfeiture law, Extinción de Dominio.
Published in ACFE Insights Blog

As the modern fascination with true crime escalates, perhaps no documentarian today presents the stories of our past with more profundity than Joe Berlinger. The director’s next endeavor figures to hit home for not just millions of Americans but anti-fraud professionals around the world, too.
Published in ACFE Insights Blog

Armed with an innate passion for justice and a keen understanding of the criminal mind, Allison Benkert, CFE, has carved a remarkable career path dedicated to unraveling fraud, seeking truth and ensuring accountability.
Published in ACFE Insights Blog

Frank Dara, CFE worked his way up from a Loss Prevention in-store Detective to becoming the North America Investigations Manager for Nike after years of fraud fighting. This is his story in his own words.
Published in ACFE Insights Blog

Aristotelis Konstantinos Koufos and Francesca Gabella, CFE, a dynamic duo united by their shared passion for fraud prevention and audit, take us on an insightful journey through their mentor-mentee relationship and their experiences in the ACFE Mentoring Program.
Published in ACFE Insights Blog

This exclusive resource marks a consolidation of our three existing newsletters into a unified, comprehensive source of knowledge and insights aimed at empowering you in the fight against fraud.
Published in ACFE Insights Blog

If you have the CFE Exam Prep Course, the Prep Toolkit or are planning to get either of the two, we invite you to sign up for the 90-Day CFE Exam Challenge and earn your Certified Fraud Examiner (CFE) credential.
Published in ACFE Insights Blog

Often linked to organized crime, white-collar crimes pose a persistent challenge today. These are usually nonviolent crimes like identity theft, mortgage fraud, computer crimes and tax evasion. To bring the culprits to justice, it's important to prosecute them rigorously.
Published in ACFE Insights Blog

Tax season can be a stressful time for many people, and it's important to be vigilant in order to protect yourself from tax preparer fraud. By following these tips, you can help protect yourself from tax preparer fraud and ensure that your tax return is accurate and handled properly. If you suspect that you've been a victim of tax preparer fraud, contact the IRS immediately.
Published in ACFE Insights Blog

To counter fraud's growing threat, information sharing mechanisms related to fraud detection and prevention have advanced significantly. Notably, an increasing number of fraudulent information-sharing initiatives are now adopting a public-private partnership approach, involving cooperation between government agencies, law enforcement and private sector entities.
Published in ACFE Insights Blog

Meet Hasmik Meloyan, one of the latest recipients of the ACFE's Ritchie-Jennings Memorial Scholarship. Hasmik's journey is a testament to her relentless pursuit of academic and professional growth, all aimed at making a significant difference in the anti-fraud arena.
Published in ACFE Insights Blog

Meet Jordan Newman, a driven individual who received the prestigious Ritchie-Jennings Memorial Scholarship for excelling in his professional and academic pursuits.
Published in ACFE Insights Blog

Co-published by the Committee of Sponsoring Organizations of the Treadway Commission (COSO) and the Association of Certified Fraud Examiners (ACFE), the Fraud Risk Management Guide provides direction for creating a comprehensive program to manage fraud risks within an organization.
Published in ACFE Insights Blog

Today, Pride Month is a time to celebrate the achievements of the LGBTQ+ community and to advocate for greater equality and acceptance. For those who identify as LGBTQ+ or are allies, it's an opportunity to learn more about the community and support their rights.
Published in ACFE Insights Blog

Despite all of the advancements in security measures in our modern era and through the long history of check fraud, the creativity and sophistication of fraudsters continue to pose significant challenges.
Published in ACFE Insights Blog

In the aftermath of events like Hurricane Idalia and the wildfires in Hawaii, it is crucial to be aware of the various types of fraud that can emerge.
Published in ACFE Insights Blog

The investigative process is essential for uncovering crimes, particularly white-collar crimes. These are crimes committed by individuals, organizations or public officials for financial gain, often without resorting to violence. Edwin Sutherland, one of the pioneers in this field, recognized the complex nature of these offenses.
Published in ACFE Insights Blog

Sam Bankman-Fried's meteoric rise was coupled with an aura of mystery, and questions began to circulate about the integrity of his financial dealings.
Published in ACFE Insights Blog

The U.K.’s Economic Crime and Corporate Transparency Bill made its way through the House of Commons and, more recently, the House of Lords. As the bill approaches becoming law and faces only a few final steps before being law, an analysis of details and slated changes is timely.
Published in ACFE Insights Blog

In the ever-evolving landscape of the digital world, influencer marketing has taken center stage as a powerful tool for brands and businesses to reach their target audience. However, with great power comes great responsibility, and as the industry continues to grow, so does the potential for fraud. Let's delve into the world of influencer fraud and explore its many faces, consequences and potential solutions.
Published in ACFE Insights Blog

As part of the Internet Archive, the Wayback Machine contains a historic log of an estimated 735 billion web pages, making it an incredibly powerful database supporting a range of businesses and industries.
Published in ACFE Insights Blog

Multi-level marketing (MLM) companies and pyramid schemes share similarities like recruitment-focused structures but have key differences, such as the sale of products in MLMs versus pyramid schemes that redistribute payments and fees to early investors.
Published in ACFE Insights Blog

Booking a vacation rental online comes with the convenience of browsing listings from the comfort of home. But it also opens the door to scammers trying to take advantage of unsuspecting travelers.
Published in ACFE Insights Blog

In the world of corporate espionage, uncovering the truth can be a daunting task. But when a global research firm approached us to investigate the simultaneous resignation of two key employees in the latter half of 2020, we knew we had our work cut out for us. The management suspected that the employees were leaving to join a competitor in the same region and requested an eDiscovery review to determine the truth.
Published in ACFE Insights Blog

A group of investors who had invested USD $100 million in an educational institution were concerned about the institution's operations and suspected that their funds were being misused. Our team of experts took on the case, employing a range of techniques and procedures to uncover the truth.
Published in ACFE Insights Blog

Patient Assistance Programs (PAPs) provide free or low-cost medications to eligible patients who cannot afford them. Despite regulatory oversight, instances of PAP fraud have been reported globally.
Published in ACFE Insights Blog

Toward the end of the spring season, our team was contacted by the internal audit head of a global retail organization who requested that we investigate several abnormal transactions in a recently acquired subsidiary, referred to as "PQR," located in the western region of India.
Published in ACFE Insights Blog

As the landscape of financial crime continues to evolve, financial institutions must stay vigilant and prepared to address emerging risks. In this regard, aligning anti-money laundering (AML) programs with the Financial Crimes Enforcement Network AML Priorities becomes crucial.
Published in ACFE Insights Blog

This year, nine candidates have been selected to fill three positions on the 2024-2025 Board of Regents.
Published in ACFE Insights Blog

Although well-intentioned, the U.K.’s fiscal response to the COVID pandemic has been seriously flawed, creating huge opportunities for fraudsters to exploit multiple shortcomings of the various schemes offered by the government to help support businesses.
Published in ACFE Insights Blog

Behavioral biometrics are used to verify the identity of an individual through the analysis of patterns of human behavior. Unlike traditional biometric methods, behavioral biometrics are a more convenient and less intrusive form of identification.
Published in ACFE Insights Blog

The most affordable homes can be the ones built as part of a homeowner’s association (HOA) – nothing wrong with that. The surroundings are always maintained through the HOA and the only thing homeowners need to worry about is the interior of the house, as well as paying regular monthly dues to the HOA. But after settling in, it may quickly become apparent that living under an HOA involves a level of oversight that can be surprising.
Published in ACFE Insights Blog

Explore how iterative learning, strategic planning and adaptive execution can drive meaningful outcomes — even in the face of overwhelming odds.
Published in ACFE Insights Blog

In 2025, fraudsters continued finding new ways to perpetrate schemes. Drawing from industry trends, news stories and expert insights from the ACFE staff, this recap highlights some of the most prominent fraud schemes and developments taking place this past year.
Published in ACFE Insights Blog

When managed properly and overseen with care, sober homes can offer a valuable and stable foundation for recovering addicts. But when operators and others misuse these facilities, it can lead to medical insurance and health care fraud, impacting the lives and well-being of the residents.
Published in ACFE Insights Blog

What happens when those we trust become the problem themselves? In this blog, the author examines several case studies of psychiatrists, psychologists and other behavioral health providers who have crossed the line into non-compliance and outright fraud.
Published in ACFE Insights Blog

Learn how natural language processing converts unstructured information into a visual knowledge graph. This step-by-step guide shows you how to quickly map complex, hidden networks of actors and transactions to uncover fraud schemes.
Published in ACFE Insights Blog

How do you detect and prevent behaviors that aren't perceived as wrong? Learn more about how behavioral economics and experimental game theory can offer tools to go beyond procedural audits by looking at how people think and behave.
Published in ACFE Insights Blog

Learn why tools like scam trackers and professional expertise are critical to verifying cryptocurrency investment opportunities and protecting yourself from fraudulent schemes that have resulted in billions in losses.
Published in ACFE Insights Blog

Preventing fraud is not one easy step, but rather multiple components combined to increase efficiency of fighting fraud. Discover how to simplify your fraud prevention strategy by breaking it down into four balanced steps.
Published in ACFE Insights Blog

Explore how brand trust can become a reputational smokescreen that enables opportunistic fraud, such as quality-washing and fraud-washing, and what to look out for.
Published in ACFE Insights Blog

Ghost fraud schemes are not about spooky spirits — but insidious financial attacks. Explore these scams that involve non-existent employees draining payrolls and silent ghost taps stealing information from mobile wallets.
Published in ACFE Insights Blog

Whether it is hosting a training session, sharing educational materials on social media or joining a community initiative, there are many ways to contribute to the fight against fraud.
Published in ACFE Insights Blog

Learn from ACFE Research Director Mason Wilder, CFE, about how to protect your information online this year during Cybersecurity Awareness Month.
Published in ACFE Insights Blog

A lawsuit filed in Florida accused a group of elder care professionals of a racketeering scheme defrauding an elderly man with dementia. This case explores the challenges of combating elder fraud and the importance of finding the "predicate" fraud that started the chain of illegal acts.
Published in ACFE Insights Blog

Protect yourself from "smishing" scams by learning how to spot and avoid trending text message scams including fake delivery notifications, job offers and toll agency scams.
Published in ACFE Insights Blog

Through the ACFE Law Enforcement and Government Alliance (LEGA) program, government agencies can explore anti-fraud training and resources to prevent, deter and reduce fraud within their organizations.
Published in ACFE Insights Blog

Explore why preventative measures alone aren’t enough and how detective controls like reconciliations, exception reporting and management reviews help organizations catch fraud that slips through the cracks.
Published in ACFE Insights Blog

Explore how the ACFE Corporate Alliance creates a collaborative space for members to share anti-fraud knowledge, tools and strategies to stay ahead of evolving fraud schemes.
Published in ACFE Insights Blog

Lean management systems relying on technical controls alone fail to prevent fraud due to social and cultural dynamics causing employees to circumvent or ignore policies. Explore the author’s breakdown and solution to this fraud prevention issue.
Published in ACFE Insights Blog

A new benchmarking report from the Association of Certified Fraud Examiners (ACFE) and the Anti-Fraud Collaboration (AFC) uncovers insights into how fraud is affecting U.S. public companies and what can be done to fight back.
Published in ACFE Insights Blog

Dive into the forensic review of an engineering, procurement and construction (EPC) company, exploring the red flags and insights discovered from the investigation.
Published in ACFE Insights Blog

From government corruption and fraudulent cryptocurrency networks to celebrity wire fraud and massive health care scams, the first six months of 2025 have been filled with high-profile fraud cases. Here are six fraud cases that defined the first half of the year.
Published in ACFE Insights Blog

From keynote session highlights to the sights and sounds from Nashville, this blog provides an overview of what you may have missed the 36th Annual ACFE Global Fraud Conference.
Published in ACFE Insights Blog

It is important to recognize the critical role whistleblowers play in efforts to combat financial crime. However, while countries such as the United States and Canada have paved the way here, the United Kingdom has been slow to follow suit.
Published in ACFE Insights Blog

The 36th Annual ACFE Global Fraud Conference is set to have an extraordinary lineup of keynote speakers, networking opportunities, a fundraising concert and more.
Published in ACFE Insights Blog

What if the largest enabler of fraud is not a rogue employee, but an executive who believes they are doing the right thing for the business? Discover how senior leaders can unintentionally enable fraud by prioritizing efficiency over ethics.
Published in ACFE Insights Blog

Wondering how to turn “invisible” fraud-prevention wins into a clear case for a raise or promotion? In this Q&A, veteran managers reveal the performance metrics, certifications and soft-skills that convince decision-makers you’re ready for the next step.
Published in ACFE Insights Blog

What if the very strategy that makes a company efficient is also what makes it vulnerable to fraud? Explore how fraud can quietly thrive in streamlined organizations and what anti-fraud professionals can do about it.
Published in ACFE Insights Blog

What does it take to earn your CFE credential? Two professionals share their motivations, study strategies and how becoming a Certified Fraud Examiner (CFE) advanced their careers.
Published in ACFE Insights Blog

In 2021, JPMorgan acquired Charlie Javice's startup, Frank, for $175 million, only to soon discover they were victims of her scam. Learn how even banking giants like JPMorgan can fall victim to fraud by not taking the proper due diligence measures.
Published in ACFE Insights Blog

Even well-intentioned medical professionals can face legal consequences when they neglect the business side of health care. Understanding the revenue cycle is key to spotting fraud, reducing risk and maintaining compliance.
Published in ACFE Insights Blog

Responding to fraud requires careful investigation, objective decision-making and clear documentation. Discover the steps organizations should take after discovering fraud, from internal investigations to criminal referrals, with insights from Occupational Fraud 2024: A Report to the Nations.
Published in ACFE Insights Blog

David Judd, a Michigan nurse practitioner, billed for an unattainable number of patient visits and hours, leading to significant overpayments from Medicare. Read more about this scheme, known as the "Impossible Day", where health care providers will fraudulently claim they worked more than 24 hours in a single day.
Published in ACFE Insights Blog

Risk management professionals play a vital role in identifying vulnerabilities and building resistance against fraud. By integrating fraud risk into broader organizational strategies, they help prevent schemes before they start and support a culture of accountability.
Published in ACFE Insights Blog

Health care fraud continues to drain vital resources from the U.S. system, impacting patients and providers alike. This blog breaks down the latest data, trends and enforcement efforts behind the $54 billion recovered through the False Claims Act since 1987.
Published in ACFE Insights Blog

Drexel University held their 11th annual Fraud and Internal Control Case Competition (F1C3), giving students the opportunity to practice their anti-fraud skills in a realistic, professional environment.
Published in ACFE Insights Blog

Home health care is ripe for fraud, with the federal government estimating that 69% of the population will need caregiving—a vulnerable population that could be very appealing to fraudsters seeking to exploit Medicare and Medicaid systems.
Published in ACFE Insights Blog

As private sector companies in Mexico continue to reshape business efficiencies and increase in value, accountability and oversight remain as important as ever. Explore why regulatory efforts and internal investigations must meet the growing demand in the region.
Published in ACFE Insights Blog

Traditionally a heavier lift, spear phishing is using new tools to make these schemes more effective and easier for fraudsters to execute. Explore how AI is automating research to craft customized spear phishing strategies.
Published in ACFE Insights Blog

Recent cases highlight how kickbacks are often disguised through lavish gifts, hidden payments and sham business arrangements, emphasizing the importance of maintaining ethical practices in health care.
Published in ACFE Insights Blog

Fraud detection is a growing challenge, but researchers like Ivy Munoko are exploring how AI and key audit factors can improve detection efforts. Supported by the ACFE Research Institute, her work provides critical insights for auditors, fraud examiners and regulators navigating an evolving fraud landscape.
Published in ACFE Insights Blog

Health care fraud remains a major problem in the anti-fraud field, requiring a deep understanding of industry terminology for effective investigations.
Published in ACFE Insights Blog

As fraud risks evolve, having a strong in-house investigation team is crucial—but how do you gauge its effectiveness? The In-House Fraud Investigation Teams: 2025 Benchmarking Report delivers key insights on team structure, case resolution and training investments to help you strengthen your fraud response strategy.
Published in ACFE Insights Blog

While many organizations are still adjusting to AI-driven risks introduced by industry leaders like OpenAI and Google, a new wave of AI tools like DeepSeek presents fresh challenges that organizations must address.
Published in ACFE Insights Blog

The first ACFE Report to the Nations was published nearly 30 years ago in 1996. It would be overly simplistic to say that fraud has grown since then, but the data clearly shows significant increases as more information has been reported by CFEs around the world.
Published in ACFE Insights Blog

The next generation of Certified Fraud Examiners (CFEs) must navigate blurred ethical boundaries, hidden conflicts of interest and inconsistent regulatory standards across industries and borders. To meet this challenge, the author proposes case-based learning.
Published in ACFE Insights Blog

Fraud can infiltrate even the most secure organizations, leaving a trail of financial and reputational damage in its wake. When fraud arises, forensic accountants play a critical role in uncovering the truth, guiding investigations and safeguarding organizational integrity.
Published in ACFE Insights Blog

Read on to discover Cecilia’s approach to exam preparation, how the challenge helped her succeed and her advice for future participants aiming to earn their CFE credential.
Published in ACFE Insights Blog

For anyone who made a New Year’s resolution to pass the CFE Exam this year, now may be the perfect time for you to take the first necessary steps to earn the Certified Fraud Examiner credential. Sometimes the hardest part of achieving a goal is simply getting started.
Published in ACFE Insights Blog

According to the ACFE’s Report to the Nations, organizations with less than 100 employees suffered larger median losses than those of larger companies. In other words, fraud can happen at any organization, no matter the size, so it’s important to understand the warning signs. So, what are the warning signs to look out for?
Published in ACFE Insights Blog

Recently, Charles Washington, CFE, spoke on a panel for an ACFE webinar titled “A Conversation About Diversity, Equity and Inclusion in the Anti-Fraud Profession.” In this post, he digs in even further into this topic to share insights and advice on how you can make an impact in your own workplace and foster a culture of diversity, equity and inclusion as an anti-fraud professional.
Published in ACFE Insights Blog

Monica Modi Dalwadi, CFE, CPA, is a managing partner in the D.C. area for Baker Tilly. She works primarily with owners and financial officers of companies, providing business consulting services. She also acts as a valued advisor to her clients as a partner and leader in risk, internal audit and cybersecurity.
Published in ACFE Insights Blog

In this episode of Fraud Talk, Mason Wilder, CFE, ACFE senior research specialist, and Brian Fox, vice president of strategic partnerships at Thomson Reuters and president & founder of Confirmation, discuss the rise and fall of the German payments group, Wirecard.
Published in ACFE Insights Blog

We all have so many questions right now. When will this be over? How can I keep moving when it feels like the world is telling me to stand still? What does the future hold? While I can’t answer any of these questions for you, I can answer a question we have been getting here at the ACFE: what are some easy ways for me to get my CPE while social distancing?
Published in ACFE Insights Blog

As anti-fraud professionals, we are trained to find and fix the opportunities for fraudulent activity within our organizations. But there are usually only a few of us and many employees. How is a small team, or single fraud professional, supposed to deter and detect all fraud?
Published in ACFE Insights Blog

The ACFE’s 2020 Report to the Nations not only identifies the top anti-fraud controls that can help protect organizations, but also illustrates what can happen when controls are weak or altogether missing.
Published in ACFE Insights Blog

Arthur Andersen, Enron and WorldCom certainly left behind a legacy that changed the financial world, especially that of the public company. The Public Company Accounting Oversight Board (PCAOB) was born thanks to SOX and with it brought attention and improvements.
Published in ACFE Insights Blog

Each year, Certified Fraud Examiners (CFEs) in good standing are given the opportunity to help foster the growth and development of the anti-fraud profession by casting votes for the Association of Certified Fraud Examiners (ACFE) Board of Regents.
Published in ACFE Insights Blog

In today’s modern age almost every business is dependent on the internet and information technology to accomplish a variety of daily operational tasks. From emails to e-commerce and e-banking, sensitive business activities are conducted via the internet. While the internet has undoubtedly made it easier for businesses of all shapes and sizes to operate, it has also made it easier for cybercriminals to gain access to confidential information and systems.
Published in ACFE Insights Blog

Abigail had her first introduction to the fraud industry when a former coworker referred her to an open position at their health insurance company. Later she began her work as a Fraud Coordinator in 2018 and since has made the transition to becoming a Fraud Analyst. In 2021, Abigail joined the 90-Day CFE Exam Challenge, where she was able to study and pass her exams within 90 days.
Published in ACFE Insights Blog

After years of experience leading hundreds of fraud-related investigations, Dr. Tim Klatte, CFE made the decision to prepare for the CFE exam with the help of the 90-Day CFE Exam Challenge.
Published in ACFE Insights Blog

Now available at ACFE.com/Government, this new hub offers multiple forms of content for government and public administration professionals to expand their knowledge base and continue developing skills essential to the prevention and detection of fraud at various levels of government.
Published in ACFE Insights Blog

The U.S. Department of Justice (DOJ) announced in early February 2022 that they had arrested two individuals, Ilya Lichtenstein and his wife Heather Morgan. When the couple was arrested in connection with the theft of cryptocurrency from the Bitfinex cryptocurrency exchange in 2016 and subsequent laundering of the proceeds, it led to one of the most valuable seizures of illicit proceeds in law enforcement history.
Published in ACFE Insights Blog

It comes as no surprise to learn that Lisa Osofsky is stepping down next summer after five years as head of the U.K.’s Serious Fraud Office (SFO). Ms. Osofsky has overseen an often contentious five years at the helm of the U.K.’s leading fraud prosecution agency.
Published in ACFE Insights Blog

On July 14, 2022, Mike Esposito, owner of The ‘In’ Groove record store in Phoenix, Ariz., stated that MoFi has been using digital files in its production of so-called original master tape albums despite marketing the reissues as authentic.
Published in ACFE Insights Blog

An investigation into fraudulent activities was turned over to me after three other independent investigators did not satisfy the leadership of the results. Here is how my team calculated the $611K loss due to fraud that other investigations missed.
Published in ACFE Insights Blog

Recently, I worked on a case wherein a whistleblower raised allegations on two employees that the company was engaging in unethical practices. The allegations included bribery and corruption, conflict of interest, breach of code of conduct, misappropriation of assets, high prices and poor quality of products supplied and abuse of position.
Published in ACFE Insights Blog

Unfortunately, not all causes we are called to join have a noble motive; some of them are organized by unscrupulous individuals who take advantage of our generosity to steal our money. But how can you donate without being a victim of a charity scam?
Published in ACFE Insights Blog

A self-proclaimed amateur rapper nicknamed the “Crocodile of Wall Street,” Heather Morgan, along with her husband Ilya Lichtenstein, were arrested and charged with conspiracy to allegedly launder $4.5 billion in stolen Bitcoin.
Published in ACFE Insights Blog

Joshua David Nicholas, the head trader of cryptocurrency platform EmpiresX, pleaded guilty on September 8 in an alleged investment fraud that raised around $100 million for the company, according to the U.S. Justice Department.
Published in ACFE Insights Blog

The growing trend of shoppers preferring pajamas and pumpkin pie to cold weather and crowds reached an all-time high in 2021 as online shopping for the holiday season soared due to the COVID-19 pandemic. In 2022, global online sales again hit a new high of $281 billion during Cyber Week (Thanksgiving Day through Cyber Monday). So, what do all these numbers mean for fraud examiners?
Published in ACFE Insights Blog

After seven days of deliberations, a jury in California found Theranos founder Elizabeth Holmes guilty on four out of 11 federal fraud charges on January 3, 2022.
Published in ACFE Insights Blog

On Thursday, a jury of seven women and five men convicted Ramesh “Sunny” Balwani on 12 counts of federal fraud.
Published in ACFE Insights Blog

While victims of traditional identity theft often catch it quickly, victims of medical identity theft may not know they are victims until they need critical medical treatment. In this episode of Fraud Talk, Scott Ward, CFE, senior vice president at Qlarant, discusses the insidious nature of medical identity theft, the impact it has on its victims and what people and governments can do to help combat it.
Published in ACFE Insights Blog

Tod McDonald, CPA and Garth Leonard, CFE, from Valid8 Financial, join ACFE Community Manager Rihonna Scoggins in the most recent episode of Fraud Talk to explore the current resources at hand for fraud examiners.
Published in ACFE Insights Blog

In this excerpt from episode 118 of Fraud Talk, Jim Ducharme, COO of Outseer, talks with Rihonna Scoggins, ACFE Community Manager, about how Buy Now, Pay Later services are being exploited through identity theft.
Published in ACFE Insights Blog

In this excerpt from episode 123 of Fraud Talk, Kate Pospisil, ACFE Communications Specialist, and associate professor of accounting, taxation and business law at SUNY Old Westbury, Dr. David Glodstein, speak about how the Justice for Fraud Victims Project benefits underprivileged groups and small businesses, while allowing the next generation of fraud fighters to learn and gain professional experience.
Published in ACFE Insights Blog

In Episode 125 of Fraud Talk, ACFE Training Director Jason Zirkle, CFE, is joined by Collins Wanderi, CFE, Bill Stakes, CFE, and Monica Meeks, CFE, to discuss the tools they’ve gained and advice they offer to veterans and active-duty military members looking to earn their CFE credential.
Published in ACFE Insights Blog

In this excerpt from episode 124 of Fraud Talk, ACFE Chief Training Officer John Gill, J.D., CFE, and Gary Weiss, author of “Retail Gangster: The Insane, Real-Life Story of Crazy Eddie,” talk about the insurance scheme Eddie Antar committed but was never caught for.
Published in ACFE Insights Blog

The Justice Department charged 47 defendants on September 20th for allegedly defrauding a federal program that provided food for needy children during the pandemic, describing the scheme — totaling nearly $250 million — as the largest uncovered to date.
Published in ACFE Insights Blog

In an email obtained by “The Ankler,” it was revealed that Michael Lewis, the author of "The Big Short", has been working on profiling the Sam Bankman-Fried’s rise to power, as well as a once-budding rivalry between the 30-year-old billionaire and Binance CEO Changpeng Zhao.
Published in ACFE Insights Blog

Synthetic identity fraud occurs when perpetrators combine piecemeal and, at times, factual information to create a new identity.
Published in ACFE Insights Blog

In the past year, record numbers of employees have been quitting their jobs, and sometimes leaving entire industries. With so much turmoil in the job market, it comes as no surprise that fraudsters are pouncing. Career scammers are targeting job seekers using LinkedIn to reach out with fake offers and requesting personal information.
Published in ACFE Insights Blog

Cognitive bias is when an investigator's own assumptions or beliefs impact their judgment of information and evidence. When investigating fraud, it is important that the investigator be able to think clearly and make unbiased decisions.
Published in ACFE Insights Blog

Alexandre De Genaro, CFE, realized he was on the right path when he garnered his first confession during a fraud investigation. After spending time in information security and loss prevention, De Genaro is now the Head of Business Security, Latin America for General Mills.
Published in ACFE Insights Blog

Angelica Isgleas Pacheco, CFE, began her career as an auditor for an accounting firm. She found her love for fighting fraud through her career and has excelled due to her passion for her community. This is her story in her own words.
Published in ACFE Insights Blog

Diana Muyibi is a graduate student studying at State University of New York (SUNY), Old Westbury and also a proud past recipient of the ACFE’s Ritchie-Jennings Memorial Scholarship. Diana is in the Master of Science in forensic accounting program and is expected to graduate this spring.
Published in ACFE Insights Blog

Michael Mingo-Dabney, CFE, began his career as an anti-fraud professional after learning about the prevalent embezzlement and money laundering corrupting a town in Colombia while serving as a volunteer for the Peace Corps. Michael continues his work against fraud as a fraud analyst for C2 Alaska, as well as serving as a contractor for the Securities and Exchange Commission’s Division of Enforcement.
Published in ACFE Insights Blog

Paul McCormack, CFE, began his career in anti-fraud as a forensic accountant and after gaining a wealth of experience, he made the leap and started his own freelance writing business in the fraud and compliance space. Paul has written for countless publications and companies throughout the industry, including Fraud Magazine.
Published in ACFE Insights Blog

Ryan Cannon is an undergraduate student studying at the University at Albany and also a proud past recipient of the ACFE’s Ritchie-Jennings Memorial Scholarship. Ryan is pursuing a dual major in Homeland Security and Business Administration.
Published in ACFE Insights Blog

Sherene Teo, CFE, began her career in anti-fraud as an auditor in China and after encouragement she applied to become an in-house investigator which helped her gain experience to join her new team at Microsoft.
Published in ACFE Insights Blog

ACFE member William Klun spent decades working in the financial industry before setting his sights on fighting fraud. In addition to his drive to seek the truth, he also spends time helping refugees find asylum. Here is his story in his own words.
Published in ACFE Insights Blog

The ACFE Mentoring Program connects members to anti-fraud professionals from all over the world who can offer a wealth of resources, experience, advice and guidance. Mentees can search among registered mentors to find individuals whose experience and expertise match the areas in which they wish to be mentored. Caroline Kaye initially reached out to Holly Atkins, CFE, after viewing her mentor profile on the ACFE Community, and since then the pair have been connecting through their personal and professional experience.
Published in ACFE Insights Blog

The ACFE Mentoring Program connects members to anti-fraud professionals from all over the world who can offer a wealth of resources, experience, advice and guidance. Kate Rolan initially reached out to David Harper, CFE, after seeing his experience in law enforcement and investigations on the ACFE Community. This is Kate and David’s mentoring story.
Published in ACFE Insights Blog

CFEs have a good eye for email scams and can usually spot them quickly. But sometimes the language and graphics are so convincing that they fool even the most skilled observer.
Published in ACFE Insights Blog

Could increased disclosure and whistleblower protections for private companies prevent another fraud scheme like Theranos?
Published in ACFE Insights Blog

We have compiled a list of the most popular recent limited series, documentaries and films about fraud that can add context to known cases, illustrate some common fraud schemes and provide insight into the fraudsters at the center of these now infamous frauds.
Published in ACFE Insights Blog

With all the busy work of report writing, speaking to law enforcement, preparing for court and filing examination findings, investigators do not always remember the trauma a financial loss can be to the victim.
Published in ACFE Insights Blog

As experienced fraud examiners know, fraud comes in many varieties, including tales that are truly frightening. These fraudsters were willing to play any type of trick to take their ill-begotten treats. Read on to learn more about this year’s tales of terrifying fraud, but don’t say we didn’t warn you.
Published in ACFE Insights Blog

Reality is simply based in fact, whether it be an event or transaction. A fraudster’s movement is a documented reality. Reality, or the truth, is simply confirmed by documentation, digital footprints and verifiable eyewitnesses, which can be pieced together to reveal the factual timeline.
Published in ACFE Insights Blog

In September 2021, the IRS published a request for proposal titled, “Development of Exploitation Techniques Against Cryptowallets.” According to supporting documentation, it appears that the digital forensics unit of their Criminal Investigations branch has repeatedly run into scenarios involving the seizure of crypto hardware wallets (also known as cold storage devices) that could not be accessed due to their security features.
Published in ACFE Insights Blog

Besides its stable political and economic environment, what makes the land of tulips and windmills so attractive to corporate giants such as Starbucks, Google and Amazon?
Published in ACFE Insights Blog

Supreme Audit Institutions (SAIs) play an important role in national and global economy by ensuring that public resources are managed properly and in accordance with established rules.
Published in ACFE Insights Blog

The U.S. Department of Justice (DOJ) has brought insider trading charges against Ishan Wahi, a former Coinbase product manager, Nikhil Wahi and Sameer Ramani after they allegedly made profits of more than $1 million by buying crypto assets before their listings on the exchange.
Published in ACFE Insights Blog

The Association of Certified Fraud Examiners (ACFE) is proud to announce that Thomas Caulfield, CFE, and Natalie Lewis, CFE, have been elected to the 2023–24 ACFE Board of Regents. Fellow Certified Fraud Examiners (CFEs) elected them from candidates selected by the Board's nomination committee. Caulfield and Lewis will take office at the Board's meeting in February.
Published in ACFE Insights Blog

In 2021, Russian crude and condensate output reached 10.5 million barrels per day, making up 14% of the world’s total supply. In the same year, Russia exported oil worth USD 300 billion, accounting for 11% of the global oil trade. The country exports most of its oil production, with almost all going to Europe (about 80%) and Asia (about 20%).
Published in ACFE Insights Blog

Money mules continue to play a key role in international money laundering operations. Accordingly, both Europol and the FBI have recently stepped up their efforts to raise public awareness about money mules and how to avoid becoming one.
Published in ACFE Insights Blog

Whistleblowing is one of the most powerful weapons in the fight against fraud, money laundering and corruption, but the United Kingdom’s approach needs to be reconsidered. Whistleblowing can be a testy subject, but I believe it is potentially one of the most powerful weapons in our anti-money laundering (AML) arsenal.
Published in ACFE Insights Blog

Online payments through apps such as Zelle are easy to use and serve a valid purpose in today’s digital society. However, as easy as they are to use, they also give fraudsters an easily accessible path to steal your money.
Published in ACFE Insights Blog

At the 33rd Annual ACFE Global Fraud Conference, Roderick Chambers speaks with ACFE Research Manager Mason Wilder, CFE, to discuss the importance of technical controls and knowledge to protect your organization from fraud.
Published in ACFE Insights Blog

In this excerpt from episode 117, Larry Nielson talks with Mason Wilder, CFE, about how prevalent cryptocurrency is in his fraud work, and how crypto is being used in traditional crime as a new medium.
Published in ACFE Insights Blog

William Shakespeare is widely considered to be one of the most prolific and influential writers of all time. But one group of individuals, who call themselves “Oxfordians” and their theory the "Shakespeare Authorship Question," falsely claim that what we know to be Shakespeare's plays and poetry were actually penned by someone else.
Published in ACFE Insights Blog

International pop star Shakira has been in the spotlight this past week – not because of a new album or performance, but for a looming trial in a tax fraud case.
Published in ACFE Insights Blog

Pride Month may be over, but, for scammers, the calendar doesn’t matter: There’s fraud to be had every month of the year.
Published in ACFE Insights Blog

Recent reports show that PPP loan fraud soared in the last two years, putting billions of taxpayer dollars in the pockets of fraudsters and criminals.
Published in ACFE Insights Blog

Stock market manipulation and insider trading fraud are perennial challenges, with fraudsters capitalizing on information asymmetry and exploiting investor psychology.
Published in ACFE Insights Blog

If you have the CFE Exam Prep Course, the Prep Toolkit or are planning to get either of the two, we invite you to sign up for the 90-Day CFE Exam Challenge and earn your Certified Fraud Examiner (CFE) credential by March 31, 2025.
Published in ACFE Insights Blog

Welcome to Fraudify Wrapped 2024! Drawing from industry trends, news stories and expert insights, we have compiled a recap of the biggest fraud developments of the year.
Published in ACFE Insights Blog

The Association of Certified Fraud Examiners (ACFE) is proud to announce that Annemari Krugel, CFE, and Mark J. Sullivan, CFE, CPP, CFI, have been elected to the 2025–2026 ACFE Board of Regents. Fellow Certified Fraud Examiners (CFEs) elected them from candidates selected by the Board's nomination committee. Krugel and Sullivan will take office in February 2025.
Published in ACFE Insights Blog

When the Association of Certified Fraud Examiners (ACFE) conducted its first Report to the Nation in 1996, one of the purposes was to describe the typical occupational fraud perpetrator. In 1996, our results showed that the typical fraudster was a college-educated, married, white, male employee. While some consistencies remain, much has changed in recent years.
Published in ACFE Insights Blog

Food fraud is dangerous for many reasons. It has the potential to cause harm to people and the economy through its deception. When ingredients are removed or added, it greatly changes the product that is being sold, which may harm individuals, as well as damage the reputations of companies and industries at large.
Published in ACFE Insights Blog

Among the most valuable assets in an organization’s fraud prevention toolkit is its internal audit team. Internal auditors have the advantage of an insider’s view of an organization’s controls, making them uniquely positioned to help identify fraud risks and support investigations.
Published in ACFE Insights Blog

What does it mean to have an organization that has a culture that ensures a massive theft does not occur—or if someone does attempt a fraud, it is caught early?
Published in ACFE Insights Blog

This year, six candidates are on the ballot and will fill two open positions on the 2025-2026 ACFE Board of Regents. All CFEs who are in good standing have until November 30, 2024, to cast their votes. The newly elected Regents will each serve a two-year term beginning in February 2025.
Published in ACFE Insights Blog

As part of this exciting shift, Fraud Magazine will transition to become a fully digital, online publication. The January/February 2025 issue will be the final printed and shipped version of the magazine, honoring the publication’s long history and celebrating its growth into the future.
Published in ACFE Insights Blog

Are you gearing up to take the Certified Fraud Examiner (CFE) exam? Proper preparation is key to success, and here is how you can effectively strategize and streamline your study process.
Published in ACFE Insights Blog

This yearly compilation, which dates back to 1990, highlights key cases involving conflict of interest, bribery and corruption by federal employees, contractors, grant recipients and others.
Published in ACFE Insights Blog

This article presents a detailed case study of a leading automobile company that undertook a comprehensive investigation into allegations of kickbacks, conflicts of interest among its vendors and employees, and theft of high-quality automotive paint.
Published in ACFE Insights Blog

Whether it is hosting a training session, sharing educational materials on social media or joining a community initiative, there are many ways to contribute to the fight against fraud.
Published in ACFE Insights Blog

The 2024 Compensation Guide for Anti-Fraud Professionals comes with several new findings and analysis, reflecting the evolving landscape of the anti-fraud profession.
Published in ACFE Insights Blog

We are thrilled to announce that Fraud Magazine will relaunch an updated version of our website in the spring of 2025!
Published in ACFE Insights Blog

Motivated by the potential for recognition, professional growth and networking within the anti-fraud community, Isaac Asamoah Amponsah seized the opportunity, seeing his scholarship not just as financial support but as a catalyst for future career advancement and impact in the field of anti-fraud.
Published in ACFE Insights Blog

The Chase Bank "money glitch" trend recently gained traction on social media platforms, where influencers and scammers misled many into believing they can get free money from banks by exploiting a so-called "glitch."
Published in ACFE Insights Blog

On July 19, 2024, CrowdStrike pushed out an update to one of its programs, a vulnerability scanning tool called Falcon Sensor, that contained a significant bug. For computers running on a Microsoft Windows operating system, this faulty update caused the computer to crash.
Published in ACFE Insights Blog

By examining some of the most notorious historical frauds and integrating insights from the ACFE’s Occupational Fraud 2024: A Report to the Nations, businesses can better protect themselves from similar pitfalls today.
Published in ACFE Insights Blog

While support groups play a critical role, there are additional resources and strategies that can further aid in the recovery process for fraud victims.
Published in ACFE Insights Blog

This article provides an overview of a comprehensive forensic investigation conducted for a prominent Indian firm in the IT and ITeS industry.
Published in ACFE Insights Blog

The suspected borrower company was dealing in garments, while the suppliers were traders of animal husbandry products, revealing even more inconsistencies in the trade activities and additional evidence of round-tipping of transactions.
Published in ACFE Insights Blog

Package delivery scams typically involve fraudulent communications claiming to be from legitimate shipping companies. Scammers use various tactics to deceive recipients into believing they have a package waiting for delivery, a missed delivery attempt or an outstanding fee that needs to be paid.
Published in ACFE Insights Blog

In the specialized field of Applied Behavior Analysis (ABA) therapy, which is crucial for improving behaviors in individuals with autism and other developmental conditions, the importance of adhering to ethical standards cannot be overstated. However, dishonest and fraudulent activities frequently jeopardize this field's credibility.
Published in ACFE Insights Blog

Fraud detection often requires sharp observational skills and a keen eye for detail. While many tools and techniques can aid in this process, one of the most effective methods is recognizing behavioral red flags.
Published in ACFE Insights Blog

Occupational Fraud 2024: A Report to the Nations not only identifies the top anti-fraud controls that can help protect organizations, but it also illustrates what can happen when controls are weak or altogether missing.
Published in ACFE Insights Blog

Artificial intelligence (AI) is becoming an increasing problem not just for hackers and fraudsters, but also for identity theft. Recently, there have been an influx of deepfakes of celebrities, but not just their faces—their voices.
Published in ACFE Insights Blog

The ACFE's recently released Occupational Fraud: 2024 A Report to the Nations paints a clear picture: tip lines remain the most effective tool for detecting fraud, uncovering 43% of cases.
Published in ACFE Insights Blog

On March 28, 2024, Samuel Bankman-Fried, the founder of the cryptocurrency trading firm Alameda Research and the cryptocurrency exchange FTX, was sentenced to 25 years in federal prison for his role in several fraud schemes. Because the sentencing guidelines are advisory, federal judges have discretion when sentencing offenders. This can result in wide discrepancies between offenders who have been convicted of similar or identical offenses, even within the same federal jurisdiction.
Published in ACFE Insights Blog

From massive corporate fraud in China to sophisticated cryptocurrency thefts and international scam networks, these cases underline the persistent challenges in combating financial crime.
Published in ACFE Insights Blog

Having a safe, secure and reliable reporting system for employees to use will help ensure that wrongdoing is reported while whistleblowers are protected.
Published in ACFE Insights Blog

Artificial Intelligence to commit healthcare fraud or to prevent healthcare fraud? The gradual acceptance of artificial intelligence in many industries including the healthcare sector is seen by many as a giant revolutionary step.
Published in ACFE Insights Blog

The latest insights from the Occupational Fraud 2024: A Report to the Nations spotlight a significant shift towards web-based reporting mechanisms, signaling an opportunity to involve Generation Z (Gen Z) in the fight against fraud.
Published in ACFE Insights Blog

In a webinar presented to ACFE Corporate Alliance members and ACFE Law Enforcement and Government Alliance members, Lauren Kohr and Victor Cardona, CFE, delve into the significance of establishing public-private partnerships (PPP).
Published in ACFE Insights Blog

The ACFE is not only here to help you attain your Certified Fraud Examiner (CFE) credential, but to help you utilize it to its fullest potential. From improving your skills to finding the perfect job fit, the ACFE has your back every step of the way.
Published in ACFE Insights Blog

According to the UN Conference on Trade and Development, in 2023 maritime trade accounted for over 80% of international trade, carried out by vessels flagged and owned by different countries and manned by international crews.
Published in ACFE Insights Blog

Beneath the glossy labels and vibrant packaging, a darker trend is emerging: greenwashing. This deceptive practice not only misleads consumers but also undermines genuine efforts toward environmental sustainability for a profit.
Published in ACFE Insights Blog

The SNPR proposal seeks to “add a prohibition on the impersonation of individuals and extend liability for violations of the Rule to parties who provide goods and services with knowledge or reason to know that those goods or services will be used in impersonations of the kind that are themselves unlawful under the Rule.”
Published in ACFE Insights Blog

The Indian pharmaceutical sector is increasingly facing a formidable challenge — the diversion of institutional drugs to retail markets.
Published in ACFE Insights Blog

From unlocking new career opportunities, to staying ahead of industry trends, networking empowers fraud examiners to thrive in a dynamic landscape where collaboration and knowledge exchange are essential.
Published in ACFE Insights Blog

Few leaders have demonstrated a commitment quite like Jeanette LeVie, who is celebrating her retirement after 32 years of service to the ACFE.
Published in ACFE Insights Blog

In this guide, we will explore various strategies to help you leverage your CFE credential effectively and advance your career in the fraud examination field.
Published in ACFE Insights Blog

As recipients of the ACFE Research Institute (ARI) grant, Marie Rice and David Glodstein stand at the forefront of advancing the field of fraud examination and prevention.
Published in ACFE Insights Blog

The 13th edition of the ACFE’s biennial research report continues its pivotal role in shedding light on the pervasive issue of occupational fraud, offering unparalleled insights into the mechanics of fraud within organizations worldwide.
Published in ACFE Insights Blog

There are consistent factors in fraud, like social engineering tactics that exploit human behavioral tendencies or external financial pressures that lead fraudsters to commit their crimes, but there are also trends and themes that emerge and affect the anti-fraud profession on a more limited timeframe.
Published in ACFE Insights Blog

February is Black History Month, a time when we celebrate the contributions and achievements of Black Americans throughout history. As we reflect on the past and present struggles of the Black community, it's important to highlight and support organizations that are actively working to make a difference.
Published in ACFE Insights Blog

The 2024 Anti-Fraud Technology Benchmarking Report, developed by the Association of Certified Fraud Examiners (ACFE) in partnership with SAS, highlights a significant trend in the fight against fraud.
Published in ACFE Insights Blog

Between 1999 and 2015, more than 900 U.K. post office branch managers were wrongly accused of theft or fraud due to a flawed computer system. This scandal has had profound consequences, including imprisonment, financial ruin and other tragic outcomes in the years that followed.
Published in ACFE Insights Blog

Finding work in the fraud examination field can be very challenging. Colin May, CFE, provides some perspective and ideas on how to stay motivated and resilient during a difficult job search.
Published in ACFE Insights Blog

While it may seem like a lower-level scam, gift card fraud has real consequences for retailers. An analysis of data drawn from the Federal Trade Commission’s Consumer Sentinel database found that gift card scams have led to a consumer loss of $148 million.
Published in ACFE Insights Blog

Fighting fraud is everyone’s responsibility, and I thank all of you, our members, for rising to the challenge.
Published in ACFE Insights Blog

In the continued pursuit of reducing fraud worldwide, the Association of Certified Fraud Examiners (ACFE) has joined the Anti-Fraud Collaboration (AFC) as its newest member.
Published in ACFE Insights Blog

Each year, the ACFE honors outstanding individuals and organizations who make significant contributions to fighting fraud. The ACFE is proud to recognize these exceptional individuals for their invaluable service in the ongoing fight against fraud through the ACFE Awards.
Published in ACFE Insights Blog

There appeared to be an overwhelmingly substantial number of “high loss” fraud schemes being perpetrated in 2022 (as reported by the Federal Trade Commission). This was shocking as it appeared to show more high loss cases than low loss cases. This would signal a marked departure from decades of historical statistics. Statistics we, in program oversight, rely upon to strategize our anti-fraud endeavors.
Published in ACFE Insights Blog


The growing abundance of internal and external threats can make it difficult to stay ahead of fraudsters. While fraud itself hasn’t changed all that much in recent years, the risks continue to grow in both size and complexity as technology changes and the ability to move, share and expose corporate assets becomes easier. In today’s technology-crazed age, the scope of risk is growing, and businesses that do not keep up with evolving threats will be vulnerable.
Published in ACFE Insights Blog

Dubbed the “archetype of avarice” by The New York Times, Dennis Kozlowski could have written the book on how NOT to set an ethical tone at the top.
Published in ACFE Insights Blog

If you suspect fraud has occurred at your organization, take these immediate action steps.
Published in ACFE Insights Blog

As a result of the memorandum titled “Individual Accountability for Corporate Wrongdoing” issued by former U.S. Deputy Attorney General (DAG) Sally Yates on September 9, 2015, even those who merely had knowledge that something wrong was happening but didn’t report it would potentially face penalties.
Published in ACFE Insights Blog

According to the National Health Care Anti-Fraud Association, the U.S. loses tens of billions of dollars each year to health care fraud. This post discusses five common billing schemes, and how to detect and prevent them.
Published in ACFE Insights Blog

An act of fraud rarely occurs without subsequent acts to hide it. In the time after a fraud takes place, perpetrators are working in multiple ways to either circumvent controls or take advantage of a lack of controls.
Published in ACFE Insights Blog

In order to protect yourself and your company from a business email compromise (BEC) attack, you should stay up to date on different tactics and techniques used by fraudsters. Here are a few key pieces of information included in a recent Better Business Bureau report that you should know about BEC scams.
Published in ACFE Insights Blog

Take a look at the current fraud prevention plan you have in place and evaluate its effectiveness.
Published in ACFE Insights Blog

In the most recent episode of the ACFE’s podcast, Fraud Talk, Julia Johnson, CFE, Research Specialist at the ACFE, breaks down three recent case studies of frauds that were committed from behind bars. She explains how the schemes were perpetrated and what fraud examiners can learn from each case.
Published in ACFE Insights Blog

Benford’s Law can be a tricky concept to grasp at first, but it provides an extra method for fraud examiners to test data for potentially fraudulent activity. Here’s more on what it is exactly and how fraud examiners can use it.
Published in ACFE Insights Blog

We have compiled a list of 10 fraud-related podcasts that will have you laughing and learning the whole way through.
Published in ACFE Insights Blog

Joseph Cox, an investigative reporter at VICE, enlisted the help of a friendly hacker to report on a service called Sakari, a company that streamlines mass SMS messaging for businesses. The hacker was able to use the service to reroute all of Cox’s text messages to the hacker’s device, and Cox didn’t receive a single notification about the theft of his number. He just stopped receiving text messages.
Published in ACFE Insights Blog

I hosted a weekly virtual class and talked about the 5Ws and 1H of writing — What, Why, Who, Where, When and How. I learned this concept from a former boss while working on an investigation, and it’s a tool commonly used by journalists, researchers and psychologists. These occupations can be similar to investigators in that they all strive to unearth issues as well as understand the psychology behind an individual’s actions.
Published in ACFE Insights Blog

E-payment through third-party channels or platforms — like Venmo, Cash App, Alipay or WeChat Pay — is widely used in our daily life, especially as COVID-19 spread and stay-at-home restrictions fueled precipitous growth of third-party payments. To understand these risks, let’s take a look at the third-party payment flow and bring out the iterated anti-money laundering (AML) measures as well as the major difficulties to implement them.
Published in ACFE Insights Blog

Bernadette Kakooza, CFE, is more than just an accomplished fraud fighter. As the first female Inspector General for the Detroit Public Schools Community District, she works hard for her geographic community as well as her anti-fraud community. In addition to spearheading investigations to save taxpayer money, she’s an active member of the Southeastern Michigan ACFE chapter and mentors fellow ACFE members.
Published in ACFE Insights Blog

Matthew Stock, J.D., CFE, CPA, is the director of the Whistleblower Rewards Practice at Zuckerman Law, where he leverages his experience as an attorney and external auditor to assist whistleblowers to investigate and disclose complex financial frauds to the government.
Published in ACFE Insights Blog

For me, one thing that came about during the pandemic is that my husband and I love watching movies together. We both have our favorite genres, but I especially enjoy a movie that involves parts of my career in the anti-fraud profession. Recently, on an ACFE Community discussion post, a question was posed: What is your favorite fraud movie?
Published in ACFE Insights Blog

In February 2021, a user known as Singularity0x01 posted a .ZIP file on RaidForums, an online forum used by hackers and cybercriminals to share leaked data. The file, entitled “Compilation of Many Breaches (COMB) 3.8Billion (Public),” contained usernames and passwords from potentially more than half of all internet users.
Published in ACFE Insights Blog

No-show jobs, where individuals collect paychecks without performing any actual work, may sound like something out of a mob movie, but they occur in a surprising range of real-world settings. From organized crime to family-run businesses and public corruption cases, these schemes reveal how falsified payrolls can become a vehicle for fraud, tax evasion and abuse of power.
Published in ACFE Insights Blog























Published in Videos








Published in Videos



We all know fraud isn’t a new phenomenon. But what plays in the news can surprise even the most skilled anti-fraud professional. Cases of multimillion-dollar companies entangled in fraud now take precedence over other kinds of criminal activity. But is the high-stake game of fraud limited to multimillion-dollar organizations?
Published in Fraud Magazine

In two unrelated but sadly similar cases, Harvey and Larry carried on secret, sexually aberrant lives that were decidedly at variance with their known, socially respectable lives. Unfortunately, Harvey and Larry encountered extortionists who exploited their secrets, which cost each man thousands of dollars and one his life.
Published in Fraud Magazine

I’ve thoroughly enjoyed writing this column for you. I hope it was useful. Fraudsters have more ways than ever to cook the books, and CFEs need to be diligent in monitoring and investigating the financial and nonfinancial reporting of companies. At one time, we thought financial reporting fraud didn’t have a lot of variety. But now this couldn’t be further from the truth.
Published in Fraud Magazine

Summary of recent ACFE Board of Regents' disciplinary actions
Published in Fraud Magazine

Activities at school districts typically generate local media coverage. In the case of the Simptomkin School District, the local newspaper ran an article about superintendent Smith’s annual performance review. The article noted that during his tenure, Smith’s scores on his reviews had steadily declined. The article also said that he’d been the subject of a police investigation resulting from his electronic communications with a female student.
Published in Fraud Magazine

Our natural inclinations tell us that the more information we have, the better decisions we can make, according to the author. However, thanks to one grocery store study, the opposite might be true. Read how a jam taste test proves that information overload can actually stymie a fraud examination.
Published in Fraud Magazine

Investigative reporter Andrew Jennings, the 2017 ACFE Guardian Award recipient, has been chasing bad men around the world for more than three decades. He’s dug into the crimes of the members of the International Olympic Committee. And his discoveries at FIFA have led to the eventual indictment and convictions of scores of fraudsters. And he’s still ready with the shovel.
Published in Fraud Magazine

HFCC, a fertilizer and chemical applicator, went bankrupt. Investigations discovered the owner committed bank fraud, financial statement fraud and performed fraudulent conveyances or fraudulent transfers. However, a judge ruled that the author and the company’s outside CPA didn’t prove the company was insolvent during all the transfers, which limited the penalties. Here the author proposes a better way to establish the date of the insolvency of an entity and thus recover more fraud proceeds.
Published in Fraud Magazine

For the uninitiated, witness prep (shorthand, of course, for witness preparation) is a standard practice in which civil and criminal trial attorneys meet with all the witnesses they’ve subpoenaed to testify in their cases. They review the cases and the witnesses’ anticipated testimony, and ... do that, over and over and over again.
Published in Fraud Magazine

Higher education must keep pace with changes in the world, and anti-fraud educators are no exceptions. While much has been written about changing delivery of courses and new ways of learning for millennials and Generation Z, actually altering traditional methods has been a slow process.
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

Andrew Jennings, an independent investigative journalist, has spent more than 15 years laboriously examining the economic intricacies of FIFA (Fédération Internationale de Football Association). His reporting of entrenched FIFA corruption — bribes, kickbacks, vote rigging and ticket scandals — eventually caught the attention of the FBI. In 2015, the U.S. Department of Justice indicted scores of FIFA-related officials under the U.S. Racketeer Influenced and Corrupt Organizations (RICO) Act and the U.S. Travel Act.
Published in Fraud Magazine

Fraud examiners use many investigative techniques in the course of a fraud examination including, but not limited to, document review and analysis, public records checks, surveillance and interviews. Seasoned CFEs will tell you they spend a great deal of time and effort in the document review — the investigation and analysis of paper trails, which provide us with many leads as we follow evidence in fraud schemes.
Published in Fraud Magazine

This aerospace case history illustrates how fraudsters are able to easily commit procurement fraud because they can hide behind “veils of trust” they have with organizations’ employees and victims. Here’s how to thrust back the curtains and let the light shine in on cozy arrangements.
Published in Fraud Magazine

Organizations can prevent massive, paralyzing frauds. And they can detect small frauds before they become massive frauds. Practical anti-fraud support is available in the new COSO/ACFE Fraud Risk Management Guide.
Published in Fraud Magazine

The ACFE Foundation has awarded $52,500 to college and university students through the Ritchie-Jennings Memorial Scholarship Program for the 2017-2018 school year. Each recipient also will receive a one-year ACFE student membership.
Published in Fraud Magazine

Although the Theranos saga is far from over — the company is fighting multiple lawsuits and regulatory actions — I’ll limit my analysis to the “Mad Money” interview. It provides us with valuable insights into how we can apply our interviewing skills as fraud examiners not only to the standard-type fraud examinations we deal with daily but also to unusual high-profile “personality cases” like Theranos.
Published in Fraud Magazine

We’ve all dreaded answering unanticipated job interview questions. When you’re caught off guard or just aren’t prepared, the tendency is to go with the first answer that pops into your head. Your response usually does little to improve your chances of continuing in the hiring process.
Published in Fraud Magazine

Harvard business professor Eugene Soltes is on a years-long quest to discover why topflight executives become white-collar criminals. His conversations with close to 50 convicted criminals so far have led to insights on hubris and humility — not just in them but in all of us.
Published in Fraud Magazine

In our firm’s recent assignments, we’ve faced several fraud schemes at our client companies because of poor bank account management. We’ve been amazed at the lack of internal controls. We observed these frauds on several continents, regardless of the maturity of company internal controls. In some cases, companies have lost a great deal — in finances and reputation. Executives in these companies, including the boards, have, of course, reacted strongly.
Published in Fraud Magazine

Identity theft, impostor scams, increased exposure through free Wi-Fi, ransomware, phishing schemes, spearfishing — these are no longer topics confined to fraud examiners or industry specialists. College students find themselves victims of fraud in increasing numbers.
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

Eugene Soltes, a Harvard Business School professor, wants to know why some C-suite executives appear to risk everything to commit fraud. Middle management and employees further down corporate ladders might do it because they’ve found a ready source of cash to ease their economic problems. However, top-flight business people seldom lack for anything; their organizations often reward them spectacularly. Why would they need to steal?
Published in Fraud Magazine

Erin Reitz, CFE, knew early on that she wanted to work as an investigator in financial crimes and has worked tirelessly during her career to help people who are unable to help themselves. She’s now a senior fraud risk analyst at the Federal Reserve Bank of Cleveland, a job that allows her to work with a team to help protect financial institutions and revenue collection for the U.S. Treasury.
Published in Fraud Magazine

Fictitious insurance claims filed by Joshua Miller, owner of a Syracuse hearing-aid dispenser, cost the New York state insurance fund $1.65 million. Learn how he, and others, edged the system to commit the crime.
Published in Fraud Magazine

The facts discussed in this article are based on the information provided in the indictment. All persons and entities are innocent until proven guilty. — ed.
Published in Fraud Magazine

In part one, experienced CFEs described how preparation and flexibility are the keys to good interviews. Here they discuss how they can discover surprising new evidence by asking incisive questions and waiting for serendipitous moments. We also cover question typology, body language, moving toward admissions and more.
Published in Fraud Magazine

College student employment scams have been common for many years and continue to proliferate because of their profitability. Students learn about these fraudulent “job opportunities” by visiting college employment websites at which fraudsters post phony ads or send via emails to their school accounts.
Published in Fraud Magazine

Family members, friends and caregivers often prey on defenseless adults. Here’s a “starter kit” to aid CFEs on how to gather and analyze financial, medical and real estate records; present cases to prosecuting authorities; and conduct successful interviews.
Published in Fraud Magazine

Longtime ACFE member, Michael G. Kessler, CFE, one of the New York-area’s foremost forensic accountants and private investigators, died June 6 at age 65 after a long battle with cancer.
Published in Fraud Magazine

As an ACFE member, you can enjoy the newly redesigned Fraud Magazine app, which offers streamlined readability and functionality. Enjoy every issue plus extra content such as popular topics, case studies and all-time top articles. Use the offline download function to access current or archived issues any time, any place.
Published in Fraud Magazine

It doesn’t matter what kind of organization makes the news — whether it’s a manufacturing plant, a sales and marketing company, an importer, a nonprofit, a university or a government entity — when someone behaves badly, someone else usually knows. Fraudsters seldom stop to consider the effects of their actions for their organizations and the people who are witnesses to and/or complicit in the fraud, nor do they let potential consequences change their behavior.
Published in Fraud Magazine

Published in Fraud Magazine

Fraud is a global problem, so companies worldwide continue to recognize the need for anti-fraud professionals. The 2017/2018 Compensation Guide for Anti-Fraud Professionals, a members-only resource, shows the ACFE’s ongoing effort to gather data that anti-fraud professionals need to ensure their careers are moving in the right direction.
Published in Fraud Magazine

Board of Regents expels two CFEs; corrections
Published in Fraud Magazine

More than 3,000 anti-fraud heroes gather at the largest anti-fraud conference in the world to learn new techniques in their fight against fraud.
Published in Fraud Magazine

On February 22, Swiss-based global engineering group ABB announced it was the victim of a $100 million internal embezzlement scheme in its South Korean subsidiary. The money and the alleged perpetrator vanished, and an international manhunt is so far unsuccessful. To the best of my knowledge, this is the largest case of employee embezzlement.
Published in Fraud Magazine

The ACFE Board of Regents ponder the exciting, frustrating and exquisite challenges of the fraud examination profession during the 28th Annual ACFE Global Fraud Conference.
Published in Fraud Magazine

Many organizations allow business-traveling employees to report certain expenses and receive reimbursement for these costs. Unfortunately, this can lead to expense reimbursement fraud. This fraud is a form of asset misappropriation in which an employee steals or misuses their organization’s resources.
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

It’s rare when former students fraudulently entering the U.S. are turned over to the federal government for prosecution. However, technically, the consequence should lead to permanent inadmissibility to the U.S. because of prior fraud or misrepresentation, according to the Immigration and Nationality Act of 1965.
Published in Fraud Magazine

Dr. Donald Cressey’s Fraud Triangle has endured because it’s correct and simple. However, the ACFE has never stated that the triangle can explain every case of fraud. So, be careful when you use the Fraud Triangle in court. The judge might reject it. The Fraud Triangle is a useful tool to help us understand why and how people commit fraud, but it’s not a scientific theory.
Published in Fraud Magazine

I’m taking over this column just this once to tell you that ACFE President James D. Ratley’s autobiography, “Policing Fraud” is finally out. It’s a terrific read as you’ll see for yourself. But even in his own words, the book can’t quite capture Jim’s essence. If there’s anyone who knows, it would be me — we’ve been together over 31 years.
Published in Fraud Magazine

Rick Schumacher, CFE, says he’s always wanted to achieve a more complex understanding of rationalization. He spent years as a cross-cultural communication specialist in the U.S. military, but says he felt a need to link that knowledge to fraud and misconduct. “I started looking to broaden my exposure at a large, multinational organization with a footprint in international markets,” he explains. Schumacher found that at Nissan Motor Corporation as a senior global compliance investigator.
Published in Fraud Magazine

Longtime ACFE member, Michael G. Kessler, CFE, one of the New York-area’s foremost forensic accountants and private investigators, died June 6 at age 65 after a long battle with cancer.
Published in Fraud Magazine

Long before James D. Ratley, CFE, helped form the ACFE with Founder and Chairman Dr. Joseph T. Wells, CFE, CPA, he had worked with the Dallas Police Department as a street cop, and on the vice squad, in internal affairs, the child abuse unit and other departments. In 1985, he was part of a joint task force assembled to investigate possible widespread fraud at the Dallas/Fort Worth International Airport (DFW). In this excerpt from his autobiography, “Policing Fraud: My Journey from Street Cop to Anti-fraud Leader,” Ratley describes some of the skills he’d later apply and teach as an ACFE leader. — ed.
Published in Fraud Magazine

Congratulations! You have a fraud hotline, but now what? It’s useless without investigation and communication. The author outlines his experiences creating a fraud mitigation program for his multibillion-dollar company.
Published in Fraud Magazine

Once fraudsters have identified the individual who has the authority to perform wire transfers, fraudsters search social media websites and phishing emails to learn more about this person before they precede with the BEC scam. They can gain an accurate understanding of the roles that individuals perform in a business and the messaging procedures for wire transfers.
Published in Fraud Magazine

Imagine an organization in the middle of an accounting investigation related to the recording of fictitious revenues. The organization’s external auditors have now come to perform the year-end audit and opine on the current year’s financial statements. The organization, as it should, informs the external auditors of the investigation. These auditors naturally begin to ask questions about the investigation.
Published in Fraud Magazine

Jeff Filliter was working at a bank in Canada when he was flown to Mexico City to investigate the murder of a 41-year-old branch manager who was last seen entering the back seat of a black Jaguar after work a few days earlier. What Filliter, a CFE and investigator of more than 40 years, relayed to attendees at the 2017 ACFE Fraud Conference Canada in Toronto earlier this month was a story straight out of a Netflix series. The six-year, multijurisdictional fraud and money laundering investigation is also the subject of Filliter’s newly released book, The Shallowest of Men.
Published in Fraud Magazine

Organizations throughout the world use benchmarking data to evaluate how their performance, structure and operations compare to those of their peers. Benefits of benchmarking include assessing operational efficiency, pinpointing knowledge gaps and identifying areas for potential improvements.
Published in Fraud Magazine

Nine candidates have been selected to compete for three positions on the 2018-2019 Board of Regents. The board sets standards to promote professionalism and to ensure the reputation of the CFE credential. “The committee has a very difficult task paring down the final selections from a vastly qualified group of CFEs,” said James D. Ratley, CFE, president of the ACFE and chairman of the ACFE Nominations Committee. “I would like to thank all the applicants who participated in this very important annual event.”
Published in Fraud Magazine

Fraud is a non-violent offense, right? Most times. But this is the story of how fraudulent economic arson in a small suburban neighborhood in Indianapolis, Indiana, turned deadly. Community members are reassembling their lives. Here are lessons from the investigation for discovering evidence on arson-for-profit cases.
Published in Fraud Magazine

Martin Shkreli’s fraudulent activity as a hedge fund manager led to his arrest, trial and conviction on securities fraud. This is the first fraud trial since Bernie Madoff’s to garner such media attention, public interest and academic discussion. But that wasn’t just because of Shkreli’s reputation for frequently and outlandishly using social media or his lawyer quoting Lady Gaga in his opening statement.
Published in Fraud Magazine

Dr. Sam Foote didn’t plan to be a whistleblower. He didn’t even plan on being a doctor, let alone one in the U.S. Veterans Affairs Department (VA) during the height of scandal in Arizona. But the moon landing in 1969 altered the course of his future and potentially the lives of thousands of U.S. veterans.
Published in Fraud Magazine

Recent economic crimes have only highlighted the need for more qualified anti-fraud professionals. Many universities and colleges across the U.S. now offer courses that provide such training for students. The ACFE Anti-Fraud Education Partnership supports this growth by providing expert training to accounting, auditing and other business students plus educational tools and resources to instructors.
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

Unlike the bank, retail, health care and insurance sectors, discovery of fraud in education is still evolving. School reform, growth of for-profit universities, expansion of distance learning programs, restriction of student loan debt forgiveness and school vouchers represent just a few challenges impacting the landscape.
Published in Fraud Magazine

I've met many whistleblowers in my time, and what’s always resonated with me is that they persist despite nearly impossible odds. Dr. Sam Foote, a physician with a genius mind and audacious spirit, persisted when he found himself facing Goliath: the Phoenix Veterans Affairs (VA) Health Care System. When scandal rocked the department in Arizona, he didn’t back down.
Published in Fraud Magazine

“It’s fascinating to me how CFEs each have a different ‘investigative fingerprint,’ ” says Wendy Evans, CFE, senior corporate ethics investigator at Lockheed Martin. Evans’ investigative fingerprint first formed when she began her career as a radio reporter. She says she honed her ability to take a broad subject and condense it into concise sets of 30-second sound bites.
Published in Fraud Magazine

You’re in the grocery store, and you’re pleased with yourself. You’ve just chosen a beautiful bottle of extra-virgin olive oil labeled with a picture of verdant Italian olive groves. Unfortunately, the liquid in that bottle also contains soybean, corn, sunflower, cotton, hazelnut, peanut and palm oils. Olive oil fraud is rampant. Here’s how the oily criminals commit their crimes and how to prevent them.
Published in Fraud Magazine

Here are five employee faces to look for when trying to prevent procurement fraud, abuse and noncompliance. Their aberrant behavior can lead to manipulated purchasing systems plus major financial and reputational losses, potential litigation and/or contract termination.
Published in Fraud Magazine

In 2016, we surveyed 18 Swiss companies — only banks and insurers — about their anti-fraud training programs.1 The findings can be benchmarks for organizations and provide insights into how to enrich programs. Much of our study’s results are easily transferable to any industry in any country.
Published in Fraud Magazine

Juice jacking is a form of cyberattack in which a malicious hacker can gain access to personal or sensitive corporate data stored on a personal or business-issued mobile device or inject malicious code into it when an unsuspecting victim uses a compromised public charging station at an airport, business center or hotel at a conference or other public place. All travelers, especially frequent ones, are at a heightened risk of this type of data breach that can lead to increased identity theft activity.
Published in Fraud Magazine

The author, a former Los Angeles Times reporter, provides a first-person account of how his newspaper broke the Wells Fargo scandal — how employees opened millions of unauthorized deposit and checking accounts, often transferring funds from consumers’ existing accounts without their knowledge or consent.
Published in Fraud Magazine

What do pizza chains, horror movies and ski lodges have in common with rockets, satellites and space stations? The U.S. National Aeronautics and Space Administration (NASA) has paid for all these things, whether knowingly or unknowingly.
Published in Fraud Magazine

SWIFT messages are often the most significant primary sources of information for investigators conducting forensic inquiries into possible money laundering, sanctions violations and other forms of financial malfeasance. But while SWIFT messages are standardized, they aren’t very user-friendly, and investigators can encounter a number of potential issues when they extract, process, store, and analyze them.
Published in Fraud Magazine

Here’s a simple way to help prevent health care fraud. Patients, with their doctors’ consent, can audio record doctor visits with their smartphones. Audio recordings can verify bills submitted for health care services. And medical providers can upload and store audio files in patients’ electronic medical records to help ensure the veracity of physicians’ diagnoses and interventions.
Published in Fraud Magazine

The Toshiba Corporation has struggled since at least 2008 to meet its financial targets. In 2015, the company made a shocking admission: Because of its struggles, Toshiba had committed a multi-year $1.22 billion accounting fraud that culminated in the resignation of CEO Hisao Tanaka in July of that year. What made this most surprising was that Toshiba had been perceived as “a totem of strong and virtuous Japanese corporate governance.”
Published in Fraud Magazine

Alexis C. Bell, CFE, PI, and Vidya Rajarao, CFE, CA, took their oaths of office as newly elected members of the Board of Regents during the board’s semi-annual meeting on February 22 at ACFE headquarters in Austin, Texas.
Published in Fraud Magazine

You have to decide if an anti-fraud life is your path. I knew it was for me, so I didn’t give up when faced with initial rejection. I can help you avoid some of the common mistakes when trying to enter this promising field.
Published in Fraud Magazine

All fraud cases leave trails. It’s like a kid’s connect-the-dots puzzle. At first glance the puzzle looks like a bunch of randomly scattered spots. But you draw a line linking the specks in the proper sequence that reveals a clear outline of a picture. However, unlike the typical puzzle, in which the dots are usually located in one area, related dots in fraud cases are often scattered throughout multiple jurisdictions, financial institutions, bank accounts, transactions, witnesses, suspects and so on.
Published in Fraud Magazine

On Feb. 22, 2017, the ACFE Board of Regents voted to permanently expel Jeffrey Hughes, CFE, of Lawrenceburg, Tennessee, in accordance with the recommendation of the ACFE Board of Review for violating Article II of the ACFE Code of Professional Ethics. The decision was based on Hughes’ convictions for “Theft of Property - $250,000 or More” and “Theft of Property - $10,000-$60,000,” both felonies under Title 39 of the Tennessee Code.
Published in Fraud Magazine

Delayed responses to impending financial disasters can send shockwaves through investor and shareholder communities, and can create cracks in the pillars of corporate ethics and fiduciary responsibility. Here we explore how one high-profile company waited too long to respond to faulty vendor parts on computer motherboards, which led to compounded market share loss, accounting irregularities, customer lawsuits and an SEC investigation.
Published in Fraud Magazine

Fraud is a global problem with no geographic boundaries. While there are many differences in laws and practices from country to country, the biggest challenge to becoming a true citizen of the world is understanding, and appreciating, cultural differences. Students are encouraged to study abroad during their college years to develop global perspectives. Studying the U.S. Foreign Corrupt Practices Act (FCPA) and its effect on business helps students and faculty develop global points of view.
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

Jennifer Shasky Calvery has been fighting money laundering and other crimes for years — first at the U.S. federal government and now as the Global Head of Financial Crime Compliance at HSBC Bank. Before joining HSBC in 2016, she was director of the Treasury Department’s Financial Crimes Enforcement Network (FinCEN) for four years after a 15-year career at the U.S. Department of Justice. She’ll be receiving the ACFE Cressey Award at the 28th Annual ACFE Global Fraud Conference.
Published in Fraud Magazine

I see many similarities between ski jumping and being a CFE,” says Placide Schmidiger, CFE, head of corporate special investigations at a global logistics company in Switzerland. He says that both require immense preparation. “When I ski jump, I must be prepared mentally and physically. I also analyze the particularities of the jumping hill, the wind and snow conditions, the condition of my equipment, and so on.”
Published in Fraud Magazine


We asked some experienced CFEs to ponder their interviewing philosophies and techniques. Their responses are diverse and thought-provoking. Now let us know what you think.
Published in Fraud Magazine

Jennifer Shasky Calvery, the recipient of the 2017 ACFE Cressey Award, fought fraud for 20 years in the U.S. federal government — most recently as the FinCEN director. Now she uses her experience to tackle money laundering and other crimes in the international banking world.
Published in Fraud Magazine

Health care fraud examinations can be laborious. Discovery of evidence can be elusive. You need the most reliable sources and resources. Here’s a practical sampling of some of the best places to start from a fraud examiner who’s worked scores of cases.
Published in Fraud Magazine

Travel scams have been around for years, and fraudsters continue to come up with new versions. Vacationers need to be especially careful from the beginning when they book their travel plans and throughout their entire vacations as fraudsters wait to hijack their personally identifiable information (PII) and use it for identity theft purposes.
Published in Fraud Magazine

Do employees make conscious decisions to commit fraud, or are they so morally disengaged that they don't associate their actions as unethical or unlawful? Does moral disengagement negate their responsibilities because they don't understand the negative effects of their acts?
Published in Fraud Magazine

An internal auditor usually analyzes an organization’s ethics when it has an important impact on other key governance aspects, such as risk management, compliance, strategy and how it conducts its business. Strong ethics helps an organization perform better. Here are some practical difficulties that auditors might face when auditing an organization’s governance (not an exhaustive list):
Published in Fraud Magazine

On Sept. 9, 2016, Audible released the first episode of “Ponzi Supernova: Madoff Speaks,” a six-part series hosted and reported by Steve Fishman. The series focuses on the $65 billion Ponzi scheme at Bernard L. Madoff Investment Securities LLC, spearheaded by Madoff, which crumbled with the 2008 financial crisis. As many have said before me, this is a great series for fans of the “Serial” podcast, but for anti-fraud professionals this also serves as an in-depth look into a disturbing case of widespread, unchecked fraud.
Published in Fraud Magazine

Certified Fraud Examiners elected Alexis C. Bell, CFE, PI, and Vidya Rajarao, CFE, CA, to the 2017-2018 ACFE Board of Regents from six candidates selected by the board’s nomination committee. Bell and Rajarao took office at the board’s meeting in February at ACFE headquarters in Austin, Texas.
Published in Fraud Magazine

When the ACFE first started, it was called the National Association of Certified Fraud Examiners and it didn’t operate globally. In LeVie’s 25 years, she’s seen substantive growth domestically and abroad.
Published in Fraud Magazine

On Sept. 18, 2015, the U.S. Environmental Protection Agency (EPA) issued a notice of violation of the Clean Air Act to German automaker Volkswagen Group. The EPA contended that Volkswagen had intentionally programmed diesel engines to activate certain emissions controls only during laboratory emissions testing.
Published in Fraud Magazine

Some wealthy wine aficionados are comfortable spending millions on supposedly rare vintages. But if they discover that they’re holding hundreds of bottles of worthless wine they might try to unload it to less sophisticated collectors, and bogus wines will continue to circulate. Here are some cases to illustrate the problem and ways to investigate the fraud.
Published in Fraud Magazine

As professional anti-fraud practitioners we should take a page out of academics’ playbooks and get published too. You don’t have to publish in academic scholarly journals. You can share your ideas in many trade and practitioner journals, magazines or newsletters, including Fraud Magazine.
Published in Fraud Magazine

What happens when a CFE’s friend falls into fraud? This veteran interviewing expert grapples with the duality of a young Jekyll and Hyde who became a fraudster, next an informant and finally back into deep deception.
Published in Fraud Magazine

The FBI had tasked Eric O’Neill to investigate Robert Hanssen, a 25-year FBI veteran and suspected spy for the Russians, but he’d have to do it face to face as Hanssen’s office assistant. O’Neill’s courageous work helped bring Hanssen down and end the greatest security breach in U.S. history.
Published in Fraud Magazine

Frequently, CFEs who investigate financial crimes are tasked with obtaining financial records from banks, credit unions, credit card companies, investment houses, mortgage lenders and other institutions to help determine whether a financial crime has been committed and the dollar dimension of the crime.
Published in Fraud Magazine

As tools for teaching and methods of delivery have evolved, so has anti-fraud education. The members of the ACFE Higher Education Advisory Committee are interested in advancing anti-fraud education in colleges and universities.
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

Have you ever been asked to review procurement practices for your organization or as a third party? Procurement is prone to corruption and bribery and can cost large organizations millions of dollars annually. Here I shed light on some of the best tools and techniques fraud examiners can use to combat procurement fraud.
Published in Fraud Magazine

Here's the situation. You’re a new FBI undercover field operative. But the bureau has called you into headquarters, put a suit and tie on you, and ordered you to take a desk job as the assistant to a longtime FBI special agent and computer systems expert. You’ll be locked in a soundproof, two-office vault to do one thing: covertly surveil this man suspected of being a master spy for the Russians.
Published in Fraud Magazine

“Strive to be great even when others doubt your capabilities,” says Chris Blunt, CFE, senior fraud investigator at Toyota Financial Services. Blunt has lived by this motto throughout his career, even when an injury on the job became motivation to work his way into the fraud-fighting field. Realizing he could contribute more to the corporate environment, Blunt applied for an entry-level job at Toyota and worked his way to a senior-level position. And he credits obtaining his CFE credential for helping him get there.
Published in Fraud Magazine

Scott London, a senior partner at a Big 4 accounting firm, shared inside secrets to help a buddy in a tight financial spot. After following the rules for 26 years, why would he commit fraud? Insider traders — mostly males — do it for the money, of course, but they’re also influenced by hubris, feelings of conquest, playing seduction games and adrenaline highs.
Published in Fraud Magazine

This column offers a diverse sampling of four recent research studies that might benefit your daily efforts to curb fraud, improve detection and contribute the most value to your limited time. The brief review of these research studies extracts some of the most practical aspects of recent academic literature with a link to each paper for you to obtain more details.
Published in Fraud Magazine

Gambling is an attractive entertainment option for some, but it can also be a hotbed for money laundering, organized crime and other illicit activity. That means, of course, job opportunities for CFEs in a growing field. Can CFEs help deter bad actors from defrauding gaming operations?
Published in Fraud Magazine

Technical support scams are very lucrative because fraudsters have a captive audience of electronic device users who know the importance of keeping updated with recent security software and, as a result, will normally listen to spiels about an offer to do a “free” check to spot malware on their computer or “new” software products that they can purchase that supposedly will fix current or future security problems. But, alas, good things sometimes have dire consequences.
Published in Fraud Magazine

During my six-plus years as a regional bank fraud investigator I’ve delved into a legion of cases categorized as romance or sweetheart scams. You might believe that only simpletons fall prey to romance hustles, but con artists don’t discriminate. Victims are male, female, young, middle-aged, elderly, benighted, well-bred and of various races, creeds and nationalities.
Published in Fraud Magazine

Fair value is one of the more complicated and controversial areas of accounting. Some assets and liabilities are initially recognized at their fair values, and some of those are subsequently adjusted to account for changes in fair value.
Published in Fraud Magazine

Sidney P. Blum, CFE, CPA/CFF, Leah D. Lane, CFE, and Nancy E. Rich, CFE, took their oaths of office as newly elected members of the Board of Regents during the board’s semi-annual meeting on February 25 at ACFE headquarters in Austin, Texas.
Published in Fraud Magazine

In part 2, the author applies his unique letter analytic techniques to a variety of examples, including keyword searches and predictive analysis using benchmark data. The aim? Finding fraud in the words.
Published in Fraud Magazine

When fraud examinations cross borders and cultures, interpreting services are crucial. Here you’ll learn what to do before, during and after an interaction with a foreign-language speaker and how to effectively communicate through the use of an interpreter.
Published in Fraud Magazine

In early 2013, employees of a trucking company were trying to use their health care benefits, but their doctors and hospitals were rejecting them. Their insurance carrier was denying their claims. Their paychecks showed their employer had been deducting their shares of medical insurance premiums, but their insurance cards were worthless.
Published in Fraud Magazine

This study shows that untrained employees are the linchpins for most data breaches. Organizations can help prevent them if they're filled with savvy and aware employees at all levels.
Published in Fraud Magazine

Sometimes the seemingly subtle yet damaging impact of poor leadership can make it difficult to identify as a root cause. In other cases, it’s clear something is wrong, but the leaders are in denial of their shortcomings and will attribute all other possibilities to explain their ineffectiveness.
Published in Fraud Magazine

Budding fraud examiners, of course, need to learn how to conduct effective interviews. Most major fraud examination textbooks discuss the interviewing process and many are excellent primers. The ACFE and other organizations produce excellent training videos.
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

Let’s say you find an accounting regulation violation that your organization might have ignored for years. You bring your concerns to your boss who agrees you’ve discovered a problem. Other accounting department staff members concur until they figure out the restatement costs. You stew over this and realize that your organization is breaking the law.
Published in Fraud Magazine

"I’m passionate about educating people about health care fraud and creating a fire in others that will ultimately fuel the fight for future generations," says Jala Attia, CFE. "Many people don’t realize the extent of the problem we’re facing."
Published in Fraud Magazine

Tony Menendez, CFE, found some questionable accounting practices at Halliburton. When he realized the company was knowingly violating Securities and Exchange Commission rules — and the SEC wasn’t going to investigate — he brought a whistleblower claim against Halliburton for violating his rights under the Sarbanes-Oxley Act. After a nearly nine-year fight, he was vindicated.
Published in Fraud Magazine

The ACFE’s Report to the Nations on Occupational Fraud and Abuse has led to the classification and analysis of thousands of occupational frauds. But, perhaps, more importantly, it has shown organizational management and the public the dire need for well-planned fraud awareness, deterrence and prevention programs.
Published in Fraud Magazine

Writing skills are essential in this profession. The most successful fraud examiners, investigators, attorneys and business people are those who can write clearly, articulately and persuasively using facts they’ve uncovered in the course of the fraud examination.
Published in Fraud Magazine

Fraudsters know that we sometimes get rushed and make mistakes when we dial telephone numbers. So they’ve purchased hundreds of telephone numbers, including those of the toll-free variety, that are similar to common business numbers — except for one digit.
Published in Fraud Magazine

The ACFE has collaborated with the Committee of Sponsoring Organizations of the Treadway Commission (COSO) to produce the Fraud Risk Management Guide (FRMG) to help organizations focus their anti-fraud efforts.
Published in Fraud Magazine

Lives Well is a fictional name for a real perpetrator of transaction laundering. It’s the kind of company that flies through automated application checks for most financial products because this thoroughly modern-day enterprise is nothing but a front — an empty shell company hiding a dark secret.
Published in Fraud Magazine

In one week in June, more than 3,000 fraud fighters met in Las Vegas to fill up their tanks and charge their batteries with hours of practical anti-fraud techniques and networking with peers. And to revel in their value to the anti-fraud profession.
Published in Fraud Magazine


As technology continues to shape the world, advances in travel and communications have made international business easier to conduct. Anti-fraud professionals can reap the benefits of these advances to help prevent and detect fraud. But heed this caveat: The playing fields are changing. Border-crossing frauds are presenting new challenges to fraud examiners.
Published in Fraud Magazine

What happens when you fill a boardroom with highly intelligent people and ask them a few questions about fraud topics? You yield 90 minutes of insights that can’t be contained in one article. In this article, the Board of Regents discuss new frauds on the horizon, data breaches, new practices and training millennials as practitioners.
Published in Fraud Magazine

Many naïve taxpayers — who believe that all tax preparers have to be certified, licensed or regulated in some way — place their entire trust in supposed experts to handle one of the most serious dimensions of adult life.
Published in Fraud Magazine

Organizations in every industry sector — private and public — need to step up to the plate and develop comprehensive risk management strategies that include strong ongoing data protection and security awareness programs to help protect the PII and other sensitive information of their customers, clients and employees.
Published in Fraud Magazine

The Utah legislature began to fight back against affinity fraud in 2011 when it modified the Utah Uniform Securities Act to include harsher penalties for those who used positions of authority to defraud others or who preyed on adults who are impaired because of age, mental or physical disability. The battle continued in 2015 with the White Collar Crime Registry (WCCR).
Published in Fraud Magazine

Future fraud fighters, whatever their specialties, benefit greatly from having opportunities to practice skills such as interviewing and expert-witness testimony. Who better than a practitioner to help bring these activities to the classroom?
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

Ryan Duquette, CFE, CFCE, author of the cover article, quotes studies that show that half of all departing employees leave with confidential company information — either deliberately or unintentionally. That’s sobering. How are your organizations deterring the fraudulent flow of intellectual property out the door?
Published in Fraud Magazine

“My greatest achievement is my ability to reinvent myself as I encounter different points in my life,” says Cristiane Soares, CFE, senior investigator at TD Bank. Soares reinvented herself when she moved from her home country of Brazil to Canada to study English.
Published in Fraud Magazine

Don’t let departing employees leave with valuable intellectual property. Use digital forensics in daily workflows before they resign and in exit interviews to prevent IP theft rather than potentially be involved in litigation after they’re gone.
Published in Fraud Magazine

For years, companies reported their figures under GAAP or IFRS standards. But what happens when a company commingles the GAAP/IFRS-based financial information with other performance metrics in its reports and press releases? These extra measures have no standards, and no one audits them — perfect conditions for fraud.
Published in Fraud Magazine

As a former student member of the ACFE, I can’t think of a better way for budding fraud examiners to explore the profession than as members of university ACFE student chapters. They not only learn valuable anti-fraud skills, but they meet professionals and make contacts that can lead to internships and jobs.
Published in Fraud Magazine

According to the FBI’s Internet Crime Complaint Center (IC3), in most cases the fraudsters claim to work for cable or internet companies and offer to resolve technical problems with victims’ routers, modems, digital cable boxes or connections to the internet.
Published in Fraud Magazine

The world knows Orville and Wilbur Wright as the team that designed, built and flew the first successful powered flight in a heavier-than-air machine. However, few know that Wilbur and his older brother, Lorin, once came to the aid of their father, Bishop Milton Wright, an itinerant “circuit” preacher, to expose suspected financial abuse in the United Brethren Church.
Published in Fraud Magazine

Crime, of course, doesn’t pay. And committing another crime in an attempt to resolve the financial consequences from the first will only dig the perpetrator into a deeper hole. In Dixon’s case, she narrowly avoided jail time for her initial fraud at Classen, but she’s now serving time for the Tompkins County probation violation and could serve even more from the drug charge in Nebraska.
Published in Fraud Magazine

Financial identity theft occurs when someone misappropriates your personal information to open new accounts, or uses your existing bank or credit accounts to make purchases. A newer type of identity theft — criminal identity theft — is spreading across the country and can be even more damaging than having a criminal destroy your credit rating.
Published in Fraud Magazine

Greed is everywhere. It pollutes all industries and organizations, including those dedicated to helping the poorest and most vulnerable of our society. And it breeds fraudsters within these organizations who have profound canniness and precisely zero moral queasiness when selecting their victims. Fraudsters like Emma and Kate.
Published in Fraud Magazine

Because of worldwide laws, hotline-reporting programs are ubiquitous. But many fail because employees don’t trust them. Here’s how to ensure you have a quality system that concerned employees will use without fear of retribution.
Published in Fraud Magazine

This column’s cases deal with improper accounting for special arrangements made with customers. Companies go to great lengths to meet sales goals, including offering special incentives for customers to buy their products. But the accounting rules provide a framework for how and when such incentives should be reflected in a company’s financial statements.
Published in Fraud Magazine

The ACFE Foundation has awarded $55,000 to college and university students through the Ritchie-Jennings Memorial Scholarship Program for the 2016-2017 school year. Each recipient also will receive a one-year ACFE student membership.
Published in Fraud Magazine

What? You didn’t get that job offer you were hoping for, even though you followed all the right strategies and tactics (hopefully the ones I’ve previously recommended in this column)? Well, you have no control over some of the variables in the hiring process, such as the economy, the fraud examination profession and regulatory compliance that stymies job growth, among others.
Published in Fraud Magazine

Cybercrime and identity theft have evolved into a sophisticated global economy. Perpetrators use the anonymity provided by digital currency and the internet to hide themselves, their criminal acts and their gains. This nine-year cybercrime investigation case illustrates one of the few law enforcement successes in fighting these crimes.
Published in Fraud Magazine

In this column, we’ll discuss the details of how instructors can prepare in-class practical applications so students can develop and practice their interviewing skills. I’ll supply the specific steps of preparation and execution of the in-class practical interview exercise. (See sample copies of the scenario outline and related documents discussed below at fraudscenarios.com.)
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

In our cover article, "Top 10 factors leading to hotline distrust: Understanding why no one calls," authors Ryan Hubbs and Julia Kniesche write that whistleblowers have always been subject to false allegations, retribution from management and even dismissal.
Published in Fraud Magazine

Guest columnists Howard Wang and Kent Kedl posit that traditional investigations don’t work well in China because of ingrained features of China’s business and legal environment. They suggest changes that will help foreigners in their fraud examinations.
Published in Fraud Magazine

Charles Washington, CFE, has learned over his many years in the anti-fraud profession that it takes tenacity, patience and good communication to discover and remediate fraud. As a director – global security, Americas, Washington is responsible for drug diversion and drug discount pricing fraud investigations at Pfizer.
Published in Fraud Magazine

A major finding of this study is that contrary to public opinion data breaches have hit organizations of all sizes and in every type of industry. Nobody is safe. Immunize your employees to prevent the insidious infections.
Published in Fraud Magazine

Alexandra Wrage, founder and president of TRACE International and a former member of FIFA’s Independent Governance Committee, shares her thoughts on last year’s FIFA scandals, the recent release of the Panama Papers and the keys to tackling global corruption through anti-bribery and corruption compliance support.
Published in Fraud Magazine

As I walked up to the podium to make a presentation at a fraud seminar at the Rutgers University Business School, I looked out into the audience. I saw students, law enforcement veterans, New Jersey ACFE Chapter members, auditors and accountants. And I wondered how many sitting there were going to be our future CFEs.
Published in Fraud Magazine

The leak of the huge cache of offshore data in the Panama Papers reveals decades-old shell companies — many of which fraudsters have used to launder money and hide crimes. How can fraud examiners use the data? Will the revelations cause governments to overcompensate with overbearing regulations? Or will the exposé ultimately be ignored because unethical systems are so entrenched?
Published in Fraud Magazine

Fraudsters, who find bankruptcy information and contacts in public records, are effective because they prey on the fears of stressed, panicked victims.
Published in Fraud Magazine

While today’s leading virtual currencies, like bitcoin, may or may not pass the test of time, the underlying technology is here to stay. Innovators are taking us into a new realm in the exciting (and to some, terrifying) world of virtual currency. How do we prevent criminals from abusing the system in this still fairly new technology?
Published in Fraud Magazine

Unaoil, a Monaco-based oil consulting company, was recently exposed in a media investigation for potentially supporting or facilitating bribes on behalf of large multinational firms in the oil and gas industry. The Unaoil case provides several lessons on using forensic email reviews to help gather evidence or indications of fraud, misconduct and regulatory non-compliance.
Published in Fraud Magazine

Why is it such a challenge to control opioid abuse? It’s a combination of the sheer number of pharmacy claims and the woefully outdated manual methods used to review them. The slow, labor-intensive process of manually inspecting spreadsheets, even those generated from a database, can lead to false positives. It also uses time and resources that should be spent tracking down those who are actually committing FWA. The sheer size of data can cause processing time and infrastructure issues, and overwhelm the system.
Published in Fraud Magazine

In this edition, I’ll examine some recent cases involving improper accounting for inventory resulting in overstated assets. As with so many of the companies in the cases I profile, the players in two of the three cases were motivated primarily by a desire to meet published or internal goals for gross profit.
Published in Fraud Magazine

The ACFE Nominations Committee has selected six candidates to compete for two positions on the 2017-2018 Board of Regents. The board sets standards to promote professionalism and to ensure the reputation of the CFE credential.
Published in Fraud Magazine


Auto insurance fraud is a global fraud phenomenon with billions in losses. This primer will cover the basics plus an innovative way to combat it: social network analysis (SNA). SNA tracks claims patterns among individuals, vehicles, and locations involved in accidents, as well as supports entities such as repair shops, law firms and medical clinics. The result? Evidence discovery.
Published in Fraud Magazine

As reported in the media on September 9, Wells Fargo negotiated a deal to settle a lawsuit filed by the U.S. Consumer Financial Protection Bureau, the Office of Comptroller of Currency, and the City and County of Los Angeles. As part of the $185 million settlement Wells Fargo didn’t admit to any wrongdoing. However, it did confirm to the regulators and media that employees had opened more than two million checking, savings and credit card accounts without customer approval.
Published in Fraud Magazine

In part one of this two-parter, we examined the schemes of Bonnie G, a self-styled tax preparer who worked out of her basement creating federal and state income tax returns for her clients that contained lies cut from whole cloth to falsely qualify her clients for tax refunds and induce them to continue using — and paying for — her services. Here we’ll examine the simpler but equally effective (or lucrative) scheme of Donnie Z., another tax preparer who never made it out of the basement.
Published in Fraud Magazine

What tears at the fabric of a small town? Theft, betrayal and a loss of confidence in the very institutions that make the town a great place to live. This is the story of how a small gap became a gaping hole in oversight, management and internal controls, which resulted in a theft of more than $250,000.
Published in Fraud Magazine

Corporate management has significant latitude in choosing what numbers to report and when. But business pressures can cloud their judgment. This article examines how using accounting gimmicks and manipulating financial statements might satisfy investors but can cross into fraudulent territory.
Published in Fraud Magazine

Canada’s history and reputation as a “fraudster’s playground” might finally be coming to an end as regulatory and enforcement authorities enter a more well-rounded anti-fraud regimen. In the past, Canada’s approach to fraud was plagued with inadequacies, which left investors vulnerable and victims with little chance of recovery.
Published in Fraud Magazine

Whether we’re teaching how to interview, give expert witness testimony or prepare clients’ reports, storytelling is an integral component. How can we provide memorable experiences for our students while making sure that we cover foundational information successful fraud examiners need to know?
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

Kathleen Daly, Ph.D., professor of criminology and criminal justice at Griffith University in Brisbane, Australia, coined the term “pink-collar crime” in her 1989 article, “Gender and varieties of white-collar crime,” in the academic journal, Criminology, to describe the growing number of lower- to mid-level office women — bookkeepers, office managers, accountants, clerks — who steal from their employers.
Published in Fraud Magazine

The editors of Fraud Magazine know the value of a good story. They like to begin feature articles and many of the columns with case histories because they know you want illustrations of fraud examination principles in action.
Published in Fraud Magazine

Although CFEs might not regularly come across microcap stock manipulation, it’s important to be aware of the methods and motivations behind this significant criminal activity. (A microcap is a publicly traded company whose stock might be worth only pennies, which causes prices to be volatile and easier to manipulate.)
Published in Fraud Magazine

“Fighting fraud isn’t a career for individualists or opportunists,” said Marcel Simonis, CFE. “Fighting fraud is a team effort that includes a lot of hard work, and involves employees with complementary skill sets who can effectively communicate, listen and share their opinions, and work collaboratively to achieve the best results for the business.”
Published in Fraud Magazine

Identity theft attracts fraudsters because they can steal significant amounts with extreme anonymity, and victims and law enforcement can seldom pursue them. However, the authors describe an investigation that yielded the arrest and prosecution of a fraudster who used “synthetic identity theft” and other crimes to steal millions. Learn about their practical methods and a stunning twist.
Published in Fraud Magazine

According to the ITRC, fraudsters sent emails to New York teachers from two school districts purportedly from their superintendents asking them to send their PII, including Social Security numbers. One employee complied. Instant compromise. Phishing schemes, the most common of fraudsters’ mechanisms for stealing PII and using it for identity theft purposes, come in two types: mass driven and custom made.
Published in Fraud Magazine

When your work duties revolve around auditing or the detection of fraudulent behavior, the Fraud Triangle model is a useful resource in identifying potential offenders or situations. But what if your duties involve risk assessment or training? The Fraud Triangle can also provide a visual analysis of future business decisions and the building blocks of instructor-led training.
Published in Fraud Magazine

While it’s crucial that CFEs are aware that mobile devices — smartphones and tablets — bring fraud risks to organizations, it’s also critical that they know the risks of using their own mobile devices in professional settings.
Published in Fraud Magazine

With a nod to Pete Townshend and The Who, many auditors have expressed their determination to not get fooled again after being deceived by creative fraudsters. One of the underlying questions in many of the cases I’ve profiled is: “What did the auditors do?”
Published in Fraud Magazine

The "Research Findings" column and "Back Home to the ACFE" are corrected.
Published in Fraud Magazine

International Fraud Awareness Week 2015 last November was another great opportunity for fraud fighters around the world to educate the public about preventing and deterring fraud.
Published in Fraud Magazine

For the second year, the ACFE challenged its local chapters to raise funds for the ACFE Foundation’s Ritchie-Jennings Memorial Scholarship program. Chapter leaders once again answered to call to help college students continue the fight against fraud.
Published in Fraud Magazine

Nearly 15 years ago the actions of Enron’s C-suite executives led to the company’s demise. In this interview with Andrew Fastow, former Enron CFO, read how the toxic corporate culture and his rationalizations behind “finding the loopholes” led to one of the largest and most well-known cases of corporate fraud and corruption.
Published in Fraud Magazine

Fraud examiners have used Benford’s Law for years to detect anomalies and possible fraud in organizations’ ledgers and journals. Now the author is researching a method to analyze letters of the alphabet in business documents — “Letter Analytics” — to find fraud patterns. His new approach could expedite fraud examinations.
Published in Fraud Magazine

Jordana Stroud excelled at fundraising. From as early as anyone could remember she had a knack for getting people to part with their money for a good cause. She paid her way through Indiana University by fundraising on behalf of various nonprofit organizations and earned a bachelor’s degree in nonprofit management.
Published in Fraud Magazine

You have to tell your students that the good guys are losing the battle to hackers. Organizations are vulnerable, and criminals are perpetrating vast amounts of online fraud daily. Here’s what you can teach them.
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

Jed S. Rakoff, U.S. district judge for the Southern District of New York, says in our cover article that the reasons for the government’s lack of prosecutions ranged “from the diversion of FBI agents to other priorities to prosecutors’ increasing unfamiliarity with how to pursue such cases.”
Published in Fraud Magazine

Passwords are an integral part of our lives. We use them to gain access to our phones and computers and to withdraw cash or pay bills. They help keep our personally identifiable information and finances safe.
Published in Fraud Magazine

Joseph B. Wells, CFE, not only shares his name with ACFE founder and Chairman, Dr. Joseph T. Wells, CFE, CPA, but also experience as FBI special agents.
Published in Fraud Magazine

Senior U.S. District Judge Jed S. Rakoff, keynoter at the upcoming 27th Annual ACFE Global Fraud Conference, hasn’t shied from vividly chastising Wall Street and the U.S. government in the wake of the Great Recession.
Published in Fraud Magazine

ACFE faculty members share more notable cases from the trenches with practical principles that you can apply.
Published in Fraud Magazine

When you hear about “millennials,” also known as “Generation Y,” what’s your reaction? Do you cringe or do you smile? Do your eyes roll thinking about their alleged feelings of self-entitlement, or do you breathe a sigh of relief knowing their technological expertise has helped you work through important problems?
Published in Fraud Magazine

People are dying from drug overdoses in increasingly alarming numbers. They’re from poor, middle-class and wealthy communities. The deaths have jumped in nearly every county just in the U.S. — driven largely by an escalating increase in addiction to prescription painkillers and heroin.
Published in Fraud Magazine

In this column, we hear from a seasoned fraud fighter and educator who has some excellent advice on skill building for new CFEs and students. You can discover how to develop these essential core traits through a mentor relationship or by observing those professionals you admire.
Published in Fraud Magazine

Online scams abound! Cybercrooks aren’t resting as they work to pry cash from your wallets and purses. The Identity Theft Resource Center (ITRC) recently reported scams involving XFINITY, Amazon, Facebook and Wal-Mart.
Published in Fraud Magazine

Crimes such as counterfeiting or trafficking in drugs, humans or arms always will have a global and local impact. It doesn’t matter whether they occur in a low-income housing project in the U.S., a jungle in Bolivia, or a business district in New York, Panama, Costa Rica or Puerto Rico — even the most modest enterprise has global impact, requires transnational border crossings and has an endgame.
Published in Fraud Magazine

On March 8 we celebrate International Women’s Day. Since the inception of the ACFE in 1988, female membership has grown tremendously. We can be proud that the anti-fraud profession has become an ideal place for ambitious women fraud fighters who can use their unique qualities.
Published in Fraud Magazine

Certified Fraud Examiners have elected Sidney P. Blum, CFE, CPA, CFF; Leah D. Lane, CFE; and Nancy E. Rich, CFE, MPA, to the 2016-2017 ACFE Board of Regents from nine candidates selected by the Board’s nomination committee.
Published in Fraud Magazine

Under the kind patronage of His Highness Sheikh Maktoum Bin Mohammed Bin Rashid Al Maktoum, the Deputy Ruler of Dubai and Chairman of the Financial Audit Department, and hosted by the FAD of Dubai, the inaugural conference brought together more than 400 anti-fraud professionals to learn the latest anti-fraud techniques and tools.
Published in Fraud Magazine

Companies sometimes employ cookie-jar reserves during periods of strong financial performance as cushions for the inevitable future periods when performance will decline.
Published in Fraud Magazine

“When the ACFE was founded in 1988, the life of the Certified Fraud Examiner was not as complicated as it is today,” said Jim Ratley. “The computer was still in limited use, and we were just beginning to hear a new term: ‘the Internet.’ There was also a new device sitting on people’s desk called the fax machine. Little did we know how technology was about to change our profession.”
Published in Fraud Magazine

Integrity is the quality of always doing what you know you should do. Think about it. How many of the things that you know you should do, do you always do and never skip? How you would feel about yourself if you consistently did what you know you should do?
Published in Fraud Magazine

The opaque and unregulated global art market is vulnerable to forgeries, tax fraud, insurance fraud and money laundering. Here are details on how fraud examiners can detect and investigate crimes in this murky corner of creative commerce and why circumstances are often in the fraudster’s favor.
Published in Fraud Magazine

Much of our days are consumed with the meat-and-potatoes, real-time components of fraud examinations: taking reports; interviewing suspects, victims and witnesses; obtaining financial records, other pertinent documents and media; analyzing all of the information; and developing conclusions of possible criminal offenses.
Published in Fraud Magazine

Fraud examiners must think innovatively to stay ahead of fraudsters and prevent fraud from growing exponentially. We all know this, but this maxim challenges practitioners and educators because the business environment is changing rapidly.
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

David Barboza, a business correspondent for The New York Times, is the 2016 Guardian Award recipient because he exposed corruption at high levels of the Chinese government, including billions in secret wealth owned by the prime minister’s relatives.
Published in Fraud Magazine

Most frauds, of course, cross borders. In previous columns we've looked at romance scams, the 419 con and lottery fraud — all of which fraudsters still use to extract money from the vulnerable and gullible.
Published in Fraud Magazine

“Get started on your journey! Don’t wait until the perfect job opportunity comes your way,” says Nicole Biskop, CFE, project officer for the DOJ in Sydney, Australia. “Reflect on your experiences, skills and motivation, and decide on the direction you want to take in your career."
Published in Fraud Magazine

New York Times reporter David Barboza — a keynoter at the 27th Annual ACFE Global Fraud Conference — discovered at least $2.7 billion in assets controlled by relatives of the former Chinese premier. Read how he found the smoking guns among public records.
Published in Fraud Magazine

After 16 years as a U.S. special agent, Liseli Pennings, CFE, returns to the ACFE to help worldwide agencies fight fraud and work efficiently with private sectors.
Published in Fraud Magazine

ACFE faculty members share some notable cases from the trenches with practical principles that you can apply.
Published in Fraud Magazine

On Sept. 26, 2016, 28 ACFE staff members, their friends and family participated in their first-annual Susan G. Komen Race for the Cure in Austin, Texas. This one-day event raises funds and awareness for the breast cancer movement, celebrates breast cancer survivorship and honors those who’ve lost their battles with the disease. Team "Toned at the Top" raised $2,466 for the event.
Published in Fraud Magazine

Published in Fraud Magazine

Pamela Johnson, a low-level accounts assistant, had a hidden gambling problem and the trust of the Tompkins Consolidated Area Transit. Here’s how she exploited her employer’s confidence and how the external auditors actually discovered the devastating three-year fraud.
Published in Fraud Magazine

With large caseloads and limited resources, fraud examiners need to be able to effectively and efficiently complete fraud examinations. A case is easier, of course, when we’ve isolated the fraudsters, discovered what they’re doing and how they’re committing the crimes.
Published in Fraud Magazine

Fraudsters target businesses working with foreign suppliers and/or businesses that regularly perform wire-transfer payments. The crooks use social engineering or computer intrusion techniques to compromise real business email accounts and create unauthorized transfers of funds out of business bank accounts.
Published in Fraud Magazine

Voting for the 2026–2027 Association of Certified Fraud Examiners (ACFE) Board of Regents is open now through November 30. This year’s ballot features nine candidates vying to fill three open positions on the Board. The new Regents will take office in February 2026 for a two-year term.
Published in Fraud Magazine

Becoming an expert witness in U.S. federal courts can be challenging, exciting, nerve-wracking and fulfilling. But before you make plans, first study the rules and history contained in the U.S. Daubert standard.
Published in Fraud Magazine

It might be incomprehensible to think someone entrusted with investigating fraud could be a fraudster. But cases of anti-fraud professionals who’ve committed fraud remind us of the importance of proper oversight during fraud examinations and how “trust but verify” is a maxim for fraud fighters to live by.
Published in Fraud Magazine

Fraud schemes like the Black Friday gold scandal of 1869 capitalize on market flaws and the rules that direct them. To protect investors against financial market manipulation, fraud examiners can learn from past cases and the patterns they reveal.
Published in Fraud Magazine

Children are the perfect victims of identity theft because of their lack of credit history. Criminals can exploit a child’s identity for years until the fraud is discovered, usually when the child gets older and applies for loans, jobs or a credit card. Fraud Magazine examines the rise of the crime and methods fraudsters use to carry it out.
Published in Fraud Magazine

Former FBI hostage negotiator Chris Voss talks to Fraud Magazine about the inner workings of successful negotiations and how empathy for your negotiation counterpart is essential to any interaction. And Voss explains how the techniques used by hostage negotiators can help fraud examiners crack tough admission-seeking interviews.
Published in Fraud Magazine

Few people have been more influential in the development of the Association of Certified Fraud Examiners (ACFE) than James D. Ratley, CFE. Fraud Magazine remembers the ACFE co-founder and president emeritus, who passed away in August 2025, and his lasting impression on the anti-fraud field.
Published in Fraud Magazine

In a sweeping indictment unsealed by the U.S. Department of Justice (DOJ), Chen Zhi, the 37-year-old chair of Cambodia-based Prince Holding Group, is accused of masterminding one of the largest forced labor and cryptocurrency fraud operations in modern history. Austrian ex-property tycoon René Benko has been sentenced to two years in prison. Messaging platform Discord has revealed that approximately 70,000 users may have had their official identification photos exposed following a cyberattack on a third-party age verification provider. Wendy Osefo, a sociology professor at Wesleyan University and cast member of “The Real Housewives of Potomac,” was arrested in Maryland alongside her husband, Eddie, on 16 counts of insurance fraud.
Published in Fraud Magazine

Eurojust coordinates a takedown of an international credit card scheme, researchers develop a tool for detecting food fraud, Meta profits from scam ads, and ex-founder and CEO of Beneficient is indicted for a scheme that triggered a bankruptcy.
Published in Fraud Magazine

Whistleblowers courageously speak out despite being met with employment backlash, condemnation and exclusion. The author explores legal protections afforded to whistleblowers and considerations they should weigh before speaking out.
Published in Fraud Magazine

From accounting student to ACFE Associate member to chair of the ACFE Knoxville Chapter, Kathy Birri’s passion for problem-solving guided her career in forensic accounting. She attended her first ACFE Global Fraud Conference on a student scholarship and now investigates allegations of fraud, waste and abuse for the Tennessee Comptroller of the Treasury.
Published in Fraud Magazine

The author examines fraud prevention in the retail industry and how visual controls can help deter fraud.
Published in Fraud Magazine

Consumer cash-use studies like the U.S. Federal Reserve’s Consumer Payment Choice study can be an effective means of estimating missing funds in cash skimming cases. The authors explain how they’ve used these studies in fraud cases and how fraud examiners may deploy these studies.
Published in Fraud Magazine

Rationalization — how someone justifies behavior — isn’t always the focus of fraud examinations, but the authors of this article say that understanding it can help make fraud examinations more effective. Through the lens of a former health care executive convicted of defrauding his investors, the authors explain the mechanics of rationalization and provide a framework for better understanding why some people ultimately commit fraud.
Published in Fraud Magazine

The ACFE Research Institute funds real-world, actionable research that’s helping professionals detect, prevent and respond to fraud more effectively.
Published in Fraud Magazine

When California businessman Kenneth Casey died in 2020, he left behind a Ponzi scheme that defrauded more than 1,200 investors. Those investors sued Casey’s lender, Umpqua Bank, accusing it of being a partner in the scheme. In March, Umpqua agreed to pay $55 million to those investors. Here, the author details the scheme, the litigation that followed and how banks may strengthen their due diligence procedures to avoid accusations of fraud.
Published in Fraud Magazine

The Association of Certified Fraud Examiners (ACFE) remembers Fabio Tortora, CFE, past president and co-founder of ACFE's Italy Chapter. Tortora passed away in June 2025.
Published in Fraud Magazine

More than 5,400 fraud examiners from across the globe traveled to Nashville, Tennessee, or tuned in virtually for the 36th Annual ACFE Global Fraud Conference this past June. There, keynote speakers drew connections to fraud examiners and extolled their work to reduce fraud and corruption worldwide.
Published in Fraud Magazine

A fraudulent invoice sent to a state police agency exposes the challenges that state agencies often face in preventing fraud. The author recounts this case of invoice fraud to Fraud Magazine and provides strategies for state agencies to better protect themselves against such schemes.
Published in Fraud Magazine

Chief Resiliency Officer Paul Zikmund, CFE, achieved his dream job protecting real estate company Berkadia from embezzlement and financial statement fraud. He’s investigated Foreign Corrupt Practices Act violations and enjoys reading books related to the anti-fraud profession.
Published in Fraud Magazine

Financial statement fraud is one of the costliest and most complex forms of fraud. Despite being the least common type of fraud (5% of cases), organizations lost a median $766,000 from it. The author explains how the 3P framework can help fraud examiners detect and prevent financial statement fraud.
Published in Fraud Magazine

Unauthorized tracking technologies can steal personal data and threaten the security of company websites and applications. Here, the authors explore the benefits and disadvantages of using tracking technologies and lay out specific steps for investigating data leaks caused by unauthorized trackers.
Published in Fraud Magazine

For years William King ran a successful medical practice, but when his patients left his office, the Philadelphia, Pennsylvania, doctor had a practice of a different sort — a medical billing scheme known as upcoding. Fraud Magazine examines how King perpetrated a years’ long upcoding scheme that defrauded an insurance company of hundreds of thousands of dollars and details how fraud examiners can detect similar schemes.
Published in Fraud Magazine

Learn more about common tariff fraud schemes, what importers lie about, and how customs agencies discover and deter crimes. CFEs with expertise in customs fraud provide notable case studies.
Published in Fraud Magazine

The practical, culturally nuanced approach to interviewing subjects from a variety of backgrounds presented in this article sets fraud examiners up for success. See how interviewing subjects with sensitivity to their cultural backgrounds encourages good rapport and productive interviews.
Published in Fraud Magazine

With this six-step method, auditors can reverse engineer cash flow and recover potentially significant unspent or misappropriated funds, identify areas of noncompliance or inefficiency, and save money.
Published in Fraud Magazine

The ACFE’s mentoring program is a free benefit for ACFE members looking to grow their careers and connect with others in their field to share resources, advice, support and guidance.
Published in Fraud Magazine

Know-your-customer policies should apply equally to all banking clients. However, ultra-wealthy clients sometimes escape proper scrutiny. Here, the author describes why banks might fail to conduct due diligence on ultra-high-net-worth clients and the high-stakes pitfalls of underestimating their risks.
Published in Fraud Magazine

The rising demand for musical instruments like guitars means more opportunities for fraudsters to take advantage of lax trademark laws and sell modified fake instruments to unsuspecting victims. The author, a guitar enthusiast himself, breaks down the elements of this fraud scheme and provides ways for music lovers and fraud examiners alike to avoid common scams and fight counterfeit fraud.
Published in Fraud Magazine

U.S. seeks to ban Huione Group for money laundering. Credit Suisse confesses to tax fraud. UHG investigated for alleged Medicare fraud. Texas doctor who falsely diagnosed patients gets prison sentence.
Published in Fraud Magazine

The latest identity theft schemes involve convincing victims to pay with gift cards to receive steep discounts on utility services, paying to claim a million-dollar prize and using stolen identities to file unemployment claims.
Published in Fraud Magazine

On battlefields, soldiers have traditionally teamed up with ‘Battle Buddies’ so that no one is left behind. The authors encourage anti-fraud practitioners to help prevent and detect elder fraud, especially among military vets — a particularly vulnerable population.
Published in Fraud Magazine

The trove of leaked files from the Panama Papers and Paradise Papers exposed the secret offshore financial dealings of the global elite. Digging through those terabytes of data were hundreds of reporters led by Marina Walker Guevara. The Pulitzer-Prize-winning journalist talks to Fraud Magazine about managing news media collaborations, data investigations and the urgency for stories that hold the powerful to account.
Published in Fraud Magazine

Tricking insurance and other companies into paying for fake injuries is a perennial, and often complicated, scam. Here the authors examine the three principal players typically involved in these schemes and how evidence of an injury isn’t always what it seems, especially when fraudsters deliberately throw everything but the “kitchen sink” at payers.
Published in Fraud Magazine

Unlike nonviolent white-collar criminals, red-collar criminals commit acts of violence to conceal their crimes. This article describes the red flags that signal red collar criminals' propensity for violence.
Published in Fraud Magazine

The not-so-merry evasion of value-added taxes is a vicious cycle of false trading across multiple countries. Around these trader schemes, known as carousel fraud, fraud examiners work to uncover complex international fraud networks and identify at-risk business entities.
Published in Fraud Magazine

A freshman-year class ignited Erika Correll’s passion for accounting and sparked a career in managing audits and fraud risk assessments for federal clients. Correll’s dedicated to trying new activities with her children, early-morning CrossFit workouts, and leading her team with innovation and discretion during audits.
Published in Fraud Magazine

Findings from the Association of Certified Fraud Examiners’ (ACFE) In-House Fraud Investigation Teams: 2025 Benchmarking Report show that internal fraud teams want more investigative personnel, effective training and resources. Company leaders and anti-fraud professionals alike may use the findings from this report to evaluate their investigative efforts, identify areas for improvement and plan future anti-fraud strategies.
Published in Fraud Magazine

By exploiting automated processes, fraudsters can bypass payment security measures at a faster, subtler rate. The authors explain how payment-processing companies can increase their defenses and better protect their customers against this growing threat to their security.
Published in Fraud Magazine

In June 2025, the former CFO of a seafood wholesaler was convicted of embezzling $9 million from her company. The Certified Fraud Examiner (CFE) who examined the case recounts the multilayered scheme he uncovered and explains the workplace culture and behavioral attributes of the perpetrator that allowed fraud to flourish.
Published in Fraud Magazine

ACFE Board of Regents expels three Certified Fraud Examiners (CFE) and revokes their credentials for violating the ACFE's Code of Professional Ethics bylaws.
Published in Fraud Magazine

International Fraud Awareness Week, or Fraud Week, is celebrating 25 years of community anti-fraud education.
Published in Fraud Magazine

The Ritchie-Jennings Memorial Scholarship awards students who’ve declared a major or minor in accounting, business administration, finance, criminal justice or a similar fraud-related subject. The scholarship program serves as a catalyst for students, furthering their fraud examination careers by reducing financial barriers and increasing access to education.
Published in Fraud Magazine

Artificial intelligence can enhance litigation support by helping accounting experts simplify complex accounting concepts and present compelling evidence. Here’s how to navigate the technology’s limitations, legal implications and best practices for using AI to advance justice.
Published in Fraud Magazine

Fraud Magazine sat down with members of the ACFE of Board of Regents at the 36th Annual ACFE Global Fraud Conference, in Nashville, Tennessee, in June 2025 to discuss the current state of the anti-fraud field, the schemes they worry about the most and the skills that fraud examiners need to defeat fraudsters.
Published in Fraud Magazine

Dr. Ngozi Okonjo-Iweala earned the moniker “Okonjo the troublemaker” for her fierceness in fighting corruption as finance minister of Nigeria. The economist and director-general of the World Trade Organization (WTO) talks to Fraud Magazine about battling corruption in the most populous country in Africa.
Published in Fraud Magazine

In a scandal that’s shaken Thailand’s Buddhist community, police arrested a woman known as “Ms. Golf” in July 2025 for a three-year scheme in which she allegedly blackmailed monks after having sexual relationships with them.
Published in Fraud Magazine

Fraud examiners may be unfamiliar with the inner workings of the music publishing industry, but their investigative skills are in demand. The author identifies areas where fraud examiners may encounter risks, red flags, and opportunities to add value through audits, investigations and fraud prevention.
Published in Fraud Magazine

As jurisdictions across the globe legalize cannabis and entrepreneurs look to grow their fortunes, fraudsters lie in wait ready to exploit this burgeoning multibillion-dollar industry. The author, an accountant with expertise in legal cannabis businesses, details the types of schemes affecting the industry and what fraud examiners should know about preventing fraud in this growing field.
Published in Fraud Magazine

Juliette Gust, CFE, got her start fighting fraud in the hospitality industry. Since then, the current lead investigator for tech company ABB Motion has conducted bribery, money laundering and embezzlement investigations across the globe. She also founded ethics hotline and case management system company Ethics Suite.
Published in Fraud Magazine

Online investment scams are on the rise, and they’re carefully crafted performances that use human psychology to lure victims. Here, the author discusses his research on the emotional tricks that fraudsters use and how understanding these tactics can help stop such crimes in their tracks.
Published in Fraud Magazine

Laci Mosley, aka “Scam Goddess,” has transformed her fascination with fraud into a successful franchise that includes the binge-worthy documentary series “Scam Goddess,” a successful podcast and a book titled “Scam Goddess: Lessons from a Life of Cons, Grifts, and Schemes.” Mosley sat down for an interview during the general session of the 36th Annual ACFE Global Fraud Conference and spoke to Fraud Magazine.
Published in Fraud Magazine

Fraudsters always find new ways to steal PII and money. This time, they’re sending customers to fake websites for fake Amazon refunds and putting a 21st century twist on a classic jury duty scheme. Plus, the FBI cautions that identity thieves are revictimizing people by posing as lawyers offering to recover funds for crypto investment scheme victims.
Published in Fraud Magazine

In any organization, tone at the top matters. Leaders who emphasize teamwork without building a strong ethical foundation risk creating an environment prone to collusive fraud. The author offers advice for mitigating collective rationalization and reducing the risk of collusive fraud within a corporation.
Published in Fraud Magazine

Old password habits die hard, but clinging to your weak password might be the death of your account. The author examines the growing threat of account takeover and considers the effectiveness of the most common security practices.
Published in Fraud Magazine

The U.S. Securities and Exchange Commission (SEC), FBI and U.S. Department of Justice coordinated a large-scale takedown of fraudulent cryptocurrency firms involved in market manipulation.
Published in Fraud Magazine

In 1995, the Association of Certified Fraud Examiners (ACFE) hired a young editor named Dick Carozza, CFE, to turn a newsletter into a magazine. It’s three decades later, and Fraud Magazine is set for another transformation. This is our last printed issue as we tackle a new assignment: delivering the latest fraud prevention and detection content in a digital-only format.
Published in Fraud Magazine

Fraud Magazine has always been in a state of transformation, from its start as a simple newsletter to a glossy magazine. Now, the magazine is making another big change as a digital-only publication.
Published in Fraud Magazine

Gabriella Marshall, CFE, major case consultant at Nationwide Insurance, discusses the benefits of earning the Certified Fraud Examiner credential, her professional background, her greatest achievement and more.
Published in Fraud Magazine

Through the Justice for Fraud Victims Project, college students obtain valuable real-world experience in the field of forensic accounting while aiding victims of fraud.
Published in Fraud Magazine

Who monitors and oversees high-risk transactions in your organization? In this article, I explore who owns transaction and controls monitoring for vendors, customers and employees.
Published in Fraud Magazine

The Evergrande Group, one of China’s largest property developers, recently went bankrupt and was liquidated because of excessive borrowing, mismanagement and alleged financial misreporting. In this column, the author conjectures that behavioral and data analytics could’ve gone a long way in detecting and preventing this scandal.
Published in Fraud Magazine

Fraudsters work year-round to perpetrate their schemes. Fraud Magazine also works year-round tracking the news for those schemes we believe will live in infamy and serve as cases for anti-fraud professionals to study for years to come. Here are the most scandalous frauds of 2024.
Published in Fraud Magazine

U.S. citizens can receive free COVID tests again; beware of scammers who want to charge you. Fake charities are following the recent hurricane disasters. And fraudsters are using artificial intelligence to gain the upper hand to invade inboxes with sophisticated malicious emails.
Published in Fraud Magazine

In 2021, Troy Gochenour became a victim of cryptocurrency fraud after striking up a correspondence with a scammer he met on a dating app. The Ohio-based voice actor talks to Fraud Magazine about his experience as a fraud victim and how it transformed him into an activist raising awareness and fighting against cyber scams.
Published in Fraud Magazine

The ACFE and SAS release their 2022 Anti-Fraud Technology Benchmarking Report; nominations open for the 2023-2024 Board of Regents
Published in Fraud Magazine

Alex Gibney’s documentaries have covered some of the biggest frauds of our times. The award-winning director talks to us about what he’s learned about the psychology of corporate fraud and more. It might not be what you expect.
Published in Fraud Magazine

U.S. bankruptcies — and bankruptcy fraud — greatly decreased during the pandemic because of temporary lifelines. But as government stimulus, pliant lenders, and cheap and easy funding dissipates, we’re seeing crimes rise. Changes in U.S. federal bankruptcy law could accelerate prosecution of bankruptcy fraud.
Published in Fraud Magazine

Management at Collin Street Bakery, the maker of famous fruitcakes, trusted its close-knit family of employees. Big mistake. That faith cost the company close to $17 million in a massive fraud that serves as an excellent case history.
Published in Fraud Magazine

During their careers, fraud examiners will inevitably run into major problems on a high-profile project such as a forensic investigation. Human interaction can be a messy affair and often a major hindrance in project management. Here are tips to minimize cognitive bias and other psychological pitfalls that sabotage the best-laid plans.
Published in Fraud Magazine

Rachel Wilson was a cybersecurity expert before the broader world was even aware of such threats. The former head of the U.S. National Security Agency’s cyber exploitation operations now works to protect Morgan Stanley’s wealth management clients and systems. She talks to us about the latest dangers lurking in cyberspace and much more.
Published in Fraud Magazine

What if a company could significantly improve its financial results, regardless of reality? That opportunity exists today. The fallout from the COVID pandemic has made financial estimates increasingly difficult to calculate and open to manipulation and fraud. Here’s why.
Published in Fraud Magazine

The U.S. Small Business Administration’s Office of the Inspector General faced unprecedented challenges during the COVID-19 pandemic, but a diverse staff was able to weather the storm. Inspector General Hannibal Ware details how his organization built a diverse workforce able to withstand tough times and how other organizations can do the same.
Published in Fraud Magazine

The former Czech prime minister is indicted for fraud; A Wisconsin dentist breaks his patients' teeth as part of an insurance fraud scheme; The U.S. Department of Justice appoints a chief prosecutor to handle pandemic fraud.
Published in Fraud Magazine

Alex Gibney has documented many fraud cases in his three decades as a filmmaker. From his first big hit in 2005, “Enron: The Smartest Guys in the Room,” to the more recent documentary about Elizabeth Holmes, “The Inventor: Out for Blood in Silicon Valley,” Gibney has long been exploring the psychology of deceit and why bright and talented people turn to the dark side.
Published in Fraud Magazine

While conducting forensic and fraud examinations involving small organizations, Julie Aydlott saw just how devastating fraud could be for businesses with limited resources. Aydlott and a colleague founded Business Fraud Prevention, Inc., a nonprofit dedicated to providing free training and resources to help small business owners implement internal controls and fight fraud.
Published in Fraud Magazine

Fraud is constantly evolving. So too should our technologies for detecting and preventing it. Inspired by the Seven Wonders of the World, I present my seven favorite anti-fraud techniques. Some have been in use for over a decade, some are new and evolving — but all of them are “wonderful.”
Published in Fraud Magazine

While external fraudsters who absconded with billions of dollars in pandemic relief have dominated headlines, less attention has been paid to employees scamming those very same programs. Here we spotlight internal fraud at state agencies and what organizations can do to fight this pernicious type of fraud.
Published in Fraud Magazine

Fraudsters continue to harvest PII by targeting professional tax preparers, compassionate givers and COVID unemployment insurance benefits money.
Published in Fraud Magazine

The ACFE's 2022 survey of CFEs around the world and the occupational frauds they have detected and investigated
Published in Fraud Magazine

2022-2023 Ritchie-Jennings Memorial Scholarship winners.
Published in Fraud Magazine

Choosing an investigator with the right skill set is key to successfully resolving a fraud case. An attorney is often best suited for the role but not always. Here we look at the pros and cons of using someone with a legal background to investigate fraud and the challenges of wearing two hats.
Published in Fraud Magazine

Billing fraud may not capture all the big headlines, but it’s pervasive, hard to detect and has been growing since the outbreak of the COVID-19 pandemic. Here are some recent case studies and a bird’s-eye view of how and why this type of fraud thrives.
Published in Fraud Magazine

We’ve all been in meetings where prominent issues needed resolution, but after a couple of hours, the team made little or no progress. A neutral, third-party facilitator, moderator or mediator can help run meetings more efficiently and navigate all parties to desirable outcomes.
Published in Fraud Magazine

Tony Kwok knows a lot about corruption and how to fight it. He was the former deputy commissioner of the Independent Commission Against Corruption, Hong Kong’s ace anti-graft agency. He talks to Fraud Magazine about how it changed the city forever and what he’s doing now to help other countries fight fraud and corruption.
Published in Fraud Magazine

Fraudsters create identities from bits and pieces of fictitious or stolen personally identifiable information. The U.S. Federal Reserve provides a one-stop online toolkit with downloadable resources to help educate financial institutions and other businesses about synthetic identity fraud and how to protect themselves.
Published in Fraud Magazine

Netflix investors sue the streaming service for securities fraud; Spanish police crack a luxury car scam; Lincoln College shuts down in part because of a ransomware attack.
Published in Fraud Magazine

ACFE President and CEO Bruce Dorris, J.D., CFE, CPA, discusses Cressey Award winner, Tony Kwok and his success fighting corruption in Hong Kong. Kwok was the deputy commissioner of Hong Kong's anti-graft agency, the Independent Commission Against Corruption (ICAC). Dorris also discusses the growing problem of corruption all over the world.
Published in Fraud Magazine

As a child, Kenneth Boey read mystery novels and dreamed of fighting crime as a police officer. Now, Boey is a full-fledged fraud fighter, ensuring that his company, Etiqa Insurance, has strong controls in place to protect its systems from threats.
Published in Fraud Magazine

Artificial intelligence (AI) is changing how businesses run — especially in anti-fraud and compliance. Here we describe how to build an AI-focused, anti-fraud technology company and what mindsets, strategies and tactics work well for organizations and entrepreneurs.
Published in Fraud Magazine

When a cybercriminal breaches an organization’s data and financial systems, management automatically begins investigating the culprit’s financial motives. But often hackers are just curious to see if they can invade mainframes. Or they’re bored and want to have some fun. Here’s how to investigate cybercriminals’ minds, understand their nuanced purposes and then prevent more breaches.
Published in Fraud Magazine

Amid the current enthusiasm for all things crypto, interest in decentralized finance (DeFi) has exploded. Proponents think it will help democratize finance. But fraud is running rampant in this corner of the market. Here’s how it works and why fraud examiners should be paying attention.
Published in Fraud Magazine

It seems like identity thieves never sleep. Now they want to imitate your friends and hack into your social media accounts. And they want to compromise your credit scores. Here’s how to protect yourself and your loved ones.
Published in Fraud Magazine

Fraud examiners don’t need cutting-edge techniques to fight fraud in the burgeoning area of environmental, social and governance (ESG) initiatives. They can simply build on existing tools and guides to mitigate those risks, according to the latest report from the ACFE and Grant Thornton LLP, "Managing Fraud Risks in an Evolving ESG Environment."
Published in Fraud Magazine

Fraud examiners came together for the first time since the outbreak of the COVID-19 pandemic at the 33rd Annual ACFE Global Fraud Conference in June. The association’s first hybrid event for both in-person and virtual participants enjoyed record attendance and has proven to be a winning formula.
Published in Fraud Magazine

A vocabulary of influence can be an effective advantage for anti-fraud professionals when implemented ethically and with forethought. But fraudsters use linguistic tools, too. Learn how to recognize the difference between the two and not be fooled.
Published in Fraud Magazine

Catching and preventing fraud in the European Union is no easy task, and its anti-fraud agency OLAF has more than its fair share of wrongdoing to contend with. We talk to Ernesto Bianchi, OLAF’s acting deputy director-general of operations and investigations, about challenges ahead as the EU prepares to disburse money from its biggest-ever budget.
Published in Fraud Magazine

An organic farmer is busted for selling non-organic grains; Ukrainian law enforcement arrest cybercriminals for a phishing scheme against Ukrainian citizens; Salt Lake City 'Real Housewife' Jen Shah and and rapper Nuke Bizzle plead guilty to fraud schemes.
Published in Fraud Magazine

ACFE President and CEO Bruce Dorris, J.D., CFE, CPA, discusses quantum technology to fight fraud and how important it is for CFEs to anticipate fraudsters using the technology as well.
Published in Fraud Magazine

Many organizations that have nurtured new business via cross-border e-commerce sales are vulnerable to payments fraud, especially during the COVID period. Here’s how to fight global cybercriminals at their own game.
Published in Fraud Magazine

Ricky D. Sluder, CFE, first discovered a knack for solving fraud cases when he was a detective in Dallas County, Texas. Now the head of healthcare value engineering for Shift Technology is using his investigative know-how to help other investigators better prevent and detect fraud.
Published in Fraud Magazine

It’s been over a decade since we examined Fraud Triangle Analytics, a method of risk ranking individuals by applying keywords for pressure, opportunity and rationalization to electronic communications. Here we look at how advancements in technology have helped improve FTA in today’s battles with tech-savvy fraudsters.
Published in Fraud Magazine

Fraud examiners working in financial services are familiar with cutting-edge innovations to fight fraud. But quantum computing may be a game changer. Here we explore how this groundbreaking technology could help CFEs and some of the dangers it might entail.
Published in Fraud Magazine

Fraudsters have stolen an unprecedented amount of U.S. COVID-19 relief funds — possibly more than the GDPs of many world economies. But millions of dollars had already been streaming from government programs long before the pandemic, and those cases hold valuable lessons. Here’s how to stanch the flow of money from vulnerable agencies.
Published in Fraud Magazine

Fraudsters want your personally identifiable information. And they’ll steal it by trying to convince you to apply for phony jobs, respond to a fake alert that illegal goods were shipped in your name and have been intercepted, and bogus student loan forgiveness programs. Foil them before they try to punk you.
Published in Fraud Magazine

The world is changing quickly, and fraud fighters must adapt to the times. The ACFE Board of Regents relate their experiences in fighting fraud, waste and abuse, and the new battle opening up on the technological front.
Published in Fraud Magazine

Each year always brings a fresh array of fraud-related scandals, and 2021 was no different. The massive theft of COVID-relief funds continued to play out, but other notable schemes hit the headlines. Here we list the most scandalous of the lot.
Published in Fraud Magazine

Over the past 20 years or so, Africa has seen an exponential growth in anti-corruption agencies as governments across the continent seek to fight what’s still considered to be an endemic problem. Here we look at the history behind ACAs, some case studies and how CFEs can assist in these efforts.
Published in Fraud Magazine

Price-fixing, bid-rigging and allocation agreements are conspiracies you should always be looking for. These experts in illegal and anti-competitive collusion show you how to detect red flags and prevent these crimes. And they give you tips on how to leverage data analysis and cross-border cooperation.
Published in Fraud Magazine

The ability to make a good presentation is a key skill for fraud examiners looking to advance their careers. How you convey your ideas is important. Here are some practical ways to present your thoughts, and it’s not just about putting together a visually appealing PowerPoint.
Published in Fraud Magazine

Any economic disruption leaves businesses vulnerable to fraud both from within and outside an organization. Here we look at how today’s bottlenecks along global supply chains are creating the potential for financial wrongdoing in the coming months and what fraud examiners and auditors should know to prevent it.
Published in Fraud Magazine

Most organizations need vendors to conduct business, but they’re often lax in investigating firms before they use their services. Here are tips for vetting your vendors and avoiding serious fraud problems.
Published in Fraud Magazine

Michael Pocalyko found his passion for fighting fraud when a troubled public company asked him to join its board as a fixer. Since then, the CEO of SI — a Washington D.C.-based intelligence and cyber-sector professional services company — has investigated numerous cases involving governments, corporations, executive misconduct and board-level improprieties. Pocalyko warns that fraudsters are more sophisticated than ever before and to anticipate fraudsters’ creativity.
Published in Fraud Magazine

Businesses and consumers across the globe are quickly adopting cryptocurrencies in daily transactions. And many organizations are scrambling to catch up with this evolving technological innovation. Here’s an update on this new means of exchange, key fraud risks and how CFEs can help with the responsible adoption of crypto.
Published in Fraud Magazine

Cultivating whistleblowers is harder work than persuading traditional interviewees to talk during an investigation. Use these profiles to categorize Victims, Avengers, Samaritans and Intellectuals.
Published in Fraud Magazine

From paper to computer chips, products we once took for granted have become precious commodities as the global supply chain cracks under the weight of labor shortages and renewed demand in the wake of the COVID-19 pandemic. And as every fraud examiner knows, whenever there’s a need for a product or service, fraudsters are there to exploit it for their own gain.
Published in Fraud Magazine

Tom Golden’s latest thriller is not only entertaining but it’s also a handy case study of a fraud investigation. The veteran fraud investigator and forensic accountant talks to us about what he’s learned, how the ACFE made all the difference to his illustrious career and why we need more CFEs.
Published in Fraud Magazine

Six candidates have been selected to compete for two positions on the 2023-2024 Board of Regents. The board sets standards to promote professionalism and to ensure the reputation of the CFE credential.
Published in Fraud Magazine

The ACFE kicks off its 2022 International Fraud Awareness Week, Nov. 13-19, with high-profile organizations like Walmart, Microsoft, General Mills and ADP signed on as Fraud Week Ambassadors to host in-person and virtual educational events meant to raise awareness about fraud and promote anti-fraud training.
Published in Fraud Magazine

Inflating codes that determine how much Medicare and Medicaid pay to health care providers is common practice among fraudsters. Now they’re doing it in increasingly sophisticated ways. Here we examine how statistical graphics can help spot upcoding in what can be an arcane and complicated billing process.
Published in Fraud Magazine

Facing skepticism due to his age and inexperience, a young expert witness prepares for his first deposition with intense study and guidance from seasoned colleagues. What starts with an intimidating test from the plaintiff’s counsel turns into a lesson in composure and confidence, proving that preparation is the key to holding your ground in the courtroom.
Published in Fraud Magazine

Authorities apprehend Leonard Francis, who recently escaped house arrest after involvement in Naval corruption case; the Federal Trade Commission sues Roomster Corp. for using false apartment listings and fake reviews; Police in China arrest criminal gang responsible for major banking scandal
Published in Fraud Magazine

Many companies have charitable programs that match employee donations, supporting causes and people in dire need of the funds. Yet those contributions are also susceptible to fraud. Here’s one story of abuse and what it teaches us about how to prevent this type of scam.
Published in Fraud Magazine

ACFE President and CEO Bruce Dorris, J.D., CFE, CPA, discusses the importance of understanding cybercrime and the tactics used by cybercriminals to prevent fraud in an increasing complex financial landscape.
Published in Fraud Magazine

Long before she became a fraud examiner, Gogi Overhoff, CFE, had her sights set on becoming an actress. But instead of a life on stage, she shines a spotlight on licensed accountants accused of defrauding their clients in her role as an investigator for the California Board of Accountancy.
Published in Fraud Magazine

Technology-assisted review (TAR) has been used for nearly two decades in e-discovery matters to reduce costs, increase efficiencies and speed up the often-tedious task of manually reviewing emails and user documents for relevance. Fraud examiners can also use TAR techniques (with some guard rails) to find potentially improper payments (PIPs) or transactions in structured data.
Published in Fraud Magazine

Stories of criminals hiding ill-gotten gains in offshore trusts have become all too common. But a new age of transparency has begun as governments look to lift the veil covering this secretive world. Here we examine the history of offshore trusts and how fraudsters have gamed the system to their advantage.
Published in Fraud Magazine

All whistleblowers pay huge costs for their honesty and courage. But internal whistleblowers, who have few legal protections, endure the greatest hardships. Here’s what you need to know to support and encourage them and to protect yourself if you ever become a whistleblower.
Published in Fraud Magazine

North Korean state-sponsored cyberfraudsters are attracting increasing attention and, so far, have been outsmarting the government authorities pursuing them. Here’s what fraud examiners can learn from the authoritarian regime’s tricks to exploit the latest technology and what they need to know to stop them.
Published in Fraud Magazine

Commercial fisherman, Carlos Rafael, known as “the Codfather” in New Bedford, Massachusetts, spent years selling thousands of pounds of misrepresented catch under the table for cash, laundered his money and overvalued his business to the IRS, among other crimes. His illegal monopoly predated well-intentioned conservation efforts of governments and citizen groups that inadvertently might have created an environment ripe for fraudulent fishing and reporting activities.
Published in Fraud Magazine

Susan Jones received a letter from a law firm that told her that she might be the recipient of a long-lost relative’s multimillion-dollar inheritance. To process the claim, she wired the firm a deposit, her Social Security number (SSN) and bank account numbers, but she didn’t receive any correspondence after that. Two weeks later, her bank account had a zero balance.
Published in Fraud Magazine

Theodore Swaggen was above reproach. This eight-year employee of a major Midwest bank, had won the trust of his coworkers and supervisors. But as the supervisor of the bank's wire transfer room, Swaggen handled ridiculous sums of money. He decided it was time to get his hands on some of it; $68.7 million to be exact.
Published in Fraud Magazine

The phrase "getting off on a technicality" is well-known in the criminal law arena. If a law enforcement officer is found to have violated the rights of a suspect during a search or arrest, the suspect could walk free, regardless of his guilt or culpability. That same concept applies in the employment law setting as well.
Published in Fraud Magazine

A substantial amount of information can be gathered about a company using entirely legal methods. Much more data can be gathered through illegal methods. This article explores the policies and procedures a company should have in place to protect against both legal and illegal intelligence gathering.
Published in Fraud Magazine

Preview of the 12th Annual Fraud Conference & Trade Show Offers the Best in Fraud Examination Training.
Published in Fraud Magazine

Fraud examiners must hone their financial statement fraud detection methods to overtake the sophisticated crimes of corporate America. (This concludes an article that appeared in the September/October issue of The White Paper and is reprinted with permission from the June 2001 issue of National Association of Credit Management's Business Credit magazine.- ed.) Corporate fraudsters are committing more devious forms of financial statement fraud by concealing and suppressing the true worth of assets, liabilities, cash flows, sales and profitability. Fraud examiners must stay one step ahead.
Published in Fraud Magazine

Thanks to a recent policy change, the Federal Bureau of Investigation will now begin giving special consideration to Certified Fraud Examiners who apply for investigative and technical positions with the FBI.
Published in Fraud Magazine

This article describes the contributions of Edwin Sutherland and Gill Geis in recognizing and defining what we now understand to be white collar crime.
Published in Fraud Magazine

The fraudster may have deceived you but that doesn't mean you can't receive full compensation from your crime insurance carrier. Here's how to ensure you have an adequate fidelity policy and a professional fraud recovery team.
Published in Fraud Magazine

Preview of the 12th Annual Fraud Conference & Trade Show, Aug. 5-10 at Walt Disney World Dolphin Hotel.
Published in Fraud Magazine

Fraud examiners should know the red flags of elder financial abuse and how to identify and protect those who may be vulnerable. Ninety-six-year-old "Mrs. Mabel Hunt" wanted to live out her life in her longtime home. One of her neighbors, "Rev. Bob," a minister, knew this and convinced her to allow him to become a "joint tenant," so that the state Department of Social and Health Services, he said, wouldn't be able to force her to sell her home and move her to a nursing facility. But Rev. Bob was lying and Mabel was too trusting. She walked straight into a financial exploitation trap.
Published in Fraud Magazine

Fraud examiners and auditors should familiarize themselves with the types of cases that can violate U.S. antitrust regulations including price-fixing, bid rigging and market allocation.
Published in Fraud Magazine

In fraudulent financial statement cases, the fraud examiner must competently interview the Chief Executive Officer and Chief Financial Officer for one reason - they probably committed the crime. Financial statement fraud doesn't occur in an isolated environment. The competent and experienced fraud examiner must have the ability to solicit honest answers from the CEO and CFO to tough - but vital - questions about whether anyone has tampered with the books.
Published in Fraud Magazine

When fraudsters recognize illicit money-making opportunities, they often create Trojan horse-like vehicles that allow them future access to necessary files, vaults, accounts, or computers to perpetrate fraud at an opportune moment. This article gives an example of Trojan horse fraud and methods for minimizing the possibilities of it occuring in your company.
Published in Fraud Magazine

Naturally charged with expectations and emotions and requiring participants to share of vast amounts of personal information, Adoption can be the perfect environment for fraud.
Published in Fraud Magazine

In a courtroom, the defense counsel often attacks the way evidence, including digital evidence, is collected and preserved and its chain of custody, rather than the actual analysis of the evidence. Errors in these areas can't be corrected at a later date and that's why the initial response to a computer-related offense should be handled like any other crime scene - with primary emphasis on securing and protecting potential evidence. The only difference is that - unlike a smoking gun at a crime scene - the majority of the evidence (floppy disk, etc.) will be latent and require forensic analysis.
Published in Fraud Magazine

Preview of the 12th Annual Fraud Conference & Trade Show at the Walt Disney World Dolphin Hotel in Lake Buena Vista (Orlando), Fla.
Published in Fraud Magazine

Charles Ponzi, an immigrant from Italy to Boston, Mass., wasn't the first to foist an illegal pyramid scheme on the public but he did manage to develop it into a fine art. Most fraud examiners know about his investment swindle (after all, it warrants a dictionary entry) but few know the specifics. This excerpt, adapted from "Frankensteins of Fraud," by Joseph T. Wells, CFE, CPA (Obsidian Publishing Company, Inc. ©2000), describes the scam that bears his name, and his eventual demise.
Published in Fraud Magazine

The kinesic interview or interrogation is a method that has become more popular among the law enforcement community in recent years. This type of interview is different than traditional methods because the interviewer isn't necessarily looking for information nor a confession from the interview subject; instead, the interviewer is attempting to assess whether the subject is telling the truth.
Published in Fraud Magazine

Fraud examiners must have a new level of analytical comprehension and intellect to uncover Financial Statement Fraud. This article looks at key methods in uncovering Financial Statement Fraud. (This article is reprinted with permission from the June 2001 issue of National Association of Credit Management's Business Credit magazine.)
Published in Fraud Magazine

While healthcare providers who scam insurance companies often do so serially, and the monetary results are huge, insured subscribers who defraud the system are many, and the costs add up.
Published in Fraud Magazine

Your investigative work had paid off: the suspect is now a defendant. Now what happens? Includes information on the Grand Jury, Immunity, Indictment and Information, Arraignment, Prosecutorial Discretion and Plea Bargains, The Burden of Proof in Criminal Trials, Pre-trial Motions in Criminal Court, Motion to Dismiss, Discovery, Rule 16, The Jencks Act, Exculpatory Information (Brady Material) and Disclosures.
Published in Fraud Magazine

The promise in the pioneering work of Edwin Sutherland on white-collar crime has been fulfilled more in the works of Geis than in the works of any other scholar. That promise was vast, and there was much work to be done at the time of Sutherland's death in 1950 in spite of his vigorous labor.
Published in Fraud Magazine

This article helps to devise a logical examination process to find fraud committed through general ledger suspense accounts.
Published in Fraud Magazine

Two collection agencies - which bought delinquent credit card and other bank debt - raised millions based upon misrepresented collection histories and the misapplication of GAAP.
Published in Fraud Magazine

A ghost employee is someone on the payroll who doesn't actually work for a victim company. Through the falsification of personnel or payroll records a fraudster causes paychecks to be generated to a ghost. The fraudster or an accomplice then converts these paychecks. The ghost employee may be a fictitious person or a real individual who simply doesn't work for the victim employer. When the ghost is a real person, it's often a friend or relative of the perpetrator.
Published in Fraud Magazine

Right-to-audit clauses in vendor contracts help control fraud and abuse by affording discovery devices in examinations. Management was finally getting worried. On six different occasions, employees in the purchasing department and other vendors of the ABC Company had alerted executives of a cozy relationship between a department purchasing manager and an outside vendor. The company called our firm, we conducted a fraud examination, and their worst nightmares were confirmed: a $6 million kickback scheme. And it could have been prevented with a simple vendor audit clause in the contract or purchase order.
Published in Fraud Magazine

In 1996 and 1997, I participated in the preliminary hearing for what would turn out to be Canada's largest tax fraud ever prosecuted. While the trial lasted 14 months, we felt that it would have been much longer if the documents hadn't been electronically stored.
Published in Fraud Magazine

CFEs elect three new members to the ACFE's Board of Regents for the 2022-2023 term.
Published in Fraud Magazine

Jeanette LeVie, CFE, the ACFE's vice president and chief operating officer, celebrates her 30th anniversary at the leading anti-fraud training and education organization.
Published in Fraud Magazine

Countries across the world are increasingly recognizing the importance of whistleblowers in the fight against corruption and fraud. Here’s some useful background for CFEs wanting to know about the latest whistleblower protections and legislation.
Published in Fraud Magazine

Digital fraud has surged as the COVID-19 pandemic only accelerated the use of computers and cell phones for everything from banking to shopping. Here’s the latest on the evolving threat landscape and what CFEs and security experts are doing to stop cybercrime.
Published in Fraud Magazine

Pav Gill is now widely recognized as the internal whistleblower who helped expose corruption and fraud at the now-defunct German fintech Wirecard. In a little over a year, his professional and personal life was turned upside down. Gill tells Fraud Magazine his story and the lessons he learned from this bizarre journey.
Published in Fraud Magazine

As organizations and people across the globe observe International Women’s Day in March, the author talks to anti-fraud professionals about the challenges they face in the field, their successes and how they’re overcoming gender bias.
Published in Fraud Magazine

Global anti-fraud and compliance enforcement is on the rise, and regulators want proof that fraud risk management programs are effective. Here we look at some of the hard questions organizations need to ask and some examples of how companies have updated their systems to tackle fraud in the post-COVID environment.
Published in Fraud Magazine

It’s a fact: Data monitoring and analysis can help catch fraudsters. Here’s a primer on incorporating data analysis into your organization along with the latest ACFE tools.
Published in Fraud Magazine

Thirteen people indicted for a $100 million no-fault car insurance scam, sisters perpetrate a tax return fraud scam and Pakistan contemplates banning cryptocurrency.
Published in Fraud Magazine

Commercial-loan agreements can pressure borrowers and lenders to cross the line to avoid bankruptcy or fleece customers. Here are some common fraud schemes that desperate parties can use in this cat-and-mouse game.
Published in Fraud Magazine

The ACFE honors Pav Gill as the Wirecard whistleblower.
Published in Fraud Magazine

Having an environmental, social and governance strategy has become all-important for companies. But as criticism over misleading and fraudulent claims grow, regulators are clamping down and pushing to clarify ESG disclosure rules. As they do in financial reporting, CFEs will have a big role to play in this hot but nascent corner of the market.
Published in Fraud Magazine

Monica Meeks is a U.S. Army veteran and veteran fraud investigator who first honed her fraud-fighting skills as a service member probing credit card fraud committed by Army officials. Now the financial services investigator for the Tennessee Department of Commerce and Insurance, she shares lifelong lessons with students and fellow veterans, educating them about fraud and the value of earning the CFE credential.
Published in Fraud Magazine

Deficient due diligence during the pandemic has allowed real estate investment schemes to proliferate amid a boom in property prices. Consulting fraud examiners and those who work for potential investors and financial institutions can help prevent these extravagant frauds.
Published in Fraud Magazine

U.S. federal government agencies will never text, email or contact citizens on social media or via robocalls. But scammers will. Here’s information on the child tax credit, broadband benefit program, pandemic-related economic payments and fake QR frauds.
Published in Fraud Magazine

Case study of a mining company that intentionally downplayed serious injuries, resulting in the receipt of hundreds of thousands of dollars in government rebate money.
Published in Fraud Magazine

A poorly run loading dock is a death sentence for an otherwise vibrant business; the one thing common to all docks is their vulnerability to fraudulent activity.
Published in Fraud Magazine

Compliance units must not only ensure their companies are complying with laws and regulations, they must also address and manage the risk of money laundering.
Published in Fraud Magazine

A prominent N.J., attorney vanished on July 7, 1994, hours before he was to surrender to police on charges of defrauding a local bank of $8.4 million in a mortgage loan scheme.
Published in Fraud Magazine

Drug diversion fraud is more than just an asset misappropriation scheme: it can have an immediate and potentially life-threatening impact on patients.
Published in Fraud Magazine

Have you heard the one about the company that needed to hire a chief corporate accountant? In the last interview session each finalist was given financial information and asked, “What are the net earnings?” All applicants but one dutifully computed the net earnings but none of them got the job. The candidate who landed the position answered the question by replying, “What do you want your net earnings to be?”
Published in Fraud Magazine

Case study of a procurement fraud scheme in the telecoms industry; a CFE faces the challenge of investigating someone three levels higher in the company.
Published in Fraud Magazine

Securities fraud includes Pyramid schemes, Ponzi schemes, advance fee loan schemes, and many others.
Published in Fraud Magazine

How New Jersey's Medicaid Fraud Control unit - a group of fraud examiners, investigators, attorneys, auditors, and analysts - stopped a $1.5 million Medicaid fraud.
Published in Fraud Magazine

By using income determination methods, such as the cash available technique, fraud examiners can build a case of circumstantial evidence that often leads to a successful prosecution.
Published in Fraud Magazine

Wire transfer fraudsters are knowledgeable about wire transfer activity, have at least one contact within the target company, and are aggressive in carrying out the theft.
Published in Fraud Magazine

Being aware of and prepared for issues like personal safety, office supply needs, technology, and language barriers will help you adapt more smoothly to a foreign environment.
Published in Fraud Magazine

How to use commonly available spreadsheet software to quantify data from a digital frequency analysis and distill it down to a single meaningful number.
Published in Fraud Magazine

CFEs must recognize their companies' and clients' vulnerabilities to Internet fraud and help design controls and solutions.
Published in Fraud Magazine

The story of Cassie Chadwick, excerpted from the book, "Frankensteins of Fraud," by Joseph T. Wells, CFE, CPA.
Published in Fraud Magazine

The civil False Claims Act is the workhorse in the fight against fraud in federal programs. Its special weapon is its reward provision, known as "qui tam," which allows whistleblowers to file suit on the government's behalf.
Published in Fraud Magazine

Internal audit departments are challenged by the often unbridled power of college athletic departments, but must still seek ways to implement appropriate checks and balances to help ensure the integrity of their organizations.
Published in Fraud Magazine

Case study of a CFE who loses his new job but keeps his integrity and his CPA license.
Published in Fraud Magazine

Unfortunately, a laissez-faire attitude toward fraud is representative of the way white-collar criminals have been treated in Australia. Consequently, fraud has proliferated “down under.”
Published in Fraud Magazine

Background investigation check lists can ensure that you’ll complete the appropriate searches and quickly collect the right data the first time.
Published in Fraud Magazine

Neither the FASB nor the GASB have issued any authoritative guidance on soft dollar reporting. Consequently a great deal of soft dollar activity goes unreported, creating exposure to fraud risks.
Published in Fraud Magazine

Fraud examiners from around the globe converged on the Big Apple for the Eleventh Annual Fraud Conference and Trade Show and got practical instruction and invaluable networking.
Published in Fraud Magazine

This article concludes the story of Cassie Chadwick begun in the September/October 2000 issue. It is excerpted from “Frankensteins of Fraud,” by Joseph T. Wells, CFE, CPA.
Published in Fraud Magazine

A review of how fraud examiners can inspect air travel records to find incriminating evidence that can help nail flying fraudsters.
Published in Fraud Magazine

The savvy fraud examiner includes signed statements, visual aids, summaries of witnesses' statements, and the engagement contract in the written case report.
Published in Fraud Magazine

Preview of 13th Annual Fraud Conference & Trade Show.
Published in Fraud Magazine

As fraud examiners we need to recognize the red flags of revenue inflation and deflation long before they become mini-WorldComs or Enrons and the lawyers reveal the nasty details in bankruptcy court.
Published in Fraud Magazine

Because inventory fraud is often more difficult to prevent and detect than other asset thefts, fraud examiners need to understand the mechanics of inventory accounting and the signs of overstated inventory schemes.
Published in Fraud Magazine

The Association offers the syllabus, instructor notes, materials, and teaching aids derived from its recent University of Texas graduate fraud examination course free of charge to institutions of higher learning.
Published in Fraud Magazine

This fraudulent practice - older than time - can be summed up simply in two sentences: "If someone is taking payoffs, then they're doing something they shouldn't officially be doing. Look for what that something is, and you'll find the answer."
Published in Fraud Magazine

Retail store managers occasionally manipulate inventory systems to increase their year-end bonuses and preserve their jobs. Here's how to find this fraud and deter it.
Published in Fraud Magazine

Don't ignore travel and entertainment expense reporting records. Small infractions can add up to thousands in losses and lead to greater frauds.
Published in Fraud Magazine

When you decide to prosecute a fraud suspect, don't expect a prosecutor to accept your case unless you bring a professional package to the referral meeting...certain cases may be processed more effectively within the civil legal system or, in some instances, an irregularity may look like a crime but it may not really be a crime.
Published in Fraud Magazine

Preview of the 13th Annual Fraud Conference
Published in Fraud Magazine

An airline catering company was charging airline companies at the Elmville International Airport a 4.55 percent port fee and 6 percent state sales tax on those fees. The problem was that the port fee had been eliminated at the Elmville airport 10 prior; ICS was pocketing it all.
Published in Fraud Magazine

In the May/June issue of The White Paper, we began by explaining how corrupt officials burden developing countries with unfinished projects and crushing debt, which can lead to economic decline and international terrorism. In this second part, we look at red flags, countermeasures, proof of fraud and corruption in international cases, and possible remedies.
Published in Fraud Magazine

Many fraud examiners would like to be expert witnesses. But before you provide testimony, review the cases and rule changes that affect all testifying experts in federal cases.
Published in Fraud Magazine

Many say that identity theft is unavoidable, undetectable, and unstoppable. But fraud examiners can use their skills to fight this ubiquitous crime.
Published in Fraud Magazine

Methamphetamine addicts steal personal and business checks from the mail, give them a bath, and cash the revived drafts to feed their habits.
Published in Fraud Magazine

Corrupt officials burden developing countries with unfinished projects and crushing debt - conditions that lead to economic decline and international terrorism. Specifically, this article examines kickbacks and bribes to influence the award of a contract, bid rigging to assure selection of the corrupt bidder, and fraud to recover the cost of the bribes and exploit the corrupt relationship
Published in Fraud Magazine

Preview of the 13th Annual Fraud Conference & Trade Show Aug. 4-9 at the Renaissance Hollywood Hotel.
Published in Fraud Magazine

We continue to sharpen our focus on our search for white-collar criminals as we review the legal definitions of the principal types of fraud. In this issue we conclude with conflicts of interest, theft of money or property, theft of trade secrets or intellectual property, and breach of fiduciary duty.
Published in Fraud Magazine

Applicants for top executive positions may have impressive résumés and reputations but extensive background investigations may uncover hidden, illegal activities that can hinder or destroy the organization. This article is adapted from "A Baseline of Executive Backgrounds," which appeared in the Winter 2002 issue of Directors & Boards magazine.
Published in Fraud Magazine

Though identify theft is growing precipitously, the problem isn't untenable. Fraud examiners need to know current statistics and methods so they can fight this insidious crime.
Published in Fraud Magazine

The numerous investigations into the current sensational corporate failures will expose many of the same operations control weaknesses that led to the collapse of the Barings Bank of London.
Published in Fraud Magazine

Fraud examiners can greatly help their employers by conducting vendor audits. Using a team approach to the task leverages the efficiency of the vendor audit and the likelihood that a fraud will be uncovered. It also improves the fraud awareness of both purchasing and user personnel.
Published in Fraud Magazine

The written case report, often the only evidence of investigative work, forces the fraud examiner to consider his or her actions. Cases can be won or lost on the strength of the written report. It conveys to the litigator all the evidence and provides credence to the fraud examination and to the examiner's work. This articles outlines how to write a good report.
Published in Fraud Magazine

Preview of 13th Annual Fraud Conference & Trade Show in Hollywood, California, Aug. 4-9
Published in Fraud Magazine

The executive secretary of a local charity was beloved for her hard work and generous nature. Unfortunately, she was working hard to tamper with the organization's checks so she could be generous to herself.
Published in Fraud Magazine

This article explores computer forensic investigation, offering information on binary files, metadata, and GUID.
Published in Fraud Magazine

A review of the legal definitions of the principal types of fraud will help sharpen our focus in searching for white-collar criminals. This article reviews the main fraud categories of misrepresentation of material facts, concealment of material facts, and bribery.
Published in Fraud Magazine

Trust exists in degrees and its meaning may change with context. Trust is cognitive in that each individual chooses whom to trust and under what circumstances. In this age of computer business, speed and efficiency are displacing trust and verification.
Published in Fraud Magazine

Certified Fraud Examiners (CFE) elected two new members to the 2025–2026 ACFE Board of Regents.
Published in Fraud Magazine

Thousands of fraud fighters will gather in-person in Nashville, Tennessee, and virtually at this year’s ACFE Global Fraud Conference in June to learn from leaders in the anti-fraud field and hear from world-class keynote speakers.
Published in Fraud Magazine

Hackers cash out $300 million from attack on crypto exchange, Bybit; fraud concerns plague academic journals; student loan fraud in the U.K.
Published in Fraud Magazine

From employees who embezzle funds to criminals who exploit disasters for profit, charitable organizations are vulnerable to many types of fraud schemes. The author reveals the methods perpetrators use to deceive donors and charities, and how organizations can protect themselves to carry out their philanthropic missions.
Published in Fraud Magazine

Datasets of documented fraud cases can be instrumental in detecting anomalies and patterns in all sorts of transactions, but many times those datasets aren’t available. With fraudsters perpetrating increasingly sophisticated schemes, fraud fighters need an edge on the criminals with advanced techniques. Here, the author describes how to use machine-learning models and other advanced techniques to detect fraud when you don’t have historical data to learn from.
Published in Fraud Magazine

In this second installment in our series on fraud examinations around the world, an anonymous complaint from an employee sparked an in-depth investigation into allegations of corruption in the bidding process for a large-scale infrastructure project in Bangladesh. The author recounts the intricacies of the case and provides invaluable insight into conducting fraud examinations in this developing country.
Published in Fraud Magazine

Conducting a forensic interview for the first time can be a nerve-racking experience. But with the right tools and resources, you can obtain vital firsthand information from those with knowledge of an alleged crime.
Published in Fraud Magazine

China, Myanmar and Thailand join forces to tackle telecom fraud centers operating in Myanmar; a woman in Texas pleads guilty to smuggling and distributing an unapproved, altered drug used to treat cats; the prison sentence of former Mozambique finance minister, Manuel Chang, is increased; and former U.S. Senator Bob Menendez is sentenced to 11 years in prison.
Published in Fraud Magazine

Onetime runner and current golf enthusiast Lim Huck Hai, CFE, has considerable international executive management experience. He’s helped clients from both private and public sectors implement fraud prevention and regulatory measures and leads investigations guided by integrity and perseverance.
Published in Fraud Magazine

Despite significant regulatory advancements and the availability of innovative tools, many anti-bribery and corruption compliance teams avoid implementing data-driven strategies. The author emphasizes the necessity of embracing an innovative approach to address these risks in the wake of evolving regulatory and enforcement demands.
Published in Fraud Magazine

Companies across the globe have unknowingly hired remote information technology workers acting on behalf of the Democratic People’s Republic of Korea (DPRK). Using stolen identities and gaining access to sensitive data, the workers illicitly generate revenue for the DPRK’s Weapons of Mass Destruction (WMD) and ballistic missiles programs (weapons program). The author breaks down elements of the scheme and provides tactics for organizations to avoid hiring bad actors.
Published in Fraud Magazine

Creative scammers offer Medicare hospice services (to those who aren’t terminally ill). Beware of sophisticated job-offer frauds on mobile devices. And here’s how to spot pesky phishing scams.
Published in Fraud Magazine

Generations that grew up with the internet aren’t immune to online fraud schemes. Trust in online platforms, heavy involvement in social media and financial pressures facing Gen Z and millennials put them at greater risk of being victimized by fraudsters than older adults. Fraud Magazine explores how younger generations become victims — and perpetrators — and what fraud examiners can do to educate them about fraud.
Published in Fraud Magazine

ACFE CEO John Warren, J.D., CFE, discusses the new presidential administration's policies and executive orders regarding anti-fraud laws and enforcement.
Published in Fraud Magazine

Companies may engage in a deceptive practice known as channel stuffing when facing pressure to meet short-term sales targets or enhance stock price.
Published in Fraud Magazine

A real life story of a fraudulent credit card application and aftermath that followed
Published in Fraud Magazine

The article presents the results of the first-ever Occupational Fraud Forum, which took place last August 1999 in New Orleans, La., just prior to the Ninth Annual Fraud Conference.
Published in Fraud Magazine

The information contained in this article is intended to supply the reader with some bankruptcy fraud basics and common schemes that every anti-fraud professional should be familiar with.
Published in Fraud Magazine

“Fraud on the Internet” was adapted from an article in the Summer 1998 issue of the Law Enforcement Report, a publication of the U.S. Postal Inspection Service
Published in Fraud Magazine

A case study of a small town church treasurer accused of fraud and the steps taken in the ensuing fraud examination.
Published in Fraud Magazine

Scenario planning is a device used to strategically analyze risk. This actual case study from a certain Department of Motor Vehicles uses an example of specific risk scenarios to fight fraud.
Published in Fraud Magazine

Slush funds were designed to avoid internal controls and disguise dubious transactions. Slush funds can become havens for fraud and theft. This article examines some common methods used for this purpose.
Published in Fraud Magazine

Electronic imaging technology provides organizations with the tools required to quickly categorize, filter, customize, analyze, store, and retrieve enormous amounts of information residing on multiple media. In the investigative arena, the future of managing complex fraud cases lies increasingly in the effective use of electronic imaging.
Published in Fraud Magazine

This is an excerpt from the Association’s Fraud Examiners Manual, Third Edition. This article covers the discussion on Interview Theory and Application, pages 3.201 to 3.273
Published in Fraud Magazine

Identity theft is one of the fastest-growing white-collar crimes. Fraud examiners and investigators need to know the scams and the ways they can be detected.
Published in Fraud Magazine

While Switzerland moves to the forefront in the fight against money laundering, far more difficult obstacles are being deployed in the Caribbean. Until those nations decide to follow the example of Switzerland, the criminal element will continue to flock to their shores with their tainted money.
Published in Fraud Magazine

An open list of potential issues to consider when designing and implementing ethical standards within a corporation
Published in Fraud Magazine

As academic institutions begin to recognize their benefits, the number of courses offered in fraud examination and forensic accounting should dramatically increase and the amount organizations lose to fraud should decrease.
Published in Fraud Magazine

The University of West Florida (UWF) in Pensacola creates a partnership between campus police and internal audit to alleviate some of the work load.
Published in Fraud Magazine

Fraud examiners can reduce the incidence of charity fraud and abuse by informing others of the red flags associated with fraudulent solicitations for donations.
Published in Fraud Magazine

A/P software packages with "built-in controls" promise to streamline financial operations and help prevent fraud within an organization. However, no business software can completely safeguard against fraud.
Published in Fraud Magazine

By applying their forensic accounting, analytical, and legal skills, fraud examiners can help clients identify potential issues before they commit to purchase a company, preventing unfortunate surprises after the deal has closed.
Published in Fraud Magazine

Fraud examiners and auditors, using software programs like Microsoft Excel, can use Benford’s Law to discover major fraud schemes that couldn’t be found any other way.
Published in Fraud Magazine

Results from the 1998 European Fraud Survey
Published in Fraud Magazine

This article is an excerpt from the ACFE's Fraud Examiners Manual, Third Edition. In this issue, the article covers the discussion on "Qui tam Suits and the False Claims Act," pages 2.273 to 2.277.
Published in Fraud Magazine

Many corporations are susceptible to promotional funds fraud - the embezzlement of hundreds of millions of dollars annually from the promotional budgets of consumer product manufacturers. .
Published in Fraud Magazine

CFEs elected two new members to ACFE’s Board of Regents for the 2023-2024 term. The new members, Thomas A. Caulfield, CFE, and Natalie S. Lewis, CFE, replaced outgoing Regents Hannibal “Mike” Ware, CFE, and Alexandra Sagaro, CFE, whose terms ended in 2023. Caulfield and Lewis took their oaths of office during the board’s meeting in February.
Published in Fraud Magazine

Achieving the fraud-fighting career of your dreams is more than just a matter of luck. Creating a strategy and executing a plan for cultivating your personal brand can help establish your skills and expertise, while differentiating you from others in the field. Here’s how to get started.
Published in Fraud Magazine

Sales of “gray market” products generally are viewed as legal, but diversion of deeply discounted products from authorized distribution networks is often based upon fraud. Here we examine schemes to illicitly obtain millions of dollars of discounts through this pervasive but relatively unknown type of fraud. And we offer ways to ward off fraudsters’ efforts.
Published in Fraud Magazine

Why would someone confess to a crime they didn’t commit? Often an interviewer, trained to be accusatory and aggressive, will pressure subjects to admit guilt. Here’s how fraud examiners — rightfully constrained by higher ethics guardrails — can prevent false confessions that result in wrongful terminations and improper convictions, and ruin innocent subjects’ lives, while leaving the guilty free to commit additional crimes.
Published in Fraud Magazine

When inflation skyrockets, central banks increase interest rates to slow spending. Here, the author details why periods of high inflation might lead to high rates of fraud in the lending industry and what lenders can do about it.
Published in Fraud Magazine

When countries devastated by war, natural disasters or other calamities must rebuild, valiant efforts to rise from the rubble must be paired with another intangible quality: integrity. But prior experience with hastened economic relief underscores the need to couple that relief with a fortifying effort to deter corruption.
Published in Fraud Magazine

Fraudsters are using dilutions, substitution, counterfeits and mislabeling to infiltrate the global food market; a software engineer in Washington steals from his employer in a scheme inspired by the comedy movie "Office Space"; executives in South Korea are convicted in a $1.5 billion V Global scam.
Published in Fraud Magazine

ACFE President and CEO Bruce Dorris, J.D., CFE, CPA, reflects on the lack of oversight and controls that led to the fall of FTX and the importance for CFEs to prevent and detect fraud in the growing cryptocurrency market.
Published in Fraud Magazine

Iryna Shkraba, CFE, has conducted anti-fraud investigations in almost a dozen European countries. She’s a governance, risk and compliance professional who’s worked for organizations such as EY as well as financial industry companies. And while Shkraba is currently based in Vienna, Austria, she takes every chance she can to visit her family and friends in her hometown of Kyiv, Ukraine.
Published in Fraud Magazine

Recent anticorruption research shows that when companies collaborate to share information about third-party payments and high-risk transactions, they have a 25% greater chance of predicting improper payments than when each company’s model is performed in isolation. A new data-sharing consortium led by a nonprofit at MIT is working to make such collaboration possible.
Published in Fraud Magazine

In 2020, the U.S. Department of Justice (DOJ), in its largest health care fraud enforcement action to date, indicted 345 various health care professionals for submitting $6 billion worth of fraudulent claims to federal programs and private insurers. Among those ensnared in the takedown were pharmacies, which were accused of scheming with telemedicine entities and other licensed health care providers to purchase unnecessary medical equipment and prescription pain medications in exchange for illegal kickbacks and bribes, as well as the illegal distribution of opioid drugs. (See “National Health Care Fraud and Opioid Takedown Results in Charges Against 345 Defendants Responsible for More than $6 Billion in Alleged Fraud Losses,” U.S. Department of Justice, press release, Sept. 30, 2020.)
Published in Fraud Magazine

Andy Greenberg first became fascinated with the dark web and the tools that give people anonymity online when he landed a job as the security reporter at Forbes in the mid-2000s. It seemed at the time that law enforcement and even intelligence agencies couldn’t lift the virtual veil that hid all the wrongdoing taking place in this relatively new digital world.
Published in Fraud Magazine

The meteoric rise and sudden downfall of crypto exchange FTX, and its founder Sam Bankman-Fried, is likely to become an essential case study for fraud examiners seeking to understand the new Wild West of the financial markets. Here we look at what happened and lessons learned from possibly one of the largest U.S. financial frauds.
Published in Fraud Magazine

The ACFE Foundation has awarded $85,000 in funds to the recipients of the 2023-2024 Ritchie-Jennings Memorial Scholarship. Twenty-three university students from across the U.S., Europe, Asia and Africa received scholarships ranging from $2,000 to $10,000 for demonstrating academic achievement in a fraud-related field of study and a desire to pursue a career in fraud examination or similar anti-fraud profession.
Published in Fraud Magazine

Economic shifts, crypto deposits, weak controls and incompetent administration have led many tech-heavy banks to bite the dust this year. But none of the institutions’ C-suiters should’ve been caught flat-footed. Since the Great Depression, risk management has been the mantra of the money world. And we know that complacency and hubris can lead to fraud. Here’s how the bank collapsed and reminders for organizations to get it right.
Published in Fraud Magazine

At 2:07 p.m. on Friday, Nov. 22, 1963, the New York Stock Exchange (NYSE) halted trading shortly after news broke that U.S. President John F. Kennedy had been fatally shot. The market had been on a downward slide, losing $11 billion in capitalization in the previous seven minutes. But hours before Kennedy’s assassination, NYSE president G. Keith Funston was doing all he could to prevent a potential market crash as one of the largest futures commodities scandals of the 20th century started to unravel.
Published in Fraud Magazine

Trade compliance professionals help protect companies, but they also play a role in safeguarding national and global security. This emerging field offers exciting career opportunities for CFEs whose skill sets are a great match for companies that need professionals who can prevent and detect trade violations that threaten real harm.
Published in Fraud Magazine

Michael Horowitz, the inspector general of the U.S. Department of Justice, has earned a reputation as a straight shooter and an adept investigator. He talks about his latest role as chair of the Pandemic Response Accountability Committee, mistakes made during the disbursement of COVID-relief money, how to avoid a repeat performance of the resulting fraud fiasco and the importance of strictly sticking to the facts.
Published in Fraud Magazine

Everyone has personal biases, but letting these biases color our views of a suspect can affect the integrity of fraud investigations. Here we explain what unconscious biases are and what fraud examiners can do to overcome them.
Published in Fraud Magazine

Cases of document fraud, including check fraud, have exploded in recent years. The authors explain what’s behind the proliferation of this age-old scam and the modern technology CFEs can employ to stop it in its tracks.
Published in Fraud Magazine

A Manhattan construction company fakes diversity hires to win government contracts; Jalisco drug cartel members scam elderly U.S. citizens with timeshare scam; and the U.K. government fights fraud with new investigative team.
Published in Fraud Magazine

ACFE President and CEO Bruce Dorris, J.D., CFE, CPA, praises Cressey Award winner Michael Horowitz's achievements in detecting and preventing fraud in his role as inspector general and chair of the Pandemic Response Accountability Committee (PRAC).
Published in Fraud Magazine

M. Brian Reid, CFE, says that in a parallel universe he might’ve been a nuclear physicist. But the CEO of Brison LLC applies the same passion he has for exploring the mysteries of the universe to examining the complexities of fraudsters and their schemes against his business clients.
Published in Fraud Magazine

The line between corporate crime and geopolitics has become increasingly blurred as the U.S. sanctions a broad range of bad actors across the globe. Organizations can quickly find themselves in violation of these rules. Here’s how fraud examiners can use one type of technology to prevent this fraudulent behavior.
Published in Fraud Magazine

All organizations have employees who are so smart, energetic and indispensable that they can manage integral functions without close supervision. But some of these “Radars” will succumb to their freedom and rob you blind.
Published in Fraud Magazine

As if finding gainful employment isn’t hard enough, job seekers now must be wary of scammers posting false advertising to steal their money and personally identifiable information. Here we look at why employment scams are on the rise and how to spot the red flags.
Published in Fraud Magazine

Using a computer these days is fraught with fraud risks. That ad about artificial intelligence may be interesting, but a click on the wrong website and you could be hacked. Here are some tips to avoid malware and having your personal identifying information stolen.
Published in Fraud Magazine

The ACFE, the world’s largest anti-fraud community, continues to thrive in an increasingly challenging environment, growing its membership, expanding its presence across the globe and becoming more diverse and inclusive. That’s the message from the most recent ACFE Report to Members.
Published in Fraud Magazine

Rapid changes in technology have meant that work environments now demand faster decisions at all levels, creating the type of conditions where fraudsters thrive. Here we look at how organizations and fraud examiners can best face these challenges in an increasingly agile age.
Published in Fraud Magazine

Just weeks after OpenAI, a U.S. artificial intelligence (AI) research laboratory, launched ChatGPT in November last year, the U.S.-Israeli cybersecurity firm Check Point noticed a spike in dark web conversations. The AI chatbot has astounded, but also unnerved, the public with its ability to do many human tasks from coding to passing an MBA-level exam to writing flawless text. However, in a popular hacking forum, a post entitled “ChatGPT – Benefits of Malware” described how one fraudster used the AI tool to recreate malware strains, such as so-called stealers that infiltrate computer systems, search for specific types of files and then remove those files without the owners’ knowledge. While the creation of malware is nothing new, the discussion on the dark web was disturbing because, as Check Point notes, its apparent purpose was to show less tech-savvy fraudsters that they too could use ChatGPT to code for malicious purposes. (See “Cybercriminals starting to use ChatGPT,” Check Point, Jan. 6, 2023.)
Published in Fraud Magazine
Miranda Patrucic has exposed corruption across Central Asia and in Europe. The award-winning journalist talks about her experiences and the challenges she’s faced in tracking down corrupt officials across the globe and why they still evade the law.
Published in Fraud Magazine

When an accountant raised questions to his organization’s management in 2016 about the possible manipulation of employee remuneration at an Indonesian mining operation, little did he know that he was pulling the string that would unravel a larger fraud scheme involving top executives. Once discovered, though, the fraudsters’ downfall came quickly.
Published in Fraud Magazine

Many U.S. businesses willingly defrauded the government’s Paycheck Protection Program loan program. But PPP’s byzantine procedures, applicants’ mistakes and some banks’ disinterest might have inadvertently caused well-meaning applicants to receive money they shouldn’t have. Now investigators must sift the wheat from the chaff.
Published in Fraud Magazine

Former Goldman Sachs banker Roger Ng receives jail sentence for money laundering and violating anti-bribery laws; in Chicago a woman used information stolen from dozens of dead people to defraud the government of over $45,000; the Texas Department of Public Safety (DPS) left 3,000 Asian Americans vulnerable to identify theft by unknowingly sending multiple driver’s licenses to a New York-based Chinese crime group.
Published in Fraud Magazine

While fraud examiners are hard at work keeping their organizations safe from scammers and other criminals, they must also think about how their loved ones can fall victim to fraudsters’ wily ways. Here we interview CFEs about how they keep family and friends safe.
Published in Fraud Magazine

Barry Tong, CFE, wanted to be an accountant ever since he was in secondary school, but it wasn’t until he joined a Big Four firm’s insolvency and restructuring department that he became interested in fighting fraud. Now, Tong spearheads fraud investigations as Grant Thornton China’s national leader of Forensic and Investigation Services (FIS) based in Hong Kong.
Published in Fraud Magazine

What are the telltale signs of an improper payment? Here we explore the leading research into what can be measured and observed to find common patterns and profiles around improper, and sometimes corrupt, payments.
Published in Fraud Magazine

Identifying and finding people efficiently online is a useful skill for fraud examiners, business investigators and due diligence professionals. Many cases require us to follow paper and money trails by searching for subjects, potential witnesses and former employees, who are generally more willing to speak about their workplaces and colleagues than current employees.
Published in Fraud Magazine

Charles Cullen, a former registered nurse, is serving 11 consecutive life sentences for murdering 29 patients in 16 years at New Jersey and Pennsylvania hospitals. The author, who helped investigate the case, shares organizational deficiencies that have helped him in subsequent fraud investigations.
Published in Fraud Magazine

“Corruption is an integral part of humanity,” says investigative journalist Miranda Patrucic in this issue of Fraud Magazine. It’s a sad summation, but it rings true. According to the ACFE’s Occupational Fraud 2022: Report to the Nations, corruption was indeed the most common fraud scheme in every global region we surveyed. Thank goodness the public has strong journalists like Patrucic, the focus of our cover story and the recipient of the ACFE’s Guardian Award, which we’ll present to her at the 34th Annual ACFE Global Fraud Conference in Seattle, June 11-16. The award honors journalists whose determination, perseverance and commitment to the truth have contributed significantly to the fight against fraud.
Published in Fraud Magazine

Prior to the U.S. Veterans Day holiday, Winston Mittens, a retired Army staff sergeant, answered a call from someone who said he worked at Mittens’ bank. The caller said the bank was beefing up its security, so it needed Winston to verify his account information and Social Security number, which he did. But in the next week, Winston visited his bank to deposit a check and found he had a zero balance in his account. A bank official told Winston that someone had used his identity to steal his banking credentials and drain his money. Lucky for him, the bank covered the fraud and restored his balance. The bank also changed his account credentials so he hopefully wouldn’t be a victim again.
Published in Fraud Magazine

Certified Fraud Examiners (CFEs) earn 17% more than their non-certified counterparts, and 62% report being happy on the job. These are just a few of the insights from the Association of Certified Fraud Examiner’s (ACFE) 2022 Compensation Guide for Anti-Fraud Professionals, which also revealed a slow trend toward gender diversity in the anti-fraud profession and changing workplace habits since the COVID-19 pandemic.
Published in Fraud Magazine

Because of the enormous amount of government funding that goes into the defense sector, the U.S. military has long suffered its fair share of fraud. And counterfeit components/product substitution — which is really a category of procurement fraud all on its own — remains an ongoing problem.
Published in Fraud Magazine

Growing up, we all tried at some point or another to squirm our way out of being accountable for something we shouldn’t have done or said. (I admit to throwing my little brother under the bus a couple of times, but my parents were wise to that approach.) We spun the facts or rationalized our action to avoid punitive measures; in short, we wanted to preserve our standing in the family unit and stay in Mom and Dad’s good graces. But alas, many of us suffered some parental wrath as a consequence for our behavior — and the fictitious tales we told to rationalize it. Our parents knew something we kids didn’t fully appreciate: Rationalization allows us to wander further away on the far side of truth. As adults gaining experience in our respective professions, we learn about compliance and ethics, but we also add to our repertoire of rationalizations.
Published in Fraud Magazine

When sailing, mariners must always know the wind’s direction and mind their points of sail — a boat’s course relative to the wind. Sails can’t catch the wind in what is known as the no-go zone, approximately 45 degrees on either side of the wind’s direction. But sailing close-hauled, or as close to the wind as possible, mobilizes sails. (See “What is Sailing Close to the Wind?” Life of Sailing.) Indeed, sailing requires working with the wind to move ahead. Managing fraud risk and investigations is a similar process: Just as the mariner works with the wind, collaboration among teams of experts is the best way to propel forward. When people come together and share their expertise, they can truly succeed.
Published in Fraud Magazine

In March 2019, former New York Lt. Gov. Brian Benjamin, at the time a state senator, asked a real estate developer to help procure a number of small-dollar contributions for his latest political campaign. Benjamin’s unnamed contact, who also led a nonprofit organization, later told investigators from the U.S. Department of Justice (DOJ) that he initially rebuffed Benjamin’s request for several reasons: He didn’t have experience “bundling political contributions” in that manner; he was focused on fundraising for his own nonprofit; and any potential donors he could target were the same ones from whom he intended to solicit contributions for the nonprofit.
Published in Fraud Magazine

In the U.K., a man is arrested for attempting to sell a house he was renting; tech workers in Southeast Asia are conned into working for cybercrime rings; a 58-year-old woman receives a prison sentence for heading one of the biggest marriage fraud conspiracies in U.S. history.
Published in Fraud Magazine

Kathryn Wilson, CFE, learned in high school that accounting encompasses so much more than crunching numbers — it’s also about following the money. And accounting isn’t just a job for Wilson, who conducts risk assessments and devises ways to prevent fraud as a senior manager in CohnReznick’s government and public-sector group; it’s also a family affair with her two brothers and late grandfather in the profession.
Published in Fraud Magazine

Today’s world is fraught with geopolitical sanctions, fraud, corruption and cyber warfare, and fueled by rapidly emerging technologies that continue to change how we approach business and risk mitigation. Companies large and small are enduring a costly, but necessary, shift to digital, while transitioning operations to the cloud and scrambling to protect their systems from intrusion. With change comes risks, which is why companies often look to anti-fraud and/or forensic technology professionals to help them build the preventive and detective anti-fraud controls needed to protect their business and align with regulatory expectations.
Published in Fraud Magazine

Medicare Advantage, the private-sector arm for elderly care, is fast becoming the new battle front in the fight against health care fraud in the U.S. Here's why, and what fraud examiners think should be done.
Published in Fraud Magazine

It’s hard to believe, but it’s been almost three years since the start of the COVID-19 pandemic, and fraud fighters are still grappling with the fallout of frauds tied to government-relief funds. Yet, despite the massive scale of pandemic frauds and the staggering loss of money, governments made some progress after enacting task forces to investigate COVID-related frauds and recover stolen funds. And while some of the most scandalous frauds of 2022 were connected to the pandemic, it wasn’t all COVID all the time. Indeed, there were plenty of other frauds we believe will live on in infamy and serve as essential case studies for fraud examiners in the years to come. (See “Justice Department Announces COVID-19 Fraud Strike Force Teams,” U.S. DOJ press release, Sept. 14, 2022 and “Secret Service recovers $286 million in stolen COVID relief funds,” by Julia Ainsley and Sarah Fitzpatrick, NBC News, Aug. 26, 2022.)
Published in Fraud Magazine

Fraud, waste and abuse emerge in most areas. But, theoretically, the health care system is where most people should least expect them. Of course, fraud has long been a problem in this sector. And most recently Medicare Advantage — the private-sector arm of the U.S. national health system for elderly Americans — and the insurers that manage it have come under intense scrutiny for allegedly submitting false diagnosis codes to inflate payments from the government.
Published in Fraud Magazine

Kerry Binder thought of herself as a real computer jock. When she had a problem with her computer that she couldn’t solve, she contacted the Geek Squad, retailer Best Buy’s tech support service, for help. One day she received a text message saying she’d been charged hundreds of dollars to renew her Geek Squad membership. She knew nothing about this and thought that this was an error. The text message said Binder could dispute the charge or cancel her membership by calling a phone number within 24 hours. When she made the call, a scammer told her that he had to gain remote access to her computer to help her. When he’d finished rummaging around in her computer, he told her that he’d corrected the error and apologized for the mistake.
Published in Fraud Magazine

As protests raged in Chile in 2020 over the cost of living and inequality, the government sought to procure body cameras for the police to monitor events on the ground. After going through a public bidding process, U.S. telecommunications equipment provider Motorola Solutions won the business to supply 300 cameras at a cost of close to 400 million Chilean pesos, or about $340 each at today’s exchange rate. Soon thereafter, those involved in the bidding process found themselves under investigation for irregularities. According to the local press, government officials accepted Motorola’s bid even though the company submitted its offer on the electronic procurement portal outside the hours stipulated by the bid rules. (See “El informe de Contraloría que complica a Katherine Martorell, la actual vocera de Sichel, por millonaria compra de cámaras GoPros para Carabineros,” El Mostrador, Oct. 15, 2021.)
Published in Fraud Magazine

There’s a good possibility you’re a Certified Fraud Examiner. But you’re probably not a licensed private investigator. Are you missing out? Not necessarily, but some CFEs believe their hard-won PI skills burnish their fraud examiner careers and make them better professionals.
Published in Fraud Magazine

Nine candidates have been selected to compete for three positions on the 2024-2025 Board of Regents. Beginning Nov. 1 and ending Nov. 30, CFEs may vote online at ACFE.com/BORvoting for their selections to replace retiring Board of Regents members, Wendy Evans, CFE; Collins Wanderi, CFE; and Chrysti Ziegler, CFE. The newly elected Regents take office in February 2024 and will each serve two-year terms.
Published in Fraud Magazine

Investors have been losing their money to scammers since ancient times, but the scale and the cost of investment fraud has only grown in a digital age that has made it easier for fraudsters to steal hard-earned savings. Here we look at some of the different types of investment fraud and the red flags to watch out for.
Published in Fraud Magazine

Cody Easterday was a Washington state rancher and farmer with a sterling reputation. Then Tyson Foods discovered that for at least four years he sent fake invoices to that company, and another, for $244 million for the care and feeding of 265,000 head of cattle that didn’t exist. He pleaded guilty to wire fraud and is serving an 11-year sentence in federal prison. Here’s an analysis of the fraud from a prosecutor, investigators and fraud examiners.
Published in Fraud Magazine

Fraud now accounts for more than 40% of all crime in the United Kingdom. Here we explore what’s behind this proliferation of fraud in England and Wales and what anti-fraud experts say the government must do to crush it.
Published in Fraud Magazine

Joseph L. Ford, CFE, has spent a lifetime fighting fraud, working his way up from file clerk at the FBI to holding the bureau’s No. 3 spot. After leaving the FBI, he served as Bank of the West’s chief security officer and eventually founded his own consulting firm. Here Ford speaks of his experiences investigating both large and small frauds and what we can learn from them.
Published in Fraud Magazine

Higher-education tuition is astronomical. Prospective students and their parents are looking in every corner for financial relief. But fraudsters are searching even harder for desperate victims. Don’t let your panic disable your due diligence. Here’s how to use your fraud examiner abilities to avoid these opportunists.
Published in Fraud Magazine

Elderly victims in Australia lose half a million dollars in alleged romance scam; China and Myanmar join forces to crack down on cybercriminals targeting Chinese nationals; and risk management study reveals retailers are losing money in instances of friendly fraud.
Published in Fraud Magazine

Sometimes a fraudster signs their name, but with a different flourish, to deny later that they ever signed a document at all. The technique is called autoforgery. Here we examine why criminals might use this rare type of fraud and how to prove it in court.
Published in Fraud Magazine

Throughout her career investigating financial crimes — first in the CIA and FBI and now in the private sector — Lourdes Miranda found that understanding human behavior is instrumental to cracking cases. She now urges fellow CFEs to balance technology with human intelligence in their investigations and learn everything they can about cryptocurrency and blockchain.
Published in Fraud Magazine

‘Tis the season to set company goals. As we wrap up 2023 and look to the new year, ponder this: What are some of the key performance indicators (KPIs) companies use to measure the effectiveness of their fraud risk management program? Here, we explore some leading examples of anti-fraud KPIs that drive business value.
Published in Fraud Magazine

Empathy is the ability to understand other people’s emotions, values and behaviors. It was once believed to be too “wishy-washy” or submissive to be taken seriously as a valid approach for investigations or negotiations. But empathy is actually a highly valued dimension of interpersonal, communication and strategic competence that can help fraud examiners more easily obtain an admission of guilt from fraudsters and gain insight into their “why.”
Published in Fraud Magazine

Sam Bankman-Fried, Elizabeth Holmes and Bernard Madoff. What do they have in common? They apparently used their outsized social influence in their professional networks to illegally expand their bank accounts and prolong their crimes. Fraud fighters can’t also be duped by their wily ways.
Published in Fraud Magazine

ACFE President John D. Gill, J.D., CFE, shares lessons learned from ACFE fraud fighters across the globe.
Published in Fraud Magazine

Phishing scams never disappeared; they’re just more sophisticated. Also reject letters promising millions from insurance policies. And beware of invoices for COVID-19 tests you never ordered.
Published in Fraud Magazine

ACFE Regent Emeritus Joseph R. Dervaes, CFE, gave his final presentation and awarded the Pacific Northwest Chapter’s scholarship, renamed in his honor, at the chapter’s first hybrid annual fraud conference and the latest edition of the Fraud Risk Management Guide helps fraud examiners keep apprised of the latest threats and the multiple ways they can tackle them.
Published in Fraud Magazine

Fraud examiners shattered Global Fraud Conference attendance records in Seattle, Washington, cementing ACFE’s hybrid virtual and in-person annual conference as a can’t-miss event. And keynote speakers shared their stories of investigating fraud and corruption and revealing the truth.
Published in Fraud Magazine

The COVID-19 pandemic resulted in an increase in remote and hybrid work that has many managers concerned about declining productivity levels. Here we examine the latest buzzwords associated with the trend, how executives and employees are coping in this new environment, and whether “stealing time” is a fraudulent act.
Published in Fraud Magazine

Members of the ACFE Board of Regents always bring a wealth of experience from their respective sectors. Here they impart their thoughts on an array of topics and the importance of continual learning in the ever-evolving anti-field field.
Published in Fraud Magazine

The over $4.5 billion theft from Malaysian sovereign wealth fund 1MDB is one of the world’s biggest-ever financial scams and a sad story as it deprived ordinary people in that country of vital resources. Xavier Justo talks about his nightmare experience exposing the fraudsters responsible for this massive theft and the lessons he’s learned along the way.
Published in Fraud Magazine

Proving someone is lying, let alone getting them to confess, is difficult to say the least. Let’s face it, fraudsters are slippery characters and adept at the art of deception. Here David Lieberman, Ph.D., a psychotherapist and an expert in the field of human behavior, helps us understand the signs of deceit and how to get a confession.
Published in Fraud Magazine

Access/identity control is a fundamental component of data security that dictates who’s allowed to access and use company information and resources. But organizations still lack the necessary protections, opening the door for fraudsters to exploit their systems. Here the authors examine the latest IT resources to keep such criminals at bay.
Published in Fraud Magazine

In California a man conducted a cow manure Ponzi scheme; a former Amazon manager is sentenced for stealing millions from the company; and fraudsters in India scam victims by posting fake business numbers online.
Published in Fraud Magazine

Incoming ACFE President John Gill, J.D., CFE expresses gratitude for outgoing ACFE President and CEO Bruce Dorris, J.D., CFE, CPA.
Published in Fraud Magazine

Understanding ChatGPT and similar generative AI tools is critical for fraud examiners seeking to leverage this emerging technology. Here we explore the risks and the extraordinary potential of this new phenomenon.
Published in Fraud Magazine

In a world rife with scandals impacting all aspects of business and life, internal auditors aren’t immune to bad behavior. Here’s how to find their occasional crimes and misdemeanors, plus some practical measures to deter and detect their nefarious activities.
Published in Fraud Magazine

Don’t send in the clones! Fraudsters are using ChatGPT to replicate voices to pull off classic grandparent and family-emergency scams. And beware of this new fake income-tax refund scam.
Published in Fraud Magazine

Since 2000, the Association of Certified Fraud Examiners’ (ACFE) International Fraud Awareness Week has educated organizations and individuals worldwide about the importance of fraud prevention and detection. This year, the ACFE is raising awareness and equipping people with the knowledge they need to protect themselves and their organizations from occupational fraud.
Published in Fraud Magazine

As the accounting field braces itself for staff shortages, it’s now more important than ever to ensure that young fraud fighters are prepared to meet future challenges. Here, the author provides training techniques that he’s employed to train new employees and pass his wealth of knowledge on to the next generation.
Published in Fraud Magazine

Failures in fraud investigations can hinder the pursuit of justice and the deterrence of fraudulent activities. The author examines two case studies that illustrate the immense impact that botched investigations can have on individuals, organizations and society.
Published in Fraud Magazine

Fraud investigators strive to reveal the truth, but sometimes people are falsely accused of fraud. Here, we examine cases of wrongful convictions with insights from Certified Fraud Examiners (CFEs) and other experts in the field to see why this happens and what mistakes to avoid during investigations.
Published in Fraud Magazine

Former CIA Chief of Disguise Jonna Mendez talks about concealing spies’ true identities as they ply their trade, rising through the ranks as a woman in a male-dominated field, and the important differences between fraud fighters and undercover agents.
Published in Fraud Magazine

Aviation giant Boeing pleads guilty to fraud over 737 Max jet crashes, the U.S. Supreme Court hands down big decisions on bribery and corruption, and Interpol coordinates an international law enforcement operation to dismantle online scam networks.
Published in Fraud Magazine

ACFE President John D. Gill, J.D., CFE, discusses the energizing effects of attending ACFE Annual Global Fraud Conferences, and in particular, the 35th Annual Global Fraud Conference held in Las Vegas, Nevada, in June.
Published in Fraud Magazine

At one time an aspiring artist, Association of Certified Fraud Examiners (ACFE) Board of Regents Chair Natalie Lewis, CFE, CPA/CFF, now investigates alleged employee embezzlement and business fund misappropriation schemes. She works to combat fraud locally and globally in her leadership positions for the City of Atlanta and the ACFE.
Published in Fraud Magazine

Forced labor, an unfortunate reality in much of the world, may lie hidden (or in plain sight) in companies’ supply chains. Governments are taking notice, and CFEs have a key role to play in combating the problem.
Published in Fraud Magazine

Thousands of fraud examiners from around the globe flocked to Las Vegas, Nevada, where they hit the big time, gleaning deep insights and practical tools to combat fraud from an international cast of anti-fraud experts during the 35th Annual ACFE Global Fraud Conference.
Published in Fraud Magazine

Members of the ACFE’s Board of Regents sat down with Fraud Magazine at the 35th Annual ACFE Global Fraud Conference in Las Vegas for a wide-ranging discussion about pandemic risk management, how AI is no substitute for human expertise and how important it is to attract new people to the anti-fraud profession.
Published in Fraud Magazine

Fraudsters pose as employees of toll road agencies and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to steal money and personal information from unsuspecting consumers. Also in this column, the author details how artificial intelligence is making it easier to commit cyberfraud, and how consumers can reduce the number of spam emails in their inboxes.
Published in Fraud Magazine

Forming solid relationships with customers while protecting them from fraud and financial loss is a constant balancing act for banks. The author details the steps involved in developing a strategy that puts customer protection at the center while providing a hassle-free customer experience.
Published in Fraud Magazine

In this case study — the first in a series covering compliance and investigation issues across the globe — the author, a veteran ethics and compliance professional, details a workplace misconduct investigation involving a senior business leader at a large organization in India. The inquiry, which began with harassment allegations, revealed other questionable activities the senior leader was engaged in.
Published in Fraud Magazine

Leaders face accelerated challenges because of global uncertainty, uses and abuses of AI technology, and evolving workforces, among other factors. Anti-fraud practitioners grapple with time-critical decision-making and rapid situational responses. Here’s how to implement adaptive leadership.
Published in Fraud Magazine

According to the United Nations, an estimated 200,000 people have been trafficked into cyber scam centers where they’re forced to commit fraud schemes, causing billions of dollars in losses worldwide. Fraud Magazine talks to experts fighting on the frontlines against forced criminality about what it will take to disrupt these cyber scam operations and what fraud examiners can do to help.
Published in Fraud Magazine

Despite the diminishing use of checks in the U.S., check fraud is on the rise. The author recounts her own brush with attempted check fraud and highlights how businesses — large and small — can protect sensitive customer information.
Published in Fraud Magazine

National Public Data confirms cybercriminals conducted massive data breach involving 2.9 billion records; Missouri woman is arrested for attempting to steal Graceland mansion; and Robert Telles is sentenced for the murder of Las Vegas Review-Journal investigative reporter Jeff German.
Published in Fraud Magazine

ACFE President John D. Gill, J.D., CFE, calls on anti-fraud professionals to send contact information for convicted fraudsters who'd be willing to be interviewed by the ACFE.
Published in Fraud Magazine

Winner of the 2024 Outstanding Achievement in Outreach and Community Service Award, Erin R. Ellebracht, PsyD, CFE, actively volunteers with the elderly in her community and strives to increase awareness about elder fraud. She values insights from varying perspectives as she works to improve fraud prevention and detection processes in the fight against fraud.
Published in Fraud Magazine

For over a decade, CFEs, auditors and analysts have used Benford’s Law to identify journal entry irregularities. Today, this analysis method remains relevant as ever as new applications using AI and simulation could bring Benford’s Law to the forefront of your fraud risk management controls.
Published in Fraud Magazine

With more people traveling and spending money on leisure following the COVID-19 pandemic, fraudsters are once again turning their attention to the hospitality industry. Here we look at the variety of fraud taking place in this sector and how best to prevent it.
Published in Fraud Magazine

Identity thieves continue their quest for consumers’ personally identifiable information with three new scams. Beware fraudsters posing as airline customer service representatives on social media, mystery companies targeting job seekers on the WhatsApp instant messaging service and fake Google Authenticator ads masquerading as malware.
Published in Fraud Magazine

Interviews are essential to gathering detailed information during a fraud examination. But some interviews require special care, especially when it comes to victims of fraud. Trauma-informed interviewing practices take into account the emotional upheaval that fraud victims often face. In this article, the author explains why trauma-informed interviews are important and how their principles can be incorporated into interviewing practices.
Published in Fraud Magazine

Documenting your fraud program is a business imperative that shouldn’t be overlooked. The author details how to craft an enterprise-level fraud policy and a program document that can set your organization up for success.
Published in Fraud Magazine

Jack Sandlin, Indiana state senator and founder of the ACFE Central Indiana Chapter, passed away on Sept. 20, 2023. He’s remembered by loved ones for his integrity and commitment to public service.
Published in Fraud Magazine

Lebanon’s economy has collapsed, aided by corrupt monetary policy, embezzlement and illusory regulatory oversight. Here’s an analysis of Riad Salameh’s mismanagement of Banque du Liban during his three decades as its governor.
Published in Fraud Magazine

For many, the dark web conjures up images of poorly lit rooms where lone fraudsters scam victims behind the veil of encrypted messaging. But the reality is more akin to an open marketplace, like an Amazon for criminals — where they sell multiple fraud products and focus on branding, marketing and the bottom line. That may be frightening, but it also presents an opportunity for law enforcement. Here’s why.
Published in Fraud Magazine

Conducting international investigations abroad requires adaptability and a willingness to learn new customs. The author, who’s conducted many overseas investigations throughout her career, details her experiences to demonstrate why understanding people and their cultures can vastly improve your investigations abroad.
Published in Fraud Magazine

Global organizations employ thousands of suppliers and vendors to get their business done, so they need to use the latest investigative tools of third-party due diligence (TPDD). Here we examine how we can use TPDD to discover how suspicious third parties can use email encryption services (and corresponding primary email addresses) to mask illegal activities and steal valuable data.
Published in Fraud Magazine

‘Cryptoqueen’ associate Irina Dilkinska pleads guilty to wire fraud and money laundering for her role in a pyramid scheme; the U.S. DOJ charges 21-year-old Matthew Bergwall with mail fraud; and British media company Virgin Media 02 launches a free beer for International Fraud Awareness Week.
Published in Fraud Magazine

ACFE President John D. Gill, J.D., CFE, expresses gratitude for the diversity in professions among ACFE fraud fighters united by a passion for fairness and justice.
Published in Fraud Magazine

Credit cooperative societies across the developing world have helped local communities gain vital access to financial systems. But this access comes with a downside. Fraud and other financial vulnerabilities can put members at risk. This is where fraud examiners step in and help protect these cooperatives against such risks.
Published in Fraud Magazine

As a senior academic and researcher, Rasha Kassem seeks to mitigate fraud risks, improve methods of fighting fraud, and better understand why fraud criminals do what they do. She says that investigating fraud isn’t enough to stop it and urges fraud examiners to innovate and explore new techniques for prevention.
Published in Fraud Magazine

The better the data, the better the insight. The better the insight, the better the results. In this issue, we explore how CFEs can help their organizations break down data silos to improve business transparency.
Published in Fraud Magazine

The author uses real-life examples from his fraud investigations to dispel a major myth about bitcoin’s anonymity, showing just how traceable the digital currency is. Unspent transaction outputs are one mechanism to track payments on the blockchain and ultimately discover who’s behind any illicit activity.
Published in Fraud Magazine

We’d just filed our Most Scandalous Frauds story of 2022 when news of the implosion of multibillion-dollar crypto exchange FTX broke. It might’ve been a little too late for us to add what would become the biggest fraud scandal since Theranos to the 2022 list, but the FTX story didn’t disappear, and we had FTX founder Sam Bankman-Fried’s trial and eventual guilty verdict to keep us riveted. Of course, FTX wasn’t the only high-profile case that shocked us; there were many others that had a big impact on the anti-fraud profession. Here are the five fraud cases we found most scandalous in 2023.
Published in Fraud Magazine

Fraudsters stole billions from U.S. federal COVID-19 loan programs. Now unsuspecting victims, who never applied for those loans, are receiving bills. Plus, business ‘NetScaler Gateways’ are attacked, and Medicaid children’s health insurance recipients are scammed.
Published in Fraud Magazine

Commercial fragrances and perfumes are big business, and the multibillion-dollar industry attracts its fair share of dodgy practices and outright fraudulent activity. Here we look at the difference between knockoffs and counterfeit products, and why the big perfume houses have such difficulty protecting their brands.
Published in Fraud Magazine

The ACFE remembers Joseph W. Koletar, DPA, CFE; Kimberly A. Howell, CFE, Maheswari G. Kanniah, CFE, and Robert J. Smolich, CFE, join the ACFE Board of Regents for 2024-2025; and the ACFE Board of Regents disciplines two members.
Published in Fraud Magazine

Since the first Report to the Nation was published in 1996, the Association of Certified Fraud Examiners (ACFE) has surveyed thousands of Certified Fraud Examiners (CFEs) about the methods, costs and effects of occupational fraud. Now in its 13th edition, the Occupational Fraud 2024: A Report to the Nations provides an inside look at how fraud is committed, detected and prevented in organizations around the world.
Published in Fraud Magazine

Research shows that those with inquisitive minds seek novel solutions to unique challenges. Nowhere is this truer than in fraud investigations where curiosity and a healthy dose of skepticism are two sides of the same coin. Fraud investigators won’t detect many instances of financial deception if they don’t use curiosity as a problem-solving skill.
Published in Fraud Magazine

Jennifer Griffith, CFE, and Sarah Carver, CFE, spent years informing their superiors in the U.S. Social Security Administration office where they worked about an operation between a lawyer and an administrative law judge to fraudulently approve thousands of disability claims. But instead of rewarding them for uncovering a massive fraud, their bosses retaliated against them. Carver and Griffith talk to Fraud Magazine about their journey as whistleblowers and their courage to fight for the truth even when the odds were stacked against them.
Published in Fraud Magazine

You probably send cash via Zelle, Venmo, Apple Pay or other mobile apps. But scammers are also using those apps to trick people into authorizing payments. Banks have traditionally balked at refunding victims, but that’s changing as the U.K. government implements the Payment Systems Regulator, and the U.S. government pressures financial institutions.
Published in Fraud Magazine

Charlie Shrem was atop the cryptocurrency world as CEO of pioneering bitcoin exchange BitInstant when he was arrested for indirectly facilitating drug sales on the dark web. Now post-prison, Shrem talks to Fraud Magazine about his transformation into an evangelist for compliance and regulation in crypto and where he thinks the industry will go next.
Published in Fraud Magazine

In 2023, Christopher Linscott, CFE, CPA, CIRA, arranged a donation of $250,000 to the ACFE Foundation — the single largest donation to the foundation ever. Here’s the story of how a Ponzi scheme that bilked thousands of military veterans and retirees became the impetus for that donation.
Published in Fraud Magazine

Football — the international sport, with strikers and goalkeepers — is beloved around the world, but in an intense game where professional teams compete for wins and financial survival, fraud is commonplace. Here’s a primer on the many schemes on and off the field and meaningful steps that football clubs and leagues could take to fight fraud in the sport.
Published in Fraud Magazine

People might not be writing as many checks as they did in the past, but that hasn’t stopped fraudsters from pressing on with their schemes. The author examines why check fraud continues unabated even with the rise of noncash payment options.
Published in Fraud Magazine

Ukraine accuses Ministry of Defense and arms supplier of $40 million fraud; hundreds of sub-postmasters in the U.K. falsely convicted by the U.K. Post Office; and ESPN staff members illicitly secure Emmys for "College GameDay" on-air personnel.
Published in Fraud Magazine

ACFE President John D. Gill, J.D., CFE, shares some of his favorite insights from the latest edition of the ACFE’s biennial publication, Occupational Fraud 2024: A Report to the Nations.
Published in Fraud Magazine

Amanda Malusky Krauss’s passion for fighting fraud began early in her career when an employee of a firm she was auditing slipped her a note detailing a fraud committed by executives. Today, the lead for Axium Consulting’s internal investigations and forensic accounting practices says she’s driven to fight injustice and strives to always respect the humanity of the people she interviews.
Published in Fraud Magazine

One of four key types of analytics has long been considered a “pie-in-the-sky” concept for fraud investigators. Rather than describing or diagnosing something that’s happened or predicting what could happen, prescriptive analytics can tell us what we should do about it. With the growth of generative AI and large language models, it may just be in reach.
Published in Fraud Magazine

The FTC warns social media influencers and college students of job opportunities that are actually ploys to steal personal and financial information. Plus, identity thieves continue to scam people via work-from-home jobs and what you can do to avoid becoming a victim of these schemes.
Published in Fraud Magazine

Retired FBI agent Michael McCall has years of experience investigating white-collar crime in both the federal and private sectors. Throughout his career he’s learned that following the money is key to tracking criminals and continues to fight fraud as owner of an investigative company.
Published in Fraud Magazine

I’d been working for the ACFE for more than two years before I attended my first ACFE Global Fraud Conference. My first year — 1997 — the conference was held in Boston, Massachusetts. We had two educational tracks and a record crowd of 500 attendees. It was also the first time we had exhibitors. I think we had a total of five, including us. I’d never seen so many ACFE members together at one time. It was a little overwhelming being relatively new, but I had a great time and made friends I still have to this day. Fast forward to 2024, and our 35th ACFE Global Fraud Conference is now just weeks away, June 23-28, in Las Vegas, Nevada. It’s hard to believe how much our global conference has grown over the years.
Published in Fraud Magazine

The failure to prevent fraud offense, a key provision of the U.K.’s 2023 Economic Crime and Corporate Transparency Act, is expected to go into force later this year or 2025. The offense, part of the government’s overall strategy to fight financial crime, is meant to encourage corporate accountability for fraud. In this article, anti-fraud professionals assess the new law and consider what organizations might do to prepare as they await government guidance on “reasonable procedures” rules to prevent fraud.
Published in Fraud Magazine

In 2022, investigative journalist Jeff German had just begun picking at the threads of a story about a Ponzi scheme that targeted members of the Mormon church. But he was murdered before he got the chance to write it. After his death, another reporter, Lizzie Johnson, took up his mantle and finished the story for him. Fraud Magazine recounts Johnson’s and German’s investigation, and talks to Johnson about honoring German’s legacy and the perils that journalists can face on the job.
Published in Fraud Magazine

Many organizations provide fraud awareness training for their employees. In fact, according to survey results from Occupational Fraud 2024: A Report to the Nations, 63% of organizations provide awareness training for their staff. However, not all awareness training is created equal, and I’ve witnessed programs that fall short of their intended goals because they lack key elements. So how can organizations bridge those gaps for effective, adaptable and scalable fraud awareness training
Published in Fraud Magazine

In 2011, Diederik Stapel was a psychologist at Tilburg University in the Netherlands at the pinnacle of his academic career. He was dean of the university’s School of Social and Behavioral Sciences and had a prestigious reputation in academic circles. But that same year, Stapel came under suspicion for fraud, unleashing a chain of events that led to his dismissal after an investigation concluded he’d falsified 55 of his publications and 10 Ph.D. dissertations written by his students.
Published in Fraud Magazine

On July 19, 2021, the U.S. Securities and Exchange Commission (SEC) alleged that Aron Govil defrauded investors of over $7 million through a scheme using investor funds in two companies he controlled, Cemtrex Inc. and Telidyne Inc., for personal expenses. The SEC also alleged that Govil engaged in scalping, insider trading and failing to file required disclosures with the SEC.
Published in Fraud Magazine

The Spanish Civil Guard arrest 14 people led by a man in Morocco for conducting a scheme targeting families of missing migrants; the FTC refunds millions to victims of student debt forgiveness scams; and a woman uses TikTok to get her money back after scammers impersonate her bank and steal thousands of dollars.
Published in Fraud Magazine

Anti-fraud professionals across the globe expect generative artificial intelligence (AI) to be part of their fraud-fighting arsenals in the future, according to the 2024 Anti-Fraud Technology Benchmarking Report. In fact, an impressive 83% of respondents surveyed for the study anticipate that their organizations will add this technology to their anti-fraud initiatives over the next two years.
Published in Fraud Magazine

The new head of a milk processing plant in India was reviewing his company’s management reports when he noticed a glaring discrepancy in the amount of fuel indicated in the report and amount it actually had. The plant, which used the leaves and husks of eucalyptus to fuel its boiler, should’ve had 150 tons of fuel, or 20 heaps of eucalyptus. But the plant head could only find two heaps. He asked the head of engineering and the boiler manager to account for the discrepancy but only got evasive answers. When the company’s internal audit team began to dig into the fuel reports to resolve the discrepancy, they discovered that records were missing.
Published in Fraud Magazine

In 2022, the Association of Certified Fraud Examiners (ACFE) and the Institute of Internal Auditors (IIA) announced a partnership that sought to collaborate on “education initiatives that will raise the competency of each organizations’ members with regard to fraud auditing and investigation.” As I reflected on this announcement, it struck me that both internal auditors and anti-fraud professionals strive to protect the organizations they serve, and though the primary focus may be different, the opportunities to collaborate are indeed vast.
Published in Fraud Magazine

What makes fraudsters see dollar signs in their eyes? Personally identifiable information. Here are schemes designed to squeeze PII from victims via web links, the mail and insecure AI platforms.
Published in Fraud Magazine

Fraud Magazine examines how U.S. Attorney Damian Williams is leading the fight against financial fraud and public corruption from one of the most influential federal prosecutorial offices in the United States.
Published in Fraud Magazine

In recent years, stories of company founders committing fraud have proliferated in the news. By examining high-profile cases, the author identifies patterns and key takeaways for CFEs to better understand this seemingly all-too-common phenomenon.
Published in Fraud Magazine

White-collar criminals are adept at manipulating and exploiting the goodwill of others to carry out their schemes. Recognizing and understanding these behaviors are important ingredients in the fight against financial fraud. In this article, the author details criminal thinking traits through case studies of some of the most infamous white-collar fraudsters and provides strategies and tools that fraud examiners can use to recognize those traits.
Published in Fraud Magazine

The use of real-time deepfakes, where fraudsters use video or audio generated with artificial intelligence to replicate someone’s voice, image and movements as the scheme is happening, is the latest way that fraudsters are perpetrating a host of frauds. In this article, the authors describe real-time deepfake schemes and what can be done to combat them.
Published in Fraud Magazine

Fraud fighters recognize the ACFE’s Report to the Nations as the premier study of occupational fraud. ACFE CEO John Warren, J.D., CFE, takes readers on an in-depth tour of the 13th edition of this comprehensive report of occupational fraud, its perpetrators and victims, and its costs to help anti-fraud professionals better protect their organizations against this pernicious economic crime.
Published in Fraud Magazine

Whether you call it “friendly fraud” or a chargeback, refund fraud and abuse is on the rise and costing retailers billions. The author discusses what this fraud entails, what’s behind its growth and why this decidedly unfriendly scheme is so frustrating to fight.
Published in Fraud Magazine

Four women in England are victims of a romance scam; Yvette Wang, former chief of staff to accused fraudster Guo Wengui, pleads guilty to conspiracy to commit wire fraud and money laundering; and a mortuary worker in Arkansas pleads guilty to stealing human remains and selling them to a man she met in a Facebook group.
Published in Fraud Magazine

ACFE President John D. Gill, J.D., CFE, gives a behind-the-scenes look at the making of the CFE Exam.
Published in Fraud Magazine

At one time an aspiring artist, Association of Certified Fraud Examiners (ACFE) Board of Regents Chair Natalie Lewis, CFE, CPA/CFF, now investigates alleged employee embezzlement and business fund misappropriation schemes. She works to combat fraud locally and globally in her leadership positions for the City of Atlanta and the ACFE.
Published in Fraud Magazine

CFEs, lawyers and auditors – be on alert! The proposed PCAOB’s amendments to its auditing standards related to an auditor’s consideration of a company’s noncompliance with laws and regulations about financial statement audits will have a profound impact on our profession, bringing fraud risk management front and center.
Published in Fraud Magazine

Whether you’re drawn into a case as a fraud examiner, an auditor, or a customer encountering identity fraud, understanding credit risk modeling within financial organizations is essential. This knowledge is crucial regardless of your role because it impacts how financial products, from bank accounts to mortgages and student loans, are managed and secured globally. Appreciating how financial institutions assess the risks tied to each customer — whether an individual or a corporation — is fundamental for anyone engaged with financial services. This understanding shapes how we perceive the safety and reliability of financial products that affect everyday financial decisions.
Published in Fraud Magazine

In March, a U.S. district court shut down a student debt-relief operation that stole $8.8 million in junk fees from school debtors. Here we detail how others can avoid falling victim to scams that claim they’re helping people pay off their student loans. And a recent data security report sounds the alarm on organizations sharing data internally.
Published in Fraud Magazine

Cyber breaches and cryptocurrency scams dominated headlines in 2025 as fraudsters leveraged cutting-edge technology to steal billions. Yet, amid these high-tech schemes, some old-school fraud tactics resurfaced. Discover Fraud Magazine’s roundup of the year’s most notorious cases, as selected by the ACFE Advisory Council.
Published in Fraud Magazine

The questions you ask and how you ask them during interviews with suspects determine your ability to effectively — and ethically — resolve cases. But successful interviews depend on careful preparation. The author, a former police detective and interviewing expert, describes what can go wrong, how to construct effective questions and best practices for developing an ethically sound fact-finding interview.
Published in Fraud Magazine

The U.K.’s new “failure to prevent fraud” law, effective September 2025, makes large organizations criminally liable for lacking adequate anti-fraud systems. This article examines its impact on businesses, highlights weaknesses and proposed reforms, and offers compliance strategies.
Published in Fraud Magazine

Four men extradited in $5 million grandparent scam, pageant owners entangled in fraud and trafficking scandals, flood control corruption scandal sparks arrests and protests, and two executives convicted in $233 million ACA fraud scheme.
Published in Fraud Magazine

Health care fraud schemes targeted in U.S. and more.
Published in Fraud Magazine

Counterfeit wine is an age-old fraud scheme, but today’s tracing technologies make combating wine forgery more palatable. Here’s how to fight vintage fraud with current technologies.
Published in Fraud Magazine

Jaco de Jager learned to spot signs of fraudulent activity through his early work experiences and has helped prevent internal and external fraud at financial institutions and insurance companies. As CEO of ACFE South Africa, de Jager expanded the network in Africa and greatly contributed to the Chapter’s growth.
Published in Fraud Magazine

The evolution of impersonation and investment fraud is a call for institutions, regulators and individuals to adapt faster than fraudsters do. This article provides recent examples of impersonation and investment schemes, explains how social media propels them, examines the role of AI-generated deepfakes in these schemes and offers strategies that organizations can implement to combat deepfakes.
Published in Fraud Magazine

AI chat prompts and results can persist on third-party servers, posing security risks but also offering investigative value. The authors provide strategies to safeguard data and leverage it effectively.
Published in Fraud Magazine

In 2025, the U.K.’s education secretary ordered an investigation into allegations of millions of pounds of student loans claimed by a suspected network of fraudsters. Meanwhile, the U.S. Department of Education introduced measures to curb rising identity theft and fraud in federal aid programs. With high-profile cases of organized crime exploiting funds meant for students, Fraud Magazine examines fraud in school financial aid and strategies for prevention and detection.
Published in Fraud Magazine

Many countries are considering banning kids’ social media accounts. Australia has already taken the leap. But for all other wary parents, here’s help to protect their children from ubiquitous scams on their devices. And with U.S. tax season approaching, here are ways to safeguard tax professional firms and their clients from identity theft.
Published in Fraud Magazine

In a new ACFE research study, In-House Fraud Investigation Teams Benchmarking Report, 58% of anti-fraud professionals say their organizations have inadequate levels of anti-fraud staffing and resources.
Published in Fraud Magazine

Fraudsters are doing more than shutting down sites by flooding them with millions of automated inquiries. They’re infecting websites with malware that unsuspecting users are downloading on their devices. Here’s how to advise your organizations and clients to protect domain name servers that will prevent loss of revenue, productivity and reputation.
Published in Fraud Magazine

Most people don’t like being stuck in obscurity in their profession. They want recognition and compensation for their value. Here’s how to build a reputation or professional brand as an influencer in your anti-fraud field.
Published in Fraud Magazine

Deepfakes are no longer just amusing YouTube videos. Fraudsters are beginning to use them for business email compromises. Cyber experts say phone scams, sham celebrity endorsements, biometric fakes and bogus evidence could quickly follow. Now’s the time to advise your organizations.
Published in Fraud Magazine

An anonymous whistleblower hotline should be a critical weapon of any organization’s anti-fraud arsenal. Fraud examiners should understand some of the key success factors that make hotlines good tools in fighting fraud.
Published in Fraud Magazine

$50 million by age 50 could get lawyer 50 years; he’s just not that into you; not the outcome these execs were hoping for
Published in Fraud Magazine

The U.S. Department of Defense (DOD) is trying to ameliorate its deteriorating global advantage by using its Congress-granted “Other Transaction Authority” when working with vendors. But OTAs might allow fraud, waste and abuse to creep in. Here’s how the DOD can improve.
Published in Fraud Magazine

Jules Kroll didn’t start out to create one of the largest investigative firms in the world. However, he did recognize the need for such a service for corporations and governments after he battled corruption against his father’s printing business.
Published in Fraud Magazine

Trust your instincts, keep digging, look for patterns and know how to navigate technology to find anomalies. These are the skills Rachel Jolicoeur, CFE, has learned over the course of her career.
Published in Fraud Magazine

Artificial intelligence and machine learning seem to be included in most technology discussions. But what do these potential technologies really mean for fraud examiners and compliance professionals?
Published in Fraud Magazine

Jules Kroll assembles diverse professionals — fraud examiners, forensic accountants, academics, investigative journalists, former prosecutors and attorneys — to fight fraud. That’s been his modus oprandi since 1972. As chairman and cofounder of K2 Intelligence, he continues that course.
Published in Fraud Magazine

Fraudsters always find new ways to rip off consumers. They’re stealing money via gift cards, back- and knee-brace schemes and your American Express credit card.
Published in Fraud Magazine

The ACFE believes that large, noteworthy fraud cases like Enron or Bernie Madoff will live on in infamy and provide valuable lessons for fraud fighters and the general public. That is why we, along with input from our members, have selected the following five stories as the most noteworthy frauds of 2019. The stories were chosen based on the amount of money lost, the number of lives impacted and/or the relevance to the anti-fraud profession.
Published in Fraud Magazine

Telemedicine isn’t a new concept. It’s become an integral element of health care delivery. However, it’s prone to fraud opportunities because of the absence of direct patient contact. U.S. federal loosening of regulations during the pandemic has opened the door for more telemedicine visits and potential for fraud.
Published in Fraud Magazine

Raushi Conrad was a longtime, well-liked U.S. federal government high-tech specialist. He bucked the stereotype of the aloof, arrogant IT worker. But an anonymous email led to an investigation that showed he’d committed a one-man $1 million internal fraud scheme that involved chicken restaurants, computer viruses and “wink-and-a-nod” briberies. Here’s how to fend off similar high-tech crimes.
Published in Fraud Magazine

Lyn Cameron, CFE; Kenneth R. Dieffenbach, CFE; and Victoria Meyer, CFE, took their oaths of office as newly elected members of the Board of Regents during the board’s semi-annual meeting on Feb. 6 at ACFE Global Headquarters in Austin, Texas.
Published in Fraud Magazine

Can Benford’s Law practically identify fraud? It’s one of many tests you can use to discover fictitious numbers in supposedly random datasets, such as monetary amounts of purchase transactions. In this case, a comptroller successfully uses Benford’s Law to search for anomalies in warranty claims.
Published in Fraud Magazine

Fraudsters are beginning to find the cracks in the armor of blockchains and cryptocurrencies. Initial coin offerings, Simple Agreements for Future Tokens and fake currencies are vulnerable areas. Here’s practical information for warning your organizations and clients.
Published in Fraud Magazine

For years, journalist Daphne Caruana Galizia probed the activities of Malta’s ruling elite. She shared her findings — drug smuggling, money laundering, government corruption — on her blog, “Running Commentary,” and was regularly intimidated for her work. In 2017, she was murdered in a car bombing in Malta. Thousands have mourned her and demanded justice. Her son, Matthew Caruana Galizia, shares his mother’s story and how he and other investigative journalists worldwide are honoring her legacy.
Published in Fraud Magazine

Drexel University’s Fraud and Internal Control Case Competition (FIC3) lifts anti-fraud concepts off textbook pages and ingrains them into students’ lives. Learn how to help higher-ed institutions develop similar competitions.
Published in Fraud Magazine

Coronavirus stimulus check scam, infamous Russian hacker charged and Georgia man attempts to fraudulently capitalize on pandemic.
Published in Fraud Magazine

Daphne Caruana Galizia had the same dogged pursuit of fraudsters and the desire to bring them to justice that you do. She was an investigative journalist in Malta who was unwavering in her pursuit of allegations of corruption by government officials and businesspeople in her country. Tragically, she lost her life because of that pursuit.
Published in Fraud Magazine

Traditional corruption frauds — bribery, kickbacks and conflicts of interest — are affecting water management and availability in Australia. Droughts, fires, and floods are raising the stakes.
Published in Fraud Magazine

Mark Lee Greenblatt, CFE, says he’s learned the importance of being fair, independent and objective — as an individual and as a leader within his organization. “In the inspector general community, we have a special responsibility as the independent oversight mechanism within our departments, and I’ve learned that we can be effective only if we operate with integrity,” says Greenblatt, inspector general at the U.S. Department of Interior.
Published in Fraud Magazine

How should fraud examiners and legal professionals meet compliance standards but also keep individuals’ and organizations’ data private? “Differential privacy” is a system of cybersecurity that proponents claim can protect data far better than traditional sanitizing or anonymizing methods.
Published in Fraud Magazine

A business can legitimately sell its outstanding invoices for a percentage of their face value to receive money quickly to expedite cash flow. The process allows nearly $3 trillion in transactions per year worldwide. However, invoice factoring is vulnerable to fraudsters. This case shows red flags and susceptibilities.
Published in Fraud Magazine

In separate scams, fraudsters target would-be victims who are worried about packages they might never receive plus COVID-19 threats. The criminals play on fears to harvest personally identifiable information.
Published in Fraud Magazine

Ritchie-Jennings Memorial Scholarship program accepting applications; ACFE Board of Regents expels two members
Published in Fraud Magazine

Once a poster child for Germany’s fintech sector, Wirecard — along with its ambitious CEO — was exposed as a massive fraud that seduced investors. Learn how to analyze the case by emphasizing four attributes.
Published in Fraud Magazine

You can learn “charismatic/crisis-response” leadership characteristics to help your people continue their jobs without wavering. Crisis leadership requires intensely focused, committed actions to try to eliminate uncertainty, fear, panic and chaos.
Published in Fraud Magazine

This Lambo loan is a no-no; 6 former NFL players allegedly try to game the system; Czech your investors before you give them cash
Published in Fraud Magazine

As I listened to the stories of former U.S. Drug Enforcement Administration agents, Javier Peña and Steve Murphy — the inspirations behind the Netflix series “Narcos” — I sensed their passion for catching Pablo Escobar and other drug traffickers. Despite enduring constant danger and peril, they seized the mission to disrupt the narcotics trade in Colombia.
Published in Fraud Magazine

When Tasheika Hinson, CFE, was 8 years old, she made a pact with her childhood friend that they’d grow up to become attorneys. Hinson would go on to become an assistant U.S. attorney at the Department of Justice and now is the head of investigations at The Vanguard Group Inc. where she leads internal investigations and partners with internal teams in its 19 offices around the world.
Published in Fraud Magazine

The U.S. Department of Justice (DOJ) recently updated its “Evaluation of Corporate Compliance Programs,” the primary guidance for DOJ prosecutors when they assess penalties. These updates provide insights into the factors DOJ is likely to emphasize when it evaluates the effectiveness of your organization’s compliance program — should you come under scrutiny.
Published in Fraud Magazine

The ACFE had three months to plan a virtual 31st Annual ACFE Global Fraud Conference from scratch. The result is in the numbers and responses: 4,472 attended and 94 percent of the participants were satisfied. Lemonade never tasted so good.
Published in Fraud Magazine

In this excerpt from “Manhunters: How We Took Down Pablo Escobar,” retired U.S. Drug Enforcement Administration agents Steve Murphy and Javier Peña each share harrowing encounters with possible Escobar henchmen during their time in Colombia investigating and hunting the notorious drug lord.
Published in Fraud Magazine

On July 5, 2011, the tanker ship, Brillante Virtuoso, which was carrying 140,000 metric tons of fuel oil, was drifting within Yemeni waters. Later in the day, a small boat with seven armed men approached the vessel. The men, who claimed to be a “security team” to escort the tanker through the Gulf of Aden from the Arabian Sea, hijacked the ship and demanded that the vessel proceed to Somalia.
Published in Fraud Magazine

The recipient of the 2020 Educator of the Year Award, who owned a CPA firm for decades, had a lifelong desire to teach students forensic accounting and fraud examination at a university. In 2015, he got his chance. Now, he’s challenging ACFE members to do the same.
Published in Fraud Magazine

Retired U.S. Drug Enforcement Administration agents Steve Murphy and Javier Peña — the inspirations behind the hit show “Narcos” on Netflix — tell the tale of their time in Colombia, investigating and capturing notorious narcoterrorist and Colombian drug lord, Pablo Escobar. Not everything you see on TV is true, but their story comes pretty close.
Published in Fraud Magazine

January of this year now seems like a quaint time. Since then, the world has stretched in bizarre ways, and it probably won’t ever resume its previous shape. The Board of Regents want to encourage you as your organizations need your anti-fraud skills more than ever.
Published in Fraud Magazine

Fraudsters add to COVID-19 woes by ripping off unemployment benefits. And, of course, they’ve figured out how to profit from contact-tracing programs. Plus, employers must reduce risk of data loss and theft after layoffs and furloughs.
Published in Fraud Magazine

The COVID-19 crisis is forcing companies to tackle significant operational, financial and strategic challenges. And some employees might be tempted to engage in embezzlement schemes or even manipulate financial statements, among other improper acts, to address their immediate financial needs.
Published in Fraud Magazine

According to the ACFE’s 2020 Report to the Nations, organizations are favoring civil litigation and internal punishment over referring their fraud cases to law enforcement. Organizations opting for civil litigation increased to 28% in 2020 from the average of 23% for the past decade. Similarly, referrals to law enforcement have dropped from 69% in 2008 to 59% in 2020.
Published in Fraud Magazine

Anti-fraud professionals are uniquely positioned to diagnose sick occupational cultures. Here are answers about workplace cultures that can help head off fraud before it occurs.
Published in Fraud Magazine

At a U.S. military base, 2,400 rounds of government ammunition were missing. This NCIS special agent suspected a Marine Corps gunnery sergeant, but he needed definite proof. The special agent used an unusual mass-screening interview to discover evidence that ultimately led to the gunnery sergeant’s conviction.
Published in Fraud Magazine

Residents of C-suites and boardrooms who exhibit the “Icarus complex” often initially soar but ultimately plummet from lofty heights and take their companies with them. Here’s how organizations can identify them in the hiring process and prevent disaster.
Published in Fraud Magazine

The British Overseas Territories (such as The Cayman Islands) and the British Crown Dependencies traditionally have been jurisdictions fraudsters use to hide proceeds of crime. However, recent legislation on the Islands could make it easier to conduct investigations into fraud and white-collar crime.
Published in Fraud Magazine

Thousands falsely charged with unemployment fraud; another COVID-19 scam out of California; Fraud in the Wake of COVID-19: ACFE Benchmarking Report
Published in Fraud Magazine

One of the greatest challenges in our field is to think like the fraudsters we’re trying to stop. It’s not easy for CFEs to live inside crooks’ minds, but it’s important to put on those “glasses” and try to see our organizations from the fraudster’s mindset.
Published in Fraud Magazine

If resources are valuable, fraudsters will use them to commit crimes. And they love to misuse gold, diamonds and other glittery materials from the depths of the earth. Here’s how countries are battling the schemes and what it all means for fraud examiners.
Published in Fraud Magazine

Sudhir Gidwani, CFE, says in 1984 he first found tremendous joy piecing together the jigsaw puzzle of unearthing fraud during his investigation of the collapse of a major local bank in Hong Kong. “As my experience in fraud and corruption investigations developed, I became more passionate about what I was doing,” he says.
Published in Fraud Magazine

Organizations can’t afford to be oblivious. Anti-fraud professionals are trained to be skeptical. They should teach their “trust but verify” skills to all in their spheres. Here are some cases in which the players didn’t see (or refused to acknowledge) flaming-red flying flags and paid the cost in loss of cash and reputations.
Published in Fraud Magazine

During the COVID-19 lockdowns, how did fraud examiners manage evidence collection? Learn from forensic technology industry experts about collecting custodian information and remote data preservation.
Published in Fraud Magazine

Fraud examiners who work for health care providers should know the stipulations of the EU’s General Data Protection Regulation to protect patients from data breaches. The law also applies to U.S. organizations that provide care for EU citizens.
Published in Fraud Magazine

The last time you probably thought about supply chains was during the early days of the COVID-19 crisis when the toilet-paper shelves were empty. But that TP had to wend its way through a complex journey from pulp mills to your home that involved many parties and chains of events. Disrupt just one step — say because of pandemic fears or fraud — and the chain breaks. Here’s how to help prevent supply chains from fraudulent acts and mitigate them when they do break.
Published in Fraud Magazine

Fraudsters, disguised as potential customers, are sending phishing emails to businesses to foist on them a con game. And scammers are claiming to be approved lenders under the U.S. SBA Paycheck Protection Program, which is part of the Coronavirus Aid, Relief, and Economic Security Act.
Published in Fraud Magazine

Fraud examiners tend to de-emphasize the rationalization factor — to the detriment of prevention efforts. Here’s some of the science behind would-be fraudsters’ justifications and how we can use it practically to deter their crimes.
Published in Fraud Magazine

Published in Fraud Magazine

Six candidates have been selected to compete for two positions on the 2021-2022 Board of Regents. The board sets standards to promote professionalism and to ensure the reputation of the CFE credential.
Published in Fraud Magazine

Leadership is part art, part science and perhaps a bit of alchemy. Selecting individuals to lead companies has become more complex for boards of directors. CEOs must address the interests of all stakeholders — not just shareholders. Organizations should consider grooming honest and proven managers from within to help prevent and deter fraud.
Published in Fraud Magazine

These case studies will help inoculate medical practices against fraud through sound ACFE principles — from financial oversight to segregation of duties.
Published in Fraud Magazine

You might be a brilliant fraud examiner, but if your “emotional intelligence” is stunted, you’ll be ineffective with those you work with and investigate. Here’s how to buck the stereotypes of your hard-wired personality, learn practical ways to change your management style and be more empathetic in your job and life.
Published in Fraud Magazine

Fraudsters tend to steal in similar ways. Here are six number patterns you can search for and possibly find hidden fraud. Learn from the acclaimed authority on Benford’s Law on how numbers can become your best friends.
Published in Fraud Magazine

Defense contractor allegedly rips off $12.8 million in COVID-19 relief aid; Singapore charges businessman for claiming he held $1 billion for Wirecard; Grand Prix CFO’s tax-defrauding racer stalls
Published in Fraud Magazine

National agencies are adopting income-asset disclosure management systems to help ensure transparency and accountability among high-level political and governmental officials.
Published in Fraud Magazine

Interviewing narcissists during a fraud examination demand special skills. Here are some practical ways to interview those who have inflated self-perceptions and are missing solid self-esteem fundamentals.
Published in Fraud Magazine

From the President
Published in Fraud Magazine

When Priti Amin, CFE, was young she knew she wanted to do something that helped others because honesty, trust and personal integrity were important to her. Those values compelled Amin in her journey to fight fraud. Within Vodafone Group, a global technology communications organization, Amin is the Vodafone Business fraud manager. She’s responsible for managing fraud risks for the entity, its products, services and customers.
Published in Fraud Magazine

Given the current economic climate and regulatory expectations, monitoring procurement spending for fraud, waste and abuse (aka “leakage”) is even more important. We can proactively monitor procurement data via big data analytics, which will reveal transactions that are fraudulent or diminish working capital.
Published in Fraud Magazine

Use the new Anti-Fraud Playbook, produced by the ACFE and Grant Thornton, to operationalize leading guidance from the ACFE/COSO Fraud Risk Management Guide to help your organization move from theory to practice.
Published in Fraud Magazine

CFEs discuss how they know when they should devote resources to launch fraud examinations or at least preliminary investigations.
Published in Fraud Magazine

Travel and entertainment spending is common in many industries, but it also opens the door for disgruntled or seedy employees to steal from organizational coffers. Falsified invoices, altered receipts and spending on personal luxuries can add up. Fraud examiners can use data analytics and tested fraud examination techniques to root out employees with nefarious intentions.
Published in Fraud Magazine

The IRS won’t call you or text you to threaten jail. And the pandemic has created security threats and opened new opportunities for cybercriminals. Plus, tax pros need VPNs.
Published in Fraud Magazine

Incidences of fraud and counterfeiting are escalating in most high-stakes collectibles markets — take art fraud, coin fraud and wine fraud, for example. But the vintage comic-book industry stands impervious even as comic book values soar.
Published in Fraud Magazine

The growing pandemic of coronavirus disease 2019 (COVID-19) is a global concern. It threatens to disrupt everything from international travel and supply chains to health care operations and the global economy. Like other natural disasters, the outbreak has also become an opportunity for fraudsters to cash in on public fears.
Published in Fraud Magazine

Taz Kalolwala has worked her way up the corporate ladder during the course of her career, but it’s her people skills and team-nurturing abilities that sets her apart. She advises fellow CFEs to remain humble and continuously seek help from other anti-fraud professionals.
Published in Fraud Magazine

Published in Fraud Magazine

Fellow Certified Fraud Examiners elected Lyn Cameron, Kenneth R. Dieffenbach and Victoria Meyer to the 2020-2021 ACFE Board of Regents from candidates selected by the Board’s nomination committee. The three new regents took office at the Board’s meeting in February at ACFE headquarters in Austin, Texas. They replaced Ryan C. Hubbs, Tony Prior and Elizabeth Simon who’ve served their terms.
Published in Fraud Magazine

Cryptocurrencies and cybercriminals aren’t going anywhere. Here’s how some fraud examiners discovered systematic patterns of attacker activity at a bank and instituted controls that protected the institution and helped a cryptocurrency exchange prevent future attacks.
Published in Fraud Magazine

Employees in the trenches are tired of management talking to them like non-compliant kids. Instead, ask them to think with the curiosity, courage and clarity of kids. Here are ways to elicit anti-fraud compliance by understanding operating environments, clearly stating instructions, avoiding proscriptive rules and more.
Published in Fraud Magazine

A euphemism is an almost automatic and alternative method we use to phrase possibly negative things in a less harmful fashion. Fraudsters use euphemisms to rationalize their crimes. Fraud examiners can use them to elicit confessions or detect fraud in an organization. Here’s what you need to know to spot euphemisms and when fraudsters are using them to mask nefarious deeds.
Published in Fraud Magazine

Once fraud becomes part of an organization’s culture, it can spread and affect employees like a virus. But why would persons with apparently high ethical standards transform into fraudsters? And how can we counteract these fraud viruses?
Published in Fraud Magazine

‘Massive’ Ponzi scheme, Jordan Belfort sues and bettor makes bad gamble
Published in Fraud Magazine


Peruvian fraudsters take advantage of victims’ gullibility and interest in pre-Columbian Andean history plus the vulnerability of powerless indigenous peoples and rampant corruption to commit archeological frauds that exploit and denigrate cultures.
Published in Fraud Magazine

Howard Wilkinson smelled smoke when he was a trader for the Estonian branch of Danske Bank. The fire he discovered is a $230 billion debacle — possibly the largest-ever money-laundering scheme. Wilkinson’s investigative skills could help accelerate European reforms.
Published in Fraud Magazine

Siddharth Kher, CFE, first learned about the anti-fraud profession when he was working at Amazon. His curiosity piqued when he searched the internet for anti-fraud specialization courses and discovered the ACFE.
Published in Fraud Magazine

The U.S. Department of Justice appears to have collusion in its crosshairs with its formation of a procurement and collusion strike force. Here are typical schemes and red flags in the context of new DOJ guidance.
Published in Fraud Magazine

Fraud examiners are always working to persuade management to search for internal fraud and adopt wise prevention controls. However, anti-fraud professionals can only give their best counsel and then work hard for a good outcome. Here are a fraud examiner’s early successes in a case and later frustrating management decisions. Regardless, he’s not daunted.
Published in Fraud Magazine

Nothing’s sacred. Cybercriminals are now faking those “https” secure websites. Don’t fall for them plus assorted new phishing scams and fraudulent Federal Trade Commission letters.
Published in Fraud Magazine

A bond of trust joins auditors with all who depend on the accuracy and completeness of their findings. But venal executives, captured regulators and compromised auditors can subvert that bond, betray confidence and dissipate capital. This article offers key insights and best practices to help CFEs — including those who are auditors — expose and mitigate threats to audit reliability.
Published in Fraud Magazine

The startup world contains ample pressure, opportunity and willingness of entrepreneurs to rationalize decisions to secure market share and deliver on the promises they made to investors. Rarely do the teams that conduct due diligence for VCs and PE firms include someone with experience in detecting and investigating fraud.
Published in Fraud Magazine

Deborah Kovalik, a member of the ACFE since 1995, died Jan. 26, 2018. Kovalik was a director in the EisnerAmper Tax Department with a specialty in forensic, litigation and valuation services. Kovalik is survived by her husband, Walter Pagano, CFE, CPA, a partner at EisnerAmper LLP.
Published in Fraud Magazine

Certified Fraud Examiners elected Eric R. Feldman, CFE, and Bethmara Kessler, CFE, to the 2019-2020 ACFE Board of Regents. Fellow CFEs elected them from six candidates selected by the Board’s ACFE Nomination Committee. Feldman and Kessler took office at the board’s meeting in February at ACFE headquarters in Austin, Texas.
Published in Fraud Magazine

A pensive 25-year fraud examiner shares lessons on working well with colleagues and thriving in the profession. Though much has changed in a quarter of a century, foundational rules will always be in style.
Published in Fraud Magazine

Criminals are using a new form of fraud called credit privacy numbers (CPN) to defraud financial institutions and game credit bureaus. Fraud examiners will have to pool their resources and use investigative skills to connect the dots between credit bureaus and banks, and find new ways to combat this plague.
Published in Fraud Magazine

Fraudsters increasingly are using shell companies to commit everything from asset misappropriation and money laundering to bribery and corruption schemes. Audit committees want fraud examiners to make sure their organizations aren’t victims. Here’s how to use fraud data analytics to sniff out illegal shells.
Published in Fraud Magazine

Sentinels face few positive reasons for reporting questionable activity or fraud. They often lose their jobs, health, reputations and family stability. Yet every year a handful of whistleblowers step out from the crowd. Here are some reasons why they do it.
Published in Fraud Magazine

Hackers target DNA tests, elder abuse fraud costs soar and home goods giant accused of securities fraud.
Published in Fraud Magazine

Time thieves can become time fraudsters in the right conditions. Protect your employees and organizations by suggesting to top management and human resources departments that they embed sophisticated time-tracking software, procedures and training.
Published in Fraud Magazine

The ACFE bestows our Cressey Award annually on someone who’s demonstrated a lifetime of achievement in the detection and deterrence of fraud. This year’s winner couldn’t be more deserving. Lisa Osofsky, the director of the U.K.’s Serious Fraud Office (SFO), has devoted a lifetime of service to fraud awareness on a global scale.
Published in Fraud Magazine

The United Kingdom is a haven for dirty money. Some estimate that money launderers might be hiding 90 billion pounds per year — primarily through high-end real estate. The “Unexplained Wealth Orders,” introduced in 2018, might be stanching the flow.
Published in Fraud Magazine

As a criminal investigator and training & operations manager at the U.S. Army Criminal Investigation Command in Fort Hood, Texas, Kendrick Thomas, CFE, credits his expanding knowledge of white-collar crime to the connections he’s made as a Certified Fraud Examiner.
Published in Fraud Magazine

Members of the board of 1MDB — a Malaysian federal strategic investment fund — and top Malaysian government officials plus private citizens allegedly illegally syphoned and laundered billions from the fund. Here’s how they escaped controls and lined their pockets.
Published in Fraud Magazine

Lisa Osofsky views her dual citizenship as an advantage at the SFO. She’s worked in the anti-fraud private and public sectors, and in the U.S. and U.K. judicial and prosecutorial systems. She intends to use proactive techniques, global cooperation and the latest financial tools to make the U.K. an inhospitable environment for fraudsters.
Published in Fraud Magazine

Doing good deeds is generally recognized as positive. However, these gestures sometimes can be part of a psychological process to license and compensate for aberrant behaviors. A fraud examiner who’s aware of the potential psychological ramifications of these deeds might be able to proactively interdict fraud schemes and mitigate losses of these schemes.
Published in Fraud Magazine

Do you even answer your cellphone anymore? Fraudsters are sending phone messages with spoofed area codes, numbers and names. Here’s how to avoid the scammers plus information on college test prep scams and online payroll check thefts.
Published in Fraud Magazine

In August, the FBI began investigating a ransomware attack that struck 23 small local governments in Texas. Within these mostly rural municipalities, inhabitants have been unable to access birth and death certificates online, pay utility bills or engage in any city business or financial operations.
Published in Fraud Magazine

When ACFE Founder and Chairman Dr. Joseph T. Wells, CFE, CPA, stepped up to the podium at the 30th Annual ACFE Global Fraud Conference in Austin in June, the ACFE’s accumulated history accompanied him. As he accepted his induction into the ACFE Hall of Fame, he received it as a representative of the thousands who, but for his foresight, probably never would’ve received fraud examination education and skills.
Published in Fraud Magazine

In this ACFE News article, Fraud Magazine discusses how voting for the new Board of Regents begins in November, the Ritchie-Jennings Memorial Scholarship Program is accepting applications, Mary Sue Smith, a member of the ACFE since 2004, died June 13, and the Board of Regents expelled two members.
Published in Fraud Magazine

During an interview at the 30th Annual ACFE Global Fraud Conference, the Board of Regents opined on how to change corporate cultures, new corporate compliance guidance, ethics vs. profits and more.
Published in Fraud Magazine

An organization discovers devastating, costly fraudulent activity. It’s now waffling on spending money on a proactive fraud prevention plan. But while the fraud still stings, now’s the time for a consulting CFE — internal or external — to pitch substantive anti-fraud measures that could save the organization.
Published in Fraud Magazine

Fraud examiners and auditors at most organizations are cognizant of the risks of tangible assets mysteriously vaporizing. But it’s so much more difficult to keep track of proprietary digital information such as trade secrets, customer lists, product details, marketing strategies and PII.
Published in Fraud Magazine

Influencer marketing fraud, tax-credit fraud and restaurateur defrauds.
Published in Fraud Magazine

Tyler Shultz, our 2019 Sentinel Award winner, wasn’t a CFE. He was a young, idealistic, budding scientist who helped unravel one of the most prolific frauds in years. His intuition led him to start questioning what was going on at Theranos, a blood-testing company founded in Silicon Valley.
Published in Fraud Magazine

Poachers and hunters are committing fraud to enable slaughter of big game in southern Africa and shipping their trophies — or horns and tusks — over borders. One CFE is valiantly working to reverse the accelerating carnage and corruption.
Published in Fraud Magazine

The ACFE presented Norman DeBoer, CFE, the Certified Fraud Examiner of the Year award at the 30th Annual ACFE Global Fraud Conference in June. DeBoer, a detective with the Waterloo (Ontario, Canada) Regional Police Service for 29 years, completed in 2018 the precedent-setting $12 million financial advisor fraud case of Daniel P. Reeve, who received a 14-year prison sentence.
Published in Fraud Magazine

Complex business environments require fraud examiners to have diverse skills and holistic points of view to properly address the plethora of business risks. Escape your biases. Consider multiple sets of guidance to stay apprised to increase business transparency and dismantle silos of information.
Published in Fraud Magazine

Fraudsters have invented new themes on old schemes. They threaten to suspend Social Security numbers or tell victims they owe money to fake government organizations.
Published in Fraud Magazine

Opportunistic fraudsters often have an advantage over CFEs: They can freely and spontaneously select co-conspirators by skill, position and corruptibility. To level the playing field, CFEs can work more closely with other types of anti-corruption practitioners. Their experience and techniques, when combined with ours, frequently produce extraordinary synergies that outfox versatile criminals.
Published in Fraud Magazine

Tyler Shultz, Theranos whistleblower and ACFE Sentinel Award Winner, explains where things went wrong at the infamous blood-testing company and why he couldn’t sit back silently — even at the potential expense of his relationship with his grandfather, George Shultz, and facing the prospect of likely litigation.
Published in Fraud Magazine

The fact that the SEC continues to pursue AML violations, and in one instance sought a $23 million penalty, emphasizes that broker-dealers have a continuing incentive to comply with AML obligations.
Published in Fraud Magazine

The ACFE, with members around the globe, has contracts, compliance requirements, intellectual property issues and other matters that ACFE Associate General Counsel Jacob Parks, J.D., CFE, happily handles. “Fraud and corruption are the nemeses of a fair society, which was especially clear after the financial crisis of the late 2000s,” he says. “The ACFE’s mission of fighting fraud worldwide was appealing to me after I saw how much harm was due in large part to deceptive practices on a wide scale.”
Published in Fraud Magazine

The International Organization for Standardization (ISO) is developing new guidelines for whistleblowing management systems — ISO 37002. These international standards are scheduled for completion by the end of 2021. This article describes the background of ISO 37002, its scope and its added value for organizations around the globe.
Published in Fraud Magazine

The ACFE Foundation has awarded $55,000 to college and university students through the Ritchie-Jennings Memorial Scholarship Program for the 2019-2020 school year. Each recipient also will receive a one-year ACFE student membership.
Published in Fraud Magazine

Do you want to make sure you have more fraud in your organization? Then hire bad leaders and poorly train them with outdated methods. Here’s how to avoid employee disengagement by changing attitudes and behaviors.
Published in Fraud Magazine

Everybody loved Dr. Brian. He appeared to be the perfect professional, spouse, parent and friend. But he fooled everybody. At least for a while. Here’s how he, as the lead administrative physician of a once-thriving practice, skimmed and embezzled more than $25 million in 20 years.
Published in Fraud Magazine

Cybersecurity expert Theresa Payton says don’t wait until you’re in the middle of a breach to formulate plans. Practice digital disasters. Develop a playbook so everybody knows their roles. Line up your external helpers. Devise your communication strategy. Then, if you’re breached, cooler heads will prevail.
Published in Fraud Magazine

According to the May 15 ABC News article by Julia Jacobo, “96 people charged in Texas marriage fraud scheme to get Green Cards,” Houston fraudsters are responsible for granting citizenship to Vietnamese nationals who paid hefty fees. Police say ringleader Ashley Yen Nguyen operated a well-organized marriage scam — charging between $50,000 to $70,000 for a marriage license. As a result, nearly 150 people fraudulently obtained green cards to become permanent U.S. residents.
Published in Fraud Magazine

Container deposit fraud is more than just buddies transporting some empty soda bottles across state lines. We’re talking about multimillion-dollar tax fraud schemes. Here’s how to prevent them.
Published in Fraud Magazine

Modern technology advances quickly. What’s innovative and fresh one day can be quickly outdated and short-lived in just a few months. As smart devices get smarter, business and industry depend more heavily on them and the data they store, which makes fraud examinations more challenging and complex.
Published in Fraud Magazine

The Asia Pacific region has become a hotbed for cyber romance scams. Hong Kong cybercrime alone has risen 565% since 2012. The region’s global financial centers also face increasing concerns about cryptocurrency and blockchain money laundering fueled by North Korean cybercrime.
Published in Fraud Magazine

Fraud examiners are increasingly tackling complicated cases that simultaneously involve several nations. We must look for legal guidance for our organizations’ cross-border operations. Here’s a start.
Published in Fraud Magazine

Deshietha Partee-Grier, CFE, says she lives by an Eleanor Roosevelt quote: “Great minds discuss ideas. Average minds discuss events. Small minds discuss people.” Deshietha loves discussing ideas and the interplay among her colleagues as they fight money laundering and other types of financial crime. But work isn’t sufficient for her. She mentors high school girls when she’s not nurturing her five children with her husband and working on an MBA.
Published in Fraud Magazine

The compliance landscape forever shifted after the Enron and WorldCom debacles, among others. Don’t let accelerating corporate governance changes leave your organization and clients unprotected. Here’s how anti-fraud regulations evolve in phases around the globe, a review of compliance history plus practical action plans.
Published in Fraud Magazine

Oil theft and fraud affects everybody — not just those in far-away nations — because it enables everything from terrorist attacks to human trafficking. The author outlines thieves’ techniques and what countries are doing to battle this multibillion-dollar scourge.
Published in Fraud Magazine

Medical identity theft is the fastest-growing form of identity fraud. Crooks use a myriad of ways to defraud federal governments and vulnerable patients. Here are the schemes and ways to avoid becoming a victim.
Published in Fraud Magazine

This former intern learned firsthand about fraud when her boss and mentor, the senior accountant, was arrested for embezzlement and credit card fraud. The author helped discover the crimes at the nonprofit business.
Published in Fraud Magazine

Three million fraud complaints in 2018. That’s what the Federal Trade Commission received — many of them for identity theft. When we look at the stats since 2001, we see the fraud problem is worsening.
Published in Fraud Magazine

The ACFE Board of Regents voted to permanently expel two members from the ACFE.
Published in Fraud Magazine

Eric R. Feldman, CFE, and Bethmara Kessler, CFE, took their oaths of office as newly elected members of the Board of Regents during the board’s semi-annual meeting on Feb. 7 at ACFE Global Headquarters in Austin, Texas.
Published in Fraud Magazine

Bill Browder assumes the mantle of his fallen friend, Sergei Magnitsky, as he ferrets out fraud and corruption around the world and searches for $230 million in allegedly stolen laundered Russian funds. Despite the risks, this human-rights activist says he can’t look the other way.
Published in Fraud Magazine

Fraud examiners often stumble upon unsought information. Here’s how to train yourself to find that info so you can detect other potential frauds, obtain evidence, recover fraud-related losses, identify and correct deficiencies, and more.
Published in Fraud Magazine

Countries routinely use sanctions on nations to deter and penalize bad behavior. But what if economic restrictions cause criminals to seek the anonymity of alternative currencies? We possibly could see increases in fraud, money laundering and terrorism financing. Or not. The jury’s still out. Here’s what fraud examiners and law enforcement can do as nations move to their own parallel virtual and traditional monetary systems.
Published in Fraud Magazine

Here’s brutal honesty from CFEs who’ve spent decades as expert witnesses. Prerequisites: thick skin, penchant for over-preparedness and meticulousness, ability to think quickly, poise and a supply of heavy-duty deodorant.
Published in Fraud Magazine

The U.S. federal government disburses billions in grants annually to worthy recipients. These awards aim to make life better by promoting research and development, finding new disease treatments plus improving education, infrastructure, housing and much more. Of course, big money attracts fraudsters. Here we examine three main types of schemes and how fraud examiners can prevent and deter grant fraud. We also dissect the government’s latest anti-fraud guidance.
Published in Fraud Magazine

Yale dad uncovers college admissions scandal; West Coast ATM skimmers arrested; flooring company pays millions in penalties
Published in Fraud Magazine

Who’d have thought a multimillion-dollar fraud case would have the intrigue of a Cold War spy novel? And who could’ve predicted the irony of the grandson of the leader of the American Communist Party becoming a prominent capitalist in post-Soviet Russia? Truth really is stranger than fiction.
Published in Fraud Magazine

Fabulous wealth, staggering poverty, political imbalances and ancient tribal cultures can worsen fraud and corruption. But some organizations and governments in the Middle East are beginning to take tougher stances.
Published in Fraud Magazine


As cyber incidents become more complex, your organization’s ability to perform sufficient investigations must adapt. We explore pitfalls that businesses commonly struggle with as they deal with cyber incidents.
Published in Fraud Magazine

We are now at a tipping point in the field of lie and truth detection. Peer-reviewed research and high-stake applications are showing that we need two main skillsets to perform better than the average human and the polygraph: 1) recognizing deceptive behavior via multi-channel analysis and 2) using unexpected prompts in interviews to elicit truth.
Published in Fraud Magazine

In an episode of the popular television crime drama “Better Call Saul,” a lawyer stumbles upon a case of health care fraud. In real life, fraud examiners are leading the fight against these types of widespread fraud schemes by gathering evidence, analyzing documents and separating fact from fiction.
Published in Fraud Magazine

Shopping online is almost second nature now, right? But you could be jeopardizing your identity by just entering information into web page forms. Learn about “formjacking,” how fake Netflix sites are phishing for your PII, Medicare scams and more.
Published in Fraud Magazine

Anti-fraud professionals know that while it’s best to catch fraud as soon as possible, it’s even better to stop fraud before it happens — which is why active fraud prevention is a critical part of anti-fraud strategies for organizations of any size. The ACFE established International Fraud Awareness Week (Fraud Week) to give organizations a dedicated time to spread anti-fraud education with employees and within their communities.
Published in Fraud Magazine

You might not know it, but today is an important day for you. On Dec. 27, 1939 — 80 years ago — criminologist Dr. Edwin Sutherland, while speaking to the American Sociological Society, coined “white-collar crime” and placed the cornerstone in the foundation for the fraud examination profession.
Published in Fraud Magazine

On Feb. 10, 2015, Nova Healthcare Management pleaded guilty to felonious workers’ compensation fraud and agreed to repay Texas Mutual Insurance Company more than $6 million. The investigation revealed that Nova Healthcare Management (also known as Nova Medical Centers or Nova) overbilled Texas Mutual for physical therapy by billing services as more expensive one-on-one therapy when it actually provided group therapy.
Published in Fraud Magazine

It started with a phone call on Dec. 21, 2018. An 84-year-old Florida woman (we’ll call her June) received a call from a man who said he was attorney Thomas Wilson. He informed June that her grandson had caused an automobile accident, and the driver of the other car apparently was a pregnant woman who miscarried as a result of the accident. He said she was suing June’s grandson.
Published in Fraud Magazine

Fraudsters wield technology like weapons to commit their crimes. Fraud examiners must match and supersede their foes with advanced high-tech tools. Here are the results of a recent ACFE survey that show how anti-fraud professionals are using technology and their plans for the future.
Published in Fraud Magazine

Nine candidates have been selected to compete for three positions on the 2020-2021 Board of Regents. The board sets standards to promote professionalism and to ensure the reputation of the CFE credential.
Published in Fraud Magazine

On March 14, the Institute of Fraud Prevention (IFP) merged with the ACFE Foundation, which expanded the Foundation’s mission beyond college scholarships to cutting-edge, anti-fraud research that’s accessible to all CFEs. The IFP will now be known as the ACFE Research Institute. ACFE members and other anti-fraud professionals are the beneficiaries.
Published in Fraud Magazine

CFEs love fraud examinations that move in a linear fashion — from the general to the specific, gradually focusing on the perpetrator through evidence analysis. But life, of course, seldom moves in a straight line.
Published in Fraud Magazine

Like it or not, networking is key to professional success. Unfortunately, keeping our heads down and doing great work just isn’t enough to further our careers. Here are tips from a wise introvert on how to build your network.
Published in Fraud Magazine

When we have fewer emotional challenges, preoccupations and mental clutter we’re more actively aware of our surroundings. Our sharpened minds will be attuned to sights, sounds and other sensory input that can alert us to con artists’ attempts to hijack our emotions, our valuables and our dreams. Here’s practical information that you can give to your management, colleagues, families and friends.
Published in Fraud Magazine

The dark web is often seen as a mysterious and malevolent creature — built out of the myths and legends created by popular media and clickbait headlines. In reality, the dark web is home to a vibrant and thriving criminal ecosystem with a resilient fraud trade at the center of the action. Here’s what fraud examiners should know when they enter the underbelly of the internet.
Published in Fraud Magazine

Fraud examination is often challenging work, which involves various investigative skills. Be more successful in your engagements by focusing on these four traits that are shared by effective fraud examiners.
Published in Fraud Magazine

Dating app maker sued for fraud, three parents sentenced in college admissions scandal and drugmaker targets dementia patients.
Published in Fraud Magazine

As Emily Wilson, CFE, points out in her cover article, content on the dark web is designed to be hidden from search engines and from casual users. We can’t simply stumble across dark web sites by accident, Wilson writes. However, we might be surprised to learn that the dark web, which conjures images of abhorrent crimes, also stores legitimate common data and allows legal transactions.
Published in Fraud Magazine

Fraud moves like waves globally — disrespecting borders and nationalities. However, regions often have common crimes and recurring problems. Here’s a review of some of what we’ve covered since the column’s inception in 2018 plus recent developments.
Published in Fraud Magazine

Bernardin Assiene, CFE, found his passion for fighting fraud when he was tasked to investigate a financial fraud in the fuel distribution network at a major multinational American oil company in 1998. “The experience I gained and the lessons I learned shaped the rest of my career,” he says.
Published in Fraud Magazine

A typical medical practice operates with controlled chaos, generous trust of staff and two separate financial accounting software programs — all breeding circumstances for fraud. Here’s how to identify internal fraudsters’ schemes and apply remedies (even if you don’t work at a medical practice).
Published in Fraud Magazine

Think you’re completing your tax return? Think again. That frightening call from the Social Security Administration? Not who you think it is. And believe you’re getting the protection and settlement from the Equifax breach? Buyer, beware.
Published in Fraud Magazine

ACFE student member and CFE shares her journey as a young professional navigating the collegiate to on-the-job path using the help of the ACFE.
Published in Fraud Magazine

The ACFE has found that large, noteworthy fraud cases — like Enron or Bernie Madoff — will live on in infamy and can provide valuable lessons for fraud fighters. That’s why we, along with input from our members, have selected these five stories of 2018 as the most scandalous frauds of 2018. We chose the stories based on money lost, lives impacted and relevance to the anti-fraud profession.
Published in Fraud Magazine

Janet O. Hicks, a member of the ACFE since 2016, died August 13, 2018. “She was a wonderful colleague with a warm and friendly personality,” said Professor Ned Benton, her mentor, in the August/September 2018 issue of the John Jay News.
Published in Fraud Magazine

What really motivates people to be honest in business? That’s just one question economist Alexander F. Wagner is asking in his research. This University of Zurich professor will speak on some of his developing answers at the 2019 ACFE Fraud Conference Europe March 27-29 in Zurich.
Published in Fraud Magazine

Pulitzer Prize-winning investigative journalist Bastian Obermayer isn’t afraid of investigating the global elite. He’s spent his career digging into the uncomfortable truths of Nazi war criminals, abusive Catholic priests and crooked politicians. Obermayer set into motion the largest collaborative event in the history of journalism when he initiated the Panama Papers. He’ll receive the ACFE’s Guardian Award and speak at the 30th Annual ACFE Global Fraud Conference in Austin, Texas, June 23-28.
Published in Fraud Magazine

Burgeoning fraud against consumers is affecting millions. Two young investigative journalists at CNN recently reported an immense global mail fraud scheme targeting senior citizens.
Published in Fraud Magazine

My career journey has been a wonderfully long and winding road through incredible roles in a wide range of industries. I’ve audited, investigated and led large global teams of people whose services kept businesses running, including IT, finance, human resources, marketing, procurement and more. I’ve been lucky enough to work with leaders and teams that have inspired me to learn crucial career lessons along the way. As I think about those lessons, I’ve distilled them down to my top three.
Published in Fraud Magazine

Nigel Palmer, CFE, might be a native of Wales (and a dedicated rugby player), but he’s quite comfortable in the Middle East and Africa. As a former Royal Marines Commando, he learned strategies that he still applies to challenging fraud battles as security director at Mars, Inc.
Published in Fraud Magazine

Organizations are expanding into promising emerging markets. But they’re often encountering market volatility, geopolitical risks, weakening currency and fluctuations, and complex local laws, which can cause fraud and corruption risks. Here’s how to avoid some pitfalls.
Published in Fraud Magazine

Beware fraudsters who want to masquerade as your service providers. They’ll steal purchasing information, change bank account details and trick you into paying them.
Published in Fraud Magazine

Cinema heists, fraudulent pet food and more.
Published in Fraud Magazine

The initial exchange of the Panama Papers began at Bastian Obermayer’s parents’ home in Germany. His wife and kids were sick with stomach bugs, and he was graciously cleaning up one mess after another. In his words, it was a “really bad day.” He couldn’t know that one strange email would change his life, his newspaper and investigative journalism forever. The subject line read, “Interested in data?”
Published in Fraud Magazine

A report on money laundering in Canadian casinos by drug-trafficking gangs exposes more than just gamblers showing up with bundles of $20 bills. Here’s a lesson for fraud examiners whose blinders might force them to focus on just one type of fraud.
Published in Fraud Magazine

As your fraud risk landscape changes, so does the need to adapt and innovate. We explore how organizations are “operationalizing” anti-fraud innovation and continuous improvement.
Published in Fraud Magazine

You’re ahead of the curve — you’ve filed your tax return early, but then you discover that a fraudster has stolen your PII and already filed one in your name. You’re a victim of the stolen identity federal income tax refund fraud scheme.
Published in Fraud Magazine

We know how the Fraud Triangle helps explain the conditions that lead people to commit fraud. But what about the factors that could cause some to be predisposed to fraud? Here are some practical principles to consider when you’re working with fraud victims.
Published in Fraud Magazine

Organizations continue to be at risk because their auditors and accountants often don’t know about, or continuously look for, fraud red flags. And they don’t apply additional audit procedures to offer reasonable assurance that financial statements are free of misstatements due to fraud. Let’s help them and engage everybody in this good fight.
Published in Fraud Magazine

“We would not have the ACFE without Jim Ratley. Period.” So said Dr. Joseph T. Wells, CFE, CPA, founder and Chairman of the ACFE, at an in-house farewell reception on March 6 for President Emeritus James D. Ratley, CFE. Ratley has retired from the ACFE on his 30th anniversary. Bruce Dorris, J.D., CFE, CPA, formerly the vice president and program director, and an 11-year ACFE executive, has been appointed president and CEO.
Published in Fraud Magazine

The EU General Data Protection Regulation (GDPR) defines personal data as information relating to an identifiable individual, directly or indirectly. That word “indirectly” is important. By having indirect identification in scope, the regulation acknowledges that the traces one leaves behind online aren’t always the obvious descriptors like names and addresses.
Published in Fraud Magazine

Ryan C. Hubbs, CFE, CCEP, CIA; Tony Prior, MBA, CFE, CAMS; and Elizabeth J. Simon, CFE, CPA, took their oaths of office as newly elected members of the Board of Regents during the Board’s semi-annual meeting on Feb. 8 at ACFE headquarters in Austin, Texas.
Published in Fraud Magazine

Fraud fighters don’t successfully detect and deter fraud on their own — they use resources, contacts and the experiences of others to help save millions of dollars each year to their organizations. More than 3,000 anti-fraud professionals will gather in Las Vegas, Nevada, June 17-22, 2018, for the 29th Annual ACFE Global Fraud Conference to power up their network, boost their skills and recharge their careers.
Published in Fraud Magazine

The “Project Crane” investigation into alleged bullying and other inappropriate behavior of BT Italy executives uncovered the multi-year accounting fraud. In October 2016, BT estimated the fraud to be 145 million pounds. That number grew to 530 million pounds in just four months, and BT would lose more than 8 billion pounds in market capitalization as its shares entered a free fall.
Published in Fraud Magazine

Independent journalist Clare Rewcastle Brown, at the risk of her safety and without the protection of a news organization, has exposed the flow of billions of public Malaysian dollars from the government’s 1MDB development fund to the country’s top leaders and many others. She says democracies need strong, cynical, courageous media to help protect the public against the powerful.
Published in Fraud Magazine

Diamond fraudsters dupe consumers of all types, including savvy investors and collectors. The global diamond trade, like many other collectable markets, is at the mercy of the absence of transparency. Buyers must cautiously scrutinize gemstones and other low-utility/high-value objects. Here are practical ways for fraud examiners to avoid rip-offs.
Published in Fraud Magazine

As your organization grows, its business could expand into new nations. You might be conducting fraud examinations in cultures with unfamiliar social customs, laws and judicial systems. As I covered in part one in the January/February issue, you should have a solid cross-border investigative plan before you tackle a case with roots in several different countries.
Published in Fraud Magazine

In my November/December 2017 column I wrote that academia should expand traditional forensic accounting programs so our future professionals can respond well to contemporary fraud issues. Many universities do include additional training on identifying and understanding fraudulent activities and are hiring more instructors with practical experience.
Published in Fraud Magazine

'Pharma Bro' sentencing, Theranos CEO charged and beer fraud
Published in Fraud Magazine

Pablo Santamaría Cisneros, CFE, believes that a deep digital transformation is happening in the anti-fraud profession. “New cybersecurity and fraud threats are coming,” he says. As global anti-fraud senior manager at BBVA in Madrid, Spain, Santamaría is tackling these new threats by using data-driven business models and advanced analytics while adapting BBVA’s strategies to work with professionals, tools, methodologies and knowledge in the global community.
Published in Fraud Magazine

A global “quick-service” (i.e., minimal table service) restaurant business with thousands of locations accelerated its employee theft-and-error detection rate at the cash register by approximately threefold. Enhancements included the risk analysis of geographic regions, stores, employees and point-of sale (POS) transactions plus integrating “machine learning” for improved fraud detection.
Published in Fraud Magazine

Clare Rewcastle Brown just couldn’t ignore the corruption. “I could see it was a massive and underreported scandal of vast proportions,” Brown says in the cover article, written by Sarah Hofmann, CFE. “I asked why no one was covering it, and for some time I hoped someone else would. Then I realized all the local people who knew about it felt disempowered.”
Published in Fraud Magazine

Criminals have learned, through trial and error, that anonymous shell companies can pass scrutiny. Authorities and entities don’t question them, the fraudsters blend in and they don’t appear to be risky. They represent the next big sale, the new low-cost supplier or the helpful business agent. And organizations are eager to work with them. It’s time to start reversing this trend.
Published in Fraud Magazine

Susan West was perplexed when she received an email from the Internet Crime Complaint Center (IC3) notifying her that she was eligible for restitution after internet fraudsters had ripped her off. She didn’t remember that she’d been a victim. But she followed the directions to claim the restitution by clicking on an attachment, downloading a form that she filled out with her personally identifiable information (PII) and emailing it to the “IC3.”
Published in Fraud Magazine

Anonymous hotlines and tip-reporting structures are useless, of course, if informants don’t trust them. Employees won’t blow the whistle if they fear reprisals. So, their concerns often don’t enter case-management systems and frauds continue. Here’s how to earn back their trust, take them seriously and transform raw tips into valuable fraud examinations.
Published in Fraud Magazine

In 2017, Odebrecht, a Brazilian construction company, admitted to using bribery and corruption to secure more than 100 projects in 12 countries in Latin America, which generated illegal gains of about $3.3 billion. Odebrecht’s corruption reached the highest levels of government: The web of bribes implicated Latin American presidents, senators and officials.
Published in Fraud Magazine

An accounting firm took on a new client from the advice of a good friend, but it didn’t conduct proper due diligence. Big mistake. During an inventory, the client’s CEO repeatedly lied to the author — a fraud examiner — and the external auditors he worked with. Here’s how to avoid fraudulent clients and keep your sanity.
Published in Fraud Magazine

Hundreds of anti-fraud professionals will gather at the 2018 ACFE Fraud Conference Middle East, Feb. 25-27 hosted at Jumeirah at Etihad Towers by the ACFE and Abu Dhabi Accountability Authority (ADAA).
Published in Fraud Magazine

The ACFE scholarship award committee encourages all student members to apply for free main conference registrations to the 29th Annual ACFE Global Fraud Conference, June 17-22 in Las Vegas, Nevada.
Published in Fraud Magazine

Learning these principles will help you distinguish between good and poor denials and make you a better fraud examiner, executive and decision-maker.
Published in Fraud Magazine

Apart from drawing the scorn of industry regulators across the globe, Uber has been at the center of multiple fraud and workplace harassment allegations and numerous U.S. Department of Justice (DOJ) investigations. According to one Uber executive I talked to, who requested anonymity, the DOJ is conducting no less than six current investigations involving Uber.
Published in Fraud Magazine

Whether you’re promoting your expertise to a potential client, marketing a product to a possible customer or pitching an idea to your manager (or your spouse), you should first pique their curiosity before moving forward. You do that with a value proposition or positioning statement. (Business types once called it a unique selling proposition, but most have set it aside for this term that promotes value instead.)
Published in Fraud Magazine

The darknet is the latest example of technology that’s become a breeding ground for criminal activity. Combating virtual crime in this subset of the deep web is exceedingly difficult because of its anonymity. However, here are some ways law enforcement and fraud examiners are fighting these elusive miscreants.
Published in Fraud Magazine

You might eventually work on an internal fraud examination within your global organization that could cross several borders. You can immediately assume, of course, that your examination will be byzantine. If you don’t possess expert knowledge on international laws, procedures and cultural norms you’ll have to add team members who do.
Published in Fraud Magazine

In my November/December 2017 column I wrote that I’d like to share ideas on anti-fraud trainings and related issues to bring together practitioners, academics and students from around the world. Here I’ll focus on anti-fraud training needs in Europe. The International Anti-Corruption Academy (IACA) in Laxenburg, Austria, was formed to overcome shortcomings in anti-fraud knowledge and practice.
Published in Fraud Magazine

Student loan fraud, tighter enforcement on robocalls and college email phishing on the rise.
Published in Fraud Magazine

Depositions are grueling. Let’s say you’re an expert witness for the defense. As you walk into the conference room of the plaintiff’s counsel your heart rate ascends, your palms sweat and you reach for a glass of water as you sit at the table. You know what’s coming: incessant, pointed questions from attorneys as you give sworn testimony. You also know that all parties will use your words in court as evidence or as weapons to attack your inconsistencies.
Published in Fraud Magazine

“I’ve often said in mentoring staff that no matter how smart you are, no one’s successful without someone else giving them a hand up the ladder of success,” says Tom Golden, CFE, CPA. Golden, a professional speaker, author and retired partner at PricewaterhouseCoopers (PwC), now focuses on speaking engagements and the debut of his new novel but says he owes a debt to all who have helped him during his professional career.
Published in Fraud Magazine

Compliance professionals’ ultimate objective is a world in which employees receive only trainings and communications that are relevant to their roles, at exactly the right time (before they encounter compliance issues that require their attention) and in the right amount.
Published in Fraud Magazine

Kelly Richmond Pope, Ph.D., CFE, CPA, an associate accounting professor, has produced and directed a riveting documentary, “All the Queen’s Horses,” about Rita Crundwell’s historic $53 million embezzlement from the city of Dixon, Illinois.
Published in Fraud Magazine

Ransomware, which morphed from scareware fraud around 1998, isn’t abating. Fraudsters are still holding electronic devices ransom with creative variants and extorting money and personally identifiable information. Here are some of the historical and current developments plus ways to help others avoid ransomware.
Published in Fraud Magazine

New and different concepts can cause fear or hesitancy. However, biometric ID is no longer new and different; it’s proved efficient, effective and secure. The technology is part of everyday life for those younger than the baby-boom generation and probably for most baby boomers. Organizations that offer financial aid could increase security and a protection against fraud in their application processes by requiring a combination of a thumb and/or fingerprints plus numeric passcodes such as Social Security numbers.
Published in Fraud Magazine

Don’t let your performance suffer as an expert witness during a deposition because of an overbearing attorney asking the questions. Here are tips on how to keep your cool and do a great job for your client.
Published in Fraud Magazine

It’s all connected. From comic-book enthusiasts to conspiracy theorists to new-age acolytes — many believe that those seemingly random dots do connect. And now the “Internet of Things” (IoT) might start us down that road.
Published in Fraud Magazine

When Andi McNeal, CFE, CPA, was in graduate school finishing up her master’s and researching doctorate programs, she read an article written by Dr. Joseph T. Wells, CFE, CPA, founder and Chairman of the ACFE, in the Journal of Accountancy that mentioned the fraud examination course he was teaching at the University of Texas at the time. “I was trying to find a path to focus my doctoral studies on fraud — the intersection of accounting and human behavior has always fascinated me — and I ended up emailing Dr. Wells to find out if he had any suggestions or guidance about where I could find a Ph.D. program in white-collar crime,” she says.
Published in Fraud Magazine

More than 3,000 anti-fraud professionals gather at the largest anti-fraud conference in the world to power up their knowledge, networks and careers.
Published in Fraud Magazine

The $35 million “Fat Leonard” corruption scandal threatens to decimate an entire generation of experienced U.S. Navy officers. What unfolds is the rise and fall of the defense contractor who bought off Navy brass with meals, liquor, women and bribes.
Published in Fraud Magazine

The ACFE Board of Regents offer their counsel and ruminate on the dynamic anti-fraud profession during the 29th Annual ACFE Global Fraud Conference.
Published in Fraud Magazine

Once someone is entrusted in a fiduciary relationship, an opportunity is created for that person to become less trustworthy, or worse, a thief. Whether structuring a new fiduciary role to prevent fraud or investigating fraud after it has occurred, breaches of fiduciary duty are great sources of work for fraud examiners.
Published in Fraud Magazine

When corruption thrives and dirty money is kept in offshore accounts, Africa’s high levels of poverty remain. How do we reverse the trend? The solution lies in reviving countries’ primary educational standards and increasing fraud awareness and education.
Published in Fraud Magazine

Sports-memorabilia fraud, and cheating and housing scams.
Published in Fraud Magazine

Fraud examiners have implemented codes of conduct and compliance programs for decades in their organizations and agencies. Management challenges them to measure the returns on those programs and add an adjective like “integrity” to a list of potential fraud risks. But the overarching question is, “Are our people doing the right things at the right times for the right reasons?”
Published in Fraud Magazine

A recurring theme of scandals bringing down Iceland prime ministers illustrates citizens’ intolerance toward corruption. Yet are attitudes, protests and political repercussions enough to reverse the trend of worsening corruption in Iceland and other Nordic nations?
Published in Fraud Magazine

The ACFE presented Dave Cotton, CFE, the Certified Fraud Examiner of the Year award at the 29th Annual ACFE Global Fraud Conference in June. Cotton, who’s the chairman at Cotton & Company, LLP, has played a significant role in developing best practices in anti-fraud controls.
Published in Fraud Magazine

This article explores how to assess the strength of an organization’s integrity capabilities and operationalize integrity processes with contributions from Professor Eugene Soltes, Ph.D., of Harvard Business School, plus Jon Feig, CPA, and Andrew Reisman, J.D., of Ernst & Young LLP’s Forensic & Integrity Services practice.
Published in Fraud Magazine

Fraud examiners should consider an enhanced set of Fraud Triangle factors for executives: greed, pride and entitlement. But the question remains, why do these behaviors manifest in executives who might be associated with fraud?
Published in Fraud Magazine

Bluetooth can connect your phone to your car so that you can use the car’s stereo system. But vulnerabilities expose users to crooks wanting to steal personally identifiable information (PII). The column also covers phone hacking, another popular method of stealing PII.
Published in Fraud Magazine

When I started my career as a CFE, my background had been primarily in auditing and accounting, and most of my cases were corporate matters. Fraud victims were usually corporate entities looking to quantify a loss and mitigate the lapse in controls. I rarely encountered an individual who suffered a real loss because of a fraud scheme.
Published in Fraud Magazine

Six candidates have been selected to compete for two positions on the 2019-2020 Board of Regents. The board sets standards to promote professionalism and to ensure the reputation of the CFE credential.
Published in Fraud Magazine

Ileana Colón Carlo, a member of the ACFE Board of Regents from 1995 through 1996, and comptroller of Puerto Rico from 1987 to 1997, died March 19 at age 69.
Published in Fraud Magazine

Nirav Modi supposedly was one of the richest men in India. He came from a respected family and had close connections to the government. Could he really have pulled off a huge banking fraud to finance his business ventures?
Published in Fraud Magazine

Consider keeping investigative charges within corporate security and other anti-fraud functions. You might then increase reporting of fraud and other crimes.
Published in Fraud Magazine

This case involved a Nigerian crime ring that stole Apple computers and devices by impersonating U.S. defense officials. Make sure purchase orders pass the “smell test,” and call agencies to confirm.
Published in Fraud Magazine

Contract and procurement fraud, collusion and corruption can rob profits from victims. Bid riggers conspire to eliminate fair and open competition and allow some to monopolize industries. Here’s some help in detecting common contract and procurement fraud schemes, and improving the integrity of the contract-award process.
Published in Fraud Magazine

ACFE founder and Chairman Dr. Joseph T. Wells, CFE, CPA, is among professionals named this year’s Most Influential People in Security by Security magazine.
Published in Fraud Magazine

Digital analysis and search apps are invaluable. But nuanced interviewing, with an eye to discerning audiences, can yield solid evidence.
Published in Fraud Magazine

Scandal at the Vatican, health scams and ex-Enron CEO Jeffrey Skilling released from prison to a halfway house.
Published in Fraud Magazine

Most of our event speakers instruct from the knowledge they have in specific areas of fraud examination. But Kathe isn’t trained in law enforcement, auditing or compliance. She’s someone who noticed something wrong and had the guts and determination to shine a light on it.
Published in Fraud Magazine

It’s a familiar story. A country or region finally is prosperous, but inevitably fraud and corruption increase. Here are some infamous South Asian cases and ways the region has battled what affluence wrought.
Published in Fraud Magazine

Fighting fraud for Erik Anderson, CFE, is so much more than conducting an examination. “I fight fraud by making sure what we’re doing is right,” says Anderson. “Whether I’m on the front lines of an investigation or using the principles of a fraud examination to better understand the risk to the organization, being a good fraud examiner is about challenging yourself to stand up for what’s right and seeking that out with passion.”
Published in Fraud Magazine

New developments in forensic data analytics are breaking down traditional barriers to access, transparency and usability. You don’t need an advanced degree to use “data blending” software.
Published in Fraud Magazine

The ACFE’s 2018 Sentinel Award recipient had no intention of changing her orderly life as the city clerk of Dixon, Illinois. And then she found a secret account in city ledgers that led to discovery of Comptroller Rita Crundwell’s astounding $53.7 million fraud. Kathe Swanson’s life will be forever marked by her simple heroic decision.
Published in Fraud Magazine

Whether you’re at the beginning of your career — or second career — or you’ve had years of fraud examination experience, consider entering into a mutually beneficial mentor-mentee professional relationship. This article is for both of you and everybody in between.
Published in Fraud Magazine

We often focus on a fraud’s perpetrator, the conditions that allowed the fraud, plus the victim business and its owners. In this case, the authors cover the bases but also discuss the forgotten aspect: how the fraud affects so many more who live in the concentric circles around the fraudster.
Published in Fraud Magazine

If the oldest, largest and arguably most prestigious law enforcement agency in New England can become a victim of multiple frauds, what does that say about your organization’s exposure?
Published in Fraud Magazine

Learn some of the basic health care provider schemes and how to deter them from taking some easy money.
Published in Fraud Magazine

Memorial of Gilbert Geis, Ph.D., CFE
Published in Fraud Magazine

This column's author discusses the content and delivery of a senior-level, undergraduate elective course in fraud examination.
Published in Fraud Magazine

This column discusses some of the special situations of examining trade-skill education programs.
Published in Fraud Magazine

Case study of how a CFO, bullied by the CEO, used creative accounting and fraudulent schemes to falsely improve a company's bottom line.
Published in Fraud Magazine

Interview with W. Valen McDaniel, CFE
Published in Fraud Magazine

The author's team used analytical tests — including the Beneish M-Score Model — to construct a road map for investigation into a fraud.
Published in Fraud Magazine

In part 2 of two parts, the author describes some of China's plans to tackle emerging health care frauds and joint U.S.-China efforts.
Published in Fraud Magazine

Article on viable prevention options for small business fraud.
Published in Fraud Magazine

The author describes her fraud examination work on the case of humanitarian aid fraud and provides tips on working in Africa.
Published in Fraud Magazine

Disciplinary notices for Mark Dreaneen and Dr. Michael Seda, CFE.
Published in Fraud Magazine

Overview of banks that got into trouble, plus Libor
Published in Fraud Magazine

Interview with Tina Lusk, CFE, Area Controller, Northern Europe & Africa, OTIS, La Defense, France
Published in Fraud Magazine

Many auditors still have no idea what fraud means or how to incorporate an understanding of fraud risks into their work.
Published in Fraud Magazine

Detecting financial statement fraud is more complex than ever. Here are ways to investigate the books and the personalities behind the numbers.
Published in Fraud Magazine

Interview with Preet Bharara, U.S. Attorney for the Southern District of New York
Published in Fraud Magazine

In this column, the author recounts the case of the president of a small bank who stole funds through a complex loan fraud scheme.
Published in Fraud Magazine

External auditing firms are supposed to provide detailed, accurate and unbiased information about the financial situations of their clients. However, the author contends that the failures of many external auditors helped contribute to the “Great Economic Meltdown” and says we need a radical overhaul of the U.S. system of external auditing.
Published in Fraud Magazine

Overview and comparison of the IRS and SEC whistleblower awards programs
Published in Fraud Magazine

Here’s practical help for conducting risk assessments, developing global policies, employee training, monitoring, due diligence on third parties and more.
Published in Fraud Magazine

The ACFE Board of Regents expelled Robert Alonso.
Published in Fraud Magazine

Do U.S. CFEs need to be licensed as private investigators (PIs)? The answer isn’t particularly straightforward.
Published in Fraud Magazine

Overview of 7 case management system software systems and how they can help CFEs.
Published in Fraud Magazine

Overview of ransomware and ideas on how to prevent it.
Published in Fraud Magazine

Outline of the lessons we can learn from the Olympus scandal that may improve internal compliance and ethical issues in our corporations.
Published in Fraud Magazine

Social media can help investigations but hurt those future fraud examiners who post inappropriate content.
Published in Fraud Magazine

This column is the first in a three-part series presenting many scenarios of fraud and abuse in student fundraising activities.
Published in Fraud Magazine

In just more than one year the suspects had received almost $10 million in investor funds and then vanished without leaving a trace. Except for one little piece of evidence uncovered by the author.
Published in Fraud Magazine

Case study of an embezzlement
Published in Fraud Magazine

Case histories and practical information on what to do if a medical identity is stolen.
Published in Fraud Magazine

Overview of events and highlights from the 24th Annual ACFE Global Fraud Conference
Published in Fraud Magazine

As the ACFE begins celebrating its 25th year, Fraud Magazine invited the board members to a roundtable discussion to consider the future of the fraud examination and the ACFE.
Published in Fraud Magazine

This is the second article in a two-part series that provides an overview of case management software, which helps fraud examiners manage their workloads and digital information.
Published in Fraud Magazine

Article giving recommendations to avoid fraud and abuse in all types of student fundraising activities,along with several cases
Published in Fraud Magazine

Article on how anti-fraud educators can reach thousands of students via massive open online courses (MOOCs).
Published in Fraud Magazine

profile of CFE Jacqueline Pruitt
Published in Fraud Magazine

Interview with James Ratley about history of ACFE
Published in Fraud Magazine

Interview with 27 young CFEs to give readers a picture of the face of the fraud examination profession in the next quarter century
Published in Fraud Magazine

Overview of identity theft scams targeting elderly, mobile phone users and travelers
Published in Fraud Magazine

Case study on a Florida man defrauding elderly people of $450,000 by claiming to sell them hurricane shutters.
Published in Fraud Magazine

Case study of an insurance fraud involving arson
Published in Fraud Magazine

Overview on how to teach ethics to university and college students.
Published in Fraud Magazine

Interview with Michael Amory, CFE, Director, Global Ethics Case Governance, Walmart
Published in Fraud Magazine

Overview of the latest stats from the FTC's Consumer Sentinel Network Data Book.
Published in Fraud Magazine

Interview with David Green, CB, QC, Director of U.K.’s Serious Fraud Office
Published in Fraud Magazine

Part 2 of 2-part article on the future of the ACFE, as seen through the newest CFEs
Published in Fraud Magazine

QR codes are becoming a gateway for fraud
Published in Fraud Magazine

Learn how groups of tax cheats are stealing billions and how researchers and fraud fighters are finding new ways to beat them.
Published in Fraud Magazine

Article outlining affinity fraud, case histories and fraudster profile
Published in Fraud Magazine

Discussion on “strengths-based” vs. “deliberate practice” when it comes to building careers.
Published in Fraud Magazine

Case study of fraud in City of West Linn, Ore., and the efforts to rebuild the city's finance department
Published in Fraud Magazine

Article on third-party debt collection services fraud and ways to prevent it.
Published in Fraud Magazine

Article excerpted from book comparing Edwin Sutherland and Gilbert Geis and their contributions to the study of white-collar crime.
Published in Fraud Magazine

Interview with Shaun Aghili, DBA, CFE
Published in Fraud Magazine

Interview with Chris Mathers who worked undercover for 20 years for the Royal Canadian Mounted Police (RCMP), the U.S. Drug Enforcement Administration (DEA) and the former U.S. Customs Service.
Published in Fraud Magazine

Memorial article on Gil Geis, with interviews from colleagues and admirers.
Published in Fraud Magazine

The author contends that the failures of many external auditors helped contribute to the recent “Great Economic Meltdown” of 2008.
Published in Fraud Magazine

Bringing the real world into the classroom is challenging, but Tana Kristjanson and John Rankin, in this column, show how it can be done.
Published in Fraud Magazine

"Hello. This is John Wilson calling from the Federal Reserve Bank of New York Grants Department. You have been selected to receive a $9,000 federal grant based on your clean criminal history and the fact that you have paid your taxes on time. To claim your grant is very simple. You will need to pay a $250 processing fee to the Federal Reserve Bank of New York …” Would you have hung up?
Published in Fraud Magazine

ACFE Austin Chapter officers presented a proclamation from the Austin, Texas, mayor naming March 31, 2018, “James D. Ratley Day” to Ratley on the front porch of the historic Gregor Building at the ACFE Headquarters.
Published in Fraud Magazine

Wildlife trafficking has been defined as “any environment-related crime that involves the illegal trade, smuggling, poaching, capture or collection of endangered species, protected wildlife (including animals and plants that are subject to harvest quotas and regulated by permits), derivatives, or products thereof.” The Convention on the International Trade in Endangered Species of Wild Flora and Fauna (CITES) bans wildlife trafficking.
Published in Fraud Magazine

Certified Fraud Examiners elected Ryan C. Hubbs, CFE, CIA, CCEP; Tony Prior, MBA, CFE; and Elizabeth Simon, CFE, CPA, to the 2018-2019 ACFE Board of Regents from nine candidates selected by the ACFE Nominations Committee. Hubbs, Prior and Simon took office at the board’s meeting in February at ACFE headquarters in Austin, Texas.
Published in Fraud Magazine

U.S. public pension plans are facing an unprecedented crisis with an estimated shortfall of $1.378 trillion needed to pay benefits to retirees. Most pension funds have taken on higher-risk investments to seek increased returns. The rise and fall of the Dallas Police and Fire Pension System because of these non-traditional investments provides a cautionary tale with important lessons for CFEs.
Published in Fraud Magazine

In the January/February issue, we examined how Uber and its competitors have changed the hired car industry — and thereby changed the industry’s fraud profile. Here in part two, we take a deeper dive into some of Uber’s fraud, ethics and compliance issues that the business and mainstream press highlighted in 2017.
Published in Fraud Magazine

The Fraud Triangle has long illustrated the core principles of the ACFE’s training in understanding how fraud occurs. Here the authors suggest a revised Fraud Triangle that considers a more detailed look at a fraudster’s personal characteristics in addition to the rationalization component of the original triangle.
Published in Fraud Magazine

In our cover story, author Robert Tie, CFE, says Merriam Webster’s Thesaurus offers such synonyms for “whistleblower” (for obvious reasons, we prefer “sentinel”) as “betrayer,” “rat” and “snitch.” And he writes that these aren’t just words in a book; they’re manifestations of beliefs that incite and legitimize retaliation for perceived breaches of trust.
Published in Fraud Magazine

Africa’s environment promotes corruption because of its reliance on skimming, bribes and asset misappropriation within governments that are ineffective and can’t provide services and resources to their populations. Some countries in Africa have the highest levels of corruption in the world according to the Transparency International’s Corruption Index of 2016.
Published in Fraud Magazine

Jadon Fox, CFE, head of fraud control services at Taylor Fry, has analyzed countless transactions using sophisticated technologies and techniques, but he’s most proud of his relentless pursuit of dreams that live outside of the office. “My wife and I’ve always wanted to live overseas,” says Fox. “So, six years ago we sold our dream house, traveled 9,000 miles from home, settled in Australia where we knew no one and I began a job at Commonwealth Bank.”
Published in Fraud Magazine

Initial coin offerings (ICOs) are a recent phenomenon used for funding companies that are developing new digital currencies and associated technologies. However, companies offering ICOs are often eager to skirt securities regulations and disclosure requirements, leaving potential investors with vague or misleading information — and fraudsters with new opportunities.
Published in Fraud Magazine

Fraud examiners and compliance professionals have used continuous monitoring with evidence-based, anti-fraud prevention and detection analytics programs for many years. Historically, the volumes of data generated by businesses have far outpaced the ability of risk-oriented business functions to manage that data, and the inherent risks evident within it, but this is changing.
Published in Fraud Magazine

I was interested in the psychological aspects of fraud, so I conducted research that delved into the pressures and rationalizations of employees, which are closely linked with employee happiness and job satisfaction. I examined these in the context of a local non-governmental organization (NGO) in a developing country in Southeast Asia.
Published in Fraud Magazine

Why do we have so much trouble preventing and deterring fraud across borders? You know the answer: lack of cooperation. However, most European law enforcement organizations don’t want to compete with each other. They want to help each other deter and prevent crime. But they need some overarching force to help them work together. That’s where Rob Wainwright and Europol come in.
Published in Fraud Magazine

The grandparents' scam, which began about 10 years ago, is still claiming victims regardless of alerts from the media and government agencies. I’ve reported on this scam, but it’s important to address it again because fraudsters, of course, have devised a new-and-improved version that makes the voices of the targeted “grandchildren” even more believable.
Published in Fraud Magazine

Fraud Magazine recently spoke with veteran CFEs Ján Lalka in the Czech Republic, Jonathan T. Marks in the U.S., and Sean McAuley in Scotland about how fraud examiners can help organizations develop secure, workable whistleblowing programs. This article explains why they're essential and, in some cases, a matter of life and death.
Published in Fraud Magazine

"We don't have a lot of fraud." This unrealistic, and in my experience common, sentiment can lead to costly and disastrous outcomes. The fact is, organizations don't know how much fraud they have because fraud is invisible until they discover it. If you assume you have very little fraud, you'll pay for it.
Published in Fraud Magazine

Tax fraud, new Facebook news feed and more
Published in Fraud Magazine

Investors and regulators are concerned that cryptocurrencies are highly susceptible to price manipulation. This danger is particularly pronounced for the hundreds of small, thinly traded “altcoins” that have popped up in the wake of the success of bitcoin and Ethereum. In February, the Commodities Futures Trading Commission (CFTC) issued an advisory warning investors that these small virtual currencies are targets for pump-and-dump schemes.
Published in Fraud Magazine

Though fraud-risk teams worldwide don’t have psychics on staff (that we’re aware of), they can rely on predictive analytics to ascertain the future and assess the probability that third parties will commit fraud — or already have committed undiscovered frauds.
Published in Fraud Magazine

Few fraudsters have marketed their schemes on social media as effectively as the organizers of the catastrophic Fyre Festival. They branded the event as “the cultural experience of the decade” for wealthy millennials who were willing to spend thousands of dollars for an exclusive VIP weekend.
Published in Fraud Magazine

Leaders at all levels should daily use such high-level soft skills as collaboration, creativity, curiosity, problem-solving, communication skills, conflict management skills, strong work ethic, adaptability, social awareness, empathy, emotional intelligence (the arbiter between the rational brain and emotional brain) and clear self-expression (the ability to clearly express ideas, thoughts and opinions in a variety of media).
Published in Fraud Magazine

Between 1998 and February 2009, accountant James T. Hammes embezzled more than $8.7 million from his employer, G&J Pepsi-Cola Bottlers Inc. He was indicted shortly thereafter on 75 counts — including 38 for wire fraud and 36 for money laundering — but wasn’t arrested until May 16, 2015. Why did it take so long to arrest Hammes? After the FBI had questioned him in 2009 about the theft, he left his family and life, and began hiking the Appalachian Trail (AT).
Published in Fraud Magazine

A man in Los Angeles was determined to make a documentary that showed the anti-doping system in sport was a fraud. A man in Moscow helped construct that fraud. When Bryan Fogel and Grigory Rodchenkov met in 2015, neither could have guessed they’d land together in the middle of a dangerous geopolitical crisis that would expose decades-long corruption, shake up the Olympics and, ultimately, produce the riveting documentary, ICARUS.
Published in Fraud Magazine

Whistleblowers are “in.” We regularly hear spectacular U.S. stories of employees blowing the whistle on organizations and receiving large federal payouts from prosecution of multimillion-dollar fraud cases. But what’s the whistleblower situation in Europe and, more specifically, my home base, Switzerland?
Published in Fraud Magazine

App spam, terrorist financing via suitcases on flights and a psychic fails to see fraud in her future.
Published in Fraud Magazine

Bryan Fogel has most likely never performed a ratio analysis on corporate financial statements or testified in court during a fraud trial, but the story he told through the Academy Award-winning documentary, ICARUS, resonates with what we do as fraud examiners.
Published in Fraud Magazine

Did you think phishing campaigns were passé? Well, what’s past is prologue. Phishing attacks, which have increased 30 percent in each of the last three years, are still responsible for most data breaches. Here’s how to understand and prevent them from crippling your organization.
Published in Fraud Magazine

Johanna Duenser-Mardook, CFE, who’s always loved solving puzzles, says the fight against fraud is a never-ending puzzle to identify missing pieces in cases or internal controls. As the vice president, business initiative fraud policy manager at Citi, Duenser-Mardook says she thrives on closing loopholes that help prevent serious damage to a person or business, financially or otherwise.
Published in Fraud Magazine

You can’t escape blockchain. The topic’s in the media daily. It’s at the forefront of digital disruption and innovation discussions among leading businesses. We’ve seen blockchain technology applications in banking, currencies, supply chain, contracts and dozens of other areas.
Published in Fraud Magazine

The Fraud Triangle is tried and true, but we might need more to understand our cases. The authors describe a “meta-model of fraud” that combines the “why-based” Fraud Triangle with the “what-based” Triangle of Fraud Action to better explain fraud cases. We might never know exactly why fraudsters commit crimes, but we can always gather facts and evidence to help prevent and deter fraud.
Published in Fraud Magazine

Data analytics has been helping organizations detect fraud for years. But the future of fraud prevention and detection is looking toward new technologies, like artificial intelligence and machine learning, to stop fraudulent behavior before it costs companies millions.
Published in Fraud Magazine

Employees who handle cash in small towns often have few safeguards, so it’s easy for fraudsters to abscond with millions over several years. Here’s how to prevent and deter these supposedly trusted and longtime staffers and how to prosecute them under federal laws.
Published in Fraud Magazine

With the W-2 email phishing scam, the scammers ask payroll or human resources staff members for copies of W-2 forms for all employees. The forms contain a wealth of PII, including names, addresses, Social Security numbers, salary, wage and withholding information. The criminals use the pilfered information to file fake income tax returns and sometimes follow up with a request to wire transfer money to an account.
Published in Fraud Magazine

Lake Geneva's pristine water in Switzerland is renowned for attracting wealthy tourists and investors. But a few years ago a prominent resident made it the splashy backdrop for a spectacular embezzlement case.
Published in Fraud Magazine

Used to read and modify sensitive data stored in a website's databse, SQL injection attacks operate by inserting malicious code that sites' database servers process.
Published in Fraud Magazine

Applying Fraud Triangle Analytics to employee email communications can help organizations detect occupational fraud.
Published in Fraud Magazine

Identity theft and other fraud schemes are proliferating in the online world and privacy issues are becoming critical for businesses.
Published in Fraud Magazine

James H. Freis Jr., Director of the US Financial Crimes Enforcement Network, recently spoke to Fraud Magazine about FinCEN's mission and what fraud examiners need to know.
Published in Fraud Magazine

CFE can help deter fraud and mitigate some of the inefficiencies with public utility companies using many of the same methods we've used to solve dilemmas for other industries in the past.
Published in Fraud Magazine

In this column, Robert L. Bates, CFE, CPA highlights some of the various fraud risks that can occur and the red flags that indicate a fraud in progress.
Published in Fraud Magazine

A look at what cyber fraud issues may arise in an economic downturn by employees who have been layed off or those that remain with fewer internal controls
Published in Fraud Magazine

Part two of a two part series on missing disbursement documents is concluded by discussing alternative procedures you can use to determine if the transactions were made to valid vendors for authorized business purposes.
Published in Fraud Magazine

An Interview with Pamela Meyer Davis, ACFE's 2009 Cliff Robertson Sentinel Award Recipient and whistleblower whose efforts led to the arrest and indictment of former Illinois Gov. Rod Blagojevich
Published in Fraud Magazine

After 29 years of working in the gaming industry, Robert Rudloff, now vice president of internal audit for MGM MIRAGE, has had the opportunity to work through a wide variety of auditing and fraud challenges.
Published in Fraud Magazine

Before becoming an expert witness, make sure to study the past and current standards for the admissibility of expert testimony to ensure that you are familiar with the rules and case law
Published in Fraud Magazine

As more health records are computerized and made available to medical providers on the Web, more data breaches and medical record compromises will occur.
Published in Fraud Magazine

The 20th Annual ACFE Fraud Conference & Exhibition in Las Vegas sets attendee record despite recession. Read highlights from the event.
Published in Fraud Magazine

As the securities fraud scandal in San Diego illustrates, CFEs soon will have the opportunity to bring their expertise to a vast number of government public projects.
Published in Fraud Magazine

Companies are losing thousands of dollars in undetected "sub-material" fraud.
Published in Fraud Magazine

We now have tools we can use to search on the Web for the minutest details of suspected fraudsters. Use Google Alerts, social network sites, financial and relational blogs, classified and auction sites, plus new targeted search engines to find evidence that will stick.
Published in Fraud Magazine

This column will take a closer look at how cybercriminals operate underground economy servers.
Published in Fraud Magazine

Employee fraud often involves checking accounts and businesses need to take steps to prevent disbursement fraud.
Published in Fraud Magazine

Michael Chertoff, Secretary of the U.S. Department of Homeland Security, speaks to Fraud Magazine about the lessons he has learned in his career as a fraud fighter.
Published in Fraud Magazine

U.S. Laws and regulations, accounting and auditing associations, and circumstances encourage us to update our anti-fraud plans. But now we have adequate guidance to ensure compliance and deter fraud.
Published in Fraud Magazine

Entrepreneur Tom Petters has been charged with selling billions in merchandise that never existed. Learn how this happened and how frauds like this can be prevented.
Published in Fraud Magazine

Resilient corporations generally take a three-pronged strategy to deal with the problem of fraud: they conduct thorough fraud risk assessments and periodically revisit them; they put fraud prevention and detection strategies in place; and they develop response strategies to deal with the frauds they aren’t able to prevent.
Published in Fraud Magazine

Many entities have imprudent risk cultures or elaborate ethics codes that aren’t instilled among employees. CFEs can take a lead role in guiding companies through the essential fraud prevention process of creating an effective and vibrant risk culture.
Published in Fraud Magazine

This column, the first in a series of three, begins a discussion about some of the most common issues fraud examiners face when they detect false or altered documents in the organization’s disbursement records.
Published in Fraud Magazine

The accounting for the securitization of financial assets, particularly subprime home loans, has been defined by arcane accounting rules that helped many companies conceal mountains of debt and provided for the upfront recognition of massive and unearned future profits.
Published in Fraud Magazine

When the American economy slowed in 2007 and home prices stagnated, a domino effect relentlessly began to play out that had wide-reaching effects on the global economy.
Published in Fraud Magazine

Neil Barofsky walked into an enormous, historic job when he became the special IG for TARP last year. But he knows that his relentless push for transparency and dogged pursuit of fraudsters will protect his bosses – the American taxpayers.
Published in Fraud Magazine

A historical rundown of prominent whistleblowers and the cases that made them famous as well as the laws in place that help to protect them
Published in Fraud Magazine

Former Special Agent William Miles examines a Florida fraud case involving a vehicle dealership defrauding a bank with a reflooring scheme.
Published in Fraud Magazine

The best protection against a data breach of personally identifiable information is prevention, but you must still be prepared to investigate and manage a possible crisis.
Published in Fraud Magazine

Proper reviews of bank reconciliations can prevent or detect check fraud by employees.
Published in Fraud Magazine

Fluctuating gas costs and tough financial conditions are tempting employees to steal in creative ways. Don't get caught with outdated controls and review systems.
Published in Fraud Magazine

Learn from CFE and business owner Ralph Summerford as he shares lessons from the early days of his firm to the challenges he now faces.
Published in Fraud Magazine

As fraud examiners, we often suggest that organizations develop formal written procedures for preventing and detecting fraud and communicating ethics policies. "Managing the Business Risks of Fraud," a joint publication of three associations, provides the blueprint for indispensable anti-fraud planning.
Published in Fraud Magazine

Dinev's Compass for Fraud Detection offers a step-by-step blueprint - a review for CFEs and a primer for students - to evaluate possible fraud.
Published in Fraud Magazine

Private-bank executive managers often feel that they can't touch relationship managers, especially if they hold senior positions, because they reap large profits. So, banks often quietly resolve internal fraud cases without telling even their employees.
Published in Fraud Magazine

Harry Markopolos, CFE, CFA, couldn’t have known that his first fraud examination would last nine years and uncover the largest-ever Ponzi scheme.
Published in Fraud Magazine

Examining network event logs in a fraud investigation will yield more evidence contained within the trail of information left by a user’s online activity than any other technical resource.
Published in Fraud Magazine

This article focuses on how to incorporate advanced analytics techniques and presents an innovative way to calculate a fraud-risk score by applying the Fraud Triangle theory to e-mails.
Published in Fraud Magazine

This column underscores the importance of reviewing the volume of activity in small checking accounts, and it also offers lessons from the past – what fraud examiners can learn from actual case histories.
Published in Fraud Magazine

Computer forensics investigations must be a critical component of your tool kit and special training will help you hire experts, find digital evidence, and prepare for a judge and jury.
Published in Fraud Magazine

Take a look at the lessons from Markopolos’ journey for justice to learn to prepare our students to be the best future fraud fighters.
Published in Fraud Magazine

CFEs and auditors must be on the lookout for miscast worker/employer relationships and determine if professional service providers actually are independent contractors illegitimately reported as employees.
Published in Fraud Magazine

A fictional case designed for classrooms or seminars to illustrate important aspects of the fraud examination process.
Published in Fraud Magazine

Here's the case history of an engineer at a municipal transit district who went into the kickback business until the FBI caught up with him. Excerpt from "Bribery and Corruption Casebook: The View from Under the Table"
Published in Fraud Magazine

Article on creating and promoting your "professional brand," which will help you take advantage of job opportunities
Published in Fraud Magazine

An interview with John Fisher Weber, CFE, CPP.
Published in Fraud Magazine

Part 1 of this article focuses on the global impact of the relationship between international money laundering and human trafficking.
Published in Fraud Magazine

Book excerpt from "Liespotting" by Pamela Meyer
Published in Fraud Magazine

Here are the U.S. federal government's latest anti-money laundering efforts plus ways CFEs can help businesses cope with schemes and payment technology risks.
Published in Fraud Magazine

After an epiphany at her Harvard reunion, Pamela Meyer, CFE, embarked on a three-year research adventure to discover how and why people deceive. She shares much of what she learned so fraud examiners can become liespotters.
Published in Fraud Magazine

Suspects and witnesses often reveal more than they intend through their choices of words. Here are ways to detect possible deception in written and oral statements.
Published in Fraud Magazine

The authors' analysis of data-breach statistics shows that organizations poorly protect personal data. Possible solution: U.S. federal rules for guidance in developing comprehensive data protection programs.
Published in Fraud Magazine

In the following case, we will show how delayed bankruptcy schedule filings, inaccurate bankruptcy schedules and incorrect monthly operation reports can create an opportunity for a dishonest debtor to misappropriate assets of a bankruptcy estate.
Published in Fraud Magazine

During an investigation, we scour the web and social networks for employment backgrounds, contacts, education history and past behavior. However, we should be concerned about information we are posting that the bad guys can use against us.
Published in Fraud Magazine

We begin this three-part series with employee abuses of general organization credit cards.
Published in Fraud Magazine

A major, multimillion sports ticket fraud at the University of Kansas highlights how CFEs can help convince administrators and boards to reassert control over their athletics departments.
Published in Fraud Magazine

Houses of worship are particularly vulnerable to fraud, but most feel they are impervious. The authors provide reasons why churches feel so bulletproof and seven practical steps fraud examiners can use to help churches stop fraud in its tracks.
Published in Fraud Magazine

The reality is that there is probably a mixture of everything from fact and fraud to analysis and anxiety within the perceived red-hot Chinese stock market.
Published in Fraud Magazine

Follow this CFE consultant as he uncovers top collection reps at a business call center who inflated their performances for more money and job advancement. Lesson? Do not always follow the money.
Published in Fraud Magazine

This article outlines the latest schemes by fraudsters: delinquent payday loan and LinkedIn scams.
Published in Fraud Magazine

Three former frat brothers devised a high-tech scheme to win $3 million at the Breeders' Cup. Here's how they did it and how investigators quickly caught them.
Published in Fraud Magazine

Excerpt from "Bribery and Corruption Casebook: The View from Under the Table" about an elaborate web of bid-rigging and kickback schemes in a district of the Ohio Department of Transportation, spanning more than a decade, that cost the state at least $11 million.
Published in Fraud Magazine

Tips on incorporating tax fraud in a fraud examination class
Published in Fraud Magazine

Overview and case histories outlining phone fraud and abuse
Published in Fraud Magazine

Is a financial institution making an investment hedge or wager bet when engaging in certain trading practices? When do these bets border on fraud?
Published in Fraud Magazine

Small-town comptroller Rita Crundwell has pled not guilty to embezzling $53 million. Here is the investigation by Otterbein University professor Henry C. Smith, III, and his students.
Published in Fraud Magazine

An interview with Lisa S. Duke, CFE.
Published in Fraud Magazine

Identity theft is alive and thriving. The U.S. Federal Trade Commission's Consumer Sentinel Network reports a significant increase in complaints.
Published in Fraud Magazine

In part 1 of 2 parts, Al Scott, CFE, describes lesser-known but emerging health care frauds, including fraudulent treatments, cures and devices, and crimes involving the manufacture, sale or distribution of unapproved FDA-regulated products.
Published in Fraud Magazine

Speaking from the front lines, three CFEs tell how they provide state-of-the-art services to meet client needs' of finding and returning fraud proceeds
Published in Fraud Magazine

Disciplinary notices for Joseph Barbagallo and Luis Santiago
Published in Fraud Magazine

The authors describe cases in which companies ignored the warning signs and faced the consequences of inadequate anti-money laundering programs.
Published in Fraud Magazine

In starting your firm, this article covers some specific aspects of being a new entrepreneur, including the legal forms of business organizations, insurance, tax responsibilities and retirement savings.
Published in Fraud Magazine

Case study of a small-town comptroller, Rita Crundwell, accused of misappropriating more than $53 million in city funds. She has pleaded not guilty.
Published in Fraud Magazine

Interview with Diana Henriques, the first reporter to obtain jailhouse interviews with Madoff, and who muses about the damages he caused and the lessons for all.
Published in Fraud Magazine

Article on risks and lessons learned from a case regarding fraud in fuel inventory
Published in Fraud Magazine

Part 2 of an article about a false billing scheme case study
Published in Fraud Magazine

Interview with Joe Ford, CFE, Executive Vice President & Chief Security Officer, Bank of the West; ACFE Regent Emeritus; ACFE Foundation
Published in Fraud Magazine

Case study involving multiple frauds that outlines the wisdom of early interviews, the problems of "investigative myopia" and the advantages of limiting the scope of a fraud examination to save time and discover evidence.
Published in Fraud Magazine

In this inaugural column, Lauren E. Davis, CFE, ASA, a consulting manager with Pershing Yoakley & Associates, P.C., describes recent cases, pertinent U.S. legislation and governing agencies, typical schemes and ways to detect and deter health care fraud.
Published in Fraud Magazine

The mobility of laptops led to an exploitation of personal data through loss and theft, but the movement to smaller portable devices represents a much larger opportunity for cyber criminals to exploit data. This article describes how they do it.
Published in Fraud Magazine

Book excerpt from 'Wizard of Lies' by Diana Henriques
Published in Fraud Magazine

In the last three decades, China has shown stunning economic and social progress. However, its super achievements have come at a cost — the dramatic resurgence of corruption and widespread fraud. Here are ways that multinational companies can keep out of trouble in China.
Published in Fraud Magazine

Tips on how to start your own anti-fraud business.
Published in Fraud Magazine

The rise in contract management and the outsourcing of goods and services has created an increase in procurement fraud. Here are some red flags that can help you save millions.
Published in Fraud Magazine

Here's help for your team on fraud brainstorming for your audit plans: delving into the details, thinking like a fraudster and using the knowledge of the processes to increase awareness of where frauds may be hiding.
Published in Fraud Magazine

We must be aware of the differing red flags of fraud, waste, and abuse (FWA), and interpret these often subtle warning signs.
Published in Fraud Magazine

Case study of a false billing scheme.
Published in Fraud Magazine

An interview with Derrick M. Copeland, CFE.
Published in Fraud Magazine

International money laundering has become a key tool in facilitating human trafficking. The author outlines how the U.S. has entered the fray and the challenges facing it and the international community.
Published in Fraud Magazine

Part of 2 of money laundering article, with reports from CFEs on six continents.
Published in Fraud Magazine

Let's look at some history about the government's philosophy on compliance and whistleblowing activity.
Published in Fraud Magazine

Embezzlement case study involving a personal assistant.
Published in Fraud Magazine

Profile of Steve Ozan, CFE, Global Fraud Prevention Project Manager, Discover Financial Services
Published in Fraud Magazine

This column is the first in a series on data analytics and their use in fraud detection and investigation. Here, we introduce the topic while subsequent columns will focus on specific methods and techniques.
Published in Fraud Magazine

Sophisticated fraudsters may be able to conceal their frauds, but they may not hide their workplace deviant behaviors. Identifying or recognizing a correlation between the two could significantly uncover fraud.
Published in Fraud Magazine

Revenue accounts are fraudsters' favorite targets in financial statement frauds. As CFEs, we need to understand the underlying causes and motivations for overstating revenues.
Published in Fraud Magazine

This column explores the value anti-fraud graduates can bring to business environments and how anti-fraud education can benefit students.
Published in Fraud Magazine

Article on rogue traders, including their characteristics
Published in Fraud Magazine

Companies need to use the latest technology and testing methodologies to uncover red flags and patterns that could indicate corrupt schemes and transactions.
Published in Fraud Magazine

Article and interview with Michael Woodford, 2012 Sentinel Award recipient and Olympus whistleblower
Published in Fraud Magazine

With an aging population worldwide, soaring health care costs and people outliving their financial foundations, fraudsters increasingly are taking advantage of the elderly and aging.
Published in Fraud Magazine

Article describing how fraudsters are exploiting the cellphone arena to market their scams and harvest personally identifiable information.
Published in Fraud Magazine

Members of the Board of Regents discuss the ACFE's effect on the profession, looming frauds, global topics, spreading the word, anti-fraud research, and catching the bad guys.
Published in Fraud Magazine

Hackers penetrated a large retailer's central database and stole at least 45 million credit card and debit card numbers along with 456,000 customers' personal information. Fraudulent charges approaching $100 million appeared around the world.
Published in Fraud Magazine

Malware -- malicious software -- has been around for years. From the (c)Brain virus in 1986 -- the first to affect the PC -- to the Sasser worm in 2003, scores of viruses and worms have plagued computers.
Published in Fraud Magazine

One of the oldest home-improvement companies in Washington had bad news for its 210 employees: they wouldn't be receiving holiday bonuses. The owner discovered that an accountant had embezzled $1.2 million in five years.
Published in Fraud Magazine

Clients often don't understand the process, litigators lack the training, and accountants don't have the mandate. CFEs are poised to assume an even more responsible role in fighting fraud in the marketplace.
Published in Fraud Magazine

ACFE Founnder and Chairman Dr. Joseph T. Wells sat down for a Q&A session with Fraud Magazine.
Published in Fraud Magazine

Fraud examiners have tough jobs, but they could be tougher without sentinels -- courageous insiders who risk all to do what's right. Here we revisit sentinels who have been honored through the years in Fraud Magazine.
Published in Fraud Magazine

Bank fraud involves the use of fraudulent means to obtain something of value from a financial institution. There are numerous types of bank fraud including identity theft, account takeover, loan fraud, wire transfer fraud, and check fraud.
Published in Fraud Magazine

I am delighted to have been able to play a part, however small, in the life story of the ACFE. I owe the organization a debt of gratitude for the pleasure and knowledge that it has given me. And I want to join in the congratulations on its 20th birthday and offer wishes for many more wonderful years.
Published in Fraud Magazine

In a mere two decades, the ACFE has produced a grass-roots, anti-fraud movement that's just getting started. Though the ACFE seemed to spring up almost overnight, its philosophical ideas had been brewing in Wells' imagination for years.
Published in Fraud Magazine

Martin Biegelman, CFE, ACFE Fellow, discusses the fraud prevention program he built as a director at Microsoft: Microsoft's Financial Integrity Unit. Biegelman explains the structure and purpose of the FIU and how it contributes to a culture of compliance.
Published in Fraud Magazine

As fraud examiners and auditors, it's crucial that we not only comply with professional standards but that we go way beyond the call of duty. During an investigation or audit, break away from the desk the client assigned to you, walk around the job site, make friends, ask questions, listen intently, and then skeptically analyze your findings.
Published in Fraud Magazine

Here we'll examine several cases, taken from recovery audits, which at first glance didn't seem blatant but actually were fraud.
Published in Fraud Magazine

This column, part 3 of 4, proposes steps that an independent volunteer should take to monitor the cash disbursement function of small organizations. Fraud examiners can also use the columns in this series as a checklist for all types of organizations, regardless of size.
Published in Fraud Magazine

This article explains in detail what fraud examiners must learn about electronic evidence -- how it's stored and retrieved, what and how to ask for it, and the federal discovery rules that surround its admissibility.
Published in Fraud Magazine

Our investigation into the largest private embezzlement in Massachusetts history revealed that it was the trusted bookkeeper who had stolen directly from the company's cash accounts and deposited the money to several of her and her husband's personal bank accounts.
Published in Fraud Magazine

Don Rabon discusses how an effective interviewer must be able to not only understand the dynamics of an interviewee's immediate situation but gain insight into that person's life. Then, the interviewer must use the information to guide the interview. Understanding the dynamics and gaining insight are paramount to the interview's successful conclusion as a "communication event."
Published in Fraud Magazine

At age 35, "Roger Buckley" was ready to settle down to raise a family and get serious about financial planning for the future. His career was on track with a CPA firm. He made good money, drove a new car, lived in a nice home he had purchased, and had paid off the last of a student loan and other college-related debts. But he wanted more.
Published in Fraud Magazine

Fraud examiners who work for global corporations need to protect their employers by being savvy with the latest "under/over-invoicing" schemes used by money launderers and terrorist fundraisers. If they don't, the courts might find their businesses criminally liable.
Published in Fraud Magazine

The FAA has returned Mark Lund to his original duties as a safety inspector, and he continues to be one set of "eyes and ears of the airline passenger," as he says. For his courage and tenacity in protecting the public, the ACFE has awarded Lund its 2008 Cliff Robertson Sentinel Award.
Published in Fraud Magazine

Town Mark Ltd. of India retained this accountant and fraud examiner to document and streamline the information systems in preparation for ISO certification. But like the proverbial Pandora's Box, when he and others lifted the lid off the accounts, scores of errors and issues tumbled out.
Published in Fraud Magazine

Philanthropists and charities should protect themselves against fraud schemes to ensure that donated money is truly benefiting good causes. Here's information that all fraud examiners need.
Published in Fraud Magazine

In part 2 of this series, we discover the similarities between Ivar Kreuger's con games and the Unit Trust of India devastation.
Published in Fraud Magazine

This new column critically analyzes identity theft issues to keep readers current about this growing problem that has become a plague to consumers and businesses worldwide.
Published in Fraud Magazine

Compliance involves many different elements; knowing and following all the relevant laws, rules, and policies is but one part of the mix. A strong compliance program is absolutely necessary to protect an organization both internally and externally.
Published in Fraud Magazine

An FBI financial analyst worked on a "hit and run" bank account fraud that involved stolen identities, frustrating twists and turns, and just enough good luck to crack it.
Published in Fraud Magazine

In part 1 of this two-parter, we compare the accounting frauds of Ivar Kreuger with the Parmalat crimes.
Published in Fraud Magazine

Fraud examiners can show management that ethics promotion influences the decisions of consumers, prospective employees, and investors. The result: a bottom-line advantage in the marketplace.
Published in Fraud Magazine

Check fraud will occur in your organization - it's not a matter of if but when. So make sure your organization not only has excellent internal controls but a companion program to monitor those controls to deter and detect fraud.
Published in Fraud Magazine

This article review areas in which language, specifically incorrect spelling and punctuation, could be helpful tools in fraud examinations to identify a perpetrator from a group of possible suspects.
Published in Fraud Magazine

Not all psychopaths become fraudsters, but some fraudsters are psychopaths. A fraud examiner's job is to help deter fraud by discretely noticing those employees who might be exhibiting psychopathic tendencies.
Published in Fraud Magazine

Cynthia Cooper, CFE, CISA, CPA and corporate whistleblower, relays the incidents that led up to the infamous fraud she uncovered while working at WorldCom in this excerpt from her book, "Extraordinary Circumstances: The Journey of a Corporate Whistleblower."
Published in Fraud Magazine

Cynthia Cooper, corporate whistleblower, discusses her discovery of one of the largest frauds in corporate history while she was vice president of internal audit at WorldCom in Mississippi.
Published in Fraud Magazine

This article explores the linguistic, persuasive process found in Mark Antony's famous speech in Shakespeare's "Julius Caesar."
Published in Fraud Magazine

Employees of international humanitarian organizations are givers. Unfortunately, a few are also takers. Management, often in crisis mode, unwittingly enables the fraudsters by relaxing regulations to quickly deliver aid.
Published in Fraud Magazine

Criminals are riding the wave of technology just like the rest of us. The advent of the "convenient" technology of online banking actually now enables criminals to eliminate human interaction in transferring millions of dollars around the world.
Published in Fraud Magazine

Essentially three tools are available to the fraud examiner regardless of the nature of the fraud examination: interviewing, examining financial statesments and observing behavior.
Published in Fraud Magazine

There are clear benefits to the practice of continuous auditing. This article outlines six successful steps to a continuous auditing program.
Published in Fraud Magazine

In this product review, Philip C. Levi reports his findings on the hardware and software products that could aid fraud examiners in recovering hard drive data.
Published in Fraud Magazine

CFEs on legal teams can respectfully help inform judges about pre-trial motions, internal controls, discovery, chain of custody, and other matters.
Published in Fraud Magazine

We're all aware of the critically important components of background checks - convictions, driving histories, credit reports, references, drug tests - in profiling suspected fraudsters. But we should explore a component that's often misunderstood: civil litigation histories.
Published in Fraud Magazine

From real-time social virtual worlds to "massively multiplayer online games" (MMOGs), the Internet and advances in technology have enabled the creation of virtual communities where individuals can interact in cyberspace.
Published in Fraud Magazine

Pharmacists who commit fraud by diluting prescriptions pose a serious threat to patients. Integrating new controls to stop these criminals in their tracks might save lives.
Published in Fraud Magazine

Our expertise can also bring unexpected responsibilities: We might be called upon for advice when fraud rears its ugly head in the halls of academia.
Published in Fraud Magazine

As you're read many times in these pages, small businesses are typically more vulnerable to fraud because of a lack of segregation of duties, job rotation, and good internal controls. The risk and opportunities to commit fraud and embezzlement increase quite dramatically in small businesses.
Published in Fraud Magazine

Sen. George Mitchell knows that listening leads to valuable interviews and substantive negotiations - vital strengths for fraud examiners. He will share his techniques and his observations on the Middle East, Northern Ireland, the Olympics, and Major League Baseball in his keynote address at the 19th Annual ACFE Fraud Conference & Exhibition.
Published in Fraud Magazine

Fraud examiners who work for global corporations need to protect their employers by being savvy with the latest "under/over-invoicing" schemes used by money launderers and terrorist fundraisers. If they don't, the courts might find their businesses criminally liable.
Published in Fraud Magazine

Millions of "forgotten" dollars in payroll checks, utility deposits, bank accounts, money orders, unredeemed gift cards, and stock dividends are sitting in company coffers as unclaimed property. Make sure your organization follows all regulations, remits property to the state, and installs stringent internal controls.
Published in Fraud Magazine

This column provides some tips for multinational companies and their fraud examiners operating in China.
Published in Fraud Magazine

This column continues our discussion about cash larceny frauds. Here we'll discuss fraud in advance travel funds.
Published in Fraud Magazine

In Garcetti v. Ceballos, the U.S. Supreme Court was asked to determine the breadth of the First Amendment as it relates to speech that would be a routine part of a public employee's employment.
Published in Fraud Magazine

Fraud examination stands at the threshold of recognition in academia as a discipline worthy of degree status.
Published in Fraud Magazine

Some groups and businesses have no desire for their members or employees to complete fraud surveys, and fraud researchers should prepare themselves for possible litigation.
Published in Fraud Magazine

This column examines what examiners can do when interview subjects just do not want to talk - when their answers are short and not to the point."
Published in Fraud Magazine

This column examines the latest schemes used to steal data from debit card holders through merchants' and service providers' faulty cardholder data security systems.
Published in Fraud Magazine

This column features an interview with Bunny Greenhouse, recipient of the 2006 Cliff Robertson Sentinel Award.
Published in Fraud Magazine

Undisclosed agreements - side letters - between an insurance company and a reinsurer can hide egregious and fraudulent transactions from regulators, investors, and consumers. Here's how to find them.
Published in Fraud Magazine

Even if you're already using fuzzy matching and algorithms, here are some ways to utilize the classic methods and avoid some common pitfalls of accounts payable fraud.
Published in Fraud Magazine

A heightened awareness of fraud and fraud prevention is critical to an organization's success. Implementing the new and enhanced corporate governance requirements is just the beginning of a culture of compliance.
Published in Fraud Magazine

Unscrupulous cashiers often prepare false accounting records or alter these documents in cash receipting operations to conceal a misappropriation of funds from their employers. The next three columns present fraud cases that illustrate some of the common alterations of accounting records I've encountered in my practice.
Published in Fraud Magazine

Contract and procurement fraud can be especially enticing to those seeking to line their pockets at the expense of taxpayers and military personnel. Here are some lessons we can learn from the crimes of the "Dragon Lady."
Published in Fraud Magazine

Most of us are daunted by a complicated case's massive quantities of data. But Frank Hydoski, an internationally recognized forensics expert, says take a deep breath, formulate the basic question of the case, use technology wisely, and don't forget your intuition.
Published in Fraud Magazine

Digital evidence allows fraud examiners to "fill in the blanks," analyze competing theories, substantiate a hypothesis, or take the investigation in another direction. Realizing that digital evidence forensic examiners can serve an important role in a corporate investigation is the first step to improving the quality of the investigation and insuring that vital evidence isn't overlooked or left out of the process.
Published in Fraud Magazine

When this CFE was being ignored by his heating and cooling company he suspected more than poor customer service. Sure enough, the office manager was pilfering the firm. Here's the CFE's story of how he helped devise a plan to prevent subsequent employee fraud.
Published in Fraud Magazine

Here's the selected question for this issue: "I interviewed a pathological liar on several occasions who had bribed a government official. He exhibited no anxiety and actually seemed to enjoy the interviews. What techniques can you suggest using in this situation?
Published in Fraud Magazine

Here we describe the approaches and techniques we used to recover potential assets postmortem plus the lessons we learned.
Published in Fraud Magazine

Why do the Association of Certified Fraud Examiners and the American Institute of Certified Public Accountants work together? The main reason is to protect the public interest, according to AICPA President and CEO Barry C. Melancon, CPA. Melancon spoke to Fraud Magazine from his office in New York, N.Y.
Published in Fraud Magazine

Employers sometimes quake in their boots when they can't get detailed references for possible new hires. But fraud examiners can help their bosses glean information from references that can prevent disastrous hiring decisions and costly frauds.
Published in Fraud Magazine

Environmental fraud includes such schemes as falsification of data, marketing fraud, inflation of invoices, and fraudulent insurance claims. Here we'll describe the ways environmental fraud is perpetrated and what can be reasonably done to limit it.
Published in Fraud Magazine

If you're serious about stopping financial statement fraud, consider using effective journal entry controls and automated tests.
Published in Fraud Magazine

As we continue our discussion of cash larceny frauds, we begin to look at manual and computer cash register manipulations that cashiers use to misappropriate funds from the organization.
Published in Fraud Magazine

Higher-education fraud examination programs are finding novel partnerships as they train working and budding fraud examiners. For example, the U.S. Air Force has enlisted the services of Saint Xavier University and the Chicago Police Department to educate Air Force Office of Special Investigations (OSI) agents.
Published in Fraud Magazine

Gift cards are the perfect solutions for birthdays and holidays. Unfortunately, they're also becoming the perfect tool for money launderers and they're not interested in giving. Here are the facts for fraud examiners who need to know about the newest scam.
Published in Fraud Magazine

Disasters bring out the best and, of course, the worst in people. Catastrophic events are a beacon for opportunistic predators. Here are the latest schemes, conditions for fraud, and prevention and detection methods.
Published in Fraud Magazine

Preventing fraud is good business. Inspiring employees to follow ethical standards starts with the tone at the top in the executive suite. Learn the steps to prevent fraud in your workplace.
Published in Fraud Magazine

We can't fight an enemy that we don't know. The Institute for Fraud Prevention, directed by Dr. William K. Black, is striving to build a statistical foundation that will increase the global body of knowledge and improve anti-fraud efforts. Black spoke to Fraud Magazine from his office in Santa Clara shortly before he began his new position as associate professor of economics and law at the University of Missouri at Kansas City.
Published in Fraud Magazine

Almost all organizations use a petty cash fund to disburse funds to employees who make miscellaneous purchases on their behalf. This column demonstrates some of the ways that employees commit petty cash fund fraud.
Published in Fraud Magazine

Here we'll address the instable state of waiving the attorney-client privilege as it relates to corporations, and in particular, internal investigations.
Published in Fraud Magazine

Managers who use intimidation and fear to run their organizations prevent employees from being their best and encourage fraud, waste and abuse. Here's a framework for combating the tactics of these managers and deterring fraud.
Published in Fraud Magazine

Traveling to another part of the world to investigate global financial fraud can be challenging and daunting. Here are some things CFEs need to know before embarking on a white-collar crime investigation in the Middle East.
Published in Fraud Magazine

To record or not record? That's the controversial question many of my colleagues are asking about interviewing. It's the subject of a well-intended and spirited debate. But I think that recording interviews is a concept whose time has come.
Published in Fraud Magazine

In the last year, fraudsters have stolen data from thousands of debit cardholders through merchants' and service providers' faulty data security systems and then cleaned out victims' bank accounts. In part 2, we discuss industry initiatives, latest preventive technology, proposed legislation, and recommendations.
Published in Fraud Magazine

Private investigators and Certified Fraud Examiners have always used their unique skills to help each other in fraud examinations. However, many PIs now are realizing the value of adding CFE to their names.
Published in Fraud Magazine

Despite the FBI's renewed emphasis on battling terrorism since 9/11, it still ranks fighting public corruption and white-collar crime as top priorities. And the agency says it now uses a more efficient force in a triage system to tackle fraud of all stripes.
Published in Fraud Magazine

SOX and other regulatory standards are forcing audit committees to learn how to prevent fraud. Here's what they need to learn and how you can help them learn it so they will escape litigation, and most importantly, tackle fraud.
Published in Fraud Magazine

Extortion isn't new. But cyber criminals are taking advantage of high-tech developments to squeeze money out of individuals and organizations. Learn how to prevent a variety of threats and the steps to take if your entity is hit.
Published in Fraud Magazine

There's a definite methodology to data analysis in proactively detecting fraud. This column defines a process that presents a consistent way to minimize fraud risk.
Published in Fraud Magazine

Unscrupulous cashiers often alter manual cash receipt forms for customer payments to misappropriate funds from the entity. These manual cash receipt forms usually come in a book with three or more receipts to a page.
Published in Fraud Magazine

The latest evolution in digital forensics involves new forensic tools and methods for gathering evidence from live systems.
Published in Fraud Magazine

To the great satisfaction of CFEs, more businesses are assessing their risks. The changes increase the demand for anti-fraud skills but possibly the greatest joy is now finally finding a receptive audience.
Published in Fraud Magazine

As fraudsters become more proficient, CFEs must be able to use equally sophisticated fraud examination skills. Here's how you can stay on top of your game with criminal analytic techniques.
Published in Fraud Magazine

Byron Hollis, the national anti-fraud director for Blue Cross Blue Shield Association, spoke to Fraud Magazine from his office in Washington, D.C.
Published in Fraud Magazine

Business is constantly evolving; it's much more high tech then it was and we now operate in a global environment, and pieces of legislation have significant impact on insurance companies and the manner in which insurance investigations are conducted around the country.
Published in Fraud Magazine

Many new fraud examiners know that they need to use digital analysis in their cases but they also need some guidance through the maze. Here's some practical advice from your experienced colleagues.
Published in Fraud Magazine

Hurricane Katrina altered lives forever. Thousands of displaced survivors have lost their jobs as businesses struggle to survive. However, other opportunistic firms shamelessly have taken advantage of the disaster by altering their financial statements. Here's how auditors and fraud examiners can find this hidden crime.
Published in Fraud Magazine

This column provides companies with tools to understand how to establish document retention policies, as well as a sample policy for guidance.
Published in Fraud Magazine

This column will examine the tools, techniques, and emerging computer fraud trends that affect and aid the digital fraud examiner.
Published in Fraud Magazine

This column discusses educational and training guidelines for fraud and forensic accounting.
Published in Fraud Magazine

This column discusses how frauds and losses vary by age groups and other characteristics and what employers can do to prevent their companies from becoming victims of employee theft.
Published in Fraud Magazine

As well-off Baby Boomers age, the pool of elders vulnerable to fraud is growing. Marie F. Smith, president of AARP, encourages fraud examiners to "keep up the good fight" in protecting the elders in their communities.
Published in Fraud Magazine

The SEC voted to give smaller U.S. public companies an additional year to comply with the internal control reporting requirements of Sarbanes-Oxley Section 404.
Published in Fraud Magazine

This column discusses the latest handheld security measures that fraud examiners need to know.
Published in Fraud Magazine

On July 25, 2010, the ACFE Board of Regents voted to suspend Tom Conley.
Published in Fraud Magazine

This article discusses the finer points of fraud deterrence and detection for authorized maker schemes.
Published in Fraud Magazine

This column focuses on uses of “moot courts” and “mock trials” in anti-fraud courses and programs by reviewing examples at Stevenson University, Utica College and West Virginia University.
Published in Fraud Magazine

Fraud in the mining industry can be divided into four types: environmental, forestry, occupational and reserves or resources reporting.
Published in Fraud Magazine

Collecting documents in the U.S. might be relatively easy, but what about seizing assets or freezing accounts or securing evidence in the Far East or the U.K.? Then there are all those multijurisdictional disputes over conflicting claims.
Published in Fraud Magazine

Dr. Joseph T. Wells, CFE, CPA, the author of a colorful new autobiography, writes about his fables, follies and foibles in the wild ride of a life that has culminated in the establishment of a new profession and solid anti-fraud practices.
Published in Fraud Magazine

Roland Granger auctioned rare figurines, collected more than $300,000, did not deliver the goods and skipped town. Learn from John E. Ouellet, CFE, as he investigates the fraud and eventually discovers the evidence that gave Roland a prison sentence.
Published in Fraud Magazine

All organizations can use the free U.S. federal Excluded Parties List System during their procurement processes to find questionable vendors and reduce the risk of fraud.
Published in Fraud Magazine

Sometimes the promise of safety lures unsuspecting victims into more danger. Certified Fraud Examiners need to know about scareware, the latest evolution in the malware market.
Published in Fraud Magazine

The author relays an investigation he made, which he was able to prove through an extended records examination, fraud operational tests and, ultimately, a confession-seeking interview with a company manager.
Published in Fraud Magazine

Find out how to not become a victim of a telecommunications denial-of-service (TDoS) attack, a relatively new identity theft telephone scam.
Published in Fraud Magazine

Here are some tools that go further than the Fraud Triangle, which is inadequate for deterring, preventing and detecting fraud because pressure and rationalization cannot be observed and do not adequately explain every occurrence of fraud.
Published in Fraud Magazine

Corporations are deathly afraid of data breaches, but they need to proactively protect themselves and be frank with consumers when they are attacked. Here is help for counseling your organizations or clients.
Published in Fraud Magazine

Interview with 2011 Cressey Award recipient and securities regulation expert Prof. John C. Coffee.
Published in Fraud Magazine

The ACFE revisits San Diego, where it held its first annual conference, to offer anti-fraud education on a grander scale.
Published in Fraud Magazine

Zeus is a crimeware designed primarily to steal users' online banking credentials.
Published in Fraud Magazine

Can law enforcement officers search arrestees' cell phones without a warrant? The case poses some interesting questions for fraud examiners.
Published in Fraud Magazine

Explores the options available to prospective students who want to earn degrees in anti-fraud curricula
Published in Fraud Magazine

Every employee has the opportunity to commit travel fraud.
Published in Fraud Magazine

Mass-marketing fraud has gradually transformed in the past two decades into a "pervasive global criminal threat."
Published in Fraud Magazine

CFEs can show clients and employers how governance, risk management and compliance can help detect and prevent fraud.
Published in Fraud Magazine

Profile of Scott Cohen, CFE, CIA, CISA, director of internal audit for NATO Airlift Management Agency.
Published in Fraud Magazine

Companies struggle to determine exactly who owns the proactive and reactive responses to fraud within organizations. Here are some practical ways to determine “who owns fraud” and accelerate anti-fraud programs.
Published in Fraud Magazine

Has the accounting profession created a situation in which auditors’ ethical judgments are impaired by their professional obligations when they find fraud?
Published in Fraud Magazine

Regaining rights to stolen intellectual property can be a perpetual nightmare for companies operating in China and other countries with similar governmental and law enforcement structures.
Published in Fraud Magazine

Intellectual property theft will continue to happen. The faster the organization reacts, the less damage it might have.
Published in Fraud Magazine

If businesses don’t impose controls, policies and procedures over credit card processing and they don’t perform daily and monthly reconciliations, employees with access to the credit card systems could process fictitious or fraudulent refund or credit transactions to their personal credit cards.
Published in Fraud Magazine

This article explains what happens to your personal information (PI) after you give it to a company.
Published in Fraud Magazine

This column celebrates three advances in anti-fraud higher education: the NIJ’s model educational curriculum, ACFE resources for academics and budding fraud examiners, and current textbooks chock-full of anti-fraud principles and practices.
Published in Fraud Magazine

A new law is coming to the United Kingdom that might ultimately affect fraud-fighting communities around the globe, the new UK Bribery Act of 2010.
Published in Fraud Magazine

Admission-seeking interviews, in which a professional interviews a subject whose involvement in fraud or theft has been established, are the most critical and challenging tasks for a fraud examiner.
Published in Fraud Magazine

The FBI announced on Oct. 1, 2010, that it disrupted a large-scale, international, organized cyber-crime operation, served numerous search warrants and made scores of arrests.
Published in Fraud Magazine

Frank S. Perri offers that focusing too much on a crime’s violent or non-violent nature can lead to a punishment too severe – or not severe enough – for the crime committed.
Published in Fraud Magazine

This article explores the "Data Encryption Standard" and U.S. federal and state legislation in relation to data breach notifications and data security.
Published in Fraud Magazine

Overview of what went wrong with Satyam Computer Systems, one of the largest IT outsourcing companies in India.
Published in Fraud Magazine

Learn the vulnerabilities of smartphones and how to secure these "computers in the back pocket" from hackers who can easily steal proprietary and economic information from them, crippling your operations.
Published in Fraud Magazine

Here is how to protect your organizations and clients from government claim fraud and insider trading.
Published in Fraud Magazine

Part 3 of a series outlining travel fraud
Published in Fraud Magazine

One extremely challenging area in the higher-education classroom is teaching the digital aspects of fraud examination and forensic accounting, but it is imperative to do so.
Published in Fraud Magazine

Article outlining how procurement card abuse is perpetrated and how to detect and prevent it.
Published in Fraud Magazine

obits on Cliff Robertson and Frank Walker, CFE
Published in Fraud Magazine

Here are the techniques and technologies knowledgeable CFEs use to overcome the challenge of unintegrated email, websites, telephone and "snail mail" hotlines.
Published in Fraud Magazine

This article, from the “Financial Statement Fraud Casebook: Baking the Ledgers and Cooking the Books,” edited by Dr. Joseph T. Wells, CFE, CPA, helps small businesses learn lessons from this tale of misplaced trust, faulty internal controls and lack of segregation of duties.
Published in Fraud Magazine

The U.S. Securities and Exchange Commission and other regulatory agencies are hotly targeting audit committees and directors. Here are ways CFEs can help them fulfill their responsibilities and prevent fraud in their organizations.
Published in Fraud Magazine

Simple, second-generation (2G) mobile phones contained evidence like call histories, contact lists and short text messages. Now, 3G and 4G smartphones contain rich evidence such as emails, photos, electronic documents, and browser and instant messaging history.
Published in Fraud Magazine

There are many travel fraud schemes, and we’ll try to cover a variety of them in this and the next two columns.
Published in Fraud Magazine

Counterfeit drugs harm many unsuspecting victims. In some cases, they pay the ultimate price - their lives.
Published in Fraud Magazine

This article discusses how to debunk stereotypes and gives practical suggestions for constructing hotlines that work.
Published in Fraud Magazine

Organizations are increasingly storing data and applications on virtual servers around the world via “cloud computing” providers. The implications for fraud examinations could be enormous.
Published in Fraud Magazine

During the ACFE’s 22nd Annual Fraud Conference and Exhibition, the 2011 Cliff Robertson Sentinel Award went to William H. McMasters, the Boston publicist who, in 1920, helped take down the most notorious pyramid schemer of them all: Charles Ponzi.
Published in Fraud Magazine

The most successful fraud fighters use free social media outlets to network, expand their businesses, increase their contacts, learn new methods and stay current on the latest in anti-fraud news and resources. It is a brave new interactive world.
Published in Fraud Magazine

Dismantling a "web of lies" can strain even the most experienced investigators, but it is an important skill that new and budding fraud examiners should begin to master.
Published in Fraud Magazine

The U.S. Federal Trade Commission (FTC) has released its 2010 Consumer Sentinel Network (CSN) Data Book. Here is a summary and analysis of the data.
Published in Fraud Magazine

There is no doubt that advances in smartphones and other handheld devices are improving business communications and productivity, but failure to monitor the use of company-issued devices can cost employers tens of thousands of dollars.
Published in Fraud Magazine

This article explores human labor trafficking in military bases in Iraq and Afghanistan.
Published in Fraud Magazine

An Interview with Lanny Breuer, Assistant Attorney General for the U.S. Department of Justice Criminal Division.
Published in Fraud Magazine

This column discussing an actual authorized maker scheme investigation, including elements of the fraud, the red flags, some additional detection techniques and information about the interview.
Published in Fraud Magazine

The ACFE student chapters create anti-fraud communities on campuses that provide structure and robust skills development through training and education.
Published in Fraud Magazine

Dr. Joseph T. Wells, CFE, CPA, founder and Chairman of the ACFE, writes about a case early in his FBI career that taught him more than investigative techniques.
Published in Fraud Magazine

In part one, we defined scareware and its prevalence. In part two, we examine specific ways fraudsters lure victims, how to avoid infection, and legislation of this latest evolution of malware.
Published in Fraud Magazine

This column explores the red flags that we, as new and budding fraud examiners (and veterans), can teach our families, friends, coworkers, employees, managers and communities to look for when they engage in business and social dealings.
Published in Fraud Magazine

Faced with a possible workers' compensation fraud case? You and your casualty insurer might want to investigate the accused employee's medical provider, which could be complicit.
Published in Fraud Magazine

In the economic crime jungle, is one predator more rapacious than all others? If so, who is king of the fraud beasts?
Published in Fraud Magazine

Based on experiences and education from the CFE Exam Review Course
Published in Fraud Magazine

A look at Transparency International, a nonprofit founded by Dr. Peter Eigen, and how it is helping move anti-corruption efforts to the top of governmental and corporate agendas.
Published in Fraud Magazine

Poor internal controls resulted in fraud in excess of $500,000 for a newly acquired division of a publicly traded Fortune 500 Company.
Published in Fraud Magazine

How cryptocurrencies came about, theories of how they work, their misuse for money laundering and other illicit activities and their future.
Published in Fraud Magazine

An interview with Siobhan Fitzgerald, CFE, Chief investigator, Commonwealth of Massachusetts Unemployments Insurance Program Integrity Unit
Published in Fraud Magazine

Identity thieves are using stolen personally identifiable information to file victims’ tax returns and then receive their refunds.
Published in Fraud Magazine

The ACFE's first president discusses the beginnings of the organization.
Published in Fraud Magazine

Dr. Susan Shamrock wanted to give a non-approved, experimental allergy treatment to her suffering patients. Unfortunately, she overcharged for the drug to the tune of about a half a million dollars.
Published in Fraud Magazine

An outline of how ringleaders are committing financial aid fraud and what universities and the general public can do to combat it.
Published in Fraud Magazine

Student associate members share their ACFE Global Fraud Conference experiences.
Published in Fraud Magazine

Learn how universities, and other nonprofit organizations, can overcome entrenched ideologies to prevent and deter fraud and reputational damage.
Published in Fraud Magazine

In this ever-changing world, it’s a comfort to know that some things are universal and eternal. The morning cup of coffee. The annual FSU-Florida game. The Macy’s Thanksgiving Day Parade. And, in Fraudville, classic check fraud — arguably The Little Black Dress of financial crime.
Published in Fraud Magazine

The author outlines why conflict of interest can lead to corruption and how this information can help CFEs detect and prevent this type of fraud for their clients or organizations.
Published in Fraud Magazine

The policies and procedures for managing food service operations vary from state to state. Thus, fraud examiners in other U.S. states and in other countries should research the rules and regulations that apply to these activities for the guidance needed to investigate them.
Published in Fraud Magazine

Common interviewing pitfalls fraud examiners face, along with solutions.
Published in Fraud Magazine

Article outlining why the U.S. should be concerned about fraud worldwide, with a list of a few frauds that originated outside the U.S. but targeted Americans
Published in Fraud Magazine

Because of new anti-fraud legislation around the globe and reemphasis on FCPA enforcement, organizations have beefed up their compliance departments. CFEs, with their ingrained skill sets, can consider new job directions.
Published in Fraud Magazine

Interview with CFE Rose Karam
Published in Fraud Magazine

Overview and cautions about the amendment to the U.S. FCPA that allows for “facilitating payments.”
Published in Fraud Magazine

Case study adapted from the “Insurance Fraud Casebook: Paying a Premium for Crime,” about a gold seller
Published in Fraud Magazine

Outline of how fraudsters hit congregations and ways congregations can avoid becoming victims while still helping those in need.
Published in Fraud Magazine

Learn how you can use powerful data analytics tools to narrow your list of suspects for fraud examinations.
Published in Fraud Magazine

Disciplinary notices for John K. Freeman, CFE, and Darryl K. Swindells, Associate Member
Published in Fraud Magazine

Do's and Don'ts on how educators can give their students an assignment to create videos for learning more about fraud examination
Published in Fraud Magazine

Overview of Bitcoin, a digital money that could be used by criminals for money laundering
Published in Fraud Magazine

Profile of Joan Drabczyk, CFE.
Published in Fraud Magazine

Identity thieves are using stolen personally identifiable information to file victims’ tax returns and then receive their refunds. Here’s how they do it and ways to combat and prevent it.
Published in Fraud Magazine

Important rules when using and managing informants, whistleblowers and cooperating defendants to avoid sabotaging your cases.
Published in Fraud Magazine

Overview of Mexico's 2012 anti-money laundering law
Published in Fraud Magazine

An interview with former FBI director Louis Freeh.
Published in Fraud Magazine

Although residency fraud exists in many school jurisdictions throughout the U.S., it's a particularly serious problem in the District, which encompasses less than 70 square miles between Virginia and Maryland.
Published in Fraud Magazine

The ACFE Foundation has awarded $53,000 to college and university students through the Ritchie-Jennings Memorial Scholarship Program for the 2014-2015 school year. Each recipient also will receive a one-year ACFE student membership.
Published in Fraud Magazine

Dinesh Thakur was utterly flabbergasted when he discovered that his employer, Ranbaxy Laboratories, was falsifying data to receive approval of its generic drugs.
Published in Fraud Magazine

This column is a six-part series for educators and practitioners that will examine the importance of integrating digital forensics and data mining aspects of investigations, key technologies, methodologies and future applications and how to present them to budding fraud examiners.
Published in Fraud Magazine

As investors become more savvy they might be enticed to identify other alternative types of investments. A potential growing trend for SDIRA investments and opportunity for fraudsters might exist in the crowd-funding phenomenon.
Published in Fraud Magazine

Using mobile phones to make payments is nothing new. Mobile network operators began M-Pesa in Kenya in 2005. The service now has 17 million accounts.
Published in Fraud Magazine
The Fraud Triangle states that individuals are motivated to commit fraud when three elements come together — some kind of perceived pressure, some perceived opportunity and some way to rationalize the fraud as not being inconsistent with one's values.
Published in Fraud Magazine

According to the CSN, it received more than 79,089 fewer identity theft complaints in 2013 from 2012 (369,132 to 290,056) — a significant decrease.
Published in Fraud Magazine

The only attorney and investigator at the U.S. Federal Election Commission's Office of Inspector General (OIG), Cameron Thurber handles all legal affairs for the office — from negotiating agreements, to issues involving the inspector general's statutory independence and broad authority.
Published in Fraud Magazine

Criminals use shell companies to launder money, evade taxes and perpetuate all manner of fraud.
Published in Fraud Magazine

In part one of this article, we examined the variety-pack approach by one Trevor “Bam-Bam” Baker, who used the county recorder’s office as part of his playground to commit mortgage fraud and identity theft. In part two, we examine the more singular approach to fraud by one Rory Sykes.
Published in Fraud Magazine

In the economic crime jungle, is one predator more rapacious than all others?
Published in Fraud Magazine

Here I highlight this impact of fraud beyond the statistics in these six financial-crime victims’ stories from criminal prosecutions I assisted as a paralegal CFE.
Published in Fraud Magazine

Read every bank's account details including disclosed cost schedules before opening an account, as well as when new disclosures are sent out for existing accounts, so you’re not surprised should you ever require research.
Published in Fraud Magazine


The ability to identify micro expressions is definitely a valuable tool for any interviewer or fraud examiner. However, focusing on one slight behavior can cause an interviewer to overlook larger behavior clusters that betray a dishonest person’s message.
Published in Fraud Magazine

Here we address text mining (sometimes called text analytics) and discuss its characteristics and possible areas of application in fraud cases. We look at the components of text mining and how practitioners might utilize these methods to analyze large data sets to provide information that achieves the fraud examiner’s goals.
Published in Fraud Magazine

These three predictive analytical models can help you pinpoint fraud risk areas so you can make wise detection and deterrence decisions with available resources.
Published in Fraud Magazine

In part 2, we discuss yet even more creative ways ID thieves can rip you off, and analyze more statistics from the Federal Trade Commission’s (FTC) 2013 Consumer Sentinel Data Book.
Published in Fraud Magazine

Nancy Rich, CFE, is a top fraud expert at the Naval Criminal Investigative Service (NCIS) and recently received the Certified Fraud Examiner of the Year award at the 25th Annual ACFE Global Fraud Conference in San Antonio, Texas.
Published in Fraud Magazine

An understanding of the nonverbal behavior might prove to be more useful to the fraud examiner in determining deception.
Published in Fraud Magazine

When the ACFE began more than a quarter century ago, fraud was the word that “should not be spoken.” But speak it this group did.
Published in Fraud Magazine

Dr. Joseph T. Wells, CFE, CPA, founder and Chairman of the ACFE, offered suggestions for fraud examiners during the 25th Annual ACFE Global Fraud Conference, his last.
Published in Fraud Magazine

Fraud Magazine spoke with two veteran trial participants about the skills you need and roles you can play to support a litigation team.
Published in Fraud Magazine

According to the Centers for Disease Control and Prevention (CDC), U.S. nonmedical use of prescription painkillers results in more than $72.5 billion annually in direct healthcare costs.
Published in Fraud Magazine

University student Kevin Wendolowski discusses a growing trend of schemes designed to target a vulnerable and transient population: the homeless.
Published in Fraud Magazine

Cybercriminals take advantage of any opportunity to develop schemes to rob consumers of their resources. Even though the hackers have the upper hand, an educated community will help curb the damage.
Published in Fraud Magazine

In this interview, Senator Paul S. Sarbanes discusses the U.S. Sarbanes-Oxley Act and its impact on the deterence of fraud and the importance of Certified Fraud Examiners in the battle against white-collar crime.
Published in Fraud Magazine

This article provides tips for finding out if your company is inadvertently linked to terrorist organizations through a customer, supplier, or employee relationship.
Published in Fraud Magazine

Processing fictitious void transactions is a common type of cash register manipulation that cashiers use to misappropriate funds from their organizations. This article describes frauds committed on type 2 cash registers - registers that do permit voids to be recorded during normal transaction processing.
Published in Fraud Magazine

As business opportunities explode in Asia, it is crucial for U.S.-based businesses to have anti-fraud protections in place so as not to become victims of oversight mistakes and mismanagement resulting in FCPA violations. This article recommends ways to prevent fraud schemes in Asia and protect subsidiaries.
Published in Fraud Magazine

The non-payment of income tax can land fraudsters in jail. This article gives fraud examiners guidance on how income tax provisions can impact investigations and subsequent attempts for asset recovery.
Published in Fraud Magazine

This article describes a CFEs discovery of a fraud involving a popular university official with an aberrant psychological need to buy and preserve antiquities and send the doctored bills to the university, as well as the lessons learned throughout the investigation.
Published in Fraud Magazine

ACFE Founder and Chairman, Dr. Joseph T. Wells, questions the effectiveness of incarceration for white-collar crimes as a means of deterrence and explores alternative punishments for high-profile white-collar criminals.
Published in Fraud Magazine

This article details the prevalence and cost of pharmacy fraud and uses various case studies to demonstrate the importance of effective claims monitoring programs that incorporate data mining and analysis with desk, on-site, and investigative audit techniques to deter health-care fraud.
Published in Fraud Magazine

This study identifies a sub-group of white-collar criminals, classified as red-collar criminals, who will use physical violence, including murder, to avoid fraud detection and why CFEs should be part of the investigation process of these violent criminals.
Published in Fraud Magazine

Since the turn of the century, Japan has seen a spate of public company debacles similar to Enron and WorldCom. The government directed Professor Shinji Hatta and his ad-hoc committee of economic experts to devise an internal controls framework that would radically change the country's discrete enforcement system and emphasize fraud deterrence, raise reporting standards, and repair credibility.
Published in Fraud Magazine

Three bodies of auditors -- from the state, the corporation, and Arthur Andersen -- were unable to discover that high-ranking officials in a Middle Eastern oil tanker company had embezzled $100 million in 10 years. This article reviews the embezzlement case involving Kuwait Oil Tanker Company and how CFEs can assess what went wrong and determine red flags, and methods of prevention and detection in this high-dollar loss case.
Published in Fraud Magazine

This article delves into the prevalence and danger of phony diplomas produced by fraudulent degree mills and warns readers to avoid becoming a victim of these fraudulent institutions.
Published in Fraud Magazine

This column introduces two fraud-related jargon words and the fraud schemes that have fallen under their description.
Published in Fraud Magazine

Medical practices are particularly susceptible to internal fraud, especially embezzlement, because many physicians have zero education in accounting, finance, and business management. Here are three cases and four ways that fraudsters exploited poor management in small businesses plus practical methods that could have prevented the crimes.
Published in Fraud Magazine

Five years after SOX's passage, the scope of the whistle-blower protection section might still be uncertain. Fraud examiners need to know the latest discussions and litigation on the 90-day deadline, private companies responsibilities, and proving a case.
Published in Fraud Magazine

This article reviews the PCAOB's new Auditing Standard No. 5 which is intended to improve the efficiency and effectiveness of internal control audits while also cutting audit costs, especially for smaller public companies.
Published in Fraud Magazine

One of the most basic cash register frauds involves losses of revenue associated with missing Z tape numbers. This article instructs fraud examiners on how to calculate the amount of loss from missing cash register Z tapes and provides lessons from cash register manipulation schemes that cashiers use to misappropriate funds.
Published in Fraud Magazine

A summary of the February, 2006 amendments to the Investment Advisers Act of 1940 ("Hedge Fund Rule") that require more stringent hedge fund regulation and SEC compliance.
Published in Fraud Magazine

Practitioners provide insight into issues that arise during admission-seeking interviews, such as anxiety, interview recording, and interviewer's remorse.
Published in Fraud Magazine

Though the main Enron characters have received their prison sentences, there's no closure for corporate fraud. Sherron Watkins, Enron's sentinel, describes the debacle's details and warns that it could happen again.
Published in Fraud Magazine

As companies worldwide tighten their belts, employee pensions are being reduced or eliminated. But some employers are stepping over the line and pocketing pension funds. Learn how the Cayman Islands National Pensions Office caught one serious offender and gather some transferable tips for other cases.
Published in Fraud Magazine

Global firms are realizing that the anti-fraud profession, led by Certified Fraud Examiners, is an important component of risk measurement and avoidance. This article explores how recent risk-based management control systems are hastening the development of specialized anti-fraud agents.
Published in Fraud Magazine

Each year, employees embezzle millions of dollars in taxpayer monies from public entities. This article prescribes ways for fraud examiners to help find and recover some of these funds.
Published in Fraud Magazine

This article highlights how executives can help prevent fraud in their organizations by promoting a positive work environment and conveying the message of corporate responsibility and accountability to employees, contractors, and investors.
Published in Fraud Magazine

In any trade, a technician needs the right tools for a job. Knowledge built upon education, training and experience provides the needed skills. But without the right tools, a technician can only conceptualize the job at hand.
Published in Fraud Magazine

Online applications for ACFE committee positions opened Oct. 1 and will close Dec. 1.
Published in Fraud Magazine

The ACFE Nominations Committee has selected six candidates to compete for two positions on the 2015-2016 Board of Regents.
Published in Fraud Magazine

On June 15, the Board of Regents adopted the CFE Code of Professional Standards Interpretation and Guidance. This document is a resource for Certified Fraud Examiners to help them understand and remain in compliance with the CFE Code of Professional Standards.
Published in Fraud Magazine

ACFE member disciplinary notices
Published in Fraud Magazine

For the third year in a row, James D. Ratley, CFE, President and CEO of the ACFE, has been selected as One of the Top 100 Most Influential People.
Published in Fraud Magazine

The ACFE Board of Regents passed a resolution requiring at least one member of the Board of Regents at all times shall be a resident of a country outside the U.S.
Published in Fraud Magazine

Welcome to the first chapter of "The ACFE Cookbook," in which we'll examine recent cases and news involving alleged financial reporting fraud.
Published in Fraud Magazine

Organizations urgently need to improve their employees’ ability to report C-suite misbehavior without retribution. Here are ways that CFEs can help businesses do just that.
Published in Fraud Magazine

If you write your cover letter correctly, it will be another document in your portfolio that attests to your professional expertise and your brand. It summarizes at a high level — with a touch of marketing panache — the accomplishments and capabilities detailed on your résumé with only minimal explicit verbatim repetition.
Published in Fraud Magazine

After animal control inexplicably shoots and kills a dog even though it was wearing a collar with identification tags, many begin to scrutinize operations and an independent organization is called in to analyze expenditures.
Published in Fraud Magazine

Victims come from all walks of life, but their motives are few when they choose to engage with people they’ve never met and send money to them.
Published in Fraud Magazine

Augmented intelligence and data visualization are two technologies fraud examiners can use to make the analysis phase of a fraud examination more efficient.
Published in Fraud Magazine

Data breaches at Home Depot and Target, tightened security at gas pumps and a doctor's Medicare fraud leads to unnecessary chemotherapy.
Published in Fraud Magazine

James D. Ratley, CFE, President and CEO of the ACFE, discusses the importance of CFEs' responsibilities that go beyond just performing thorough fraud examinations.
Published in Fraud Magazine

Online romance is big business, but the percentage of fraudulent efforts is unknown. At press time, a Google search of "online love" returned more than 1.75 billion results; online dating, 14.8 million; online brides, 35 million; online husbands, 15 million; and online spouse, more than 61.5 million.
Published in Fraud Magazine

Darcy Fitzhenry, CFE, has a thirst for knowledge in the fight against fraud. As an investigative analyst at the Royal Canadian Mounted Police (RCMP) and as a director of the ACFE Calgary chapter, Fitzhenry uses his background in financial services to aid his investigations.
Published in Fraud Magazine

A team of fraud fighters uses three different analytical tools for measuring accruals (amounts that aren’t cash transactions) in a company and finds that some managers had added fraudulent loans to boost the numbers and keep the shareholders happy.
Published in Fraud Magazine

Fraud examiners can take precautions to lessen possibilities that potential fraudsters might become angry or aggressive during interviews. Here are steps fraud examiners can take to be safer when conducting examinations domestically and abroad.
Published in Fraud Magazine

In this column, Chloe Pickering, a recent graduate from the U.K., describes her story — first as a victim and then as an aspiring fraud examiner.
Published in Fraud Magazine

Fraud examiners who succeed have passion, integrity and grit. Regardless of the stage of your career, all of us need to be reminded why we decided to become fraud examiners or investigators.
Published in Fraud Magazine

On Jan. 7, SC Magazine reported that IntelCrawler, a cybercrime research company in Los Angeles, detected a new type of malware, "XXXX.apk," which has infected close to 24,000 smartphones.
Published in Fraud Magazine

Top management at Quoteron Inc. thought it was increasing efficiency when, at the urging of its procurement officer, Ken, it gave its hardware supplier, Donlane Supplies, an “umbrella contract.” However, Ken secretly owned Donlane and reaped the profits of an illegal exclusive deal. Here’s how to detect and deter fraud in the procurement process.
Published in Fraud Magazine

There are legitimate environments in which the measured use of managed "earnings" can benefit you — swap out earnings for expectations in your everyday professional lives.
Published in Fraud Magazine

This article helps companies determine the likelihood and significance of certain frauds using a qualitative approach enhanced by a quantitative analysis.
Published in Fraud Magazine

This column summarizes key points about cash larceny frauds and provides fraud examiners with a checklist to use during cash receipt testing.
Published in Fraud Magazine

This article adresses the Fifth Amendment’s impact upon incriminating statements made by employees – both public and private.
Published in Fraud Magazine

This column highlights key characteristics of Generation Y individuals and the difficulty that these characteristics pose when conducting admission-seeking interviews.
Published in Fraud Magazine

Ros Wright, chairman of the UK Fraud Advisory Panel, discusses a variety of fraud-related issues including the work of the Fraud Advisory Panel, current fraud initiatives in the UK, the challenges that fraud imposes on the global economy, and the similarities between fraud schemes in the U.S. and U.K.
Published in Fraud Magazine

Throughout the world, companies are falling victim to the Black Market Peso Exchange (BMPE). This article explains how the BMPE works and how an organization can prevent unknowingly accepting BMPE illicit funds.
Published in Fraud Magazine

This article explores the essential elements for building and maintaining a successful program to battle pharmacy fraud, specific procedures a fraud examiner can use to develop a pharmacy fraud case, and legislative actions that might unintentionally hinder these efforts.
Published in Fraud Magazine

Women/minority-owned businesses (W/MBEs) can be easy targets for fraudsters who exploit diversity policies. This article describes ways to deter and detect schemes that defraud taxpayers, corporations, and true W/MBEs.
Published in Fraud Magazine

This article guides CFEs on how to detect the unique behavioral traits of psychopathic, red-collar criminals in order to conduct effective admission-seeking interviews.
Published in Fraud Magazine

Lawrence Fairbanks was a respected, well-liked university official. But he had a bad habit of buying artistic treasures and antiquities and charging them to his employer. Here's how the university's audit department investigated his crimes and shut down the "Fairbanks Collection."
Published in Fraud Magazine

Perry Minnis describes how Alcoa manages ethics and compliance among 123,000 employees in 43 countries so that infractions don't grow into irregularities that could morph into threatening frauds.
Published in Fraud Magazine

This column provides lessons on how financial expert witnesses can help win cases by artfully and simply communicating the facts through written reports and oral testimonies.
Published in Fraud Magazine

Processing fictitious voided transactions is a type of cash register manipulation that cashiers use to misappropriate funds from their organizations. This column provides tips for preventing and detecting fictitious void transactions on type 1 cash registers.
Published in Fraud Magazine

On Dec. 12, 2006, Deputy Attorney General Paul McNulty issued a new guidance for federal prosecutors. This column reviews the McNulty Memorandum guidelines for attorney-client and work product privilege waivers and how they relate to a company's cooperation with authorities in a federal investigation.
Published in Fraud Magazine

This article delves into the epidemic of "botnets," a type of Internet crime that secretly links together computers worldwide to steal corporate and personal data and drain money from online bank accounts and stock brokerages.
Published in Fraud Magazine

This column prescribes a way to prevent potential fraudsters from siphoning corporate funds from company databases by installing "triggers": simple, low-cost, non-intrusive programs that will detect any suspicious financial movement.
Published in Fraud Magazine

Pressed by heightened fraud awareness, the global business world is defining the differences between the fraud examiner and internal roles. Learn the distinctions and the necessary core knowledge of the anti-fraud professional.
Published in Fraud Magazine

This interview with William Sanjour, ACFE’s 2007 Sentinel Award recipient, provides an account of how he spent more than three decades confronting deception and inequities in the Environmental Protection Agency.
Published in Fraud Magazine

This column stresses the importance of monitoring the internal control structure in small organizations and recommends the use of volunteers to do the monitoring.
Published in Fraud Magazine

According to the Federal Trade Commission, pretexting is the practice of obtaining personal information under false pretenses. This article reviews the Hewlett-Packard pretexting case, describes its circumstances and results, reviews legislation, and discusses if it’s permissible to use the onerous method to obtain information in fraud examinations.
Published in Fraud Magazine

In this column, guest author and ACFE Higher Education Committee member, Mark Morgan, CFE, CPA, explores the advantages of expanding anti-fraud education through what he calls “anti-fraud storytelling” in all business courses.
Published in Fraud Magazine

This article features some of the highlights, guest speakers and exhibitors at the 18th Annual ACFE Fraud Conference & Exhibition in Orlando, Fla., the perfect place to learn the latest in cutting-edge, anti-fraud information from some of the best practitioners in the business.
Published in Fraud Magazine

Pre-schools, which often receive state dollars, can be breeding grounds for fraud and abuse. This column provides practical ways to deter these conditions that can be applicable to any situation.
Published in Fraud Magazine

This column stresses the importance for fraud examiners to understand legal privileges that apply in investigations so that they can play an essential role in protecting a client’s privileges and preserve the confidentiality of certain investigation materials.
Published in Fraud Magazine

In this column, Christopher Shell, an internal auditor, describes his experiences in the loss prevention area. He shows that inventory misappropriation in the retail industry is a difficult and challenging fraud environment to investigate and recommends loss prevention as an excellent way for college students to gain real-world experience dealing with fraud prevention and detection.
Published in Fraud Magazine

Supply-chain fraud can affect every level of an organization. Learn how an inventory transfer approach can detect this rampant, inter-departmental fraud and how the traditional role of fraud examiners must shift to keep up with technology.
Published in Fraud Magazine

Explore some of the latest anti-money laundering issues, pending legislation and the effects on the anti-fraud community within two perennial targets: the mortgage and health-care industries.
Published in Fraud Magazine

Expanding industry of "lease auditing" needs scrutiny.
Published in Fraud Magazine

Interview with fraudster Frances Ellen.
Published in Fraud Magazine

Several large financial service companies recognized bogus “gains on sale” from bloated estimates of future collections upon which those gains were based. These were portents of impending economic meltdown and fraud in the late 1990s, early 2000s.
Published in Fraud Magazine

The Institute for Fraud Prevention (IFP) is supporting research to find the root causes of fraud and offering tools for deterrence and prevention to businesses and government.
Published in Fraud Magazine

Will credit card laws help reduce ID theft for young consumers?
Published in Fraud Magazine

Two notable Ponzi cases – the Bernard L. Madoff Investment Securities scheme and the alleged Stanford Financial Group fraud – show the true underbelly of corruption in the recent economic meltdown.
Published in Fraud Magazine

When Washoe County Water Resources implemented new business software, a trusted employee of nearly 20 years overrode the controls and embezzled more than $2.2 million in just one year. Here’s how his scheme was uncovered.
Published in Fraud Magazine

ACFE Chairman and Founder Joseph T. Wells, CFE, CPA, received a Doctorate Honoris Causa from York College of The City University of New York.
Published in Fraud Magazine

Here are guidelines governing the use of words describing criminal acts and ways to modify expressions to avoid defamation cases.
Published in Fraud Magazine

CFEs need to know all facts of the Foreign Corrupt Practices Act as they work with compliance officers to offer comprehensive training to all employees.
Published in Fraud Magazine

Can professionals accused of wrongdoing – even when acting professionally and ethically – effectively use apologies to help protect their credibility and reputations from negligence accusations and costly litigation?
Published in Fraud Magazine

Ways ATF instructors help teach college students practical fraud examination and forensic principles.
Published in Fraud Magazine

Here’s practical information CFEs can use to discern frauds that are being used to fund terrorist activities.
Published in Fraud Magazine

This column outlines a false billing scheme case study involving the Washington state Liquor Control Board.
Published in Fraud Magazine

Interview with Irving Picard, court-appointed trustee for Bernard L. Madoff Investment Securities.
Published in Fraud Magazine

Learn about a medical clinic’s mistakes in this “from the deposit” cash theft scheme.
Published in Fraud Magazine

Article on the 21st Annual ACFE Fraud Conference and Exhibition.
Published in Fraud Magazine

Interview with ACFE Sentinel Award winner Amy Stroupe, CFE.
Published in Fraud Magazine

Cross-referencing documents with the U.S. Social Security Administration's Death Master File might be the key to fighting the perpetrators of death fraud.
Published in Fraud Magazine

Metadata can provide the forensic examiner with context about an electronic document.
Published in Fraud Magazine

How can we help students develop the critical knowledge, skills, and abilities they’ll need to succeed in an anti-fraud career?
Published in Fraud Magazine

This column discusses the investigation, lessons learned, and recommendations to prevent future occurrences of false billing schemes.
Published in Fraud Magazine

The “2010 Report to the Nations on Occupational Fraud and Abuse” has gone global.
Published in Fraud Magazine

This article outlines how fraudsters are jumping on the green energy bandwagon.
Published in Fraud Magazine

An outline of the FTC Consumer Sentinel Network Data Book's 2009 figures
Published in Fraud Magazine

Anyone can report wrongdoing, but the level of protection an employee will receive will differ depending on whether they’re public or private, to whom they report, the manner in which they report, the type of wrongdoing they report, and the law under which they report.
Published in Fraud Magazine

How to distinguish between invoicing fraud and incompetence.
Published in Fraud Magazine

Global money laundering has been a problem for those navigating international waters with ill-gotten gains since the piracy days of Edward Teach (“Blackbeard”) and John Rachham (“Calico Jack”).
Published in Fraud Magazine

Interview with Russell Smith, Ph.D., principal criminologist and manager of the Global, Economic and Electronic Crime Program at the Australian Institute of Criminology.
Published in Fraud Magazine

Hands-on company boards must now manage risks, measure performances, and install fraud prevention and detection tools to protect their shareholders and companies’ reputations.
Published in Fraud Magazine

Fraudsters won’t get away with their crimes if you employ the powerful proof-of-cash method to draw them out and reel them in.
Published in Fraud Magazine

Top executives can drive their companies close to bankruptcy because it’s often easy for them to circumvent controls.
Published in Fraud Magazine

On Feb. 23, the ACFE Board of Regents permanently expelled Martha Faul of Arcadia, Fla., and Tracy Newkirk of Stanwood, Wash.
Published in Fraud Magazine

The Financial Abuse Specialist Team is a collaboration of concerned community members – teaming with the district attorney, law enforcement, and social agencies – to address the growing problem of financial abuse of elders.
Published in Fraud Magazine

CFEs can deter fraud resulting from irresponsible, anonymous Internet postings, but they can only do it with assistance from their in-house or retained legal counsel.
Published in Fraud Magazine

Outline on how banking Trojans work.
Published in Fraud Magazine

Fraud Triangle Analytics, introduced last year in Fraud Magazine, is becoming a valuable tool to revolutionize email and instant message searches.
Published in Fraud Magazine

Skilled fraud examiners should make it a habit to stop, look, and listen for red flags when communicating with staff.
Published in Fraud Magazine

The Securities and Exchange Commission failed to uncover Bernard Madoff’s $65 billion Ponzi scheme because of some major agency deficiencies. That was the conclusion of H. David Kotz, SEC’s inspector general, after a thorough investigation. Kotz, who has made 69 recommendations to the SEC for improvement, says he has “a burning desire to expose the truth.”
Published in Fraud Magazine

Here are tips and ideas for companies who need to be careful about the circular transaction environment prevalent in Japan’s unique marketplace.
Published in Fraud Magazine

The anti-fraud movement is lacking a private, grassroots advocacy movement that would be the voice for fraud victims.
Published in Fraud Magazine

In part two of this series, financial service industry CFEs, attorneys, and former law enforcement officers offer inside tips on preparing accurate, complete Suspicious Activity Reports.
Published in Fraud Magazine

Outline of mobile banking phishing scams.
Published in Fraud Magazine

CFEs should follow these search strategies when examining electronic evidence.
Published in Fraud Magazine

Article outlining judicial review of the Supreme Court in three fraud-related cases: One case deals with the constitutionality of a provision in the Sarbanes-Oxley Act of 2002 (SOX), and two address the constitutionality of the honest services statute.
Published in Fraud Magazine

Applying Treadway Committee concepts to a flawed internal control system explains how one of the greatest corporate scams ever took place.
Published in Fraud Magazine

Profile of Isabel Mercedes Cumming, J.D., CFE, chief of Prince George’s County’s Economic Crimes Unit.
Published in Fraud Magazine

Renewed emphasis on the FCPA and invigorated judicial efforts in Latin America are deterring corruption and other forms of fraud.
Published in Fraud Magazine

This article explores how law enforcement officers follow Suspicious Activity Report (SAR) leads, apply traditional investigative elbow grease and use technology to apprehend and prosecute perpetrators.
Published in Fraud Magazine

Bernard Madoff whistle-blower Harry Markopolos, CFE, CFA, desribes how he began his investigation into Madoff.
Published in Fraud Magazine

Though there’s no definitive research yet linking workplace bullying and fraud, here’s a discussion on a possible correlation.
Published in Fraud Magazine

On Jan. 21, the Financial Audit Department (FAD) – Dubai Government announced a partnership with the ACFE, to provide expert fraud training and certification for FAD employees.
Published in Fraud Magazine

In part one, we looked at the growing incidence of family members who defraud their aging relatives and the similarities of these miscreants to traditional occupational fraudsters. In part two, we’ll look at the pattern behavior of these fraudsters by outlining various criminal cases charged by one prosecuting authority’s specialized team.
Published in Fraud Magazine

This underreporting of financial crimes against the elderly makes it difficult to get reliable statistics. It’s possible that the aggregated financial impact on elderly victims — and society in general — will get much worse before a comprehensive national research and intervention response is entrenched.
Published in Fraud Magazine

Say what you will about short sellers, but they’ve played an interesting role over the years when it comes to uncovering financial statement fraud. And if recent news is any indication, this role appears to be expanding and becoming more controversial than ever.
Published in Fraud Magazine

To illustrate C-suite nonfeasance, this article cites recent examples from the real estate sector. As the biggest cog in America’s economic machinery, it generates 13 percent of U.S. GDP. Perhaps unsurprisingly, money laundering in the real estate industry (MLRE) is vast and, some say, under-regulated.
Published in Fraud Magazine

For several years, the Port of New York and New Jersey — whose history evokes memories of organized crime, racketeering and corruption — also served as the hub for a $7 million market manipulation scheme, more commonly known as a "pump and dump."
Published in Fraud Magazine

A pillar in the fraud examination profession provides tips, which can help ensure that at the end of a long career you'll know you did your best in fighting fraud.
Published in Fraud Magazine

Occupational fraud is serious business. In addition to the risk of financial loss, reputational damage and losing customers’ trust, corporate victims of occupational fraud can also face increased regulation plus civil and even criminal penalties.
Published in Fraud Magazine

Academic research still dominates this discipline, though more recently, businesses in general and marketing operations, in particular, have been very successful in using SNA in targeting customers, focusing advertising and motivating buyers.
Published in Fraud Magazine

We set high expectations of integrity and honesty for law enforcement and court personnel. We trust them to behave at a higher standard. When they violate that trust, the ramifications are greater than usual fraud.
Published in Fraud Magazine

I normally don’t extoll the high points of a person’s résumé, but I’m emphasizing that you should listen to this man. He knows what he’s talking about.
Published in Fraud Magazine

We must be able to identify the red flags of trafficking and be vigilant and swift to report our suspicions. Human trafficking can happen before your eyes, and you might not realize it. Often the victims are unable or unwilling (for fear of reprisal) to go to authorities to seek help, and some don’t consider themselves to be victims, which can hinder prosecutions.
Published in Fraud Magazine

Urs Steiner, CFE, dons a kilt when he plays the Great Highland bagpipe with his band, but then he suits up daily to fight fraud as the vice president and investigator at Credit Suisse, AG in Zurich, Switzerland. Steiner’s dream of becoming a police officer led to an extensive career as a criminal investigator and the work he does now at the large Swiss bank.
Published in Fraud Magazine

Organizational leaders, fraud examiners and auditors might not fully appreciate the social nature of many fraudulent acts. In fact, many of us think of a fraud perpetrator as a cold, calculating individual — a “bad seed” — who opportunistically takes advantage of internal control weaknesses. Research that we’ve conducted lends new insights into the social side of fraud.
Published in Fraud Magazine

Dan Jackson was living the good life: a well-paying job, beautiful wife, kids in private school, expensive clothes, Rolex watches. However, the façade hid a man who defrauded his company of $1.5 million. In part 1 of this two-parter, we learn Dan’s background and his collusion with Jake, a sleazy external consultant.
Published in Fraud Magazine

Are you looking for that next job opportunity? The U.S. federal government has scores of employment possibilities for fraud examiners on USAJobs.gov. In this and the next two columns, I discuss the three position classification categories that most often contain fraud examination responsibilities and opportunities
Published in Fraud Magazine

The IC3 recommends that possible victims of the Green Dot MoneyPak Customer Support scam should file a complaint with the IC3 at www.ic3.gov and be as “descriptive as possible, including prepaid card/account numbers affected and contact information of support ‘representatives.’ ”
Published in Fraud Magazine

Automated Clearing House and wire transfers are increasing but so is fraud in these transactions. All a fraudster needs is an account number and a bank-routing number. Here are ways to prevent and fight these lucrative crimes.
Published in Fraud Magazine

When a case takes an unanticipated turn, these fraud examiners regroup and refocus their examination to discover evidence that eventually helped obtain a felony conviction on a corrupt city official.
Published in Fraud Magazine

The embezzlers’ fraud wheelhouse contains a classic tool for “misappropriating funds” from their employers: the ghost employee. Simply put, “The term ghost employee refers to someone on the payroll who does not actually work for the victim company.” (2015 Fraud Examiners Manual, 1.456) Ghost employees are miracles of physics: they might or might not exist and companies don’t employ them, yet they draw regular paychecks.
Published in Fraud Magazine

As CFEs, it’s our duty to help diminish the fears that impede the fight against fraud. When our organizations acknowledge those fears we can effectively use resources to combat them. I’ve seen companies that use analytics tools and proactive monitoring turn idle threats into reality.
Published in Fraud Magazine

As a Certified Fraud Examiner (CFE) and paralegal for a financial crime prosecution unit, I’ve testified in six criminal trials, and they were always educational. In fact, being cross-examined by a defense attorney in a criminal trial is one of the best ways to learn how to become a better CFE.
Published in Fraud Magazine

This issue’s cookbook is devoted to two recent and interesting cases involving revenue manipulation — the most popular method of cooking the books. But I serve up several menu options in these cases. Which would you prefer today: round-tripping, channel stuffing or perhaps an order of side deals? Let’s get cooking.
Published in Fraud Magazine

The Jindal School Center for Internal Auditing Excellence at the University of Texas at Dallas has honored ACFE President and CEO James D. Ratley, CFE, by creating an endowed scholarship in his name. The center will present the award annually, in an amount up to $2,500, to an outstanding UT Dallas accounting student studying fraud examination.
Published in Fraud Magazine

The 26th Annual ACFE Global Fraud Conference will be the largest anti-fraud event in the world — connecting you with experts, resources and information to help you stay competitive in this rapidly evolving industry. Join us June 14-19 in Baltimore and experience for yourself why this is the most important yearly event for anti-fraud professionals.
Published in Fraud Magazine

In part 2, we examine more botnet and malware case histories, analyze data breach causal factors and related statistics, and discuss ways to avoid becoming a victim of these nefarious schemes.
Published in Fraud Magazine

Not all résumés get an initial screening by hiring managers or recruiters. Many human resources (HR) departments at large organizations have been forced to devote increasing resources to employment law, Affordable Care Act implementation and employee benefit packages. Therefore, many HR departments are turning to résumé- and job application-screening software.
Published in Fraud Magazine

Condo homeowners’ environments can be incubators of fraud because volunteers comprise the boards that oversee the collection of large sums of money, and they might not properly manage these funds for the benefit of clueless residents.
Published in Fraud Magazine

In this column, we discuss “big data,” a common term that refers to both the volume of data and the technology that’s necessary to effectively analyze and utilize that data. We address the nature and character of big data, its challenges, approaches to working in a big-data environment, many of the options available to professionals and the role of academics in educating young fraud examiners in the new technologies.
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

The global financial crisis revealed bad policies, practices and pitfalls along with outright criminality in global banks. Far-reaching internal and external investigations are finding culprits who unlawfully manipulated the London Interbank Offering Rate (Libor) — one of the cornerstones of market balance.
Published in Fraud Magazine

Alan Maran Goncalves, CFE, has a passion for travel and a free spirit. His independence and career focus took him from his home country of Brazil to the U.S. to continue his profession in business, including experience in accounting, finance, audit, compliance and fraud examinations.
Published in Fraud Magazine

The new U.S. assistant attorney general for the DOJ’s Criminal Division, of course, encourages companies that conduct business in the U.S. to prevent and deter fraud and comply with all regulations. But if they discover possible crimes within their walls, then total cooperation will greatly ease their treatment.
Published in Fraud Magazine

Shell companies have no physical presence or actual business operations, but are paper corporations that have only one purpose: to facilitate one or more transactions and then eventually dissolve. We explore how corrupt politicians and civil servants misuse shell entities to steal taxpayer funds.
Published in Fraud Magazine

Cybercriminals take advantage of any opportunity to develop schemes to trick consumers and rob them of their resources. Even though they have the upper hand, an educated community will help curb the damage.
Published in Fraud Magazine

The initial evidence pointed toward an open-and-shut embezzlement case. But the author describes the assumptions that almost led to an innocent employee’s downfall, and he details his fraud examination that revealed the truth.
Published in Fraud Magazine

Fraud examiners can help their organizations measure the economic effects of fraud and thereby aid management to more accurately assess and adjust prevention and detection efforts.
Published in Fraud Magazine

Cyberbreaches and internal information theft are often regarded as information technology (IT) problems. However, most information loss isn’t a pure-play IT issue, which might be part of data security problems. Should entities remove handling of cyberbreaches and information protection from IT?
Published in Fraud Magazine

Over the last few issues I’ve explained numerous financial reporting schemes using cases that might be obscure to some. However, in this column, I revisit three cases that captured the headlines when their stories first broke. Since then, their sagas have been relegated to the back pages, but they continue to have interesting developments.
Published in Fraud Magazine

Published in Fraud Magazine

On May 25, Memorial Day, a torrential downpour hit Austin, bringing with it tornado warnings and hail. News coverage provided photos and videos of the city that showed rising water levels and dangerous rescues.
Published in Fraud Magazine

The ACFE developed the Fraud Prevention Check-Up several years ago as an affordable, easy-to-use way to identify gaps in your organization’s fraud prevention processes. But this “evergreen” publication will never lose its value. By identifying risks early, you have a chance to fix problems before losing money and becoming a victim of fraud.
Published in Fraud Magazine

The ACFE Foundation has awarded $58,000 to college and university students through the Ritchie-Jennings Memorial Scholarship Program for the 2015-2016 school year. Each recipient also will receive a one-year ACFE student membership.
Published in Fraud Magazine
Some suggest that fraud examiners could use computerized “avatars” to collect basic information. Here we look at potential technological advancements and the implications of avatars in the fraud-fighting profession. You decide.
Published in Fraud Magazine

I once worked as a civil investigator for a check-cashing and payroll company in the private sector until I decided to be an officer and fraud examiner in a police department. Here are seven reasons I made the switch.
Published in Fraud Magazine

On June 27, 2014, Christie Talbot appeared before Judge John C. Rowley in Tompkins County Court and pleaded guilty to second degree grand larceny. Talbot stood accused of stealing more than $365,000 from the Society of Personality and Social Psychology Inc. (SPSP), a private, not-for-profit organization, at which she worked as an administrative assistant.
Published in Fraud Magazine

Fraud examiners have used the iconic Fraud Triangle, containing Dr. Donald Cressey’s principles, for decades. However, the author contends that Cressey didn’t necessarily develop his theories to explain behavior of those who don’t have financial needs and are predisposed to committing fraud even before organizations hire them.
Published in Fraud Magazine

Your front-line employees might be an untapped source of knowledge. Think about the people your organization hired. Did they all come from the same schools? The same former employer? The same life experience? Probably not. With a variety of backgrounds and experiences, these employees might be able to provide you with thoughts on how to identify customers’ possible fraudulent activity.
Published in Fraud Magazine

FIFA red carded in federal indictment, hackers target American credit cards and new sentencing guidelines for white-collar criminals.
Published in Fraud Magazine

Through the years, I’ve met scores of whistleblowers — the ACFE likes to call them sentinels — and all of them have suffered. Many have lost their jobs, relationships and health. But I don’t think I’ve known of a sentinel who’s paid the cost of integrity more than James Holzrichter.
Published in Fraud Magazine

Fraudsters, terrorists and miscreants of all sorts can now travel more easily across borders because they no longer have to pay big bucks to the shady passport maker down the alley. They can quickly find quality, affordable fake passports at several websites on the “dark web.”
Published in Fraud Magazine

Houses of worship are havens from fraud, right? Wrong. The author describes how church workers’ erroneous thinking leaves them particularly vulnerable to fraud and what congregations can do to deter and prevent fraudsters’ attacks.
Published in Fraud Magazine

Scott Swanson, CFE, always saw himself involved with the military, in the intelligence community or in law enforcement. He achieved this goal immediately following college when he became involved in financial services and economic espionage protection. Swanson has been an advisor to the U.S. intelligence and special operations community.
Published in Fraud Magazine

Based on the tremendous increase in data breaches and related compromised records in 2014 plus the soaring incidents of income tax refund fraud, it’s no surprise that identity theft is also growing. The U.S. Federal Trade Commission reports a sizable increase in complaints.
Published in Fraud Magazine

When James Holzrichter reported some management issues to his supervisor, he had no idea that he would later discover widespread alleged fraud at Northrop. He'd lose his job, health and 17 years of his life. But he'd retain his integrity and his family's love.
Published in Fraud Magazine

Before you begin your résumé and draft cover letters, you need to do a self-assessment and ask yourself four questions. Your honest answers will help you move into the next phase of your job hunt. (These questions are also important for new CFEs and those looking to change careers.)
Published in Fraud Magazine

In this scam, fraudsters send emails to college students to recruit them for supposed payroll and/or human resource positions with fictitious companies. The emails ask the students to provide their bank account credentials under the guise of setting up direct deposit arrangements. The fraudsters then add the students’ bank accounts to victim employees’ direct deposit information to redirect the victims’ payroll deposits to the students’ accounts.
Published in Fraud Magazine

If you haven’t read the story of Daniel Fernandes Rojo Filho before now, I recommend you do so. It’s a salutary and shocking tale … and a striking warning for those in charge of due diligence at banks.
Published in Fraud Magazine

Integrating the ACFE’s statistical findings into an auditing strategy can help auditors better detect fraud. The objective is to try to actively create a climate that encourages individuals to give tips during an ongoing audit.
Published in Fraud Magazine

The Supreme Court’s decision not to review a recent insider trading case produces a cloudy precedent for white-collar prosecutions.
Published in Fraud Magazine

The largest anti-fraud conference in the world provides professionals with practical tools plus some serendipitous networking.
Published in Fraud Magazine

In each of the cases I’ve covered in recent columns, the only fraud involved cooking the books. But in other cases, fraudsters commit financial statement fraud as the secondary act to conceal the primary frauds.
Published in Fraud Magazine

Longtime ACFE member, Robert Cameron “Cam” McFadyen, CFE, 66, passed away April 30 after a short illness.
Published in Fraud Magazine

The members of the Board of Regents aren’t novices. With 137 years of accumulated experience, they’ve climbed most of the limbs and branches of the Fraud Tree. Yet they’re still excited about solving puzzling cases: discovering evidence, interviewing subjects, presenting results and testifying.
Published in Fraud Magazine

Paul Laneuville and Carl Walters are true examples of a phenomenon I call the “bullybezzler.” Both cost their organizations hundreds of thousands of dollars. And the employees they bullied eventually brought them both down.
Published in Fraud Magazine

You’ve learned how to stop fraudsters from hacking your smartphone. But do you know how to determine whether each mobile recording you make is legal?
Published in Fraud Magazine

Money mules are a key element in cybercrime because they serve as conduits between victim and criminal members of illegal operations.
Published in Fraud Magazine

While collaboration might seem like the obvious answer to solving complex — and even simple — problems, the world of fraud detection and prevention has been slow to embrace it in a critical area. We’ve underestimated the importance of research to assist fraud fighters in staying ahead of the curve.
Published in Fraud Magazine

The latest fraud headlines.
Published in Fraud Magazine

It was wonderful to see so many of you at the 26th Annual ACFE Global Fraud Conference. At the opening general session, I told attendees that ACFE founder and Chairman Joseph T. Wells, CFE, CPA, and I recently were discussing the future of fraud and what lies ahead for the profession.
Published in Fraud Magazine

ISIL, or ISIS, needs lots of currency, of course, to expand its terrorist reach into the Middle East. And it’s not above committing fraud to raise funds.
Published in Fraud Magazine

Natasha Novikov, 32, CFE, CPA/CFF, a forensic accountant at the FBI, received the Certified Fraud Examiner of the Year award in June at the 26th Annual ACFE Global Fraud Conference in Baltimore, Maryland.
Published in Fraud Magazine

In part 2, we’ll analyze more stats from the Federal Trade Commission’s 2014 Sentinel Data Book and report on additional general identity theft complaint categories that reflect how ID fraudsters rip-off individuals.
Published in Fraud Magazine

Unprepared U.S.-based companies can find themselves in hot water if they don’t prevent personnel or customers from diverting their products to embargoed countries.
Published in Fraud Magazine

As of March 2015, 2,905 businesses were on the exclusions list. These companies — and any other legitimate businesses that use their services — can’t submit bills for services to a U.S. federal government health program (such as Medicare or Medicaid, among others) for payment.
Published in Fraud Magazine

The case of “Judy” is an important study in the application of the Fraud Triangle and several other fraud examination tenets. We know the Fraud Triangle by its three sides: pressure, opportunity and rationalization.
Published in Fraud Magazine

One day Katie Calvin received an email informing her that she hadn’t paid a recent toll fee and she had to pay immediately. She couldn’t remember ever driving through a tollgate without paying. Good thing she didn’t download the invoice and become the latest victim of this phishing scheme.
Published in Fraud Magazine

In many ways, Edith Chase fit one of the stereotypes of the traditional embezzler. She was a middle-aged woman in a mid-level accounting/bookkeeping job at a smallish business — wallpaper to most of the rest of the company after almost three decades of stolid, reliable work.
Published in Fraud Magazine

Chip technology, commonly called EMV (Europay, MasterCard and Visa), is being touted as one fix to this rising card-fraud epidemic. Chip cards use algorithms that are far more difficult than magnetic stripe cards to copy or breach, which can prevent criminals from stealing credit card data.
Published in Fraud Magazine

International Fraud Awareness Week, Nov. 15-21, is an especially important time for students and faculty to get involved in preventing fraud in higher education.
Published in Fraud Magazine

As we approach Thanksgiving, I give thanks to whistleblowers. I risk drifting into cliché-speak here, but their actions personify courage. When fraud confronts them, they decide not to look the other way but instead risk their jobs, families and health “For Choosing Truth Over Self” — the motto inscribed on the ACFE’s Cliff Robertson Sentinel Award.
Published in Fraud Magazine

The importance of the “tone at the top” in deterring fraud is a concept that most of us have read about in articles and studies. However, seeing tone at the top in practice and how it impacts an organization positively or negatively is the best way to understand exactly how this link works.
Published in Fraud Magazine

The ACFE Nominations Committee has selected nine candidates to compete for three positions on the 2016-2017 Board of Regents.
Published in Fraud Magazine

FAD has committed to sending at least 150 of its staff to the 2016 ACFE Middle East Conference and is promoting it to other government agencies, corporations and special guests from additional countries in the region.
Published in Fraud Magazine

Fraud Magazine recently interviewed His Excellency Abdulla Mohammed Rashid Al Huraiz, Deputy Director General, Financial Audit Department, Government of Dubai, about FAD’s anti-fraud efforts and its cooperation with the ACFE.
Published in Fraud Magazine

To address the lack of available benchmarking information for internal fraud investigation departments, the ACFE collected data about our members’ internal investigations teams.
Published in Fraud Magazine

Organizations’ procurement of goods and services — through electronic bidding processes — can save money and increase efficiency. But it can also add risks plus inflict major fraud damage when staffs betray employers’ trust. Here’s how to overcome trust breaches and fight fraud in digital and human networks.
Published in Fraud Magazine

Conveying a favorable impression — what I informally call the “likeability factor” — increases the chances that candidates will achieve their preferred outcomes, which could be second interviews or job offers. Who goes into a job interview unwilling to promote their accomplishments, expertise and character?
Published in Fraud Magazine

CFEs possess many of the skills that companies need on their boards of directors: skepticism and curiosity, analytical thinking, reading comprehension, interviewing and communication.
Published in Fraud Magazine

What do minor league baseball, candy and cupcakes have in common? For Cindy Durtschi, Ph.D., an associate professor at DePaul University, they make great topics for instructional cases in fraud examination.
Published in Fraud Magazine

The trust that manages the Bill and Melinda Gates foundation sues Petrobras for fraud, a former Harvard employee computer lab manager steals $80,000 from the school to buy Legos and Volkswagen admits to rigging pollution tests on millions of diesel vehicles.
Published in Fraud Magazine

The author of our cover article, W. Steve Albrecht, Ph.D., CFE, CPA, CIA, writes that in 2013, more than 10 boards of directors asked him to join them, and during the past 12 years, he’s been on eight boards for public and private companies.
Published in Fraud Magazine

BlackPOS disguises itself as an installed service of a known anti-virus vendor software to avoid being detected and, consequently, deleted in the infected POS system.
Published in Fraud Magazine

The ongoing migration of refugees from areas dominated by ISIS into Europe is the largest mass movement of people since World War II, according to a European Union official. United Nations figures show that 50 million people have been driven from their homes by violence in the Middle East and Africa, with Syria the hardest hit.
Published in Fraud Magazine

Thomas Boegballe, CFE, a Liverpool F.C. fan, always wanted to be a professional soccer player growing up. But as he grew older, and as he says, “more realistic,” he realized he wanted to work with people and numbers.
Published in Fraud Magazine

Tom Shaw, CFE, CAMS, a seasoned pro, knows that fraud examiners only see victories when they’ve diligently planned for every possible fraud quirk. Here’s help for incorporating metrics-driven processes into your anti-fraud efforts.
Published in Fraud Magazine

Healdton’s treasured treasurer took advantage of an oblivious city council and city manager and defrauded the city of at least $80,000 using three different methods. Her story shows how small nonprofits are particularly susceptible to fraudsters.
Published in Fraud Magazine

From the numerous complaints the IC3 received from May 2012 through March 2015, it determined that criminals were setting up fake government services websites (such as the SSA and the Internal Revenue Service) to trick potential victims into revealing their personally identifiable information (PII) and pay fraudulent fees.
Published in Fraud Magazine

The author, after working with top management for more than 20 years in corporate America, has devised the 'Executive' Fraud Triangle, which helps describes the conditions that can propel privileged and selfish senior executives to commit fraud.
Published in Fraud Magazine

Change is inevitable, but it exposes companies to significant financial, occupational and compliance fraud risks — as Waste Management Inc. showed.
Published in Fraud Magazine

Eugene Kaspersky, a world-renowned cybersecurity expert and successful entrepreneur, spoke with attendees March 23 at the ACFE Conference in London about the cyber landscape today and what needs to be done to thwart cybercriminals' attacks.
Published in Fraud Magazine

One of the more fascinating aspects of financial reporting fraud cases is the element of intent. Unlike asset misappropriations and most corruption cases, fraudulent intent isn’t always as obvious when the charges involve financial statement manipulation.
Published in Fraud Magazine

Last year, the ACFE challenged its local chapters to raise funds for the ACFE Foundation’s Ritchie-Jennings Memorial Scholarship program. And, as usual, many chapters heartily responded. The 2014 ACFE Scholarship Fundraising Challenge wrapped up in December with more than $20,000 raised by local chapters to support future anti-fraud professionals.
Published in Fraud Magazine

You’ve heard of the big-news breaches: Target, Home Depot, JPMorgan Chase, Michaels. Large and small organizations allow porous online systems to jeopardize their customers and diminish profits. Find out how cybercriminals use infectious malware to infiltrate web browsers and steal identities and personally identifiable information.
Published in Fraud Magazine

Your job interview is your audition. When your game is on, you focus on what the hiring manager wants and needs, and you own the audition — the interview — and the space in which you find yourself, rather than feel sucked into it like a semi-helpless victim.
Published in Fraud Magazine

Using a classic phishing scheme, fraudsters are taking control of company email accounts to initiate wire transfers from unsuspecting employees. We show how crooks lure victims into their traps and how you can protect your clients.
Published in Fraud Magazine

ACFE training is unlike any other. If you want to be a fraud examiner, there’s no better place to get your education, training and credential. However, the training applies to both sides. In my own private practice, there’s plenty of room and good reason to work defense cases. In fact, the work is similar no matter what side you’re working on.
Published in Fraud Magazine

In part 2, the evidence mounts against Dan Jackson as the author’s fraud examination begins. Jackson remains obstinate through his indictment and prosecution.
Published in Fraud Magazine

In this column we share our view of some new technologies that have the most promise of providing major value to future fraud examiners. We also discuss the significant role colleges and universities must play in educating professional fraud examiners of the future.
Published in Fraud Magazine

Fraud perpetrators often use a variety of excuses to alleviate the culpability of their mental states because they know they can’t be convicted unless prosecutors can prove their criminal acts were accompanied by a guilty state of mind known as mens rea.
Published in Fraud Magazine

Investigating fraud in crowdfunding could be a new frontier for CFEs. Because, as always, easy money begets fraud.
Published in Fraud Magazine

The OECD report contains a wealth of statistical information worthy of close analysis. Here I include the most relevant statistics for fraud fighters and focus on conclusions and next steps.
Published in Fraud Magazine

Investigative journalist Brian Krebs, the author of the blog, KrebsOnSecurity.com, has exposed — at personal risk — data breaches at Target, Home Depot, P.F. Chang’s and many others. His reporting has abbreviated cybercrime schemes that have saved thousands for consumers and helped rescue identities. And he’s just getting started.
Published in Fraud Magazine

Renee Hale, CFE, knew from the moment she arrived at the Federal Law Enforcement Training Center in Georgia that she’d started on a perfect path to her dream job. Hale says of her time at the center, “Even on my worst day, it was the best job ever.”
Published in Fraud Magazine

Here we’ll cover the broadest series of jobs within the government that encompass the management and program analysis — job series 0343.
Published in Fraud Magazine

Don't pay that purchase order or make that money wire before reading this column. The author outlines the latest frauds — fake purchase orders to steal merchandise and innumerous money-wiring scams — and how you can prevent them.
Published in Fraud Magazine

Learn how to bait a trap to catch insurance offenders before they claim more money. The interview skills you'll acquire will help in all other types of fraud examinations.
Published in Fraud Magazine

Here we'll present deductive and holistic data analysis techniques to find the uncommon frauds that are less predictable to the fraudster.
Published in Fraud Magazine

While Internet fraudsters will never stop finding new ways to use cyberspace to victimize, fraud examiners now have methods to prevent their crimes rather than just trying to investigate after the fact.
Published in Fraud Magazine

Messod Daniel Beneish, Ph.D., Indiana University accounting professor, has devised analysis ratios for identifying possible financial statement frauds.
Published in Fraud Magazine

In the January/February 2005 issue, we began a discussion about the primary method I've seen where the highest-risk employee skims revenue from the organization using a check-for-cash substitution scheme. This column continues the discussion on employees stealing checks from the organization.
Published in Fraud Magazine

All types of organizations are susceptible to fraud - even colleges and universities.
Published in Fraud Magazine

This bird's-eye view of five corporate crime studies in the last 50 years may help predict the future of fraud-fighting efforts in the post-SOX era.
Published in Fraud Magazine

Fraudsters ignore country boundaries. "Fraud is becoming an international crime," says Joseph T. Wells, CFE, CPA, founder and Chairman of the ACFE.
Published in Fraud Magazine

Devising and conducting an internal fraud risk assessment may be a daunting task, but every fraud examiner should have the essentials to get the job done. Here are some steps you can take to prevent and detect fraud.
Published in Fraud Magazine

This column is the first in a new series designed to keep our members updated on all things Sarbanes-Oxley.
Published in Fraud Magazine

They want to steal your name, your credit card numbers, your reputation, your money, and your life. Betsy Broder and her FTC team have one mission: to keep you from being another identity theft statistic.
Published in Fraud Magazine

The spreadsheet is one of the most brilliant software tools for almost any industry including accounting and finance. However, because everyone is so comfortable with them, spreadsheets can be excellent tools for committing fraud.
Published in Fraud Magazine

In the past three columns, we've discussed many ways fraud perpetrators steal currency and checks from organizations before accountability for the transactions has been recorded in the accounting system. This column concludes this brief coverage of skimming cash payments from customers.
Published in Fraud Magazine

Global Internet fraud is increasing so quickly and wildly that no one can devise a reliable rate of growth. But all fraud examiners know that they need to recognize the major types of Internet fraud and adhere to the "best practices" of protection.
Published in Fraud Magazine

Managers, knowingly or unwittingly, may contribute to employees' frauds by rationalizing questionable situations.
Published in Fraud Magazine

Fraud examiners are aided by numerous laws and regulations plus many detection methods when there are suspicions that Medicaid fraud is afoot.
Published in Fraud Magazine

In many countries, new home construction and remodeling is booming. But so is home improvement and construction fraud. Fraud examiners can help stanch the flow of money into the pockets of fraudulent contractors by learning the latest tricks that plague unsuspecting homeowners.
Published in Fraud Magazine

Here are some ways to help convince your C-level executives - the CEO, COO, and the CRO - that managing fraud across your entire entity can result in a positive rate of investment in the long haul.
Published in Fraud Magazine

Does your office "clean" the computer hard drives before the systems are recycled? How effective is the process they use?
Published in Fraud Magazine

John the controller tried to buy a little time with a check kiting scheme to keep two businesses alive. Unfortunately for him, the time he bought was 10 months in prison.
Published in Fraud Magazine

As the 2005 year-end approaches, fraud examiners need to remember the impact of revenue mistatements.
Published in Fraud Magazine

In the wake of Arthur Andersen's demise after its involvement in the Enron case, and the subsequent U.S. Supreme Court ruling, we've all learned something about retaining (or not retaining) business documents.
Published in Fraud Magazine

Robert Wardle, director of the UK's Serious Fraud Office, tackles not only the toughest cases but lengthy trials and mounds of evidence. A veteran of the SFO, he juggles it with aplomb.
Published in Fraud Magazine

Your employees' "protected health information" - names and addresses, social security numbers, payment histories, diagnoses - can be stolen or misused. Learn how your entity can protect its employees and add to the bottom line.
Published in Fraud Magazine

Churches and religious groups are at a greater risk for financial misconduct because of the nature of their missions and management structures. Here's how fraud examiners can help deter theft and the loss of a congregation's trust.
Published in Fraud Magazine

Here are the technological twists fraud examiners are now up against: crafty phishing e-mails, new online classified scams; and risk of intellectual property loss from MP3 players, music downloading programs, and (yes) lava lamps.
Published in Fraud Magazine

Criminals will always have to clean dirty money but fraud examiners need to be aware of the common ways many launderers infiltrate financial institutions worldwide.
Published in Fraud Magazine

Fraud examiners need only basic computer skills and the help of systems administrators to mine for gold and find vital evidence for fraud examinations.
Published in Fraud Magazine

With this column, we begin a journey through the many facets of cash receipting and types of fraud that occur in every organization. Our first step involves skimming: removing funds prior to recording accountable transactions in the accounting system.
Published in Fraud Magazine

While many professionals in the United States scramble to keep up with accounting changes mandated by the Sarbanes-Oxley Act of 2002 and the Statement on Auditing Standards No. 99 "Consideration of Fraud in Financial Statements," our international counterparts face similar challenges.
Published in Fraud Magazine

In a perfect world, employees wouldn't steal from their employers. However, this is far from a perfect world. Here are some basics in beginning an internal investigation.
Published in Fraud Magazine

Eliot Spitzer targets fraud on Wall Street, in the mutual-fund business, and in the insurance industry. He says he wants the marketplace to work more efficiently, honestly, and fairly. Spitzer's methods offer lessons for fraud examiners.
Published in Fraud Magazine

The new documentation required under sections 302 and 404 of the Sarbanes-Oxley Act helps fraud examiners by quickening the creation of deterrence programs and simplifying investigations.
Published in Fraud Magazine

With a little cash register magic, restaurant employees and owners can slyly skim receipts and decrease taxes. Here's how to catch them at their game.
Published in Fraud Magazine

Discrepancies between the dates on three bank loans and the resulting mortgages turned a routine audit into a laborious search for possible fraud. The result may have staved off collusion between a loan officer and the mortgagee.
Published in Fraud Magazine

Just like Alice in her Wonderland, the acquiring company didn't anticipate the tricks of the Mad Hatter and March Hare. But eventually the purchasers discovered the nightmare of an $18-million fraud in the company they had bought.
Published in Fraud Magazine

Despite the heavy use of credit cards and online payments, and the redoubled efforts of the FBI and police anti-fraud units, check fraud continues to increase. CFEs can benefit from reviewing the rudiments of check fraud detection and prevention, and the new twists.
Published in Fraud Magazine

Dr. David J. Graham, a scientist at the U.S. Food and Drug Administration for more than 20 years, says the agency could have prevented 60,000 deaths from the arthritis drug Vioxx. But Graham, the recipient of the ACFE's Cliff Robertson Sentinel Award, says the problems at the FDA go beyond the problems of one drug.
Published in Fraud Magazine

Year after year, fraud examiners will lament, "we need to implement technology this year to proactively detect fraud," but then never do take action. You're neither lazy nor ineffective. Rather, you're being knocked off-track by the silent killers of technology: trying to do everything at once, not building effective business cases, and not making it part of the fabric of your working lives.
Published in Fraud Magazine

Fraud examiners, when looking backwards to the early stages of an investigation, report common patterns. Like tornado watches, these signals don't indicate the funnel clouds were sighted but that they might develop because of optimal conditions.
Published in Fraud Magazine

With this column, we begin a new series about cash larceny - on-book frauds in which employees steal the organization's revenue after accountability for the funds has been recorded in the accounting records.
Published in Fraud Magazine

In January 2005, the Supreme Court in United States v. Booker and United States v. Fanfan clarified Blakely by holding that the Federal Sentencing Guidelines are no longer mandatory but merely advisory.
Published in Fraud Magazine

Law enforcement, regulatory authorities, and consumer organizations have alerted the public to Internet fraud schemes over the past few years. Here are 17 types of schemes that have most victimized Internet users worldwide.
Published in Fraud Magazine

Art fraud and forgeries often are ignored in the world of white-collar crime. Learn how to detect and prevent fraud in this multibillion-dollar industry.
Published in Fraud Magazine

Learn how to use the Print Screen function on your personal computer keyboard to save evidence and prepare it for court presentation.
Published in Fraud Magazine

Spouses may try to hide funds during divorce proceedings in several ingenious ways to improve the share of the ultimate financial settlement. Here are some of the methods and how to catch the offending parties.
Published in Fraud Magazine

With the multiplicity of dialects, less structured legal systems, destroyed or nonexistent documentation, and differences in cultural expectations, fraud examiners should equip themselves with specific tools when conducting investigations in developing countries.
Published in Fraud Magazine

Scattergraphing can help fraud examiners to effectively sift through an extensive amount of data to identify audit exceptions.
Published in Fraud Magazine

Irwin Cotler, minister of justice and attorney general of Canada, has a passion for protecting the rights of others - including those citizens hurt by corporate fraud and securities violations.
Published in Fraud Magazine

Here we'll discuss some of the methods employees use to skim funds by stealing customer payments made in cash.
Published in Fraud Magazine

This project manager for a public construction agency had earned its trust but had stolen its dollars – thousands of them. This article looks at real life kickbacks, bid-rigging and larceny.
Published in Fraud Magazine

The USA PATRIOT Act, signed into law after 9/11, strongly targets suspected money laundering activities and creates new requirements for financial institutions.
Published in Fraud Magazine

U.S. insider trading is relatively easy to commit but extremely difficult to prove. Here is a primer for fraud examiners explaining the problem, how to tell if a trade is illegal, and what can be done to detect and prevent this popular crime.
Published in Fraud Magazine

This U.S. federal prosecutor will help you review the courtroom requirements for presenting evidence and testimony, attorney-client privilege and how it affects fraud examiners, the work product doctrine, and other necessary law topics.
Published in Fraud Magazine

All fraud examiners must know about this impending assault on both the global health care sector and the public’s financial reserves.
Published in Fraud Magazine

Summary of the 7th Annual European Fraud Conference Oct. 28-29, 2003 in London. Attendees at the 7th Annual European Fraud Conference not only had many opportunities to network but they had a choice of 12 breakout sessions within three tracks - Current Issues, High Tech, and Practical Fraud Techniques.
Published in Fraud Magazine

Fraud examiners can help tackle the problem by exposing credit card fraudsters' methods and by promoting training in the cards industry, government, and law enforcement.
Published in Fraud Magazine

Investment swindles and con schemes have been around for centuries, but the Internet allows perpetrators to reach a wider audience at little cost.
Published in Fraud Magazine

In this article, we are going to examine not just the content within a document but also the physical evidence found on the document. We will also be talking about several types of latent evidence - evidence we cannot see without some sort of technology.
Published in Fraud Magazine

Special Investigation Units, in the private and public sectors, can fight fraud more effectively by developing professional relationships with prosecutors, marketing capabilities, and keeping current on fraud examination issues and techniques.
Published in Fraud Magazine

Preview of hte 14th Annual Fraud Conference & Exhibition, Aug. 3-8 2003 in Chicago.
Published in Fraud Magazine

Both the savvy and naïve are eligible prey to new business con schemes. Consumer education is the greatest weapon in the war against the pervasive scammers.
Published in Fraud Magazine

Modern document examiners not only determine authorship and authenticity but they use the latest technology to detect changes, resurrect evidence, recover entire documents, and analyze DNA.
Published in Fraud Magazine

The Sarbanes-Oxley Act, spawned from huge corporate collapses, will not make fraud disappear. But its strong language and stiff penalties could deter some executives tempted to stray.
Published in Fraud Magazine

Lies told in a heartbeat can have permanent and irreversible consequences. One instance of rationalized dishonesty can lead to a pattern of fraud.
Published in Fraud Magazine

The respected actor is honored for standing up to the duplicitous Hollywood establishment and lends his name to an award that will honor other whistle-blowers "For Choosing Truth Over Self."
Published in Fraud Magazine

An effective embezzlement investigation requires the interplay of several diverse elements. There must be a balance between the rights and responsibilities of both the employer and the employee. This article provides 10 actions to avoid even more revenue loss during the fraud examination and litigation.
Published in Fraud Magazine

Financial statement fraud usually involves overstating assets, revenues and profits and understating liabilities, expenses and losses. However, the overall objective of the manipulation may sometimes require the opposite action.
Published in Fraud Magazine

Entities throughout the world are devising models to detect and prevent fraud in the workplace. This CFE from the United Kingdom constructs a composite from three countries that can be adapted to any public or private entity.
Published in Fraud Magazine

Global money laundering has ballooned - some estimates range as high as $500 billion a year worldwide. But overt and covert methods can trace the funds, find the evidence, and make the fraudsters pay.
Published in Fraud Magazine

Established auditing approaches cannot adequately detect financial statement fraud. The ACFE proposes a Model Organizational Fraud Deterrence Program as an alternate, more effective strategy for both auditors and investors.
Published in Fraud Magazine

While occupational fraud takes various forms, the result is always the same: The numbers generated by fraud cannot hold up to the unfailing logic of the accounting equation. This article touts the benefits and gives an overview of data analysis in fraud investigations.
Published in Fraud Magazine

Excerpted from the NEW Fraud Examiners Manual, 2003 U.S. Edition ©2003 Association of Certified Fraud Examiners, Austin, Texas
Published in Fraud Magazine

This article describes insurance fraud perpetrated under the guise of mold claims.
Published in Fraud Magazine

Because nonprofit financial reporting fraud often looks quite different than it does in the for-profit world so should the methods for finding it.
Published in Fraud Magazine

Responsibility for handling employee complaints is new to audit committees. Committee members shouldn't rely on existing structures that direct complaints to management. Fraud examiners can help audit committees comply with the intent and spirit of section 301 of the U.S. Sarbanes-Oxley Act.
Published in Fraud Magazine

Brian Lamkin, chief of the FBI's Financial Crimes Section, directs his team of agents and analysts to tackle fraud while working toward additional recognition for CFEs.
Published in Fraud Magazine

Fraud examiners often have to use time-honored techniques to parse the words of alleged fraudsters during an interrogation. But sometimes the absence of a suspect's deception can help make the case.
Published in Fraud Magazine

Fraud, waste, abuse, and mismanagement of government contract and contract funds will never be eliminated. But frequent, modest proactive audits and reviews that focus on fraud indicators will help identify and prevent misuse before the funds are expended.
Published in Fraud Magazine

Outcome-oriented fraud auditing - looking at a situation as a whole rather than its individual parts - will help you think like a fraudster and find deeply embedded crimes.
Published in Fraud Magazine

The recent death of a well-known criminal left a CFE remembering how the crook committed some of the most convoluted frauds in the 20th century and how they easily could have been prevented.
Published in Fraud Magazine

A vendor can be an entity’s best colleague or worst nemesis. Keep the relationship pleasant and successful by conducting vendor audits.
Published in Fraud Magazine

The common-size diagram – a basic tool for financial statement analysis and fraud detection – is a simple, visual way to order, draw, and discuss a balance sheet. This article discusses the uses of the common-size diagram and demonstrates how to draw one.
Published in Fraud Magazine

Analysis of statements has played an important part in criminal investigations. However, new insights have shown that deceivers can now be identified by how they say things and not just by what they say.
Published in Fraud Magazine

Another Implement for the Fraud Examiner’s Toolbox SAS 99 not only requires auditors to be reasonably sure that financial statements are free of material misstatements, whether caused by error or fraud, but it gives them focused and clarified guidance on meeting their responsibilities to uncover fraud.
Published in Fraud Magazine

Marta Andreasen, the European Commission's chief accounting officer, awaits her professional fate after declaring the EC's budget was "massively open to fraud" and endures suspension because of her honesty.
Published in Fraud Magazine

Parmalat, “a milk-and-cookies conglomerate" seemed at first glance to be above suspicion. But the firm began to implode when the Italian regulatory commission began its investigation, a Parmalat bank account supposedly holding 3.9 billion Euros was found to be fictitious, and Parmalat fired its two chief auditing companies. This one will last for years.
Published in Fraud Magazine

It's a volatile combination: high volume of cash-out refinancing loans, declining performance of commercial properties, and relentless production pressures on internal loan officers. The resulting concoction often is fraud. Economic conditions are prompting desperate fraudulent property owners to use several tricks to obtain commercial mortgage loans. Following are more schemes.
Published in Fraud Magazine

In the next several years, as baby boomers begin retiring, employment experts see a problem: many openings and few qualified applicants. This is such a significant challenge for the U.S. federal government that the Department of Homeland Security, with the assistance of the Office of Personnel Management, is changing the way this newest federal agency hires people. There's an answer to this perplexing problem -- interns!
Published in Fraud Magazine

Examining identity theft suspects requires systematic, methodical techniques designed to yield evidence for possible prosecution.
Published in Fraud Magazine

An interview with Lynn Turner, CPA, the former chief accountant for the U.S. Securities and Exchange Commission (SEC)
Published in Fraud Magazine

Most frauds are found through tips and most tips come through hotlines. Here are some suggestions if you're beginning a hotline for the first time.
Published in Fraud Magazine

Executives at a large housing management firm stole thousands of federal dollars from low-income, rural rental housing projects. An extensive fraud examination found more wrongdoing than initially detected.
Published in Fraud Magazine

There may not be a more opportune time for a fraud examiner to press for a full-fledged fraud prevention program. All entities - including yours - need robust fraud prevention programs staffed with savvy and cunning fraud examiners. Here are some suggestions to help you develop a fraud prevention program in your organization.
Published in Fraud Magazine

Automatic intervention detection "an advanced computer-based tool" can be used to distinguish companies with fraudulent data from those with no indication of fraudulent reports. This article details some useful tools that automatically work to detect fraud in selected data.
Published in Fraud Magazine

Sophisticated computer forensics programs could be a bit pricey for your examinations. Knoppix, a free offspring of the open-source Linux operating system, may be just what you need.
Published in Fraud Magazine

Entities worldwide must transform security departments into rigorous fraud prevention programs staffed with qualified fraud examiners. Failed corporations and tougher legislation are forcing entities throughout the world to transform weak, reactive security departments into robust, proactive fraud prevention programs with one goal: stop fraud before it happens. This article outlines the principles from the joint professional document, Fraud Prevention Checkup.
Published in Fraud Magazine

In the Jan./Feb. 2004 issue we examined the basics of automatic intervention detection, an advanced computer-based tool. Here we describe the methodology of a research study conducted to explore the effectiveness of AID.
Published in Fraud Magazine

When reported results are intentionally misstated, earnings management becomes fraud. Corporate scandals including Enron, and WorldCom, and these entities' external auditor, Arthur Andersen, are instructive on such accounting and business abuses. They also point to the critical need for further involvement of fraud examiners in assuring the verity of published financial information.
Published in Fraud Magazine

By identifying a subject's dominant mode of expression -- visual, auditory, or sensation (and when he or she deviates from it) you can mirror the subject and begin to achieve rapport.
Published in Fraud Magazine

To increase fraud prevention, deterrence, and detection in any organization, we must make anti-fraud foot soldiers out of as many employees as possible. More information reported to the CFE concerning indications of possible fraud can only increase the amount of fraud that will actually be uncovered.
Published in Fraud Magazine

Tom Westwood could charm the paint off the side of his house. But as the controlling shareholder of a large car dealership he also could find ways to misappropriate company funds to repaint that same house. This article describes his fraud scheme and how he was caught.
Published in Fraud Magazine

Crafty manipulators will use weak employees at construction job sites to defraud companies for many months – long before the home office smells any problems.
Published in Fraud Magazine

Credit card fraud continues to be a menace especially in developing countries. But credit card companies and issuing banks are working to stay one step ahead of large global syndicates.
Published in Fraud Magazine

Determining deception in an interview requires the fraud examiner’s abilities to detect subtle change, limit disbelief in the subject, and suppress emotional responses.
Published in Fraud Magazine

Douglas R. Carmichael, Ph.D., CFE, CPA, chief auditor of the Public Company Accounting Oversight Board, has the tough task of guiding the standards-setting procedures of the Sarbanes-Oxley Act while balancing the interests of diverse groups. This CFE is ready for the challenge.
Published in Fraud Magazine

There's no shortage of desperate or fraudulent property owners in today's market for commercial mortgage loans. "Cash-out refinancing" is one favorite way to bail out of a troubled property. This primer offers advice to fraud examiners, lenders, and appraisers on spotting and preventing these and other frauds.
Published in Fraud Magazine

Non-sworn fraud examiners can optimize their chances for prosecution of white-collar crimes by avoiding things that law enforcement officers just hate. This article discusses the importance of developing the investigation's goals early on, narrowing the examination report to the criminal activity, and maintaining the worth of evidence through a proper chain of custody.
Published in Fraud Magazine

Catching identity thieves requires solid cooperation and hard-hitting procedures among fraud examiners, auditors, law enforcement, postal inspectors, the courts, banks, credit card companies, business owners, government, and many others.
Published in Fraud Magazine

David Namer had the perfect place for your retirement money: mid-yield corporate bonds – Private Placement Memorandums – backed by insurance from a top-rated company. It was perfect until the pyramid collapsed. Learn how this convicted former banker took thousands of small investors for almost $35 million.
Published in Fraud Magazine

The Personal Information Protection and Electronics Documents Act, which went into full force Jan. 1, 2004, for all entities involved in Canadian commercial activity, seriously affects the collection and disclosure of personal information including due diligence on prospective and current employees and internal fraud examinations.
Published in Fraud Magazine

An entity’s vendor search may be impeded by haste, lack of time, laziness, or entrenched tradition. Regardless, the fraud examiner should inspect the procurement competition system and its internal controls for possible kickbacks and other cozy relationships.Though inadequate competition for procuring vendor contracts is a good potential indicator of fraud, waste, or abuse, many fraud examiners fail to scrutinize the quality of the competition process. However, systematically gauging procurement competition should be a vital part of any fraud examination program.
Published in Fraud Magazine

David Walker is an anomaly: a top U.S. federal official beholden to no political party. And he likes it that way. As comptroller general of the United States and head of the General Accounting Office (GAO), Walker is charged with improving the performance and the accountability of the federal government for the benefit of the American people. Fraud, waste, abuse, and poor management are his enemies and his allies are truth, transparency, and accountability.
Published in Fraud Magazine

The C4 quotient — a combination of curiosity, creativity, critical thinking and collaboration — increases with the freedom to explore and innovate in our workplace. Backed by psychology and neuroscience, effective leaders can foster a more engaged and productive workforce, and in turn eliminate instances of fraud and abuse.
Published in Fraud Magazine

Thulisile “Thuli” Madonsela has probably done more than any single person in South Africa to bust the lid off widespread fraud and corruption during the term of former President Jacob Zuma. She speaks about her experiences during that time and what more needs to be done.
Published in Fraud Magazine

Sometimes fraud examiners need to record covert surveillance in their cases. But will their audio and video recordings be admissible in court? Here we examine a high-profile bribery case to test all the legal angles in deciding the usability of evidence in Europe and, by extension, the rest of the world.
Published in Fraud Magazine

Pet poodle comes to the rescue in German fraud case. Hospital employee accused of skipping work on full pay for 15 years. Fraudsters steal millions in Hong Kong’s biggest phone scam.
Published in Fraud Magazine

Fraudsters combine stolen personally identifiable information from many different individuals to create dangerous Frankenstein identities. Guard against this growing insidious fraud and protect the IDs of your customers.
Published in Fraud Magazine

Our profession requires plenty of insight and knowledge to understand the fraud landscape. But it also takes a good measure of moxie. Thulisile “Thuli” Madonsela is one of those unique people who possesses that know-how and fortitude — at an extraordinary level.
Published in Fraud Magazine

Since becoming a CFE close to 20 years ago, Sophia Pretrick has been fighting fraud in the Federated States of Micronesia, where she grew up. Early in her career, Pretrick quickly became fascinated with how ubiquitous fraud was and the fact that preventing it could improve the lives of her fellow Micronesians. This year, the U.S. Secretary of State Anthony Blinken awarded Pretrick with the newly created International Anticorruption Champions Award in recognition of individuals who’ve worked tirelessly to defend transparency, combat corruption and ensure accountabilities in their countries.
Published in Fraud Magazine

Fraud examiners understand the importance of knowing whom you’re doing business with. From compliance and due diligence to investigative asset tracing, solid background-checking skills are key tools for CFEs. But beyond traditional methods, new techniques are emerging to greatly enhance business transparency — and some may surprise you.
Published in Fraud Magazine

Bernie Madoff is gone, but the effects of his crimes live on. Fraud examiners endeavor to learn from all frauds, including the world’s largest-ever Ponzi scheme. What lessons have we learned? How has the regulatory environment improved? How have Madoff’s schemes affected the anti-fraud profession?
Published in Fraud Magazine

Preet Bharara speaks about lessons learned, the outlook for new insider trading rules under the Biden administration, the challenges of overseeing COVID-relief funds, the difficulties of investigating Ponzi schemes and much more.
Published in Fraud Magazine

Identity-theft fraudsters with no consciences use any opportunity to find new victims. Witness attempts to rip off vaccine hunters, caring grandparents and desperate job seekers.
Published in Fraud Magazine

It’s logical to think that companies on the verge of bankruptcy or suffering severe financial stress might be tempted to fudge their financial statements. Yet a recent university study says that large prestigious public firms are even more prone to cooking the books. We look at why this might be the case and the need to delve into the psychology of individual perpetrators.
Published in Fraud Magazine

The Wirecard case and recent PCAOB inspection reports on the top six audit firms highlight continued issues with audit quality and the independent auditor’s responsibility in uncovering material misstatements due to fraud. They also emphasize the need for the auditing profession to hasten improvements.
Published in Fraud Magazine

The battery in your cellphone could be powered by cobalt derived from copper that exploited “artisanal miners” — often children — hand dug from open-pit mines in the Democratic Republic of Congo. But a new DRC government could crack down on the illegal awarding of mine licenses, permits and contracts. And blockchain could make supply chains more transparent.
Published in Fraud Magazine

Dan McCrum, an investigative reporter for the Financial Times, spent six years questioning the finances of Wirecard, Germany’s moneymaking payments processor. Fraudulent Wirecard would strike back against McCrum and his wife with smear campaigns, lawsuits and surveillance. German banks and regulators targeted him. But his efforts paid off. Read about his crazy, weird investigation.
Published in Fraud Magazine

All of us want to look in the mirror and feel good about ourselves. But secretly we also want to benefit some from our dishonesty. Acclaimed behavioral economist Dan Ariely ponders this dichotomy every day. His research findings could help fraud examiners deter would-be fraudsters.
Published in Fraud Magazine

Deutsche Bank’s “referral fees,” China’s corruption death sentence and more
Published in Fraud Magazine

The FraudClassifier model, developed by a U.S. Federal Reserve-led industry work group, provides the payments industry with an intuitive classification approach to help fraud fighters get on the same page to understand the nature and magnitude of fraud.
Published in Fraud Magazine

Wirecard was once a fast-rising European fintech company that grew primarily through acquisitions. Now it’s dubbed the “Enron of Germany.”
Published in Fraud Magazine

Illegal logging companies in the Amazon regions, which are driving deforestation, are using multiple fraud schemes. They include fake or forged permits based on fraudulent information; corruption and collusion of and with officials who are supposed to enforce timber regulations; and front companies to avoid taxes.
Published in Fraud Magazine

Chrysti Ziegler, CFE, the president of the ACFE Houston Area Chapter, was thrilled to discover the art of fraud fighting early in her career as an auditor. Her interest was piqued when she first learned about the idea of malicious intent. She was hooked. Her passion then grew for joining the force against fraud.
Published in Fraud Magazine

Bad actors don’t let a good crisis go to waste. Shifting of governmental department of health mandates and the absence of systems to capture evidence of compliance have contributed to a perfect storm of fraudulent employment claims during the pandemic. But you can still find hard data to drive your investigations and defense strategies.
Published in Fraud Magazine

Amazon and Apple aren’t calling you to warn you of suspicious activity. And vaccine scammers are here. Plus don’t get lax in concocting new passwords.
Published in Fraud Magazine

Published in Fraud Magazine

The COVID-19 pandemic changed the way we work and provided an opportunity for fraudsters to scam the populace like never before. The ACFE Board of Regents looks back on its experiences and provides advice on how to fight fraud in this post-coronavirus landscape.
Published in Fraud Magazine

Fraudsters love a good crisis. Governments worldwide established procurement procedures during COVID-19, but quick actions to save lives often bypassed standard safeguards. Here’s how government agencies during future disasters can limit and/or prevent rampant corruption and fraud.
Published in Fraud Magazine

Published in Fraud Magazine

Cyberattacks have always made headlines. But they’re now occurring more frequently and causing widespread damage. Hackers have broadened their reach by infecting supply chains with ransomware and have recently crippled oil pipelines, meatpacking plants and grocery stores across the globe.
Published in Fraud Magazine

Tania Ramirez started her career as an internal auditor, working at such organizations as Canadian National Railway, McGill University and consultant Protiviti. She soon discovered she had a knack for uncovering dubious transactions. That talent catapulted her into the world of fraud investigations and landed her a dream job at Randstad, a global leader in the human resources services industry, where she now combines both skills to uncover cybercrimes, occupational fraud and other types of fraudulent activity.
Published in Fraud Magazine

You knew that when U.S. states began holding vaccine lotteries and sweepstakes, fraudsters would get in on the action. Also, here’s what happens when crooks attack their victims — again.
Published in Fraud Magazine

Organizations are increasingly striving to meet environmental, social and governance (ESG) standards, at least on paper. CFEs may be well versed in the “G” of ESG but they also need to know about the “E” and “S” to understand whether CEOs are truly sticking to the values they tout.
Published in Fraud Magazine

Intuition, sensitivity to nonverbal cues, pattern recognition — our brains are capable of rapidly processing information to help us make judgments and decisions. This ability is called “thin-slicing.” It can provide another tool for fraud examiners to follow their instincts to the truth but only when we use it properly and recognize its limitations.
Published in Fraud Magazine

With people increasingly living their lives online, fraudsters have never had easier access to potential victims. COVID-19 has only accelerated that trend. Indeed, business is booming for cybercriminals now focused on high-value organizations. Fraud Magazine talks to cyber expert Robert Herjavec and CFEs about how best to tackle this ever-evolving threat.
Published in Fraud Magazine

Cheating in online higher-ed classes existed long before the pandemic. Not surprisingly, exam fraud burgeoned when COVID forced most students to work in isolation. CFEs should consider how to minimize the chances for college cheaters to become occupational fraudsters and so limit negative effects for workplaces.
Published in Fraud Magazine

When the U.S. Affordable Care Act was enacted in 2010, the for-profit drug rehab industry was essentially given a blank check to treat people struggling with addiction. In the decade since, many of these underregulated businesses — rife with fraud, waste and abuse — have commoditized addicts. Through the lens of a recent high-profile criminal case in California, here’s the background on the issue, and some advice from experts on how to combat this unique type of provider fraud.
Published in Fraud Magazine

Published in Fraud Magazine

Amid a surge in global mergers and acquisitions, regulators are increasingly holding organizations responsible for the bribery, corruption and fraud found at the entities they purchase. Data analytics is becoming an important tool in a due diligence process that’s more important than ever for companies seeking to avoid such risks.
Published in Fraud Magazine

Every organization has them: toxic leaders who sacrifice others for their selfish needs. At the very least, these managers can make our jobs difficult or derail our investigations and, at worst, commit fraud. Here’s how to deal with them.
Published in Fraud Magazine

Small businesses are particularly susceptible to payroll fraud, and they can go under as a result. Here’s a story about a controller who used many tricks in the books to rob a medical practice and some lessons on how to detect and avoid such scams.
Published in Fraud Magazine

On Dec. 2, 2001, Enron declared bankruptcy. Governmental and media investigations led to criminal and civil trials of executives Ken Lay, Jeffrey Skilling, Andrew Fastow and many more. U.S. legislation ensued, but did the collapse of this corporation, which ruined so many lives, engender any lessons?
Published in Fraud Magazine

Published in Fraud Magazine

When I first started teaching fraud at the university level about 20 years ago, I had no idea that I was about to be handed a case study like no other. A few months later the now-infamous accounting scandal at Enron hit the headlines, and the once-celebrated energy firm collapsed in disgrace soon thereafter.
Published in Fraud Magazine

The COVID-19 pandemic has created a host of public health crises — and unearthed more opportunities for fraud. Scammers and fraudsters are waiting in the wings to capitalize on lax controls and vulnerable public assistance programs. Here the authors cover ways to enrich and strengthen your organization’s fraud risk management program to reduce threats from bad actors and to help spot the red flags of criminal activity.
Published in Fraud Magazine

Timothy Pikas has spent his career fighting fraud on behalf of various U.S. governmental agencies, including the Air Force Office of Special Investigations, the Nuclear Regulatory Commission and the Department of the Interior. Along the way, the 2021 Certified Fraud Examiner of the Year learned that a solid fraud case takes time to build, and he counsels fellow CFEs to keep the faith and remain patient when conducting their own fraud examinations.
Published in Fraud Magazine

The Fraud Risk Management Guide has provided valuable guidance to fraud examiners, company leaders and other professionals since it was published five years ago. Now, the Committee of Sponsoring Organizations of the Treadway Commission and the ACFE — the guide’s creators — will incorporate users’ feedback to produce a stronger, updated edition.
Published in Fraud Magazine

Fraudulent use of letters of credit has run rampant in Libya amid a chaotic civil war. We look at cases in this opaque corner of the trade finance market to better understand how fraudsters are exploiting a financial instrument that helps drive global trade but also opens doors for wrongdoing.
Published in Fraud Magazine

Non-fungible tokens are all the rage in the crypto world, potentially revolutionizing the sale of everything from art to real estate. But their complexity and the public’s poor understanding of the new technology make NFTs perfect vehicles for fraudsters.
Published in Fraud Magazine

In North America, toll-free phone numbers have one of the area codes 800, 844, 855 and several others, including 833. Fraudsters have seized that last area code to entice would-be victims to divulge personally identifiable information. Also, here’s information on a new COVID-19 scam and a gift-card fraud that purportedly involves your boss.
Published in Fraud Magazine

Most of us know it’s more “blessed to give than receive,” but hectic work and family schedules (and pesky pandemic problems) can keep us from imparting our knowledge. But don’t let lofty assumptions of mentorship keep you from the joy of giving newish fraud examiners the career boosts they need. Here are practical ways to get started.
Published in Fraud Magazine

The U.S. Congress has approved a record $5 trillion in aid packages so far to help Americans survive the pandemic, opening up new territory for fraudsters to ply their trade. Fraud Magazine talks to two of the top professionals leading the government’s fight against fraud and finds out why CFEs are required more than ever.
Published in Fraud Magazine

Insider-fraud risks are on the rise as the economic and psychological fallout from the COVID-19 pandemic takes its toll on organizations and their employees. Understanding these risks and knowing how to manage them will be an important part of many CFEs’ jobs.
Published in Fraud Magazine

Published in Fraud Magazine

SIGPR, the U.S. office mandated to audit and investigate fraud and abuse of the $2 trillion COVID-19 aid package known as the CARES Act, is now ready to take on the task at hand. It could be a busy few years ahead.
Published in Fraud Magazine

At the height of the COVID-19 pandemic last June, the ACFE pivoted the ACFE Global Fraud Conference to a virtual format to keep attendees, speakers and sponsors safe. The ACFE stood firm in its commitment to provide quality education and resources for anti-fraud professionals, and it delivered. More than 4,000 fraud fighters gathered virtually in a breakthrough format to share knowledge, network with like-minded professionals and learn from the industry’s top leaders.
Published in Fraud Magazine

In some of the first COVID-19 articles Fraud Magazine published nearly a year ago, we warned how the pandemic was creating the perfect storm for fraudulent activity to thrive. Sadly, those predictions have proven true as record amounts of COVID-relief money flood the economy.
Published in Fraud Magazine

Arpinder Singh, CFE, got his start investigating fraud when he discovered the field of forensic accountancy just as India’s economy took off following sweeping reforms in the early 1990s. Forensics proved to be an excellent career choice as corporate India increasingly focused on governance issues, including fraud detection and prevention.
Published in Fraud Magazine

The U.S. Sarbanes-Oxley Act of 2002 mandated strict reforms to existing securities regulations and imposed tough new penalties on lawbreakers. The U.K. might soon adopt similar legislation, which could significantly change board responsibility for fraud risk management and increase demand for anti-fraud professionals.
Published in Fraud Magazine

When employment circumstances change and pressures mount, criminals might disguise red flags of misbehavior. Because past actions can be a useful indicator of future behavior, background checks provide a snapshot of an applicant’s criminal, credit and employment history. Here we discuss the importance of background checks and how to properly vet your applicants.
Published in Fraud Magazine

If 2020 wasn’t bad enough, some experts believe the COVID-19 pandemic is creating the perfect conditions for an increase in Ponzi schemes. Here’s some advice on how best to deal with this type of fraud and why these schemes persist.
Published in Fraud Magazine

Most medical office practices trust their employees to handle daily financial matters. But what do they do when they catch long-term, trusted employees stealing? Here’s information you can use if you might be looking for medical-practice fraud detection and prevention business, and want to help doctors mitigate losses and claim restitution.
Published in Fraud Magazine

Unusual circumstances open opportunities for fraudsters, and 2021 is no exception. Not only has an uptick in online tax filings during the pandemic spurred new ways to cheat Americans out of their refunds, but utility scams related to winter deep-freezes are on the rise. Here’s what you should do to protect yourself.
Published in Fraud Magazine

Investigators and auditors spend hours looking for fraud and abuse but often overlook the third bad boy: waste. Fraud is flashy, and abuse is sinister. But waste often gets a short shrift. These CFEs encourage us to look for waste so we can save our organizations millions during these lean times.
Published in Fraud Magazine

“Ikigai,” the Japanese notion of being truly fulfilled and how a person’s work relates to their purpose, spurred former paralegal Tracy Swaim to seek more. Conversations with a fraud investigator excited her about entering the field. She earned her CFE credential and now works in a job that checks all the boxes for her: mission, passion, vocation and profession.
Published in Fraud Magazine

Despite futurists’ predictions, we don’t live in a paperless business world. Printer ink and toner are still an expensive necessity. Fraudsters depend on ink costing organizations more than caviar. Here’s how to prevent this asset misappropriation and possibly save millions.
Published in Fraud Magazine

How do fraud examiners conduct fraud examinations when they often can’t meet their team members and subjects in person? These experts — during pandemic constraints — discuss their biggest investigation hurdles, maintaining professional skepticism, best practices, eDiscovery challenges, chain of custody, interviewing constraints and more.
Published in Fraud Magazine

CFEs should consider all aspects of a fraud case when calculating the impact of fraud. Here are three primary calculations when reporting the amount of fraud impact: Total exposure, fraud amount and known loss.
Published in Fraud Magazine

From its early days as The White Paper to the 72-page bimonthly publication it is now, Fraud Magazine’s continued credibility and necessity to the anti-fraud profession is in part thanks to the leadership of its editor-in-chief, Dick Carozza. After 25 years at the helm, Carozza is stepping back and retiring. Here we take a look at the history of Fraud Magazine and the large role Carozza played in its success.
Published in Fraud Magazine

Ponzi schemer flees on water scooter, shysters rent parking spots and more
Published in Fraud Magazine

Imagine if citizens, journalists, oversight agencies, and internal and external auditors were able to view all transactions of taxpayer and donors’ money online. The fraud prevention and deterrence possibilities are endless.
Published in Fraud Magazine

Cybercriminals hit public institutions hard with ransomware in 2019 and 2020. Colleges and universities lost millions to fraudsters. These thieves endangered students’ records and stole PII, which they sold on the dark web. Administrators must train students, educators and staffs to avoid opening suspicious email attachments.
Published in Fraud Magazine

2020 is officially behind us, but its repercussions will live with us for a long time. Nothing prepared us — professionally or personally — for the pandemic. COVID-19 probably has permanently changed the ways we operate. But we’ve been resilient as we work through tremendous disruptions. We’re fighting the good fight to protect our organizations from fraud despite our limitations.
Published in Fraud Magazine

The pandemic is leading to increased fraud and criminals’ evolving tactics. Fraud examiners are facing budgetary and logistical constraints, and operational limitations. Here’s how these conditions could affect European anti-fraud efforts this year.
Published in Fraud Magazine

Alan Small, CFE, first became acquainted with fraud investigations in 1973 as a member of the Baltimore (Maryland) Police Department. His first assignment was with the criminal investigation division where he reviewed and followed the assignments of experienced detectives engaged in the investigation of high-profile cases, which included fraud.
Published in Fraud Magazine

More organizations are collaborating with data-sharing consortiums to safely exchange fraud risk profile information that could improve their internal prevention and detection activities. Here’s an interview with Matt Galvin, global VP of ethics and compliance at Anheuser-Busch (AB) InBev, who discusses how cross-company collaboration might affect the anti-fraud profession.
Published in Fraud Magazine

Jerry thought he had it made in the shade. As he began his company maintaining oil rigs and equipment, he'd found ways – the keys to the kingdom – to fraudulently bill his former employer as a contractor. He knew how to thoroughly exploit the system he'd helped devise. Learn lessons from this fictionalized version of an actual $2 million fraud case.
Published in Fraud Magazine

We were all glad to discard our 2020 calendars. Fraudsters took advantage of COVID-19 conditions, but not all of them needed an pandemic to pull off some big frauds. We've distilled a long list of cases to give you a few shockers.
Published in Fraud Magazine

The pandemic is bad enough, but scammers are out there waiting to steal your money and identity via COVID-19 fraud. Here also is the newest utility bill scam.
Published in Fraud Magazine

Find resources for ACFE members and others to foster diversity, equity and inclusion in the anti-fraud community and beyond.

From synthetic business identities to cybercrime to theft of services, the risks of transacting with other businesses can be significant.

Anti-fraud practitioners have a critical role to play in the future of ESG programs. Regulatory and reporting frameworks are struggling to keep up with the pace of change.

Tips are the most common way fraud schemes are detected. An effective whistleblower hotline is a vital part of a comprehensive anti-fraud program.

The Global Fraud Survey gathers meaningful information on how fraud is committed, how it is detected, who commits it and how organizations respond.

The following resources were established to aid government organizations in detecting and preventing government fraud at all levels around the world.

Since the Association of Certified Fraud Examiners began in 1988, we have produced relevant, one-of-a-kind publications dedicated to covering the latest in fraud prevention and detection.

Use these ACFE tools to help you assess fraud risk, create your own fraud response plan and find the expertise you need.

Fraud professionals can use these tools to assist organizations in identifying fraud risks and developing a fraud risk response.

Clear, credible and sound policies are the cornerstones of effective fraud prevention. Use our already developed and tested documents to guide you in crafting policies, proposals, reports and forms.

Discover our featured case studies and learn how many of today’s fraud cases are old schemes dressed in new technology with a new cast of characters.

From case studies to the latest data, find what you need to stay up to date on the latest in fraud prevention and detection with these free ACFE resources.

Shell companies can be used to commit nearly every type of fraud — from simple billing fraud schemes to complex, multi-jurisdictional money laundering operations.


If you need assistance with investigating a potential fraud or proactively protecting your organization from future frauds, a CFE is your best resource.


Strengthen fraud risk management with COSO and the ACFE's guidelines, featuring essential tools and strategies for developing effective anti-fraud programs.

The ACFE's Fraud Risk Assessment tool is an invaluable resource for fraud examiners to use in identifying and addressing their clients' or employers' vulnerabilities to internal fraud.

Discover the latest insights on anti-fraud technologies' effectiveness in managing fraud risk, and learn how organizations are leveraging data and technology in their anti-fraud programs.

The Fraud Awareness Training Benchmarking Report highlights training's role in enhancing anti-fraud controls and policy compliance.

Test your company’s fraud health with this free training resource featuring a checklist.

The latest fraud news, insights and ACFE member-exclusive resources delivered to your inbox.

ACFE report finds direct correlation between economic downswings and fraudulent activity

The ACFE Brand Guidebook, as well as the accompanying resources below, are designed to help you promote yourself and your affiliation with the ACFE.

Resources and reporting tools to use if you or someone you know has been affected by fraud.


Tips are the most common way fraud schemes are detected. An effective whistleblower hotline is a vital part of a comprehensive anti-fraud program.
